Scott Bessent’s Imaginary Friends
A week ago, Scott Bessent attempted to calm a bunch of bankers by describing that he would take a lead role in negotiations with 70 countries in the wake of Trump’s tariff flip-flops.
He claimed the US still has things called “allies” who would be willing to reach quick deals that would allow him to isolate China.
Bessent said there was great interest in negotiating with the U.S. to lower tariffs, noting that Trump had already spoken with the leaders of Japan and South Korea, and U.S. officials would meet with a delegation from Vietnam on Wednesday.
“I think … at the end of the day that we can probably reach a deal with our allies, with the other countries that have been … good military allies and not perfect economic allies. And then we can approach China as a group,” Bessent said.
He added that the sweeping reciprocal tariffs announced by Trump last week represented a ceiling for tariffs if countries didn’t retaliate, but China had not heeded that advice.
“In terms of escalation, unfortunately, the biggest offender in the global trading system is China, and they’re the only country who’s escalated,” Bessent said.
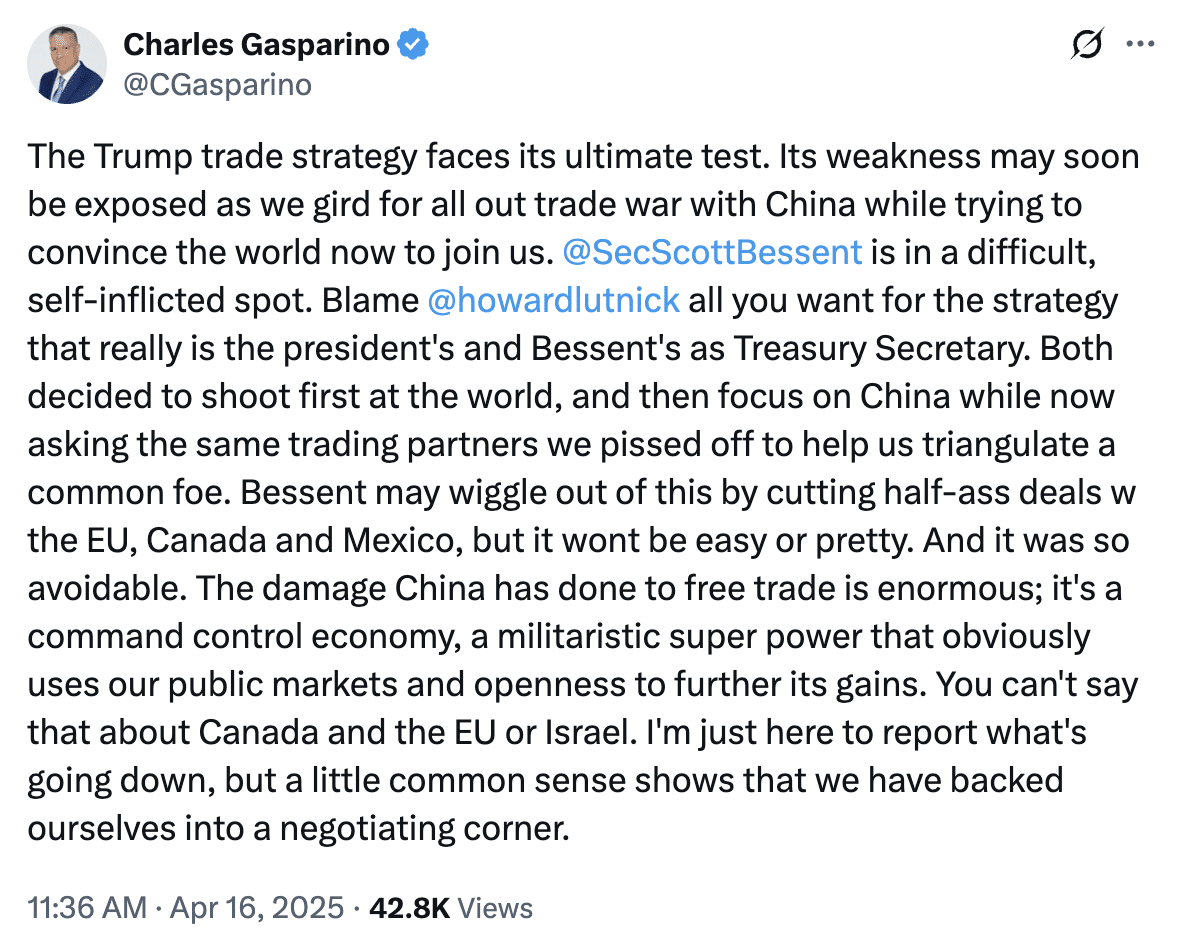
Bessent is still trying to pitch that PR line — that he has a plan — as in this WSJ article (which among other things, suggests Bessent only came up with this thing he fancies is a “strategy” on April 6, after Trump had already started destroying American credibility).
The Trump administration plans to use ongoing tariff negotiations to pressure U.S. trading partners to limit their dealings with China, according to people with knowledge of the conversations.
The idea is to extract commitments from U.S. trading partners to isolate China’s economy in exchange for reductions in trade and tariff barriers imposed by the White House. U.S. officials plan to use negotiations with more than 70 nations to ask them to disallow China to ship goods through their countries, prevent Chinese firms from locating in their territories to avoid U.S. tariffs, and not absorb China’s cheap industrial goods into their economies.
Those measures are meant to put a dent in China’s already rickety economy and force Beijing to the negotiating table with less leverage ahead of potential talks between Trump and Chinese President Xi Jinping. The exact demands could vary widely by nation, given their degree of involvement with the Chinese economy.
[snip]
One brain behind the strategy is Treasury Secretary Scott Bessent, who has taken a leading role in the trade negotiations since Trump announced a 90-day pause on reciprocal tariffs for most nations—but not China—on April 9.
Bessent pitched the idea to Trump during an April 6 meeting at Mar-a-Lago, the president’s club in Florida, said people familiar with the discussion, saying that extracting concessions from U.S. trading partners could prevent Beijing and its companies from avoiding U.S. tariffs, export controls and other economic measures, the people said.
The tactic is part of a strategy being pushed by Bessent to isolate the Chinese economy that has gained traction among Trump officials recently. Debates over the scope and severity of U.S. tariffs are ongoing, but officials largely appear to agree with Bessent’s China plan.
It involves cutting China off from the U.S. economy with tariffs and potentially even cutting Chinese stocks out of U.S. exchanges. Bessent didn’t rule out the administration trying to delist Chinese stocks in a recent interview with Fox Business.
Still, the ultimate goal of the administration’s China policy isn’t yet clear.
Bessent has also said there is still room for talks on a potential trade deal between the U.S. and China. Such talks would have to involve Trump and Xi.
In the time that Bessent has been pursuing this “strategy” to make deals with our “allies” that will isolate China, Xi Jinping had a showy appearance in Vietnam, where he posed as the guardian of “the multilateral trading system, … the stability of the global industrial and supply chains, and … the international environment for open cooperation.”
Xi also urged strengthening coordination and cooperation through regional initiatives such as the East Asia Cooperation and the Lancang-Mekong Cooperation, the ministry said, citing an article by the Chinese leader published in Vietnam media.
He called such efforts necessary to “inject more stability and positive energy into a chaotic and intertwined world”.
“There are no winners in trade wars and tariff wars, and protectionism has no way out,” Xi said, without mentioning the U.S. specifically.
“We must firmly safeguard the multilateral trading system, maintain the stability of the global industrial and supply chains, and maintain the international environment for open cooperation,” he said.
Last week, China sought to get ahead of U.S. negotiators, holding video calls with the EU and Malaysia, which is chairing ASEAN this year, as well as Saudi Arabia and South Africa, by way of reaching out to Gulf countries and the Group of 20 and BRICS nations.
And Trump has continued to destroy two important American markets that foster the kinds of friendship Bessent plans to exploit: tourism …
… And education:
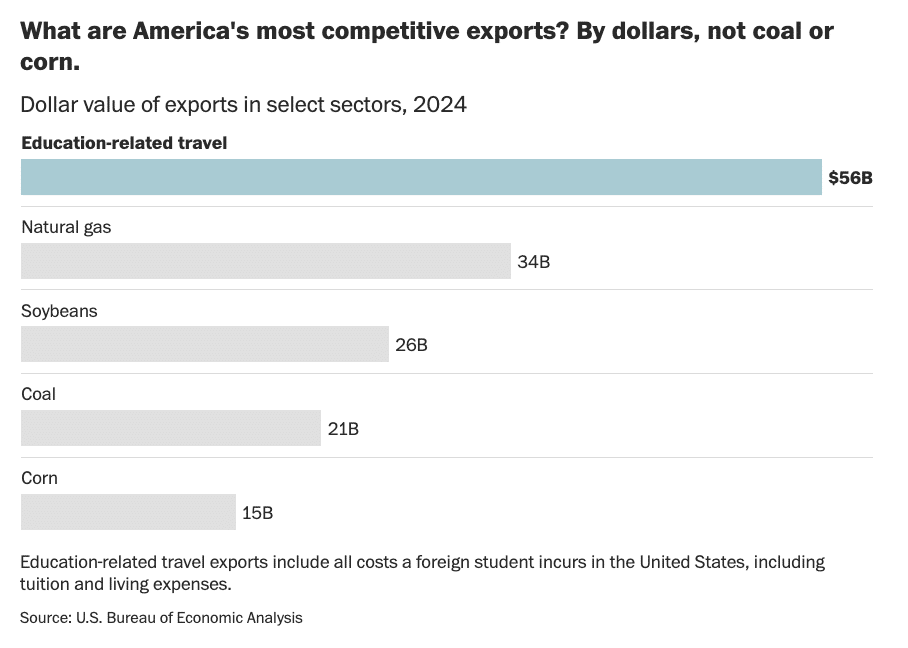
President Donald Trump says he wants to reduce our trade deficit. Yet he’s destroying one of our winningest exports: higher education.
Colleges and universities are among America’s most competitive international exporters. In dollar terms, last year, the United States sold more educational services to the rest of the world than it sold in natural gas and coal combined.
We also run a huge trade surplus in this sector, meaning that foreigners buy much more education from the United States than Americans buy from other countries. In the 2022-2023 school year, more than three times as many international students were enrolled in the United States as there were American students studying abroad. Translated to cash: Our education-services trade surplus is larger than the trade surplus in the entire completed civilian aircraft sector.
Why? Regardless of what Trumpland claims, America is really, really good at higher education.
Sure, even in spite of the damage Trump has caused to US credibility, the US retains a lot of ways to coerce its, um, friends and allies. Trump and Bessent will have a showy meeting with Japan today — a Japan that might be behind the recent US bond sell-off.
But to get just a sense of the degree to which a lot of US coverage treats the US as the sole protagonist of this story, compare this really fascinating interview with Ursula Von der Leyen.
Sure, like US sources, she brags about the friends that keep calling, coyly denying she’s now the leader of the free world while assuming that mantel.
ZEIT: You have just given the question of whether you are the new leader of the Western world a wide berth. But don’t you have to accept that Europe – the EU, with you at its head – has recently become the most important guarantor of Western values in the world?
Von der Leyen: The West as we knew it no longer exists. The world has become a globe also geopolitically, and today our networks of friendship span the globe, as you can see in the debate about tariffs. A positive side effect is that I am currently having countless talks with heads of state and government around the world who want to work together with us on the new order. This is true from Iceland to New Zealand, from Canada to the United Arab Emirates, as it is for India, Malaysia, Indonesia, Philippines, Thailand, Mexico, and South America. Right now, I could have these conversations 24 hours a day. Everyone is asking for more trade with Europe – and it’s not just about economic ties. It is also about establishing common rules and it is about predictability. Europe is known for its predictability and reliability, which is once again starting to be seen as something very valuable. On the one hand, this is very gratifying; on the other hand, there is also of course a huge responsibility that we have to live up to.
But then, amid questions about whether Europe — the lever that Bessent imagines he’ll use against China — remains friends with the US, Von der Leyen describes “reality [as] a strong ally.”
ZEIT: You have said that you are still friends with America. The problem is, of course, that the Americans are not friends with themselves. Most don’t seem to like Europe very much either. So, what is the US: a friend, a former friend, an opponent?
Von der Leyen: I’m not a fan of these kinds of classifications. There are millions of transatlantic friendships and economic, private and cultural ties that have grown over decades, and you can’t put a label on them. Right now, our relationship with each other is complicated. What is crucial in this situation is that we Europeans know exactly what we want and what our goals are. So, then we are very well placed to deal with the Americans, because they are pragmatic and open and understand clear language well.
ZEIT: The tariff conflict with the US seems to escalate and abate, and we have to wonder what on earth the basis for the negotiations is.
Von der Leyen: Reality is a strong ally. I keep pointing out how much prosperity on both sides of the Atlantic has been created by trade and that tariffs are actually like taxes on businesses and consumers. There are four points that are important to us. The first is that we are seeking to negotiate a solution. In parallel to the negotiations, we are developing countermeasures that focus on trade in both goods and services. All options are on the table. The second point is that we must be very vigilant that Chinese goods do not flood our market now because of the trade war between the US and China. So, we have protective measures in place there. The third point is that we need to build new partnerships and establish broader trade relations. The fourth point is that we need to get rid of the barriers in the single market and deepen and harmonise it.
Then, after reiterating a threat against US digital services that you should click through to read, Von der Leyen contrasts European solidarity with America’s bro culture, the same bro culture that aims to destroy US universities and tourism.
Von der Leyen: Yes, I think people have realised that in times of crisis, solidarity within a strong community is something truly precious, and has helped everyone navigate serious crises better. So whenever we overcome a crisis, this is also a victory for Europe and the European ideal. May I sing Europe’s praises?
ZEIT: Absolutely. To my knowledge, self-exaltation isn’t banned under the European Constitution.
Von der Leyen: Europe is still a peace project. We don’t have bros or oligarchs making the rules. We don’t invade our neighbours, and we don’t punish them. On the contrary, there are twelve countries on the waiting list to become members of the European Union. That’s about 150 million people. In Europe, children can go to good schools however wealthy their parents are. We have lower CO2 emissions, we have higher life expectancy. Controversial debates are allowed at our universities. This and more are all values that must be defended, and which show that Europe is more than a union. Europe is our home. And people know that, people feel that.
There is posturing all around. But Von der Leyen looks so much more like a grown-up than Scott Bessent and his imaginary friends.
It’s not just me saying that.
Even some of Trump’s closest friends question whether Trump and Bessent have any.
While both equally destructive, Trump’s efforts to destroy America’s educational and scientific leadership are at odds with his attempt to gain some advantage out of destroying global trade.
As a result, Donald Trump has left poor Scott Bessent with increasingly imaginary friends.