Susie’s Assessment: Failure after Failure
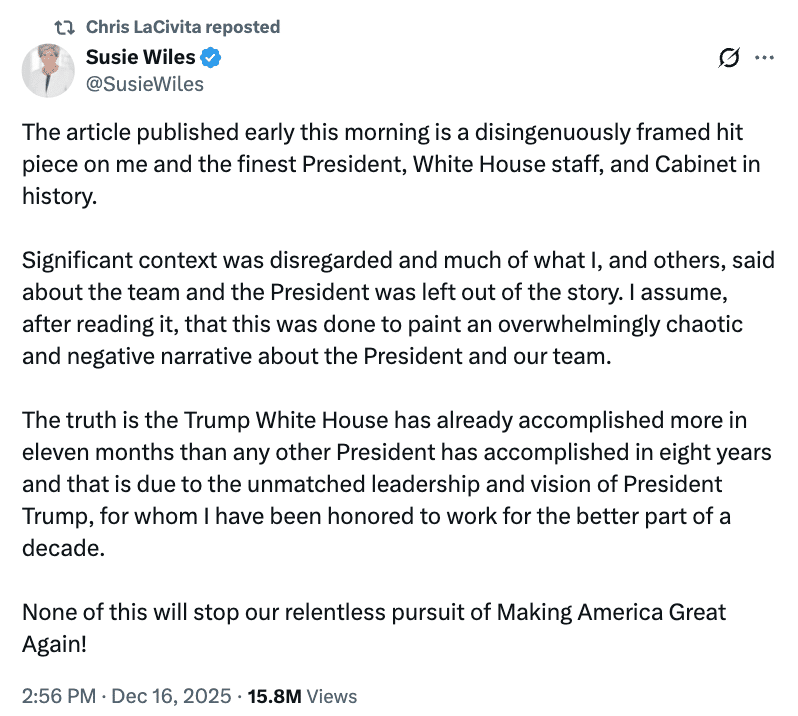
/39 Comments/in 2024 Presidential Election, 2026 Mid-Term Election, emptywheel, Epstein, January 6 Insurrection, Jim Comey prosecution, Letitia James Investigation, Russo-Ukrainian War, Trump 2.0, Weaponized DOJ /by emptywheelThe right wing response to the Vanity Fair profile of Susie Wiles (one, two) reveals a lot about the structure of Trump’s power.
While there’s nothing surprising in the profile, Chris Whipple caught Wiles admitting to failures those of outside the White House bubble all recognize, or making laughably false claims to cover them up. And while mostly the response to the profile has been a typical beltway feeding frenzy, much of the focus has been on those expressions of truth or false claims, including how some of them — Wiles’ claims that Trump was targeting Letitia James, her confession that Trump is seeking regime change in Venezuela, Trump’s awareness that Putin wants all of Ukraine — could have lasting legal and political repercussions.
Not so the right wing, though. Theirs has been a two-fold response: first, declaring not that the profile got anything wrong, much less made up any of the abundant direct quotes, but instead that they remain loyal to Susie Wiles. After everyone had performed their expression of loyalty, the right wing turned to complaining that photographer Christopher Anderson captured Trump’s aides’ ugliness and warts.
Behind those expressions of loyalty and vanity complaints, however, the profile includes a string of confessions that Trump, that Susie Wiles, that they all have failed.
Circling the motherfucking wagons
The immediate response was a performance of loyalty. First Wiles claimed in a (for her) very rare tweet that the profile had taken things out of context and ignored positive things she said. Then one after another Trump loyalist RTed that tweet and testified to how great she is and how loyal they are to her or she is to Trump.
The loyalty oaths were particularly amusing to watch through Chris LaCivita’s eyes. First he RTed Wiles’ tweet.
Then he tried to distract with yesterday’s scandal.
Then he posted one…
After another declaration of loyalty to Wiles. This Don Jr tweet — “When others cowered, she stood strong” is quite long and amusing in the original.
Scott Bessent’s claim of inaccuracy is especially notable given how Wiles described half of Trump’s advisors to be opposed to Trump’s tariffs (as I’ll show below).
LaCivita thought dumb boomerang memes would be persuasive.
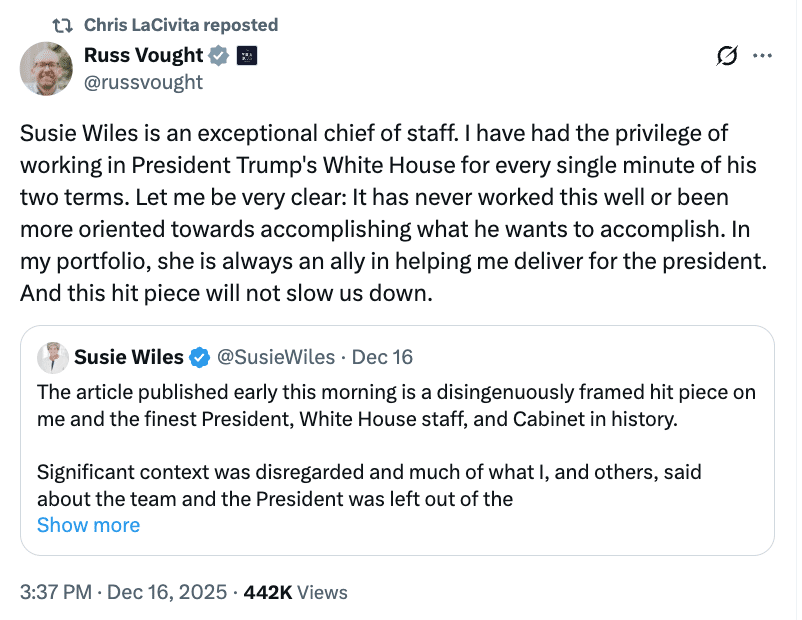
More celebration of blind loyalty.
Failures hailing her role in their failure.
All leading up to this tweet, from the lady who used to pretend to be objective but now works with the former Trump spox who tried to hide behind the shrubbery, once.
Rachael Bade really did claim it was a big scoop to describe a “Wiles loyalist and Trump ally” explaining what was visible on Xitter for all to see as “circling the motherfucking wagons.”
Sure. It’s clear that’s what you were doing. But honestly, a good many people who read the profiles weren’t seeking to split the White House, they were seeking to understand what Trump’s low-key Chief of Staff does or thinks.
The loyalty that prevents you from seeing the failures she confessed doesn’t prevent us from seeing them.
Karoline Leavitt’s nasty gender-affirming care
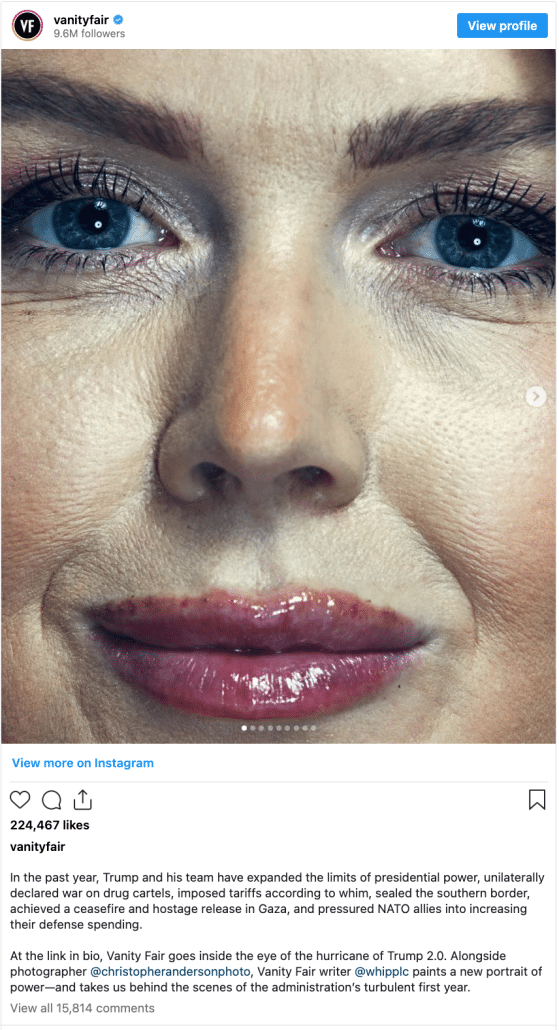
Then people started complaining about the photography, particular a picture that revealed the slop on Karoline Leavitt’s face and the injection marks in her lips.
WaPo did a great interview with the photographer, Christopher Anderson, where he explained his view of photojournalism and truth.
I want to talk to you about the portraits that you did for Vanity Fair. As I assume you have heard, they’ve caused a bit of a splash on social media. Can you tell me how you conceived of them?
I conceived of it many years ago. I did a whole book of American politics called “Stump” (2014), where I did all close-ups. It was my attempt to circumnavigate the stage-managed image of politics and cut through the image that the public relations team wants to be presented, and get at something that feels more revealing about the theater of politics. It’s something I’ve been doing for a long time. I have done it to all sides of the political spectrum, not just Republicans. It’s part of how I think about portraiture in a lot of ways: close, intimate, revealing.
[snip]
The images are really arresting. What is your response to people who say that these images are unfair? There’s been a lot of attention about Karoline Leavitt’s lips and [what appear to be] injection sites.
I didn’t put the injection sites on her. People seem to be shocked that I didn’t use Photoshop to retouch out blemishes and her injection marks. I find it shocking that someone would expect me to retouch out those things.
[snip]
Were they coming camera-ready, or was there a hair-and-makeup team?
Most of them came camera-ready or with their own hair-and-makeup team. Karoline Leavitt has her own personal groomer that was there.
I mean, we don’t know if Karoline Leavitt still has that groomer today now that the photos are published.
Well, what can I say? That’s the makeup that she puts on, those are the injections she gave herself. If they show up in a photo, what do you want me to say? I don’t know if it says something about the world we live in, the age of Photoshop, the age of AI filters on your Instagram, but the fact that the internet is freaking out because they’re seeing real photos and not retouched ones says something to me.
Click through for the great quote about Stephen Miller’s plea for kindness.
The self-deceptions and truths from within the bubble
But none of this pushback — none of it — claims that lifelong chronicler of Chiefs of Staff Chris Whipple ever made up a quote.
Accordingly, that means no one has disputed Wiles’ admission that Trump’s policies have largely failed.
Here’s how Whipple summarized Trump’s term so far, close to the beginning of part one:
It’s been a busy year. Trump and his team have expanded the limits of presidential power, unilaterally declared war on drug cartels, imposed tariffs according to whim, sealed the southern border, achieved a ceasefire and hostage release in Gaza, and pressured NATO allies into increasing their defense spending.
At the same time, Trump has waged war on his political enemies; pardoned the January 6 rioters, firing nearly everyone involved in their investigation and prosecution; sued media companies into multimillion-dollar settlements; indicted multiple government officials he perceives as his foes; and pressured universities to toe his line. He’s redefined the way presidents behave—verbally abusing women, minorities, and almost anyone who offends him. Charlie Kirk’s assassination in September turbocharged Trump’s campaign of revenge and retribution. Critics have compared this moment to a Reichstag fire, a modern version of Hitler’s exploitation of the torching of Berlin’s parliament.
How he tells this story — though Wiles’ own assessments of Trump’s success or failure — is more interesting. The following, save the last one, are presented in the order Whipple addresses them in the profile.
End the congressional filibuster and remove Nicolás Maduro from power. [A November portrayal; results still TBD]
The agenda was twofold: ending the congressional filibuster and forcing Venezuelan president Nicolás Maduro from power.
Pardon just those who were January 6 “happenstancers.” [Wiles lies to cover up her failure to achieve this goal]
Wiles explained: “In every case, of the ones he was looking at, in every case, they had already served more time than the sentencing guidelines would have suggested. So given that, I sort of got on board.” (According to court records, many of the January 6 rioters pardoned by Trump had received sentences that were lighter than the guidelines.) “There have been a couple of times where I’ve been outvoted,” Wiles said. “And if there’s a tie, he wins.”
Preserve parts of USAID. [Complete failure, but one Marco Rubio is lying about]
Musk forged ahead—all throttle, no brake. “Elon’s attitude is you have to get it done fast. If you’re an incrementalist, you just won’t get your rocket to the moon,” Wiles said. “And so with that attitude, you’re going to break some china. But no rational person could think the USAID process was a good one. Nobody.”
[snip]
Did Rubio have any regrets about the untold number of lives that PEPFAR’s evisceration might cost? “No. First of all, whoever says that, it’s just not being accurate,” he told me. “We are not eviscerating PEPFAR.
Stephen Miller’s deportation policies. [In Wiles’ estimation, a failure]
Not long after the El Salvador deportation fiasco, in Louisiana, ICE agents arrested and deported two mothers, along with their children, ages seven, four, and two, to Honduras. The children were US citizens and the four-year-old was being treated for stage 4 cancer. Wiles couldn’t explain it.
“It could be an overzealous Border Patrol agent, I don’t know,” she said of the case, in which both mothers had reportedly been arrested after voluntarily attending routine immigration meetings. “I can’t understand how you make that mistake, but somebody did.”
Tariffs. [Wiles failed to prevent Trump’s worst instincts and the results have been worse than she imagined]
Wiles believed a middle ground on tariffs would ultimately succeed, she said, “but it’s been more painful than I expected.”
Invading blue cities. [Wiles says Trump won’t do this to stay in power]
Will the president use the military to suppress or even prevent voting during the midterms and beyond?
“I say it is categorically false, will not happen, it’s just wrongheaded,” she snapped.
November’s election. [Wiles knew they were in trouble, but even so was overoptimistic]
Wiles thought the GOP had a chance of electing the governor in New Jersey, but she knew they were in for a tough night.
The Epstein files. [Trump and Kash, both lying about what was in the files but that’s okay because MAGAts aren’t obsessed with Epstein]
For years, Kash has been saying, ‘Got to release the files, got to release the files.’ And he’s been saying that with a view of what he thought was in these files that turns out not to be right.”
[snip]
Wiles said. “It’s the Joe Rogan listeners. It’s the people that are sort of new to our world. It’s not the MAGA base.”
Murderboats and frivolous wars. [Pure self-deception]
“Not that he wanted to kill people necessarily, but stopping the killing wasn’t his first thought. It’s his first and last thought now.”
[snip]
“He wants to keep on blowing boats up until Maduro cries uncle. And people way smarter than me on that say that he will.”
Russian peace efforts. [Wiles says they’re lying about Russia wanting peace]
Trump’s team was divided on whether Putin’s goal was anything less than a complete Russian takeover of Ukraine. “The experts think that if he could get the rest of Donetsk, then he would be happy,” Wiles told me in August. But privately, Trump wasn’t buying it—he didn’t believe Putin wanted peace. “Donald Trump thinks he wants the whole country,” Wiles told me.
In October I asked Rubio if that was true. “There are offers on the table right now to basically stop this war at its current lines of contact, okay?” he said. “Which include substantial parts of Ukrainian territory, including Crimea, which they’ve controlled since 2014. And the Russians continue to turn it down. And so…you do start to wonder, well, maybe what this guy wants is the entire country.” (In Wiles’s office is a photograph of Trump and Putin standing together, signed by Trump: “TO SUSIE YOU ARE THE GREATEST! DONALD.”)
Trump would only spend 90 days on retribution. [Wiles is in denial]
“Yes, I do,” she’d replied. “We have a loose agreement that the score settling will end before the first 90 days are over.”
In late August, I asked Wiles: “Remember when you said to me months ago that Trump promised to end the revenge and retribution tour after 90 days?”
“I don’t think he’s on a retribution tour,” she said.
Trump’s biggest accomplishments: Peace and the Big Ugly
“I think the country is beginning to see that he’s proud to be an agent of peace. I think that surprises people. Doesn’t surprise me, but it doesn’t fit with the Donald Trump people think they know. I think this legislation [the so-called One Big Beautiful Bill], which funded the entire domestic agenda, is a huge accomplishment. And even though it isn’t popular in total, the component parts of it are. And that will be a very big deal in the midterms.”
That is, like the Epstein scandal more generally, Wiles either invents bubble-wrapped fictions about Trump’s own success, or concedes she, or Trump, has failed.
But Trump’s aides — the people complicit in this failure — don’t care.
They’re just going to circle the motherfucking wagons and demand loyalty.
Other Nations are Updating their Threat Assessments, Too
/7 Comments/in Foreign Policy, Intelligence, Trump 2.0, Trump Administration /by PeterrIt’s not just the US updating its national threat assessments, in public and in private.
Denmark’s military intelligence service raised concerns for the first time about the United States in its annual threat assessment, saying in a report released Wednesday that shifts in American policy are generating new uncertainties for Denmark’s security.
The report points to the United States’ use of tariffs against allies and its intensified activity in the Arctic, and raises many of the same concerns that European leaders have voiced about the direction of President Trump’s America-first foreign policy.
“The United States uses economic power, including threats of high tariffs, to enforce its will, and no longer rules out the use of military force, even against allies,” the report said.
More from the Danish news site Politiken (Firefox translation):
Particularly one specific sentence stands out in the annual threat assessment, where the Danish Defence Intelligence Service (FE) lists external threats and security policy challenges for Denmark.
And notably, it is not about Russia or China. For the first time, the intelligence service in the report titled ’Udsyn 2025’ also focuses on the United States under Donald Trump’s leadership.
»The US is now using its economic and technological strength as a means of power, even against allies and partners«, the main conclusion states.
In an interview with Politiken, the head of FE cites examples such as the threats and imposition of tariffs, the belligerence over Greenland (including US-Greenland talks that exclude Denmark), and attempting to make Denmark (and others) dependent on US technologies.
But with Donald Trump’s statements about wanting to take over Greenland, are you as a service then forced to be interested in the U.S.’s actions in the same way as you do with Russia and China?
»The U.S. has for many years been and remains our most important ally when it comes to our security. So we work closely with the U.S. and with the American services in several areas. That is no secret. It is also clear that we are concerned with how the U.S. acts and also have dialogue with the U.S. regarding American interests«.
But doesn’t it almost go without saying that if someone wants to take over part of Denmark’s territory, it is your job to keep track of it?
»There is no doubt that it interests us and falls within our task. What instruments we use, we do not comment on«.
Is the U.S. our friend or enemy?
»I think that is a political question. We do not focus on friends and enemies; our task is to look at what security policy challenges and threats Denmark faces«.
Not a friend.
Not an enemy.
Someone who presents security challenges and threats.
Politiken goes on:
According to Professor of International Politics Ole Wæver from the University of Copenhagen, it is remarkable that FE »finally« suggests that the U.S. and Europe are no longer two sides of the same coin. For Denmark, he describes it as a »painful divorce« because, compared to many other European countries, we have been »hyper-Atlantic«.
»One thing is that we cannot take for granted that the U.S. is our eternal, reliable ally when we need to counter a threat from Russia and China. The next is how to relate to the fact that the U.S. itself can be a threat. Not least in Greenland. If the service really delved into that question, they would need to write an entire chapter about it in Udsyn«, he says.
Those are not exactly the words any US ambassador or US Secretary of State wants to hear said about the US. The US poses challenges and threats like an ex-spouse, rather than being an eternal, reliable ally? Ouch.
[Let us pause to remember that Trump is the ex-spouse of not one, but two women. Post-Stormy Daniels, we can only speculate on the status of his relationship with wife #3. One can only imagine how much money it has cost Trump to minimize the challenges and threats posed by ex-spouses. But I digress.]
How close was this relationship before? It wasn’t that long ago that the NSA and the FE cooperated in tapping the phones of European leaders like Angela Merkel, and now it’s come to this.
Trump has taken the US relationship with the rest of the world from being the “Leader of the Free World” to “America First” to “America Against the World.” Lovely.
Perhaps Trump might understand this if I put it another way: We’re talking about the Ryder Cup, with Nukes. (And Trump will recall how the Ryder Cup without nukes turned out.)
Yet More of a Lapsed Catholic’s Bible Study
/47 Comments/in Congress, Culture, Trump 2.0 /by Rayne[NB: check the byline, thanks. /~Rayne]
I mentioned in comments beneath my first Lapsed Catholic’s Bible Study post that I had other biblical material I was chewing on.
Funny enough, the chapter and verses I was referring to are absolutely appropriate to the Trump administration’s ethical and moral failures as well as that of the GOP’s congressional caucus.
It’s one of the most popular portions of the Bible. It may be familiar to you even if you’re not a church-going Christian as you may have heard as a reading at Christian weddings. It’s frequently used as an exhortation to the newlyweds and their future lives together.
1 Corinthians 13:1-13
13 If I speak in the tongues of men and of angels, but have not love, I am a noisy gong or a clanging cymbal.
2 And if I have prophetic powers, and understand all mysteries and all knowledge, and if I have all faith, so as to remove mountains, but have not love, I am nothing.
3 If I give away all I have, and if I deliver up my body to be burned, but have not love, I gain nothing.
4 Love is patient and kind; love does not envy or boast; it is not arrogant
5 or rude. It does not insist on its own way; it is not irritable or resentful;
6 it does not rejoice at wrongdoing, but rejoices with the truth.
7 Love bears all things, believes all things, hopes all things, endures all things.
8 Love never ends. As for prophecies, they will pass away; as for tongues, they will cease; as for knowledge, it will pass away.
9 For we know in part and we prophesy in part,
10 but when the perfect comes, the partial will pass away.
11 When I was a child, I spoke like a child, I thought like a child, I reasoned like a child. When I became a man, I gave up childish ways.
12 For now we see in a mirror dimly, but then face to face. Now I know in part; then I shall know fully, even as I have been fully known.
13 So now faith, hope, and love abide, these three; but the greatest of these is love.
Nice, huh? You can imagine the newlyweds before the altar, glowing with happiness, feeling all the wonderful attributes of love described in these verses.
Except that’s not what appears in every Bible published. In the King James version, this is 1 Corinthians 13:1-13 —
13 Though I speak with the tongues of men and of angels, and have not charity, I am become as sounding brass, or a tinkling cymbal.
2 And though I have the gift of prophecy, and understand all mysteries, and all knowledge; and though I have all faith, so that I could remove mountains, and have not charity, I am nothing.
3 And though I bestow all my goods to feed the poor, and though I give my body to be burned, and have not charity, it profiteth me nothing.
4 Charity suffereth long, and is kind; charity envieth not; charity vaunteth not itself, is not puffed up,
5 Doth not behave itself unseemly, seeketh not her own, is not easily provoked, thinketh no evil;
6 Rejoiceth not in iniquity, but rejoiceth in the truth;
7 Beareth all things, believeth all things, hopeth all things, endureth all things.
8 Charity never faileth: but whether there be prophecies, they shall fail; whether there be tongues, they shall cease; whether there be knowledge, it shall vanish away.
9 For we know in part, and we prophesy in part.
10 But when that which is perfect is come, then that which is in part shall be done away.
11 When I was a child, I spake as a child, I understood as a child, I thought as a child: but when I became a man, I put away childish things.
12 For now we see through a glass, darkly; but then face to face: now I know in part; but then shall I know even as also I am known.
13 And now abideth faith, hope, charity, these three; but the greatest of these is charity.
I don’t ever recall this selection being read at Christian weddings, do you?
But even this version in which the word charity is used to describe the greatest of three virtues still doesn’t fully convey the intended meaning.
The English words love and charity are rough approximations of a Greek word ἀγάπη, agape — the love of humanity. Agape is both love and charity; it is the emotion of love combined with action of charity, felt for and offered to fellow humans who are God’s creations.
Trump and his minions, particularly Russell Vought, wanted to reshape the U.S. by way of Project 2025:
An influential think tank close to Donald Trump is developing plans to infuse Christian nationalist ideas in his administration should the former president return to power, according to documents obtained by POLITICO.
…
Christian nationalists in America believe that the country was founded as a Christian nation and that Christian values should be prioritized throughout government and public life. As the country has become less religious and more diverse, Vought has embraced the idea that Christians are under assault and has spoken of policies he might pursue in response.
One document drafted by CRA staff and fellows includes a list of top priorities for CRA in a second Trump term. “Christian nationalism” is one of the bullet points. Others include invoking the Insurrection Act on Day One to quash protests and refusing to spend authorized congressional funds on unwanted projects, a practice banned by lawmakers in the Nixon era.
Emphasis mine. Source: Trump allies prepare to infuse ‘Christian nationalism’ in second administration, Politico, Feb 20, 2024.
By actively choosing to starve or bankrupt Americans by refusing to extend healthcare subsidies and fully fund SNAP, thereby endangering human lives, Trump and his administration are doing the furthest thing from establishing a Christian nation. They are not acting with charity, and in this sense the demonstration of agape. They are treating persons who are marginalized by circumstances with more than disrespect but malignant disregard.
It is yet another mortal sin, on top of other mortal sins committed by knowingly seeking individuals to murder in the Gulf of Mexico and the Pacific Ocean, by turning over individuals for abuse and torture abroad as part of deportations, by encouraging cruel and unusual punishments in painful forms of execution of inviduals on death row. I’m sure there are more examples in this profile of Chicago under occupation by Trump’s ICE.
Being the lapsed Catholic that I am, I don’t ordinarily ask this kind of question, however I feel I need to ask as Trump and his Christian nationalist purveyors clearly haven’t asked either. What would Jesus do if confronted with this level of hate for fellow humans? What would Christ say about consciously choosing to deny food and healthcare to those most in need, including persons who are needy because they serve now or have served in the military? This level of hate for fellow humans is creating a national security threat; we can’t expect strong defense of our nation from people who haven’t eaten, or who are worried about feeding their family.
Ed Walker examined Trumpist Moral Choice in his most recent post as part of his excellent series on Simone de Beauvoir’s The Ethics of Ambiguity. I’m beyond the eeny-meeny-miney-moe of moral choice; our fellow Americans’ urgent needs call for more than mental exercise by the Trumpists who appear unable to consider consequences in advance of decisions.
Nor are platitudes enough; they don’t pay healthcare premiums and medical bills, make the rent, or put food on the table.
We need deeds not words. Genuine, immediate demonstrations of agape, the greatest of Christian virtues.
Little children, let us not love in word or talk but in deed and in truth.
— 1 John 3:18
A Lapsed Catholic’s Sunday Bible Study
/55 Comments/in Culture, Trump 2.0 /by Rayne[NB: check the byline, thanks. /~Rayne]
Hello, I’m Rayne, and I’m a lapsed Catholic. I fell away from the Church over a period of time, beginning roughly with the Reagan years and the uptick in Christian fundamentalism’s influence on politics.
It didn’t happen all at once but I finally had enough when the Church became little more than a crypto-fascist mouthpiece for right-wing ideology, focusing almost exclusively on anti-abortion efforts instead of what I was taught were Christ’s teachings.
And yet more than 10 years of Catholic catechism shaped my values and morals, underpinning my Democratic identity. In hindsight I don’t think I left the Church so much as it left me.
Perhaps I should have nailed a thesis to the the Church’s doors in protest but when the entire Church has been subsumed by a political movement, it didn’t occur to me as an effective option.
Now we may need to figuratively nail a thesis on fellow American Christian citizens who’ve lost their way. They have forgotten altogether what Christ taught while forcing on us their corrupt vision of a white Christian nation.
If a nation is truly Christian, it’s not identified as white; the supremacy of whiteness is not what Christ taught. It’s certainly not what I was taught.
From Matthew 22:35-39, the New Testament, King James Version:
35 Then one of them, which was a lawyer, asked him a question, tempting him, and saying,
36 Master, which is the great commandment in the law?
37 Jesus said unto him, Thou shalt love the Lord thy God with all thy heart, and with all thy soul, and with all thy mind.
38 This is the first and great commandment.
39 And the second is like unto it, Thou shalt love thy neighbour as thyself.
During catechism, instructors elaborated on how we must love ourselves as we are the Creator’s handiwork; to love God as commanded means loving His works as well.
And loving His works meant to love our fellow humans because they too, were God’s handiworks.
You can see where I’m going, of course. What the Trump administration does is a rejection of what I’ve understood to be God’s commandments.
Not just the top two commandments, but so many other teachings from both the Old and New Testament representing the core of Christianity:
Old Testament
Exodus 12:49
The same law applies both to the native-born and to the foreigner residing among you.Exodus 22:21
You shall not wrong a stranger or oppress him, for you were strangers in the land of Egypt.Exodus 23:9
Do not oppress a foreigner; you yourselves know how it feels to be foreigners, because you were foreigners in Egypt.Leviticus 23:22
When you reap the harvest of your land, do not reap to the very edges of your field or gather the gleanings of your harvest. Leave them for the poor and for the foreigner residing among you. I am the LORD your God.Leviticus 24:22
You are to have the same law for the foreigner and the native-born. I am the LORD your God.Leviticus 25:35
Now in case a countryman of yours becomes poor and his means with regard to you falter, then you are to sustain him, like a stranger or a sojourner, that he may live with you.Deuteronomy 10:18
He defends the cause of the fatherless and the widow, and loves the foreigner residing among you, giving them food and clothing.Deuteronomy 10:19
And you are to love those who are foreigners, for you yourselves were foreigners in Egypt.Deuteronomy 15:7-11
“If there is a poor man with you, one of your brothers, in any of your towns in your land which the Lord your God is giving you, you shall not harden your heart, nor close your hand from your poor brother;Deuteronomy 24:14
Do not take advantage of a hired worker who is poor and needy, whether that worker is a fellow Israelite or a foreigner residing in one of your towns.Deuteronomy 27:19
Cursed is anyone who withholds justice from the foreigner, the fatherless or the widow. Then all the people shall say, “Amen!”Zechariah 7:10
and do not oppress the widow or the orphan, the stranger or the poor; and do not devise evil in your hearts against one another.New Testament
Matthew 25:35-46
For I was hungry, and you gave Me something to eat; I was thirsty, and you gave Me something to drink; I was a stranger, and you invited Me in; naked, and you clothed Me; I was sick, and you visited Me; I was in prison, and you came to Me.’ Then the righteous will answer Him, ‘Lord, when did we see You hungry, and feed You, or thirsty, and give You something to drink?3 John 1:5
Beloved, you are acting faithfully in whatever you accomplish for the brethren, and especially when they are strangers;James 1:27
Religion that God our Father accepts as pure and faultless is this: to look after orphans and widows in their distress and to keep oneself from being polluted by the world.Galatians 3:28
There is neither Jew nor Gentile, neither slave nor free, nor is there male and female, for you are all one in Christ Jesus.Hebrews 13:2
Do not neglect to show hospitality to strangers, for by this some have entertained angels without knowing it.
I don’t know how any Christian can have learned these tenets and not objected strenuously to Trump’s anti-immigrant policies and the funding of ICE as his personal anti-immigration militia.
Immigrants are strangers, travelers from foreign lands, asylum seekers looking for aid and justice. Christians haven’t been told to segregate the legal from illegal when it comes to treatment of immigrants; they have been told repeatedly to treat immigrants with kindness and generousity because all humans are ultimately the descendents of immigrants.
I thought of that last verse from Hebrews in particular after learning ICE shot a pastor in the face at the ICE detention facility in Broadview, IL.
I thought of Hebrews 13:2 again when ICE turned away interfaith clerics who came to administer communion to the faithful in detention two weeks ago.
And ICE has been harassing Catholic faithful by menacing them outside Chicago-area churches.
It doesn’t matter if Christian clerics representing the faith have appeared to protest ICE’s abuses and Trump’s immigration policies, let alone administer to the faithful. How much closer to an obvious an angel does one have to be for Trump and ICE to halt the perversion of Christ’s teachings these so-called white Christian nationalists are forcing on fellow humans?
It’s obvious Trump would have no compunction about shooting an angel in the face on Fifth Avenue given his administration’s policies and actions.
Even a lapsed Catholic like me finds the Trump adminstration’s behaviors decidedly un-Christian. It makes me think of yet another lesson I learned during catechism:
James 2:14-26
What good is it, my brothers, if someone says he has faith but does not have works? Can that faith save him? If a brother or sister is poorly clothed and lacking in daily food, and one of you says to them, “Go in peace, be warmed and filled,” without giving them the things needed for the body, what good is that? So also faith by itself, if it does not have works, is dead. But someone will say, “You have faith and I have works.” Show me your faith apart from your works, and I will show you my faith by my works. …
Deeds not words. Attacking immigrants is far from demonstrating Christian faith.
Trump’s GOP Death Panel in Progress
/52 Comments/in 2026 Mid-Term Election, Congress, Health Policy, Republicans, Trump 2.0 /by Rayne[NB: check the byline, thanks. /~Rayne]
There’s been an uptick this week in reporting on the role of health care subsidies in congressional budget negotiations.
Most Americans worry about health care costs: AP-NORC poll
By ALI SWENSON and LINLEY SANDERS | Updated 1:22 PM EDT, October 21, 2025
https://apnews.com/article/poll-shutdown-health-care-insurance-costs-trump-f0282a0f5bedf3f01172ed3fa0ba4fd2
Health insurance sticker shock begins as shutdown battle over subsidies rages
Many states have shown rising premiums ahead of open enrollment for Affordable Care Act plans. Congress is deadlocked over extending covid-era subsidies that bring costs down.
By Paige Winfield Cunningham | October 22, 2025 at 6:00 a.m. EDT
https://www.washingtonpost.com/health/2025/10/22/obamacare-aca-enrollment-price-increases/
Some Americans fear high health insurance premiums if ACA enhanced subsidies expire: ‘Very much a worry’
ACA enhanced premium tax credits are set to expire at the end of the year.
ByMary Kekatos | October 21, 2025, 10:51 AM
https://abcnews.go.com/Health/americans-fear-high-premiums-aca-enhanced-subsidies-expire/story?id=126613026
News media are finally telling us what many of us have already known: Trump’s GOP congressional caucus wants to kill Americans.
There are some GOP moderates who are pressing for some, well, moderation on health care subsidies because their constituents need the assistance.
Republican moderates press leadership on health credit extension
Millions of Americans in red states rely on subsidies to keep insurance costs down
By Sandhya Raman and Jessie Hellmann | October 22, 2025 at 12:36pm
https://rollcall.com/2025/10/22/republican-moderates-press-leadership-on-health-credit-extension/
And these moderates need their seats. Check the last graf of that RollCall article — it’s a who’s who of GOP seats in districts that are flippable.
In other words, the state of health care subsidies may mean control of the House.
Trump refuses to negotiate unless the government shutdown ends, but that means giving up the only leverage Democrats have since the moderate GOP reps have been unable to persuade Trump and the rest of the GOP House caucus to budge.
Meanwhile, reality is doing a number on Americans who rely on health care subsidies, including small business owners:
These kinds of rate increases mean households will be making choices between going without health care insurance or going without paying mortgages, skipping car payments, not making the rent, cutting back on groceries they haven’t already cut because of inflation.
Do the math:
— Median weekly earnings for wage and salary workers = $1196 / week
— Average rent for a one-bedroom apartment in the U.S. = $1631 / month
— “The USDA estimates $297–558 for a monthly food budget for one person, $614–963 for a couple, and $996–1,603 for a family of four.” (This number was reported in May 2025 and has surely risen since the underlying source report.)
— Average transportation cost per U.S. household = $819 / month
That’s just the basics and doesn’t include out-of-pocket health care expenses, or any other necessities like clothing. It’s extremely grim for minimum wage workers, and for those whose work fluctuates like freelance writers or seasonal contractors.
There’s almost nothing left or worse after rent and/or health care, and it will be worse in rural areas.
Imagine having to choose between feeding your kids and getting any necessary medication including insulin. Imagine trying to pay for prenatal care let alone delivery of a healthy child, and making the rent. Heaven help you if either you or the child suffer complications before/during/after birth.
For many of us this isn’t a thought experiment. It’s a painful reality. Some of us will have to work even longer to pay for health care, well beyond age 65; some of us are already dealing with this challenge, as Business Insider reports in these slice-of-life stories that tend to blame the victim (ex. Faber shouldn’t have been a farmer).
I’m 82 and earn $16 an hour working at a boat store. I don’t have much saved and can’t retire, but everything will work out.
https://www.businessinsider.com/cant-retire-working-at-80-social-security-minimum-wage-2025-10
A trucker in his late 70s who can’t afford to retire shares the big regret he made decades ago that may have changed his circumstances
https://www.msn.com/en-us/money/retirement/a-trucker-in-his-late-70s-who-can-t-afford-to-retire-shares-the-big-regret-he-made-decades-ago-that-may-have-changed-his-circumstances/ar-AA1HKHOP
These folks couldn’t save enough for retirement when health care costs were much lower. Today’s younger workers aren’t able to save much at all, not with inflation chipping away at all their expenses. We’ll be reading bleak stories of elderly who can’t retire for decades.
In essence, Trump and his GOP minions’ death panel have become Dickensian: “If they would rather die, …they had better do it, and decrease the surplus population.”
One might think this is the Trump-GOP’s approach to housing policy; if enough people go bankrupt, into foreclosure, or die, there will be more housing available.
It’s as destructive and thoughtless as taking a wrecking ball without a plan to the East Wing of the White House.
Investigate POTUS’ Health Cover-Up
/92 Comments/in Congress, Republicans, Trump 2.0 /by Rayne[NB: check the byline, thanks. /~Rayne]
Congress needs to investigate the cover-up of the president’s health.
No, not Biden’s health, which has become an excuse for avoiding the obvious problems with Trump’s health.
Biden’s no longer the president. He’s no longer making decisions affecting the nation’s security.
This guy, though, is:
Link to original post including the video.
This kind of confabulation is familiar to me, having a parent with dementia. They fake reality to fill in gaps in what they actually recall, and as long as they’re not called out on it they continue to roll with it. They may even believe their fabrication because they can draw on nothing that undermines it.
Depending on the time of day and who corrects them, they may back off or they may become petulant and act out if they are sundowning.
Nobody confronts him. They just let him spew that garbage and replay it to the public without context to call it into question, cementing it as alternative reality.
This is dangerous as fuck, a threat to national security.
The video in the post above was recorded August 26 in a close cabinet meeting. The meeting was held during a period when Trump wasn’t seen by the public, between August 24 and September 2, sparking questions across social media platforms asking if Trump was dead.
Photos taken of him on August 30 preparing to get into a vehicle did not assure the public of his health. He looked pale, pasty, and not very energetic.
Trump’s slack jaw open mouth appearance in several photos that day caused many to ask if he’d had a stroke.
Yesterday there was more evidence yet that Trump may have had a recent neurological event. Lauren Esposito at The Daily Beast offered several perspectives in her report:
President Donald Trump was sporting a doozy of a droopy face as he ventured outside the White House Thursday amid mounting questions about his health.
The 79-year-old president appeared at a Pentagon event commemorating the 24th anniversary of the 9/11 terror attacks, where the right side of his face sparked a wave of online speculation.
Matt Binder of Substack newsletter Disruptionist asked if this may be an AI avatar of Trump:
Link to original tweet on Xitter including video clips.
It’s not just the glitch Binder noted which is concerning; Trump’s right hand is covered by his left. It could be an attempt to hide the bruising frequently noted on his hand, or it could be an effort to hide both a spasm like dystonia or tardive dyskenia, or a decreasing ability to freely using his right hand and fingers. Whatever it is looks awkward and unnatural because Trump talks with his hands.
How would the average American know whether they’re looking at a sick man faking it through his duties, or an artificial construct created to replace him, operated by unelected handlers?
Some have speculated Trump has had Bell’s palsy which frequently manifests as paralysis of one side of the face – but not paralysis or weakening of one half of the body. There’s been no deeper speculation about the underlying cause of the palsy.
Has Trump one or more major neurological events which could affect his ability to fulfill his duties as president?
Has he already subordinated his duties to others around him — outside of the Constitution’s 25th Amendment — including whomever may have made an AI avatar of him used yesterday?
Why aren’t any of the White House staff speaking with media to address Trump’s obvious health problems, instead of covering it up by ignoring it?
When is Congress going to investigate this immediate concern rather than wasting time on a political witch hunt focusing on a former president?
And when is the GOP caucus in Congress going to grasp the reality they are under the thumb of a guy who’s health is clearly compromised? What happens to the GOP both in Congress and the party machine if Trump becomes further debilitated?
~ ~ ~
There is one more huge problem Congress won’t address, regardless of the party helming either house.
That’s the failure of U.S. media outlets. It’s clear based on the complete lack of coverage of Trump’s health that the largest and most influential newspapers conducted a partisan hit job on Joe Biden during his last year in office.
There has been little coverage of Trump’s disappearance for four days by The New York Times, the Washington Post, or the Los Angeles Times.
There has been limited coverage of Trump’s obvious hand bruises and his edema, but not a daily report on his health — not like that NYT and WaPo published day after day.
Biden’s health problems were far less obvious and yet they drew magnitude more coverage.
Trump’s latest health problem was picked up in The Daily Beast. Not a single story in any of the major newspapers or cable outlets over the last 20 hours.
It’s rather sad to see multiple Indian news outlets — Hindustan Times, Times of India, Times Now, for example — are doing a far better job of covering Trump’s health on a timely basis.
We’re going to have to build a better media ecosystem if we’re going to get the news we need because the major U.S. outlets prove repeatedly they are not capable of meeting this moment in history.
Their wall-to-wall coverage of a political pundit’s death avoiding altogether coverage of the seated president’s health is yet more evidence of the problem we need to fix and quickly.
RFK Jr. DNR’d the US Healthcare System
/64 Comments/in COVID-19, Domestic Policy, Health Policy, Trump 2.0 /by Rayne[NB: check the byline, thanks. /~Rayne]
I’ve been sick with COVID this past week, missing the first classes of the fall semester.
I was exposed by a cancer patient who finished a second round of chemotherapy earlier this month. They weren’t vaccinated within the last year because they were undergoing chemo.
They were exposed after Saturday evening mass at their Catholic church in Florida, where others around them were likely not vaccinated, and definitely unmasked, unlike the cancer patient. A dementia patient who refused to mask was the vector between the congregation and the cancer patient.
The cancer patient is still recovering and now at about 90% of their capacity. They’re moving very slowly, thinking just as slowly. They can’t be left alone because they don’t have the reaction time they used to have.
I’m about 95% recovered, still have some sinus congestion and lingering crud in my chest. My ribs and my throat feel still feel bruised from hacking up my lungs so hard earlier this week.
What I’m not certain I’ll recover from is the trauma of having to check my father the cancer patient for a pulse last week when he collapsed on the kitchen floor, reviving him, getting him up and moving and into my car so I could rush him from their remote home to an urgent care facility more than 30 minutes away.
I didn’t think to put a mask on him or a mask on myself at the time because I was worried something had gone very wrong after my dad’s two-year fight with cancer. I was worried about the monsoon-like storm I had to drive through to get to urgent care. I thought erroneously he had recovered from COVID and wasn’t contagious because he hadn’t had a fever and he hadn’t been coughing.
So I unintentionally hot boxed my dad’s COVID-laden exhalations in my car for 30 minutes trying to save my father. I’d do it again if it came down to it but I should never have had to.
This country has been deeply damaged enough by the anti-vaccine movement since the COVID pandemic began; it shouldn’t have to face worse.
~ ~ ~
By now you’ve read Peterr’s Thursday post about the government’s internecine warfare at the Centers for Disease Control and the excision of director Susan Monarez, followed by the protest resignations of senior CDC staff in support of Monarez. The senior staff who resigned are:
• Demetre Daskalakis, former director of the National Center for Immunization and Respiratory Diseases
• Debra Houry, former chief medical officer and deputy director for program and science
• Daniel Jernigan, former director of the National Center for Emerging and Zoonotic Infectious Diseases
• Jennifer Layden, former director of office of public health data, science, technology
Each of these individuals has a deep background and education in medicine, healthcare, or public health. None of then should have been expected compromise themselves to support our nation’s public health.
None of them should have been treated so shabbily by RFK Jr.’s shit-tastic management of HHS. It’s not at all hyperbole to call it shit-tastic; I strongly recommend listening to The New York Times’ podcast interview with Demetre Daskalakis because it will rid you of any doubt the label is deserved.
Here’s an excerpt I found particularly telling:
DASKALAKIS: Yeah. So this was not related to ACIP, the announcement by the Secretary to change the childhood schedule. I learned about the change of the childhood schedule on X.
ABRAMS: You learned about it on social media —
DASKALAKIS: Yes, ma’am.
ABRAMS: — like the rest of us.
DASKALAKIS: That is correct.
ABRAMS: Wow.
DASKALAKIS: So I was sitting in a meeting with senior leaders at CDC. And as I was sitting there talking about the outbreaks that I was managing, my phone blew up with, “I didn’t know you guys were changing the children’s schedule.”
ABRAMS: People texting you?
DASKALAKIS: Yeah.
ABRAMS: Wow.
DASKALAKIS: Not from HHS, people in the world. Because they saw —
ABRAMS: People in the world, your friends and family or whoever seeing this and being like, this doesn’t sound like you.
DASKALAKIS: Correct. So we then asked the question, what’s going on? Can we see some kind of documentation? Because they were like, implement the change. But we’ve never seen anything in writing, so we asked if we could see the supporting data that led to the decision. And we were told no.
ABRAMS: Just flat out no?
DASKALAKIS: Flat out no.
ABRAMS: But can I ask you, did you ever actually have a conversation with Kennedy about any of this or any of his senior staffers?
DASKALAKIS: No.
ABRAMS: Or is it just that —
DASKALAKIS: No.
ABRAMS: No communication.
DASKALAKIS: No.
ABRAMS: Did you ever try?
DASKALAKIS: Yes.
ABRAMS: And what would happen?
DASKALAKIS: So we offered to do briefings when he first started. I think some people were able to brief some lower level staff, but not staff that were Secretary Kennedy’s staff. So no one from my center has ever briefed the Secretary.
ABRAMS: On anything.
DASKALAKIS: Correct, on anything.
ABRAMS: So basically, don’t have a line into RFK, and he’s not seeking out your advice or the advice of people who are theoretically supposed to advise him on things like this. How did you feel about that at the time?
DASKALAKIS: I felt that this was highly atypical, that we weren’t able to share our expertise up the chain to be able to provide information that could be meaningful and thought process. And so what I kept thinking was, we’re not doing this, but there sure is a point of view up there. I wonder who’s doing it.
My job is to make sure that we’re giving good science so people can make good decisions. And if I can’t make sure that science is untouched by non-scientific influence, I cannot say that I’m doing my job.
I believe that CDC science is going to be compromised by HHS. And if that science becomes biased, if it gets unduly influenced, then I can’t have my name on that science as something that I think should be used to make important decisions for people’s lives.
Again, I strongly recommend listening to this podcast. The other disturbing facet is the way in which Abrams just plows on; it could be an artifact of editing, but it could be another of the many ways in which media has not paused and shouted at the public how disturbing and inappropriate are RFK Jr.’s and Trump’s management of public health, in a misguided effort to remain neutral about a subject which isn’t and can’t be neutral at all.
How can a US media outlet be neutral in the face of what looks increasingly like an occupation of government agencies by hostile forces? In the case of the CDC under RFK Jr.’s HHS, it’s damaging the administration of vaccinations to the entire country while undermining the nation’s ability to respond to pandemic and bioterrorism, not to mention its ability to safely provide basic healthcare. No one will be unaffected; no one can be neutral.
~ ~ ~
I’m not kidding when I say our healthcare is now utterly compromised. Our first responders and healthcare providers can’t be assured of necessary vaccinations. From an ER doctor on Mastodon:
This is absolute bullshit.
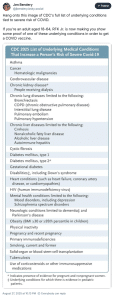
One of the biggest purveyors of anti-vaccine propaganda, one without any healthcare education and training, has decided the persons most likely to be exposed to diseases on a daily basis are no longer eligible for COVID vaccinations if they do not have a limited number of pre-existing chronic health problems. From Jen Bendery on Bluesky:
(For the record, my autoimmune disorder which has cost me lung capacity, is not on this list. I am not eligible for another COVID shot until I turn 65.)
This is a recipe for disaster. Not only are rural hospitals at risk because of cuts to Medicare under Trump’s Big Fugly Bill, all hospitals are at risk if their staff can’t be vaccinated readily in the face of a new COVID wave.
If my father were to become sick again and collapse like he did, could he be assured there would be healthcare personnel ready to receive and treat him? Or might the healthcare system be overwhelmed and triage him to the very end of the line?
The same goes for any of the rest of us, really. How can anyone in the US be assured the healthcare system will be able to respond if RFK Jr. is allowed to continue to hack away at it without supporting data, without support by seasoned, qualified professionals, without adequate oversight by Congress?
~ ~ ~
Of the many things that raced through my mind as I tried to revive my dad was the thought we had not talked about DNR status.
I’m pretty sure my dad and mom have both indicated on healthcare POAs they are DNR under certain conditions.
What happens, though, when one of them collapses at home? Should I have left him on the floor while ensuring his comfort?
Obviously I didn’t do that.
But a little over a week later I can’t help wonder if RFK Jr. has now forced DNR on swaths of Americans, and we’re already DNR where we are in our own homes whether we realize it or not.
If our healthcare system collapses because of his anti-vaccine and anti-healthcare regime, is he not assuring our healthcare system cannot resuscitate many of us?
How would this be different under a hostile foreign occupation?
It’s Time to Call Out the National Gourd
/34 Comments/in Immigration, poetry and satire, Trump 2.0, Trump Administration /by PeterrWatching the members of the National Guard being deployed in DC has been . . . painful. I’m not talking about the assault on democracy, as bad as that is, but the toll this deployment must be taking on the members of the Guard themselves. As a pastor, I’ve had countless members of the National Guard in my congregations. They’re the modern version of the Minutemen, practicing on the weekends every so often, ready to go at a moment’s notice when the need arises. And when the need passes, they go home.
Now imagine that you are one of these members of the Guard who has been deployed in DC, and you’re about to head back home. Then imagine the conversation you’re going to have with your kid . . .
Kid: Dad, what happened on your deployment?
Dad (looking down at his feet): Oh, you know. We went and did our thing, then came home.
Kid: How many terrorists did you shoot?
Dad: It wasn’t that kind of mission.
Kid: Did you blow up somebody’s headquarters?
Dad: Uh, no.
Kid: Then what *did* you do? Is it so secret you can’t tell me?
long pause
Dad (leaning in really close, and whispering): If I tell you, you can’t tell anyone. Promise?
Kid (excited): Promise!
Dad (dramatically looking left and right, to see who might be listening): We picked up . . . trash.
long pause as the Kid looks at Dad
Kid (grinning): Ok, you got me. Seriously, what did you do?
Dad: I’m serious. We. Picked. Up. Trash.
Kid (grin fades to a frown): Trash? Like you put on a day-glo orange vest over your camo uniforms and scooped up water bottles and french fry cups?
Dad: Yeah. And remember, you promised not to tell anyone about this.
Kid: Don’t worry – no one would believe me. And if they did, they’d all laugh at me all day long if they found out. Your secret is safe with me.
Seriously. This makes Alice’s Restaurant and its Group W bench look like nothing. “Son, are you manly enough and lethal enough to pick up trash?”
Trump did this for the symbolism. He did it to make it look as if he is Strong On . . . something. Whatever it is, he’s Strong, and calling out the National Guard is how he shows it. “Look at me, and how Important and Powerful I am. I, only I, the Greatest President in history, can do this!”
In response, there are all kinds of very serious, very appropriate ways to fight back against this. Mayors and governors are filing lawsuits, and working hard to keep this from happening again. Good. Do it, again and again and again. Pundits are punditing, and historians are describing how unprecedented this all it. Fine. These are necessary parts of a response, but they are not a sufficient response. No, the fullness of a response needs to take Trump on on the battlefield of symbolism, turning his desire to project power into a punch line.
As I’ve pondered this, it suddenly hit me. My friends, it is time to call out the National Gourd. I’m talking pumpkins.
 Imagine a bunch of tourists marching east from the Lincoln Memorial with their pumpkins held high, marching past the Vietnam Veterans Memorial, the MLK Jr. memorial, the reflecting pool, the Korean War memorial, and the WWII memorial. Meanwhile, at the other end of the Mall, imagine another bunch of tourists with pumpkins marching west from the Capitol. Imagine them marching past the National Museum of the American Indian, the Air and Space Museum, and the National Museum of African American History and Culture. Imagine these two groups meeting, with their pumpkins held high, at the Washington Monument, then turning north.
Imagine a bunch of tourists marching east from the Lincoln Memorial with their pumpkins held high, marching past the Vietnam Veterans Memorial, the MLK Jr. memorial, the reflecting pool, the Korean War memorial, and the WWII memorial. Meanwhile, at the other end of the Mall, imagine another bunch of tourists with pumpkins marching west from the Capitol. Imagine them marching past the National Museum of the American Indian, the Air and Space Museum, and the National Museum of African American History and Culture. Imagine these two groups meeting, with their pumpkins held high, at the Washington Monument, then turning north.
Toward the White House.
Imagine the fence around the White House suddenly surrounded by the National Gourd, as the tourists deposit their pumpkins on the sidewalks around Trump’s doorstep.
Imagine the National Gourd appearing along the mansions of Embassy Row.
Imagine the National Gourd filling Lafayette Square, just north of the White House.
Imagine the National Gourd appearing at Blair House, at the US Naval Observatory (home to JD Vance), and on the steps of SCOTUS.
Imagine the National Gourd appearing at the DC Armory, home to the DC National Guard.
Imagine the National Gourd appearing all over DC. Imagine DC businesses putting a member of the National Gourd at their doors and in their windows. Imagine Metro Stations with their own National Gourd presence. Imagine the National Gourd lining The Wall at the Vietnam Memorial. Imagine the National Gourd sitting at the feet of every soldier in the Korean War Memorial. Imagine the National Gourd alongside every figure in the FDR Memorial. Imagine the National Gourd appearing at Dulles Airport and at DC (aka Reagan) National Airport. Imagine the National Gourd appearing at Langley, the Pentagon, and the FBI headquarters.
Imagine the National Gourd showing up at Mar-a-Lago in Florida, Trump Tower in New York, and Trump’s Bedminster golf course in New Jersey.
And then imagine the National Gourd showing up at the Great Lakes Naval Station outside of Chicago, to greet the folks Trump is apparently going to send there.
Imagine the National Gourd appearing at federal buildings and offices around the country. Agricultural extension offices, military recruiting centers, federal courthouses, and post offices. Navy bases and Air Force bases and Army bases and Marine bases. National park entrances and IRS buildings and ICE offices. Imagine a member of the National Gourd showing up at every federal facility in the country.
Call out the National Gourd, and make Trump weep.
This past week, a certain coffee chain released their annual chemical pumpkin-based weapon: the pumpkin spice latte. All around the country, pumpkin-based artillery units are holding their annual “Punkin Chunkin” events (see here or here or here or here for examples), where trebuchets, catapults, and other devices launch pumpkins enormous distances (unless the pumpkin explodes in mid-air, known as “pumpkin pie”). [If you want to see more, google “punkin chunkin”] The world championships used to be broadcast on various television stations, but perhaps the powers that be realized that they were disclosing military secrets and the broadcasts have ceased in recent years. Even so, these are the regular training events for the National Gourd.
And then there’s the Half Moon Bay Art and Pumpkin Festival.
In six weeks, the little town of Half Moon Bay, California, population 11,795, will be transformed from a sleepy little coastal village to become the epicenter of Pumpkinism as around 200,000 folks come to town for their annual Half Moon Bay Art and Pumpkin Festival.
200,000 people line the streets for a grand parade, and it is the pumpkin equivalent of the USSR’s May Day parades in Red Square, where missiles and tanks were paraded before the  Soviet Politburo. In Half Moon Bay, the highlight of the parade is the Mother of All Pumpkins, as growers from all over bring their best to Half Moon Bay, hoping to be crowned the biggest and the best. We’re talking pumpkins in excess of 1000 pounds. When I lived in the Bay Area, the Half Moon Bay Pumpkin Festival was an annual pilgrimage.
Soviet Politburo. In Half Moon Bay, the highlight of the parade is the Mother of All Pumpkins, as growers from all over bring their best to Half Moon Bay, hoping to be crowned the biggest and the best. We’re talking pumpkins in excess of 1000 pounds. When I lived in the Bay Area, the Half Moon Bay Pumpkin Festival was an annual pilgrimage.
This is the parade that Trump wanted for his birthday, and never got.
We are approaching peak pumpkin season, and along with all the serious lawsuits and punditry, maybe the National Gourd can help take Trump’s ego down a notch or two. In a publicity contest between the National Guard and the National Gourd, I’ll bet on the Gourd every day and twice on Sundays. Especially in September and October.
Oh, and while we’re chatting . . .
Like many such events, the Half Moon Bay Art and Pumpkin Festival did not happen during COVID. Even so, the festival made their usual contributions to a bunch of local organizations, as if the festival had continued as usual. While this kept those groups afloat, it hurt the finances of the festival hard. Last April, local media reported that their own sustainability was in jeopardy. This is an amazing local festival, and if you are so inclined, you can help them out here.
Seriously. This is an incredible event, and they can use all the help they can get.
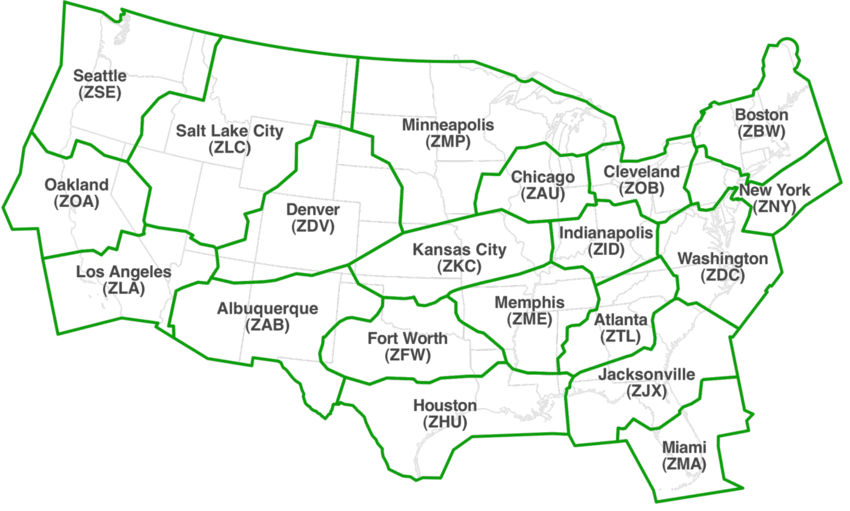
Happy Flying This Weekend – Who Needs All Those Meteorologists?
/51 Comments/in Infrastructure, Science, Trump 2.0, Trump Administration /by PeterrFrom the GAO yesterday, via Government Executive:
National Weather Service meteorologists who assist air traffic controllers are working overtime, skipping leave and taking on more responsibilities due to worsening staff shortages, according to a Government Accountability Office report published Thursday, which criticized the Federal Aviation Administration for not doing enough in response to the problem.
“Not having identified and addressed the risks of the current staffing levels is concerning given the potential safety effects if aviation meteorologists are overworked and the quality of their services to air traffic controllers is diminished,” investigators wrote.
Well *that* doesn’t sound good. What exactly do they mean by “diminished”?
As of June, NWS said the aviation meteorologist workforce is down to 69 employees, partly as a result of the federal hiring freeze and separation incentive programs like deferred resignation. FAA and NWS in February agreed to a cap of 81 full-time equivalents for such positions. (In 2024, prior to the agreement, the report said that the FAA was pushing to lower that number to 71.)
Under a 2016 interagency agreement between FAA and NWS, there are supposed to be three meteorologists and one meteorologist in charge at each of the 21 air route traffic control centers across the U.S. But that is not achievable under the February agreement.
GAO reported that the control center in Oakland, Calif., is down to one meteorologist, another four centers have only two such employees and five centers don’t have a meteorologist in charge.
OK, you’ve got my attention now. I used to live in Oakland and then elsewhere in the East Bay, and this is nuts.
But let’s back up a minute, to make a few things clear. The FAA has facilities in every airport air traffic control tower. These folks handle takeoffs, landings, ground control on the taxiways, and other local issues. These are not the places this report is discussing. The FAA also has 21 regional air traffic control facilities that handle regional air traffic flow (see the map above). These are the facilities that worry the GAO.
Suppose you are flying from Denver to Oakland. When you take off, the Denver tower is in charge. Once you reach a certain altitude/distance from the airport, the pilot switches over to the Denver regional National Airspace System [NAS] hub for instructions and guidance. As you fly west, the Denver hub passes control to the Salt Lake City hub, and eventually to the Oakland regional hub. Finally, as you approach the Oakland airport, the pilot contacts the Oakland airport control tower for the final approach and landing.
Each of these regional NAS hubs, in the course of handling traffic issues, pays a lot of attention to the weather. Ever hit turbulence or storms? The meteorologists can predict where they are likely to appear, and (depending on severity) the NAS controllers then can either warn the pilots to expect minor turbulence in a particular area, or route the flights around that area if it is deemed severe.
So let’s go back to that Denver to Oakland flight.
The Rocky Mountains can create a *lot* of turbulence. Especially in the summer. Like during the Labor Day weekend. As you fly west, you come to other smaller but similar areas, like the Sierra Nevada mountain range in California and ultimately the hills and mountains that surround the San Francisco Bay. Complicating things, the SF Bay has three major commercial airports — SF, Oakland, and San Jose — as well as dozens of smaller municipal fields, private corporate airstrips, and military bases. In other words, there is a lot of air traffic in a relatively small area.
And according to the GAO, the Oakland regional air traffic control hub, instead of having four meteorologists, is down to just one.
One.
And it’s not like that one can clock out at 5pm and tell all the planes to tune in to “weather on the 8’s” on the radio or the 5:15 weather report on the KRON evening news to get updates they need.
I’ve had the pleasure of being the pastor to more than a few NWS meteorologists, and they have told me in detail about their love for their work. I’ve rejoiced with them when their severe weather warnings have saved lives, even when a tornado blows a town to bits. Over the last six months, I’ve also grieved with them as they have seen their agency stretched beyond the breaking point. Some of their friends have been let go as “redundant” or “wasteful”, others are fearing that they may be next to get the axe or be forced to relocate themselves and their families, and *everyone* is working far more than is healthy. We’re talking vacations cancelled, days off postponed, and suddenly having to work a double shift.
And it’s been like this for half a year, with no end in sight.
The NAS [National Airspace System] is currently under tremendous strain as air traffic controller shortages and periodic equipment failures in aging air traffic control systems have been leading to delayed and canceled flights. We and others have reported on these challenges, and we currently have ongoing work in these areas.11 Severe weather can exacerbate such strains on the NAS as FAA reports that weather is the leading cause of cancellations and delays.12 Multiple stressors on the NAS can lead to compounded adverse conditions for passengers. For example, the widespread delays and cancellations Southwest Airlines experienced in December 2022 began with weather problems that were compounded by carrier system failures.13
The purpose of this report is to inform you and Congress about another stressor on the NAS—concerns about aviation meteorologist staffing levels—which we identified in our ongoing work on aviation operational preparedness.14 These meteorologists work directly with air traffic controllers in the command center and en route centers, providing face-to-face briefings as necessary, and helping them safely direct flights to avoid severe weather. We recognize that determining the appropriate weather forecasting resources to effectively support the safe and efficient operation of the NAS may take time to examine in depth. However, given the urgency of the issues, and that the interagency agreement is scheduled to expire in September 2025, we are sharing this information with you now.
This report from the GAO is a flashing red light, a bone-chilling siren, trying to get the attention of people with the power to change things. I only hope it works.
Given that we’re talking about a government headed by a guy who thinks he is smarter than all the meteorologists at the National Hurricane Center and the NWS, and can predict the path of hurricanes simply by using his sharpie, I am not confident things will change at all.
Here’s hoping the worst the flying public has to deal with this weekend are baggage problems and seats with cramped leg room.