Elmo’s Forced Marriage
I feel like a lot of the commentary about Elon Musk’s purchase of Twitter — which includes a great deal of Kremlinology about what Elmo says on Twitter — has forgotten how we got here.
Elmo entered what is effectively a forced marriage.
Consider this dramatic reenactment:
Twitter: Hey, Elon, can you come help build value in our platform? Jack said it’d be a good idea.
Elmo: It’s a deal!
Twitter: Oh wait, we have to do due diligence on you first.
Elmo: Fuck that. I’m buying you all out. Twitter sucks!!!
Twitter: Okaaayyyy… If you want to buy us without yourself doing due diligence, you got it.
Elmo: But wait! Bots! Twitter sucks!!!
Twitter: You said no due diligence.
Elmo: Deal is off! Bots! Twitter sucks!!
Twitter: See you in court.
Twitter: Huh. These emails you sent are really interesting. We really look forward to the deposition and trial.
Elmo: Uh … uh … uh, alright then, the deal is back on.
At this point, a week into Elmo’s ownership, it’s unclear whether he went through with the purchase because he really wanted to buy the joint, or because in the face of exposure in the spring (in the form of due diligence), and last month (in the form of a deposition and trial), he kept doubling down, effectively dodging scrutiny of his own suitability to run Twitter by throwing money at it, $44 billion instead of the billion he’d have to pay to back out of the deal. And for much of that time, Elmo responded to Twitter’s scrutiny by attacking the company.
Thus far, it seems clear that Elmo is not suitable to run Twitter.
If he were merely the richest man in the world and not instead a billionaire whose wealth is heavily invested in an existing company that is subject to the whim of the market, a company the value of which has been damaged by Elmo’s Twitter tantrum — if he were spending his own money on the purchase — it might have ended there. But to pull off the purchase, he added a bunch of new debt to a company already reeling under its existing debt load, making the dire financial situation of Twitter even worse, in the middle of a tech downturn.
To make matters still worse, the entire world knows that the richest man in the world just made one of the worst deals in history, buying a company worth maybe $20 billion — a company whose own worth he spent months diminishing — for $44 billion.
It’s got to rankle a thin-skinned egotist like Elmo, knowing that all the pinheads he attacked at the beginning of this process just watched him get utterly fleeced in a business deal.
The richest man in the world just got his ass handed to him, and in his first act after consummating this forced marriage, he fired the people who handed him his ass in such a way that Elmo will either have to pay severance or settle lawsuits for the way he fired them.
And that’s reason why I think people are investing far too much faith in what Elmo is saying on Twitter. Is he saying what he’s saying because he’s testing out an affirmative business plan? Or is he saying what he’s saying because he loathes many of the most prominent people on Twitter, who all told him he was wrong and just watched him make an epically bad business deal, but he nevertheless needs to con enough advertisers and funders and Twitter members in the interim to stave off further personal losses on the company?
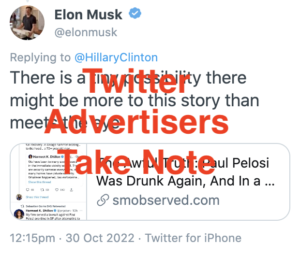
One of his first instincts was to prove those pinheads wrong about disinformation by embracing conspiracy theories about the attempted kidnapping of Nancy Pelosi.
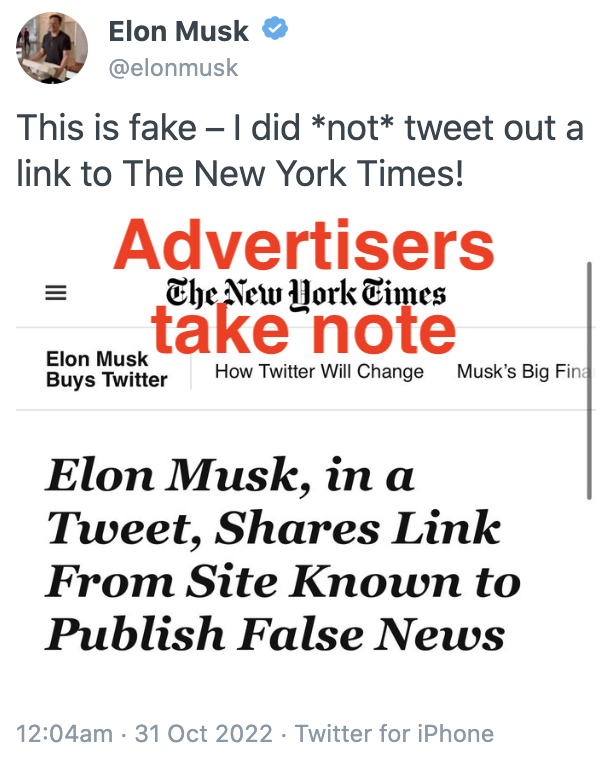
After deleting that with no acknowledgment of how stupid the tweet was, Elmo laughed it off by calling the NYT fake news, something that may have salved his ego but surely made advertisers even more wary of continuing to spend money with him.
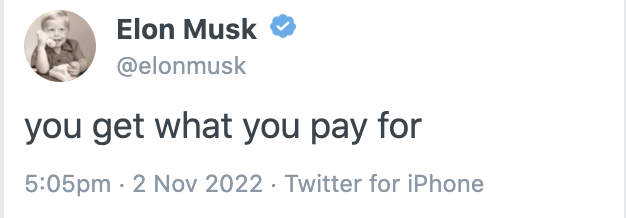
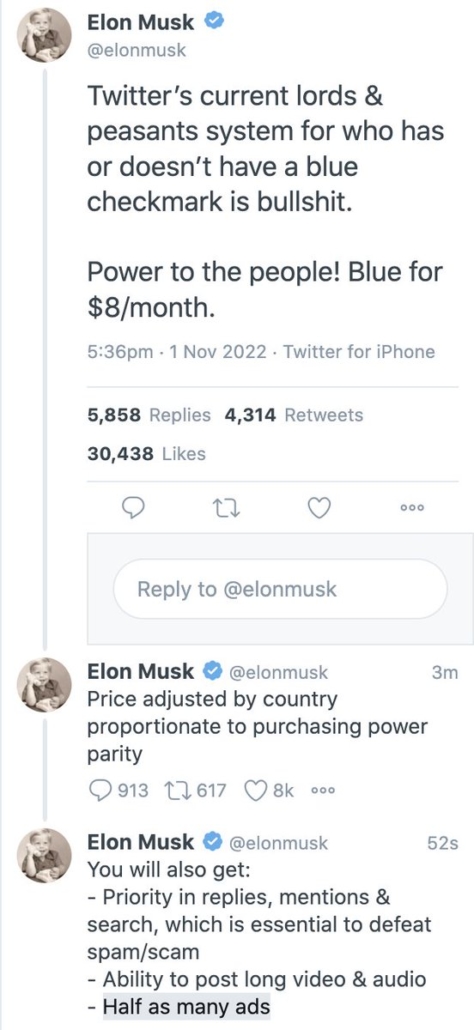
Since then, Elmo has turned to making it look like There Is a Plan to charge for Twitter.
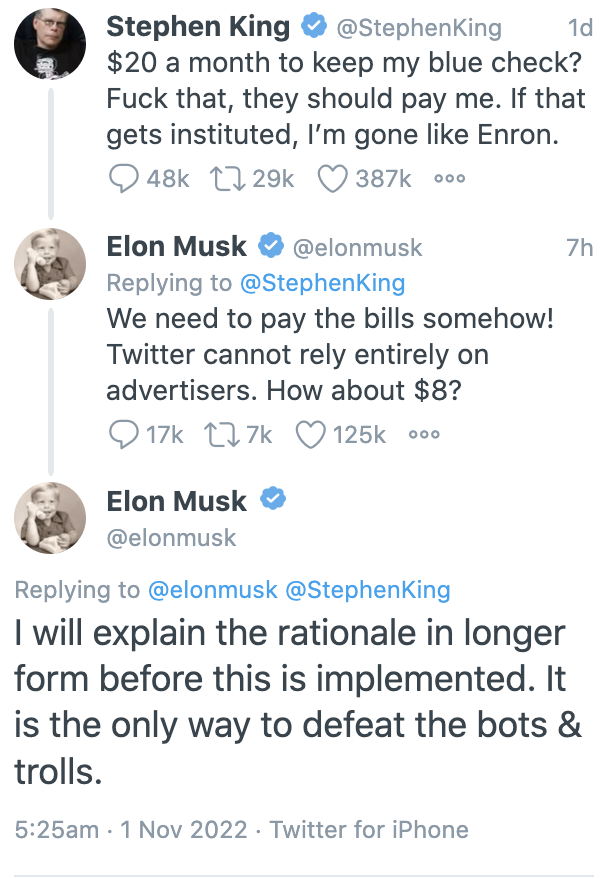
Elmo would later admit that verification would be replaced with notice of someone’s stature, akin to what is currently used by politicians. This exchange — getting put in his place by the creator of great horrors — really amounted to Elmo announcing the roll-out of the Twitter Blue program that he and Jack Dorsey talked about last spring.
Even in spite of getting rebuked by Stephen King, Elmo kept pitching the pay service — to the people he needs to keep on Twitter to retain its value — as a solution to problems other than that Twitter is over-leveraged.
In the process of his serial attempts to claim that forcing users to pay for what is free now, Elmo repeatedly revealed he either doesn’t understand or doesn’t much care about what brings value to Twitter, the free content from people like Stephen King. Similarly, he repeatedly claimed that his efforts to monetize Twitter were instead efforts to address things that the pinheads value, disinformation, and things he used to attack Twitter when trying to back out of the deal, the bots.
He has not admitted that the cost of Twitter Blue would now have to pay for his epically shitty business deal, on top of what it would have paid for in April, before he started his six month tantrum. How much of an $8 monthly fee amounts to bailing Elmo out of a deal that everyone knows was epically stupid?
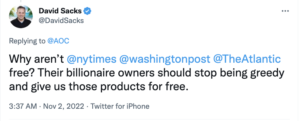
Elmo’s top advisors aren’t any better. Here, David Sacks took a break from apologizing for Putin to ask why Jeff Bezos and other billionaires don’t give away the content that their own employees create for free, apparently not understanding that Twitter’s employees don’t create the content on offer.
All the while, both these inapt advisors and Elmo himself keep boasting as if they’re not the ones who just got their asses handed to them in a business deal.
I don’t know how this is going to go — other than downhill. Once I paint my walls I’ll start building up my presence at @[email protected]. I’ve got an account at CounterSocial but for now I’m focusing on Mastodon. I hope and expect alternatives to both will be rushed out to fill the role Twitter once did.
Until then, though, I think Elmo’s serial meltdown on Twitter is better explained by his discomfort in a new role, in which he needs to convince ordinary people and security-conscious celebrities to stay, rather than persuading venture capitalists and captive tech journalists of the brilliance of his grandiose ideas, all while trying to snooker everyone into believing that the pay system will address the problems with Twitter rather than the problems built into Elmo’s purchase of Twitter.
Elmo loathes precisely the people he needs most right now, and he loathes them, in part, because they just saw him make an epically shitty business deal, a deal so epically shitty, in part, because Elmo wanted to prevent anyone from looking at him too closely. His response to that is to invite their complaints, so long as they pay $8 to make them.
It’s a con, but for some reason Elmo thinks the people who just saw him get fleeced will fall for it.
Update: One thing I didn’t provide enough focus on in this is that — as Drew in Bronx notes — Elmo really didn’t have a choice just to pay $1 billion to get out of the deal because his other DE-based property (eg, in Tesla) could have been used to fulfill his obligations. Once he was convinced he would lose at trial, he was stuck.
I agree this is a forced marriage. But to be clear, there was absolutely no way that Musk was going to get out of it once he signed the contract. Delaware Chancery Court is its own special thing, and Musk got outlawyered at the outset because of his own impulsiveness. The (chief) Chancellor in Delaware is brilliant & tough and has no pity for white shoe law firms having to work long hours on short schedules. Also, since Tesla is a Delaware corporation, once a judgement was entered, if it wasn’t honored she would simply seize Musk’s shares in Tesla to satisfy it-no recourse for Elmo.
Update: This account of how dysfunctional Twitter has been since Elmo took over is worth reading in full, especially the description of “psychological warfare” in lieu of management.
One Blind post from a Twitter worker, viewed by The Post on Wednesday, said simply, “This level of silent treatment is totally unprofessional.” Another Twitter employee replied, “It’s not silent treatment it is psychological warfare.”