When I read this passage from DOJ’s new News Media Policy, it caused me as much concern as relief.
The Department’s policies will be revised to provide formal safeguards regarding the proper use and handling of communications records of members of the news media. Among other things, the revisions will provide that with respect to information obtained pursuant to the Department’s news media policy: (i) access to records will be limited to Department personnel who are working on the investigation and have a need to know the information; (ii) the records will be used solely in connection with the investigation and related judicial proceedings; (iii) the records will not be shared with any other organization or individual inside or outside of the government, except as part of the investigation or as required in the course of judicial proceedings; and(iv) at the conclusion of all proceedings related to or arising from the investigation, other than information disclosed in the course of judicial proceedings or as required by law, only one copy of records will be maintained in a secure, segregated repository that is not searchable.
It is nice for the subset of journalists treated as members of news media whose calls get treated under these new policies and not — as still seems possible — under the apparently more permissive guidelines in the FBI’s Domestic Investigations and Operations Guide that when their call and other business records are collected, some of that information will ultimately be segregated in a non-searchable collection. Though why not destroy it entirely, given that the information used for the investigation and court proceedings will not be segregated?
Moreover, this passage represents a revision of previous existing policy.
Which means data from members of the news media may not have been segregated in the past.
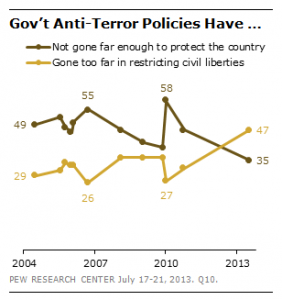
When you consider that one of the abuses that led to these new policies included the collection of 20 phone lines worth of data from the AP — far, far more than would be warranted by the investigation at hand — it raises the possibility that DOJ used to do more with the data it had grabbed from journalists than just try to find isolated sources.
Like the two to three hop analysis they conduct on the Section 215 dragnet data.
It’s with that in mind that I’ve been reading the reports that Kiwi troops were wandering around Kabul with records of McClatchy freelancer Jon Stephenson’s phone metadata.
The Sunday Star-Times has learned that New Zealand Defence Force personnel had copies of intercepted phone “metadata” for Stephenson, the type of intelligence publicised by US intelligence whistleblower Edward Snowden. The intelligence reports showed who Stephenson had phoned and then who those people had phoned, creating what the sources called a “tree” of the journalist’s associates.
New Zealand SAS troops in Kabul had access to the reports and were using them in active investigations into Stephenson.
The sources believed the phone monitoring was being done to try to identify Stephenson’s journalistic contacts and sources. They drew a picture of a metadata tree the Defence Force had obtained, which included Stephenson and named contacts in the Afghan government and military.
The sources who described the monitoring of Stephenson’s phone calls in Afghanistan said that the NZSIS has an officer based in Kabul who was known to be involved in the Stephenson investigations.
Last year, when this happened, Stephenson was on the Green-on-Blue beat, He published a story that a massacre in Pashtun lands had been retaliation for the killing of Taliban. He reported on another NATO massacre of civilians. He reported that a minister accused of torture and other abuses would be named Hamid Karzai’s intelligence chief. Earlier last year he had reported on the negotiations over prisoner transfers from the US to Afghan custody.
Now, the original report made a both a credibility and factual error when it said Stephenson’s metadata had been “intercepted.” That has provided the Kiwi military with a talking point on which to hang a non-denial denial — a point Jonathan Landay notes in his coverage of the claims.
Maj. Gen. Tim Keating, the acting chief of New Zealand’s military, said in a statement that no military personnel had undertaken “unlawful interception of private communications.”
“I have asked the officers responsible for our operations in Afghanistan whether they have conducted monitoring of Mr Stephenson . . . and they have assured me that they have not.”
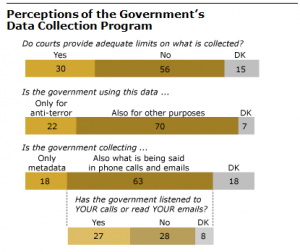
The statement, however, did not address whether metadata, which includes the location from where a call is made, the number and location of the person who is being called and the duration of the call, was collected for Stephenson’s phones. Such data are generally considered business records of a cell phone provider and are obtained without intercepting or real-time monitoring of calls. In the United States, for example, the Foreign Intelligence Surveillance Court has ordered Verizon to deliver such records of all its customers to the National Security Agency on a daily basis.
While under contract to McClatchy, Stephenson used McClatchy cell phones and was in frequent contact with McClatchy editors and other reporters and correspondents. [my emphasis]
Indeed, higher ranking New Zealand politicians are trying to insinuate that Stephenson’s call records would only be collected if he was communicating with terrorists — even while admitting the government did have a document treating investigative journalists like terrorists.
Prime Minister John Key said it’s theoretically possible that reporters could get caught in surveillance nets when the U.S. spies on enemy combatants.
[snip]
Also Monday, New Zealand Defense Minister Jonathan Coleman acknowledged the existence of an embarrassing confidential order that lists investigative journalists alongside spies and terrorists as potential threats to New Zealand’s military. That document was leaked to Hager, who provided a copy to The Associated Press. Coleman said the order will be modified to remove references to journalists.
Finally, New Zealand officials seem to be getting close to blaming this on the US.
“The collection of metadata on behalf of the NZDF by the U.S. would not be a legitimate practice, when practiced on a New Zealand citizen,” Coleman said. “It wouldn’t be something I would support as the minister, and I’d be very concerned if that had actually been the case.”
Thus far, the coverage of the Stephenson tracking has focused on the Kiwi role in all of it. But as Landay notes, Stephenson would have been using McClatchy-provided cell phones at the time, suggesting the US got the records themselves, not by intercepting anything, but simply by asking the carrier, as they did with the AP.
Ultimately, no one is issuing a direct denial that some entity tied to ISAF — whether that be American or New Zealand forces — collected the phone records of a journalist reporting for a US-based outlet to try to identify his non-friendly sources.
So what other journalists have US allies likened to terrorists because they actually reported using both friendly and unfriendly sources?