Transcribing James Clapper

Hamid Karzai refused to meet with Obama during a surprise visit just after MYSTIC disclosures, so Obama called from Air Force One instead.
Yesterday, during the Q&A to his speech at INSA (which is where defense and intelligence contractors huddle with government paymasters), James Clapper conceded that Edward Snowden brought needed transparency but had also damaged operations. Rather than obliquely pointing to the exposure that Skype was no longer safe from surveillance, as he and his ilk normally do, Clapper pointed to what he claimed was a concrete example: what journalists have reported as revelations about full take cell phone content (SOMALGET or MYSTIC) leading to loss of access in Afghanistan.
After Clapper made the claim, a lot of reporters did what reporters do: they transcribed his comments uncritically. Lots of journalists did this, but here’s WaPo’s version from Ellen Nakashima:
One of the disclosures based on documents leaked by Edward Snowden, the former National Security Agency contractor, prompted the shutdown of a key intelligence program in Afghanistan, the nation’s top spy said Wednesday.
“It was the single most important source of force protection and warning for our people in Afghanistan,” Director of National Intelligence James R. Clapper Jr. said at an intelligence conference.
He was addressing a question about the impact of revelations by Snowden, whose leaks led to a global debate about the proper scope of U.S. surveillance at home and abroad.
Nakashima and other reporters assumed Clapper meant the MYSTIC/SOMALGET program, which Nakashima noted the WaPo first described (on March 18, 2014), followed by The Intercept two months later (on May 19, 2014), followed by WikiLeaks revealing Afghanistan as the target country several days later (on May 23, 2014). [Update: Note Cryptome correctly determined Afghanistan was the country on May 19, the day the Intercept published.]
Having laid all that out, however, Nakashima doesn’t quote the part of Clapper’s answer that would either discredit his description or reveal it’s something else. Here’s Ars Technica’s transcription of that part of it.
And programs that had a real impact on the security of American forces overseas, including one program in Afghanistan, “which he exposed and Glenn Greenwald wrote about, and the day after he wrote about it, the program was shut down by the government of Afghanistan,” Clapper noted.
If it’s the MYSTIC/SOMALGET program Clapper was really talking about, then his claim is self-refuting. Because either folks in Afghanistan recognized the program themselves back when WaPo wrote about it in March 2014, or probably didn’t until WikiLeaks confirmed they were the target. It wouldn’t have been Greenwald’s story, in which he withheld the information the government requested in any case.
For the moment, I’m going to assume that was the program, but let’s remember it might not be.
If so, consider what Clapper has done. As I mentioned, normally when people want to beat up Snowden, they point to his disclosure NSA had compromised Skype. But they never confirm that — they just mention it obliquely. Here, Clapper has confirmed the thing (actually just one of the things) that NSA had asked Greenwald to withhold. Given how vague WikiLeaks was about how they knew (after all, they’re not known to have the Snowden documents themselves), if this is MYSTIC/SOMALGET it seems that Clapper has definitively confirmed something that was at least of unknown provenance before.
Although, for reasons of source protection we cannot disclose how, WikiLeaks has confirmed that the identity of victim state is Afghanistan.
In other words, Clapper has confirmed something that hadn’t been confirmed before, precisely because the journalists involved had deferred to the government’s request not to publish it.
Or did he?
Clapper claimed “the program was shut down by the government of Afghanistan.”
Admittedly, the MYSTIC/SOMALGET disclosures came at an awkward time for US-Afghan relations. Hamid Karzai had been pushing back against night raids, prisoner transfers, and CIA militias. In part because the US wouldn’t cede Afghan sovereignty on such issues, Karzai was refusing to sign the Bilateral Security Agreement (raising the same kind of SOFA negotiation problems that forced us to withdraw troops from Iraq). Throughout this two month period, the election and run-off were going on.
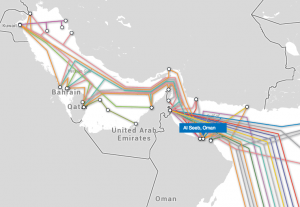
So the disclosure that the US had compromised Afghanistan’s entire cell phone system — and implicitly, had copies of every cell call that Karzai and his potential replacements might make — would surely anger the Afghans, especially Karzai. Notably, two days after the WikiLeaks disclosure, Karzai refused to meet when President Obama made a surprise visit to the country on May 25, so (as shown by the White House image above) Obama called him from Air Force One instead.
But if that’s the case — if Afghanistan forced the US to shut down the full-take collection of cell phone content even as Obama was making surprise last minute visits (which may even have been an attempt to convince Karzai to reverse that decision) — then the fault lies not just, or even primarily, with Snowden. It lies with a long history of US refusal to cede to Afghanistan’s demands for some kind of functional sovereignty. This telecom disclosure may have been one more in a series of aggravations, but it was by no means the only one. Moreover, given that President Ghani’s relationship with the US is, thus far at least, far better than Karzai’s was at the time, it’s quite possible he has permitted the US to resume full-take collection.
James Clapper would be a lot more likely to confirm that Afghanistan had shut down NSA’s full-take collection if it had been resumed again under Karzai’s successor. Not least, because it would provide adversaries with false confidence the NSA didn’t have full take coverage.
Now consider this description of the Bahamian fallout from the equivalent disclosure. It shows that two parties were involved — the country’s telecom as well as the government. Indeed, all stories on this make it clear telecom providers are centrally involved in the collection program.
Moreover, the Intercept version of the story makes it quite clear they withheld not just the target country, but also the provider at the center of it.
The NSA documents don’t specify who is providing access in the Bahamas. But they do describe SOMALGET as an “umbrella term” for systems provided by a private firm, which is described elsewhere in the documents as a “MYSTIC access provider.” (The documents don’t name the firm, but rather refer to a cover name that The Intercept has agreed not to publish in response to a specific, credible concern that doing so could lead to violence.) Communications experts consulted by The Intercept say the descriptions in the documents suggest a company able to install lawful intercept equipment on phone networks.
And they withheld it for the same reason, because revealing it would lead to violence. That provider name has not been made public (though for a variety of reasons I think that’s the key secret here). Shutting down the system would have to involve, at a minimum, the Afghan government, this provider, plus Afghanistan’s multiple cell providers.
There are more reasons to believe Clapper’s story is bullshit. From the 2005 STELLAR WIND disclosures, which revealed the US was collecting all US-Afghanistan calls, to reports as early as 2008 that the Taliban were targeting cell providers because they recognized the security risk the networks posed, there is zero chance our adversaries in Afghanistan were unaware that the US had close to full dominance over the communications lines. There were also earlier Snowden disclosures — including Tempora, XKeyscore, and what sounded like transcripts obtained using a Stingray from a Afghan raid — that would have confirmed that view. The US is collecting close to everything from most countries where it remains at war, via a variety of overlapping means. There’s little about this disclosure in particular that added to the risk — but then, our adversaries had long been learning of our tactics and adjusting accordingly.
There is, then, the possibility it was one of these other disclosures Clapper was whining about — such as the potential Stingray one.
But if Clapper was talking about SOMALGET, and if it is true that the full-take collection got shut down, it means he and the government are blaming Snowden for long-term mismanagement of the Afghan relationship. It also may well mean that Ghani has let the US resume collection and Clapper’s public “confirmation” was designed — in addition to launching some unwarranted shots at Edward Snowden — to create the false impression the collection remains inactive.
James Clapper is a confirmed liar. Even setting aside his lies to Congress, it is his job to lie to adversaries. While that doesn’t mean journalists shouldn’t report what he says, there’s a great deal of context that should accompany such transcriptions.