“I wanted to infect everything:” The Curiously Expert Pathologies of FBI Informant, Microchip
I’ve now read the substantive transcripts in the trial of Douglass Mackey, the far right troll who was convicted last month of conspiring to violate the voting rights of Hillary voters in the 2016 election.
As I noted in my first write-up of the verdict, the case has lessons that remain quite pressing, as loud boys on, who own, and claim to be interested in regulating Twitter attempt to make the site more welcoming to far right election disinformation. I plan to write that up.
Before I do, though, I want to talk about Microchip, the cooperating witness who pled guilty to the same conspiracy as part of a cooperation agreement in 2022.
We first learned the FBI had a cooperating witness on March 8 of this year, when Judge Nicholas Garaufis ordered the government to unseal its request to keep its informant’s identity secret. The filings in that discussion did not describe much about the timing or scope of his cooperation, other than that those he is targeting have the technical skills that might lead to him being hacked if he were discovered.
The fact of the CW’s cooperation is sure to be seen by many in that community as a profound betrayal, with the result that, at a minimum, online harassment is bound to follow the CW should his or her identity become a matter of public record. That harassment can have negative consequences in and of itself. In addition, to claim that intense online attacks do not endanger a person’s physical safety is to ignore the reality of our current world, as evinced in common newspaper headlines. See, e.g., Sheera Frenkel, The Storming of Capitol Hill Was Organized on Social Media, N.Y. TIMES, Jan. 6, 2021, available at https://www.nytimes.com/2021/01/06/us/politics/protesters-storm-capitol-hillbuilding.html; Eric Lipton, Man Motivated by “Pizzagate” Conspiracy Theory Arrested in Washington Gunfire, N.Y. TIMES, Dec. 5, 2016, available at https://www.nytimes.com/2016/12/05/us/pizzagate-comet-ping-pong-edgar-maddisonwelch.html. It is simply (and regrettably) a fact of the times that many acts of politically motivated violence in current society arise from campaigns of online harassment.
Beyond the risk to the CW, the potential consequences include the disruption of the CW’s ongoing work with the FBI. It is certainly true that the nature of this work is online and anonymous, but, if the CW’s name and location were to become known, the CW would become a target for all who believe that they might be under investigation (whether they are or not). Given the technical proficiency of those with whom the CW associates, it is not difficult to envision multiple scenarios in which the CW’s online work could be jeopardized by way of a cyberattack (at a minimum).
Microchip’s identity can’t be that well protected. As soon as this pre-trial discussion was posted, Mackey’s lawyer, Andrew Frisch, contacted the government to tell them he had learned of the informant’s real identity independently (possibly via Anthime “Baked Alaska” Gionet) and at least one researcher I’ve spoken with since seems to have a plausible theory as to his real identity.
But I assumed, based on those filings, that Microchip had flipped in advance of Mackey’s arrest.
The actual details are more complicated — and a bit unpersuasive, as AUSA William Gullotta got Microchip to explain in his testimony on March 23.
The thing I find most unbelievable is Microchip’s claim that he only joined Twitter — in any capacity — in July 2015, just months before he started playing a central and expert role in expanding the reach of anti-Hillary trolling.
Q When did you start using Twitter?
A Back in around July of 2015.
Q When did you start using the alias Microchip on Twitter?
A Anywhere from November 2015 through March 2016, somewhere around there.
I find this claim so surprising because, in his description of his trolling, Microchip described the kind of Twitter expertise that normally takes years to build. And two 2017 articles celebrating Microchip’s expertise (Buzzfeed, Politico) describe that he exhibited expertise from the start of his identity in November 2015.
For example, Microchip described how — the implication is all of his engagement was Microchip — he used various levels of operational security to succeed in creating new accounts anonymously, from the start.
Q When you would set up your accounts, did you set them up anonymously?
A I did.
Q How do you go about doing that?
A Using virtual private networks or proxy IP address services.
Q What’s a virtual private network?
A It’s, basically, somebody who sets up servers across the world in different locations and then you can tie into that service so you appear as if you are at that location and then they feed the internet through that.
Q So it would mask your true location from Twitter?
A That’s right.
Q What other information did you need to provide to Twitter to set up a new account?
A Yes, you need an email address or a phone number or both.
Q So would you just set up anonymous email addresses —
A Oh, yeah, through Google, Gmail, you set up a account and then you set up a Google Voice account and then if you need to change a phone number on that, you pay ten bucks and you get a new phone Number.
His description of various means to exploit Twitter to inject extremist views into the mainstream come off as pathological … but extremely savvy.
Q And why would you want it to be on a trending list?
A Because I wanted our message to move from Twitter into regular society and part of that would be — well it’s based on the idea that, you know, back then maybe — I don’t know, 10 to 30 percent of the US population was on Twitter, but I wanted everybody to see it, so I had figured out that back then, news agencies, other journalists would look at that trending list and then develop stories based on it.
Q What does it mean to hijack a hashtag?
A So I guess I can give you an example, is the easiest way. It’s like if you have a hashtag — back then like a Hillary Clinton hashtag called “I’m with her,” then what that would be is I would say, okay, let’s take “I’m with her” hashtag, because that’s what Hillary Clinton voters are going to be looking at, because that’s their hashtag, and then I would tweet out thousands of — of tweets of — well, for example, old videos of Hillary Clinton or Bill Clinton talking about, you know, immigration policy for back in the ’90s where they said: You know, we should shut down borders, kick out people from the USA. Anything that was disparaging of Hillary Clinton would be injected into that — into those tweets with that hashtag, so that would overflow to her voters and they’d see it and be shocked by it.
Q Is it safe to say that most of your followers were Trump supporters?
A Oh, yeah.
Q And so by hijacking, in the example you just gave a Hillary Clinton hashtag, “I am with her,” you’re getting your message out of your silo and in front of other people who might not ordinarily see it if you just posted the tweet?
A Yeah, I wanted to infect everything.
Q Was there a certain time of day that you believed tweeting would have a maximum impact?
A Yeah, so I had figured out that early morning eastern time that — well, it first started out with New York Times. I would see that they would — they would publish stories in the morning, so the people could catch that when they woke up. And some of the stories were absolutely ridiculous — sorry. Some of the stories were absolutely ridiculous that they would post that, you know, had really no relevance to what was going on in the world, but they would still end up on trending hashtags, right? And so, I thought about that and thought, you know, is there a way that I could do the same thing.
And so what I would do is before the New York Times would publish their — their information, I would spend the very early morning or evening seeding information into random hashtags, or a hashtag we created, so that by the time the morning came around, we had already had thousands of tweets in that tag that people would see because there wasn’t much activity on Twitter, so you could easily create a hashtag that would end up on the trending list by the time morning came around.
Perhaps most chilling is his description of how participants in this anti-Hillary trolling knew there was nothing to the John Podesta emails they made the focus of their October 2016 trolling.
It didn’t matter. They didn’t care.
They were aiming to cause chaos to hurt Hillary’s chances of winning.
Q What was it about Podesta’s emails that you were sharing?
A That’s a good question.
So Podesta ‘s emails didn’t, in my opinion, have anything in particularly weird or strange about them, but my talent is to make things weird and strange so that there is a controversy. So I would take those emails and spin off other stories about the emails for the sole purpose of disparaging Hillary Clinton.
T[y]ing John Podesta to those emails, coming up with stories that had nothing to do with the emails but, you know, maybe had something to do with conspiracies of the day, and then his reputation would bleed over to Hillary Clinton, and then, because he was working for a campaign, Hillary Clinton would be disparaged.
Q So you’re essentially creating the appearance of some controversy or conspiracy associated with his emails and sharing that far and wide.
A That’s right.
Q Did you believe that what you were tweeting was true?
A No, and I didn’t care.
Q Did you fact- check any of it?
A No.
Q And so what was the ultimate purpose of that? What was your goal?
A To cause as much chaos as possible so that that would bleed over to Hillary Clinton and diminish her chance of winning.
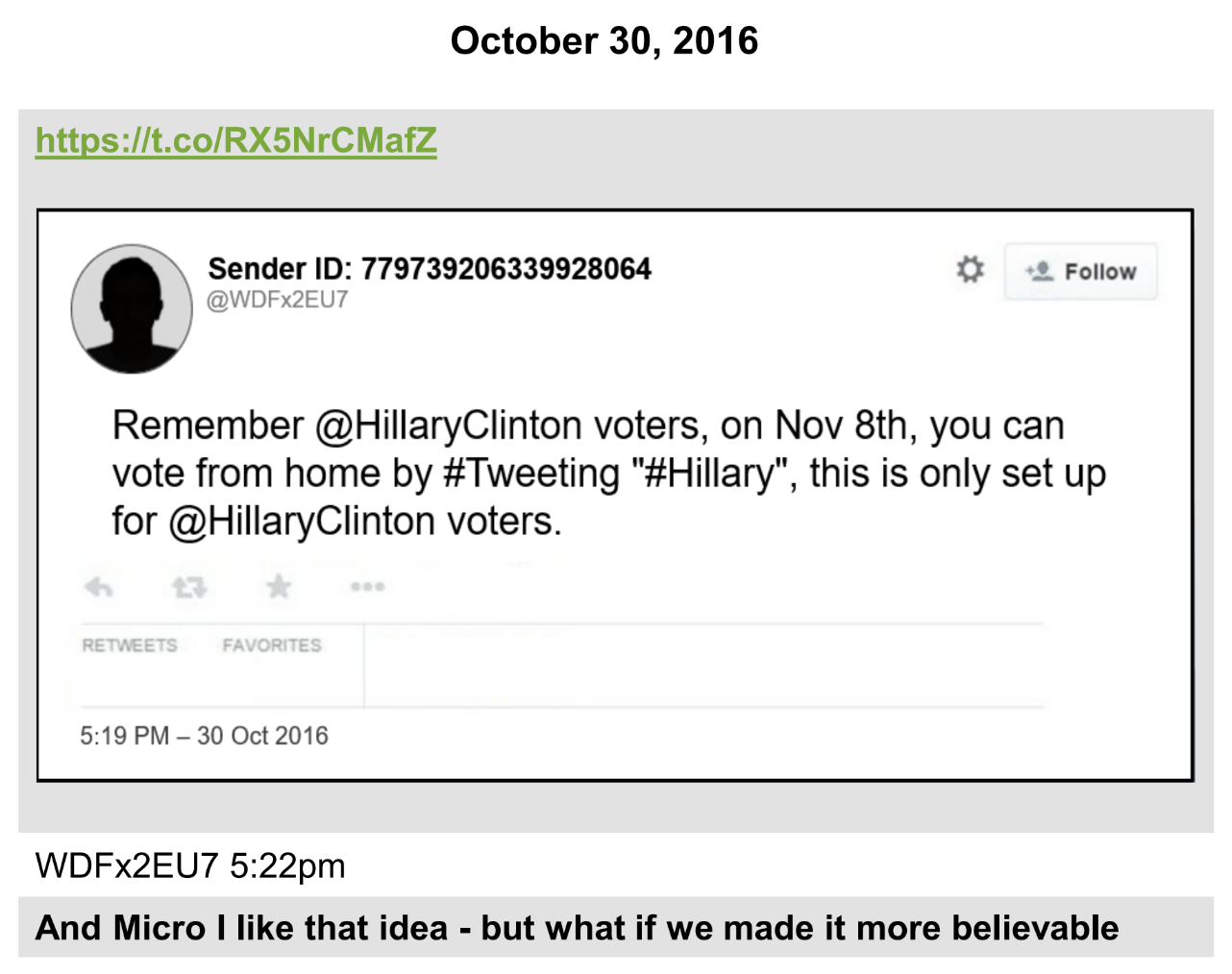
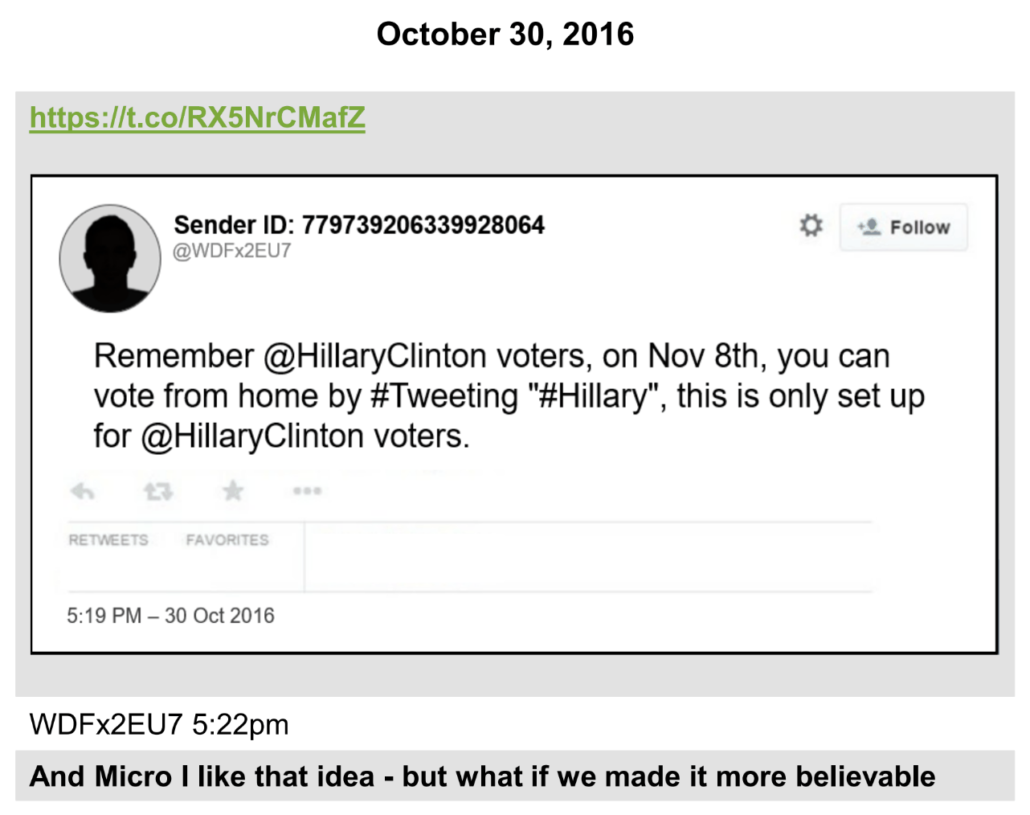
Microchip was actually one of the people who, on October 30, 2016, brought the idea of getting Hillary voters to vote from home from 4Chan to the War Room where anti-Hillary trolls workshopped ways to make it more realistic and ensure that Trump voters wouldn’t also fall for the meme.
And, as he described it, during 2016, Microchip was paying up to $500 a month, between two services, to use bots to expand the reach of right wing trolling.
A Yeah, so one of the first services to kind of seed the followers was a service called Add Me Fast, A-D-D, M-E, F-A-S-T, and that service is kind of like a peer networking service where I would insert the tweet into that service, somebody else would insert a tweet and then, we would retweet each other’s information, right? And you could gain points doing that and, if you accumulate points, you can then expend those on likes, followers, retweets. So that service, I would spend sometimes $300 a month on it. That would give you around a thousand to three thousand retweets, likes, or follows.
[snip]
Another step is using Fast Followerz and that’s F-A-S-T and then F-O-L-L – – Q O-W-E-R-S? A Yeah, but it’s with a “Z,” it’s with a Z at the end. .com, yeah. And that service you spends like, a monthly fee of, you know, a hundred to two hundred, sometimes three hundred bucks a month. And they have control of all the bots, so you don’t actually retweet anything, but you put in your Twitter handle or you put in a tweet that you want to get retweeted, and the service that I would use would be 50 to a hundred followers, something like that, a day, and then those followers would also retweet or “like” my tweets anywhere from three to five times.
No one explained where Microchip came up with $500 a month to make anti-Hillary trolling go viral.
On cross-examination, however, Mackey’s lawyer, Frisch, did get Microchip to admit that when he started cooperating with the FBI on this case in 2021, he had both IRS and bankruptcy debts.
Also on cross, Microchip described that he’s not paid for any of the assistance he provides to the FBI — though as he prepared for the trial in February, he described liking the “structure” working with the FBI provided his life.
Q Without telling us what you’re doing, how often do you do this work for the FBI?
A As often as needed, essentially.
Q You’re not getting paid for it; right?
A That’s right.
Q In fact — in fact, you met with the FBI on or about February 23, 2023, earlier, about a month ago; do you remember that? Mr. Paulson was there, Mr. Gullotta was there. All three prosecutors were there.
A Yeah, I think that was here in Brooklyn.
Q And you asked — you said — you said — do you recall saying that you wanted to keep working with the FBI because the FBI provided a structure that was valuable to you?
[Frisch refreshes his memory with his 302]
Q And that’s what you said; right?
A Yes.
While the trial showed that Mackey was important to the effort to suppress the votes of Black and Latino Hillary voters because he had so much reach, particularly among the more general public in 2016, Microchip — who claims to have been a newB Twitter user in July 2015 — seems to have played a more important role in professionalizing all aspects of the anti-Hillary campaign.
Mackey made these memes popular; Microchip made them work.
Which makes the timeline more curious. By all appearances, the FBI knew of Microchip long before they charged Mackey, starting in 2018 (about eight months after Mackey was first IDed). That’s when he first offered to cooperate with the FBI.
A No. I talked to the FBI about being useful to them when they came and actually talked to me the first time. I discussed with the FBI in the car at my residence at the time. We actually sat in the car outside of my home, and I talked to them about my use of technology and how it could possibly be useful to whatever they might be working on.
They seem to have paid him a visit, as well, as they prepared to charge Mackey in December 2020. But even in spite of the fact that his key role in preparing anti-Hillary memes would have been readily obvious in warrants served on Twitter in advance of charging Mackey, the FBI didn’t charge Microchip along with Mackey in January 2021.
And only as they looked closer after he reached out did they decide they needed him to plead guilty.
Timeline
July 2015: Microchip joins Twitter
November 2015: Microchip starts to create his persona
April 5, 2017: Buzzfeed article quoting Microchip claiming, “it’s all us, not Russians” describing he turned to Twitter in response to November 2015 terror attacks in Paris
August 9, 2017: Politico article describing Microchip as an “early player” in hard-right Twitter chatrooms starting in November 2015
December 17, 2018: FBI questions Microchip about July 2018 online threat
December 15, 2020: Second contacts with FBI, including Megan Rees (about which Microchip tells Baked Alaska), Microchip lawyers up
January 27, 2021: Mackey arrest
February 4, 2021: Microchip’s lawyer reaches out to FBI, broaches cooperation
April 22, 2021: Formal proffer with government
June 2021: First of several agreements to toll statutes of limitation
April 14, 2022: Guilty plea