When Mueller’s team released George Papadopoulos’ plea deal last year, I noted that the initial denials that Papadopoulos had advance warning of the emails the Russians were preparing to hack and leak did not account for the entire universe of emails known to have been stolen. A year and several Mueller indictments later, we still don’t have a complete understanding of what emails were being dealt when. Because that lack of understanding hinders understanding what Mueller might be doing with Roger Stone, I wanted to lay out what we know about four sets of emails. This series will include posts on the following:
- DNC emails
- Podesta emails
- DCCC emails
- Emails Hillary deleted from her server
The series won’t, however, account for two more sets of emails, anything APT 29 stole when hacking the White House and State Department starting in 2015, or anything released via the several FOIAs of the Hillary emails turned over to the State Department from her home server. It also won’t deal with the following:
- Emails from two Hillary staffers who had their emails released via dcleaks
- The emails of other people released by dcleaks, which includes Colin Powell, some local Republican parties (including some 2015 emails Peter Smith sent to the IL Republican party), and others with interests in Ukraine
- A copy of the Democrats’ analytics program copied on AWS
- The NGP/VAN file, which was not directly released by Guccifer 2.0, but is central to one of the skeptics’ theories about an alternative source other than Russia
Meuller remains coy about how the Podesta emails were released by WikiLeaks
My post on the DNC emails noted some timing curiosities about when and how the DNC emails got shared with WikiLeaks.
The curiosities about the Podesta emails, however, are far more important for questions about Roger Stone’s knowledge of the process.
As a number of people have observed, while Mueller’s GRU indictment provides extensive details describing how Podesta was hacked and showing that the infrastructure to hack him was used for other parts of the operation, the indictment is far more coy about how the Podesta emails got to WikiLeaks.
In or around 2016, LUKASHEV sent spearphishing emails to members of the Clinton Campaign and affiliated individuals, including the chairman of the Clinton Campaign.
[snip]
For example, on or about March 19, 2016, LUKASHEV and his co-conspirators created and sent a spearphishing email to the chairman of the Clinton Campaign. LUKASHEV used the account “john356gh” at an online service that abbreviated lengthy website addresses (referred to as a “URL-shortening service”). LUKASHEV used the account to mask a link contained in the spearphishing email, which directed the recipient to a GRU-created website. LUKASHEV altered the appearance of the sender email address in order to make it look like the email was a security notification from Google (a technique known as “spoofing”), instructing the user to change his password by clicking the embedded link. Those instructions were followed. On or about March 21, 2016, LUKASHEV, YERMAKOV, and their co-conspirators stole the contents of the chairman’s email account, which consisted of over 50,000 emails.
[snip]
The funds used to pay for the dcleaks.com domain originated from an account at an online cryptocurrency service that the Conspirators also used to fund the lease of a virtual private server registered with the operational email account [email protected]. The dirbinsaabol email account was also used to register the john356gh URL-shortening account used by LUKASHEV to spearphish the Clinton Campaign chairman and other campaign-related individuals.
[snip]
On or about October 7, 2016, Organization 1 released the first set of emails from the chairman of the Clinton Campaign that had been stolen by LUKASHEV and his co-conspirators. Between on or about October 7, 2016 and November 7, 2016, Organization 1 released approximately thirty-three tranches of documents that had been stolen from the chairman of the Clinton Campaign. In total, over 50,000 stolen documents were released.
Mueller’s silence, thus far, about how the Podesta emails got shared with WikiLeaks is intriguing for several reasons, even aside from the fact that (as noted in the last post) the first documents Guccifer 2.0 shared were billed as DNC emails but (as far as have been identified) are actually Podesta ones. Perhaps Mueller doesn’t know how those emails were passed on. Perhaps the sources and methods by which the FBI learned about how they were shared are too sensitive to put in an indictment. Perhaps Mueller has reserved that story for a later indictment.
The August to September timing on receipt of the emails
The publicly known timing is no more clear.
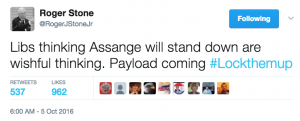
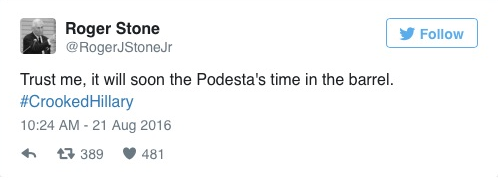
The Roger Stone tweet on which suspicions of advance knowledge of WikiLeaks’ releases rest — warning “Trust me, it will soon [sic] the Podesta’s time in the barrel” — is dated August 21, 2016.
That date is significant, because it’s not at all clear WikiLeaks had the Podesta emails by that point (and if so, may have just obtained them).
Raffi Khatchadourian cites a WikiLeaks staffer saying they received the emails in “late summer” but also points to an August 24 Fox News interview where Assange described processing “a variety of documents, from different types of institutions that are associated with the election campaign,” which doesn’t necessarily narrow down those emails to Podesta’s.
A pattern that was set in June appeared to recur: just before DCLeaks became active with election publications, WikiLeaks began to prepare another tranche of e-mails, this time culled from John Podesta’s Gmail account. “We are working around the clock,” Assange told Fox News in late August. “We have received quite a lot of material.” It is unclear how long Assange had been in possession of the e-mails, but a staffer assigned to the project suggested that he had received them in the late summer: “As soon as we got them, we started working on them, and then we started publishing them. From when we received them to when we published them, it was a real crunch. My only wish is that we had the equivalent from the Republicans.”
As we’ll see later in this series, there was more certainty that by August 24 WikiLeaks had other hacked emails than that they had Podesta’s.
Khatchadourian also notes that the raw files are all dated September 19 and describes Assange “weaponizing” the release of the data a week or two before the files were released starting on October 7.
All of the raw e-mail files that WikiLeaks published from Podesta’s account are dated September 19th, which appears to indicate the day that they were copied or modified for some purpose. Assange told me that in mid-September, a week or two before he began publishing the e-mails, he devised a way to weaponize the information. If his releases followed a predictable pattern, he reasoned, Clinton’s campaign would be able to prepare. So he worked out an algorithm, which he called the Stochastic Terminator, to help staff members select e-mails for each day’s release. He told me that the algorithm was built on a random-number generator, modified by mathematical weights that reflected the pattern of the news cycle in a typical week. By introducing randomness into the process, he hoped to make it impossible for the Clinton war room “to adjust to the problem, to spin, to create antidote news beforehand.”
That timing lines up in interesting ways with the date when retired British diplomat Craig Murray claims he got a handoff of something (he’s never explained precisely what it was, though it sounded like it could be an encryption key) relating to the Podesta emails when he was in DC to attend the Sam Adams Award ceremony on September 25.
All of which suggests significant events relating to the transfer to WikiLeaks and preparation of the Podesta emails happened after the Stone tweet.
Still later, according to a recent WSJ report, Peter Smith indicated that he knew Podesta emails were coming ahead of time (the reporting is not clear whether this was before or after the fact).
The person familiar with Mr. Smith recalled him repeatedly implying that he knew ahead of time about leaks of Mr. Podesta’s emails.
That claim is all the more interesting when you tie it to the email shared with Smith via foldering on October 11, seemingly reflecting happiness about emails already released, which would seem to point to the Podesta emails that started to drop four days earlier.
“[A]n email in the ‘Robert Tyler’ [foldering] account [showing] Mr. Smith obtained $100,000 from at least four financiers as well as a $50,000 contribution from Mr. Smith himself.” The email was dated October 11, 2016 and has the subject line, “Wire Instructions—Clinton Email Reconnaissance Initiative.” It came from someone calling himself “ROB,” describing the funding as supporting “the Washington Scholarship Fund for the Russian students.” The email also notes, “The students are very pleased with the email releases they have seen, and are thrilled with their educational advancement opportunities.”
The email apparently linking the contemporaneous release of the Podesta emails to a future hoped for release of deleted Hillary ones is significant for several reasons. First, it shows that other geriatric rat-fuckers, in addition to Stone, linked the two. The reflection of pleasure with emails on October 11 is significant given that that was the day WikiLeaks released two Podesta emails Smith associate Jerome Corsi and Stone would use to advance an attack on Podesta pertaining to his ties with Joule Unlimited, an attack that the right wing had been pushing since August (and working on since March). The WSJ notes that both Corsi and Charles Ortel (to the latter of whom Stone now ties some of his WikiLeaks claims) were tied to both Smith and Stone, though Stone claims to have been unaware of the Smith effort.
Stone’s three different explanations for his tweet and the import of Joule emails
In this post, I looked in detail at how epically shitty Stone’s current excuse for his August 21 Podesta tweet is. Over time, Stone has basically offered at least three excuses for it.
First he adopted an explanation offered in March 2017 by Jerome Corsi. In that explanation, Corsi basically conflated two efforts: an attack on John Podesta based on his service on the board of Joule Unlimited from 2010 to 2014, and an effort to respond to mid-August reports on Paul Manafort’s corrupt ties to Russia by focusing instead on Tony Podesta.
The Joule attack research was started (per web access dates recorded in this report) two days before Podesta was spearphished, on March 17, and first rolled out publicly in a Steve Bannon-affiliated Government Accountability Insitute report on August 1. Corsi and Stone resuscitated the attack starting on October 6 (the day before the Podesta emails started coming out), seemingly correctly anticipating the WikiLeaks email releases that Stone and Corsi would use to advance the attack.
The Corsi explanation that Stone once adopted conflated that attack with a report that Corsi did for Stone (starting at PDF 39), which largely projected onto Tony Podesta the corrupt ties to Ukraine and Russia that Paul Manafort had; the report only tangentially focused on John. The date on the Corsi report is August 31, ten days after Stone’s tweet, but Corsi claims he and Stone started it on August 14.
Stone offered a slightly different explanation when he testified under oath to the House Intelligence Committee. There, he generalized the attack on “the Podesta brothers” and attributed his tweet to “early August” discussions about the August 31 Corsi report. In his prepared statement, he made no mention of Joule.
In the wake of Corsi’s interview on September 6 and grand jury appearance on September 21 (in conjunction with which he reportedly shared a bunch of documents that would substantiate when he and Stone were talking about Joule and when about Tony Podesta), Stone changed his tune again, now only admitting publicly for the first time that Charles Ortel forwarded him an email showing James Rosen promising “a massive dump of HRC emails relating to the CF in September,” but also attributing any August 14 interest to something besides Corsi, a Breitbart post that may be this one.
Stone, however, says that the tweet was based on “an August 14th article in Breitbart News by Peter Schweitzer that reported that Tony Podesta was working for the same Ukrainian Political Party that Paul Manafort was being excoriated for,” and that “the Podesta brothers extensive business dealings with the Oligarchs around Putin pertaining to gas, banking and uranium had been detailed in the Panama Papers in April of 2016.”
Stone’s explanations seem to attempt to do three things:
- Provide non-incriminating explanations for any foreknowledge of WikiLeaks — first pointing to Randy Credico and now to James Rosen
- Offer explanations for discussions about Podesta that he may presume Mueller has that took place around August 14
- Shift the focus away from Joule and the remarkable prescience with which the right wing anticipated that WikiLeaks would be able to advance an attack first rolled out on August 1
With that in mind, I find the timeline of Stone’s tweets mentioning either Podesta instructive. It shows Stone never mentioned either brother until August 15 — the day after the first of the stories on Manafort’s Ukraine corruption and after that August 14 date he seems so worried about. That tweet, “@JohnPodesta makes @PaulManafort look like St. Thomas Aquinas Where is the @NewYorkTimes?” may prove as interesting as the August 21 one.
Stone mentioned John Podesta again in that August 21 tweet.
Then he remained silent on Twitter about Clinton’s campaign chairman until the day after the Podesta emails started coming out, whereupon Stone started claiming that Podesta had been money laundering for Russia.
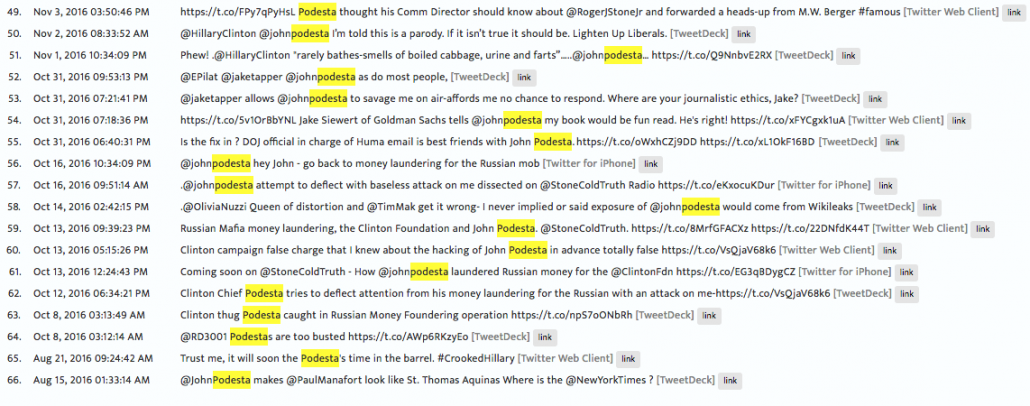
Stone’s first tweet as the Podesta emails dropped pointed back to an earlier Corsi post reporting that the Podesta Group was also under investigation. That same day, he pointed to the Corsi post that seemed to anticipate the Joule attack would be returning. Yet, in an interview done after the release on October 11 of the Podesta emails that both he and Corsi would later rely on to extend the Joule attack, Stone made no mention of those emails or the Joule attack. By the next day, however, Stone was relying on (but not linking) those emails.
In other words, at least as measured by his Twitter feed, Stone was uninterested in the Joule attack when it came out in August. He didn’t mention it at all in his two Podesta tweets that month (nor does he in his currently operative explanation). But he did become interested in the story in advance of the release of emails by WikiLeaks pertaining to the attack.
This is probably a good time to recall that many of the Stone associates Mueller has interviewed did research for Stone, and others had access to his social media accounts. Note that even this selection of his tweets show the use of multiple clients — Twitter Web Client, Tweetdeck, and Twitter for iPhone — that may reflect different people posting from his account.
Stone’s claims about WikiLeaks — and his outreach to Guccifer 2.0 — took place as Manafort started to panic about his own Russian ties
Given some of Stone’s explanations (and his apparent concern with offering some explanation for discussions about Podesta on August 14), I also find it notable the way this timeline overlaps with Manafort’s increasingly desperate efforts to stave off bankruptcy even while working for Trump for “free.” Part of those efforts, of course, involved criminal efforts to hide his ties to Russia in the wake of reporting on those ties in mid-August.
It’s unclear when Manafort knew for sure his ties with Russia would blow up. In the wake of the first WikiLeaks dump on July 27, he got asked about his and Trump’s ties to Russia, a question he struggled with before responding by pointing to Hillary’s deleted emails. In spite of the risk of his own Russian ties, Manafort met on August 2 with Konstantin Kilimnik, talking (among other things) about unpaid bills and the presidential election. Sometime in early August, in advance of the first NYT story substantiating his Russian ties, he was reportedly blackmailed over the secret ledgers of his work with Ukrainian oligarchs.
Remarkably, just as attention to Trump and Manafort’s ties to Russia started becoming an issue, Republicans had that GAI report insinuating a tie between Hillary and Russia all ready to go on August 1. That insinuation went through John Podesta and his ties to Joule. Before laying out that relationship, however, the GAI report suggested there must be more dirt on the topic in the emails Hillary deleted.
More recently, in January, 2015, Podesta became the campaign chairman of Hillary Clinton’s campaign for the 2016 presidential bid.85
During Hillary Clinton’s tenure as Secretary of State, he was in regular contact with her and played an important role in shaping U.S. policy. For one thing, he sat on the State Department’s Foreign Affairs Policy Board, appointed by Hillary. (The board was established in December 2011.)86
The full extent of Podesta’s email communication cannot ultimately be known because Hillary Clinton deleted approximately half of her emails after she left the State Department.
So along with everything else the report did, it built expectations that Hillary’s deleted emails would reveal secret dirt about Russia she was suppressing to win the campaign.
By the time the report came out, we know that Stone was already interested in what WikiLeaks might have, as Charles Ortel BCCed him on an email suggesting that WikiLeaks had Clinton Foundation emails to dump in September in late July.
Then, precisely as the Russian attack on Podesta was rolling out, Stone flip-flopped on his claimed belief about who hacked Hillary Clinton. Between August 1 and August 5, on the same days he was claiming to have dined with Julian Assange when he was instead in Southern California meeting his dark money associates, he started claiming that Guccifer 2.0 was just a hacktivist, not Russians. That stated belief has always been central to his claims not to have conspired with Russia.
In significant part because he flip-flopped publicly, he and Guccifer 2.0 started communicating, first about Stone’s claim that Guccifer 2.0 had nothing to do with Russia, then about Guccifer 2.0 being shut down on Twitter:
August 12: Guccifer 2.0: thanks that u believe in the real
August 13: Stone: @WL @G2 Outrageous! Clintonistas now nned to censor their critics to rig the upcoming election.
”
August 14: Guccifer 2.0: Here I am! They’ll have to try much harder to block me!
Stone: First #Milo, now Guccifer 2.0 – why are those exposing the truth banned? @RealAlexJones @infowars #FreeMilo
Stone:
That’s when Stone moved their conversations to DM.
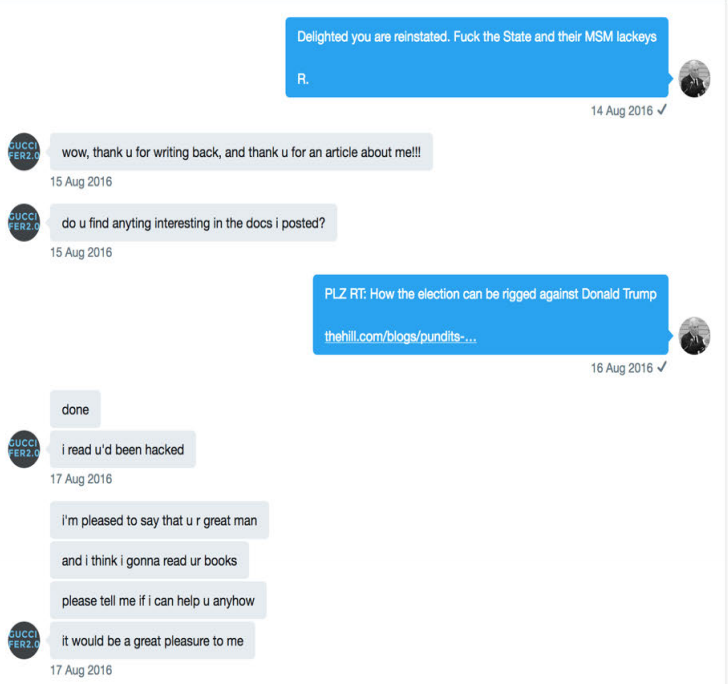
That conversation, including Guccifer 2.0’s question whether Stone found “anything interesting in the docs I posted?” (which, in public context at least, would refer to some DCCC documents Guccifer had posted on WordPress on August 12) took place even as Stone was continuing to speak about knowing what was in the next WikiLeaks dump and as he responded badly to his childhood friend becoming the target of NYT’s attention on August 14.
As noted, Stone seems to be struggling to answer why he was discussing John Podesta on August 14.
To be sure, Stone was talking to Corsi on August 14 or 15. On August 15, Corsi published an interview with Stone, in which he claimed to have been badly hacked and described what he expected would come next from WikiLeaks.
But nothing in the interview mentions Podesta.
Stone’s descriptions of what WikiLeaks might dump next in that interview could reflect the BCCed James Rosen email reporting that WikiLeaks would dump Clinton Foundation documents in September, but the information he laid out went far beyond that email (and promised an October surprise, not a September dump).
“In the next series of emails Assange plans to release, I have reason to believe the Clinton Foundation scandals will surface to keep Bill and Hillary from returning to the White House,” he said.
[snip]
In a speech Southwest Broward Republican Organization in Florida, published Aug. 9 by David Brock’s left-wing website Media Matters, Stone said he had “communicated with Assange.”
“I believe the next tranche of his documents pertain to the Clinton Foundation, but there is no telling what the October surprise may be,” he said.
Stone told WND that Assange “plans to drop at various strategic points in the presidential campaigns Hillary Clinton emails involving the Clinton Foundation that have yet to surface publically.”
“Assange claims the emails contain enough damaging information to put Hillary Clinton in jail for selling State Department ‘official acts’ in exchange for contributions to the Clinton Foundation and as a reward for Clinton Foundation donors becoming clients of Teneo, the consulting firm established by Bill Clinton’s White House ‘body man’ Doug Band,” he said.
That same day, August 15, is the first time Stone ever mentioned Podesta on Twitter.
Stone claims (and claimed, in sworn testimony) that his focus on John Podesta was a response to the allegations against Manafort. That makes the confluence of all these events all the more interesting.
Corsi’s lawyer claims he avoided criminal liability
As noted above, Jerome Corsi has explained what he knows of all this in a September 21 grand jury appearance, a grand jury appearance that Mueller seems to have been working towards since having Ted Malloch questioned way back in March.
In advance of that testimony, Corsi’s attorney David Grey seemed to suggest that Corsi declined to participate in certain activities involving Stone that might have exposed him to criminal liability.
Gray said he was confident that Corsi has done nothing wrong. “Jerry Corsi made decisions that he would not take actions that would give him criminal liability,” he added, declining to elaborate.
Asked if Corsi had opportunities to take such actions, Gray said, “I wouldn’t say he was offered those opportunities. I would say he had communications with Roger Stone. We’ll supply those communications and be cooperative. My client didn’t act further that would give rise to any criminal liability.”
But Mueller is apparently now chasing down Corsi’s associates.
FBI agents have recently been seeking to interview Corsi’s associates, according to the person.
One other key player in the Podesta hand-off conflated the Podesta brothers
The close ties between how Stone focused on both Podesta brothers in response to the public allegations against Manafort is interesting for another reason.
Former Ambassador Craig Murray, the only one not denying some role in the handoff of the Podesta emails (again, he has said he didn’t get the emails themselves, which he believed were already with WikiLeaks, but something associated with them).
Murray told Scott Horton that his source had obtained whatever he received from a figure in American national security with legal access to the information.
[H]e says “The material was already, I think, safely with WikiLeaks before I got there in September,” though other outlets have suggested (with maps included!) that’s when the hand-off happened. In that account, Murray admits he did not meet with the person with legal access; he instead met with an intermediary.
But the explanation of his source’s legal access and motivation not only doesn’t make sense, but seems to parrot what Stone was saying at the time.
I also want you to consider that John Podesta was a paid lobbyist for the Saudi government — that’s open and declared, it’s not secret or a leak in a sense. John Podesta was paid a very substantial sum every month by the Saudi government to lobby for their interests in Washington. And if the American security services were not watching the communications of the Saudi government paid lobbyist then the American intelligence services would not be doing their job. Of course it’s also true that the Saudis’ man, the Saudis’ lobbyist in Washington, his communications are going to be of interest to a great many other intelligence services as well.
As Stone did, this conflates John and Tony. It wrongly suggests that US national security officials would be collecting all of Tony Podesta’s emails, or that collecting on Tony would obtain all of John’s emails. All the more interesting, this conflation would have come in a period when Manafort’s lifelong buddy, Stone, was trying to distract attention from Manafort’s own corruption — which included telling Tony not to disclose the influence-peddling he had done for Manafort in the legally required manner — by projecting Manafort’s corruption onto Tony.
One more point about Murray. Murray has ties (including through the Sam Adams Association the awards ceremony for which he was in DC attending) to NSA whistleblowers Bill Binney (Murray received the award in 2005 and Binney received it in 2015) and Kirk Wiebe. This claim that US law enforcement would collect everything (including Hillary’s deleted emails) is the kind of line that Binney was pushing at the time, including to Andrew Napolitano, who was CCed on the email Stone received about WikiLeaks’ plans in July. Napolitano is one of the people who has championed that Binney line about the hack.
In other words, it’s not just that Murray was telling a similar story as Stone, even though they’re politically very different people. It’s that he was not that distant from the network of Republicans talking about what WikiLeaks might have had.
Update: Emma Best just wrote up something she’s been tracking for some time: there are four different numbers on how many Podesta mails there are.
WikiLeaks’ own data gives us five different totals for the number of Podesta emails:
- 50,866
- 57,153
- 58,660
- 59,258
- 59,188
The two most authoritative answers to the question come from WikiLeaks and the Special Counsel’s office, and both indicate that the total exceeded 50,000. While WikiLeaks’ stated there were “well over 50,000” emails, the Special Counsel’s indictment simply said that “over 50,000 stolen documents were released.” Since “documents” can be construed to include both the emails and their various attachments, the SC’s total is even more vague and less definitive than WikiLeaks’.

Ultimately, he best answer to the question of how many Podesta emails there are appears to be 59,188.
This raises the possibility that Stone or Corsi saw copies that WikiLeaks didn’t publish. Mueller’s distinction between how many emails were stolen and how many released suggests FBI may know what WikiLeaks chose not to public, if in fact they did.
Timeline
July 18-21: Stone meets Nigel Farage while at RNC
July 25: Stone gets BCCed on an email from Charles Ortel that shows James Rosen reporting “a massive dump of HRC emails relating to the CF in September;” Stone now claims this explains his reference to a journalist go-between
July 27: Paul Manafort struggles while denying ties to Russia, instead pointing to Hillary’s home server
July 31: GAI report on From Russia with Money claiming Viktor Vekselberg’s Skolkovo reflects untoward ties; it hints that a greater John Podesta role would be revealed in her deleted emails and claims he did not properly disclose role on Joule board when joining Obama Administration
August 1: Steve Bannon and Peter Schweitzer publish a Breitbart version of the GAI report
August 1: Stone NYC > LA
August 2: Manafort and Konstantin Kilimnik meet in the Grand Havana Room in Jared’s 666 Park Avenue and “talked about bills unpaid by our clients, about [the] overall situation in Ukraine . . . and about the current news,” including the presidential campaign
August 2, 2016: Stone dines with dark money funder, John Powers Middleton in West Hollywood
August 3 and 4: Manafort obtains the bio of Steve Calk, from whom he was getting a $16 million mortgage in tacit exchange for a role in the Trump administration
August 3: Stone claims to Sam Nunberg to have dined with Assange
August 3-4: Stone takes a red-eye from LAX to Miami
August 4: Stone flip-flops on whether the Russians or a 400 pound hacker are behind the DNC hack and also tells Sam Nunberg he dined with Julian Assange; first tweet in the fall StopTheSteal campaign
August 5: Trump names Calk to his advisory committee
August 5: Stone column in Breitbart claiming Guccifer 2.0 is individual hacker
August 7: Stone starts complaining about a “rigged” election, claims that Nigel Farage had told him Brexit had been similarly rigged
August 8: Stone tells Broward Republicans he has communicated with Assange, expects next tranche to pertain to Clinton Foundation
August 10: Manafort tells his tax preparer that he would get $2.4 million in earned income collectable from work in Ukraine in November
August 10: Stone asserts that Hillary’s deleted emails will be coming out
Early August: Manafort gets blackmail threat pertaining to secret ledgers
August 12: Guccifer 2.0 publicly tweets Stone
August 13: Stone claims to have been hacked
August 14: NYT publishes story on secret ledgers
August 14: Stone DMs Guccifer 2.0
August 14: Corsi claims to have started research on response to NYT story
August 14: Breitbart piece suggesting NYT was ignoring Hillary’s own ties to Russia; this may be Stone’s latest explanation for interest in Podesta on that date
August 15: Manafort and Gates lie to the AP about their undisclosed lobbying, locking in claims they would make under oath later that fall
August 15: In first tweet mentioning John Podesta, Stone claims John Podesta “makes Paul Manafort look like St. Thomas Aquinas”
August 15: Corsi reports Stone’s prediction that WikiLeaks will release deleted Hillary emails (also reports on claimed hack)
August 17: AP publishes story on Manafort’s unreported Ukraine lobbying, describing Podesta Group’s role at length
August 17: Trump adds Steve Bannon and Kellyanne Conaway to campaign leadership team (Manafort’s daughter claims he hired them)
August 19: Manafort resigns from campaign
August 21: Stone tweets it will soon be Podesta’s time on the barrel
August 26: Rebekka Mercer asks Alexander Nix whether Cambridge Analytica or GAI could better organize the leaked Hillary emails
September 12: Following further reporting in the Kyiv Post, Konstantin Kilimnik contacts Alex Van der Zwaan in attempt to hide money laundering to Skadden Arps
September 28: Corsi post (later linked on Twitter by Stone) noting that Podesta Group also under investigation
October 6: Corsi repeats the Joule/GAI claims
October 11: Release of Podesta email allegedly backing Joule story (December 31, 2013 resignation letter, January 7, 2014 severance letters)
October 11: Foldering email among Peter Smith operatives that may included coded satisfaction with emails released thus far
October 12: Roger Stone interview with the Daily Caller responding to Podesta’s allegations he knew of release in advance, which makes no mention of Joule attack
October 13: In response to accusations he knew of Podesta emails in advance, Stone repeats Joule story falsely claiming this WikiLeaks email, released October 11, substantiates it; Corsi also posts a story on Joule, like Stone not linking to the underlying WikiLeaks emails
October 17: Corsi post that actually links the WikiLeaks releases relied on in his and Stone’s October 13 posts
October 30: Additional Joule letter (including actual transfer signatures) released
October 31: Additional Joule letter released
November 1: Additional Joule letter released
As I disclosed in July, I provided information to the FBI on issues related to the Mueller investigation, so I’m going to include disclosure statements on Mueller investigation posts from here on out. I will include the disclosure whether or not the stuff I shared with the FBI pertains to the subject of the post.