How to Think about the Hunter Biden “Laptop”
As noted, yesterday the summary FBI witness in the Hunter Biden trial, Erika Jensen, testified that she did not do an analysis to find out whether any of the files on the laptop attributed to Hunter Biden, “had been tampered with, added to, or subtracted?” She also testified that, as someone who had, “a small basis of my understanding of how [FBI’s digital forensics experts] work” and having not done such an analysis, had not “seen any evidence whatsoever from the data [she] reviewed from [the] laptop to suggest that there was tampering”
Her job was not to do such an assessment. Her job was to do a summary of a very narrow cherrypick of files prosecutors asked her to summarize.
Indeed, her further testimony revealed how useless her opinion on the laptop is. Aside from matching the laptop serial number with one of at least seven laptops Hunter had used in the two years leading up to its delivery to John Paul Mac Isaac in 2019, the only other validation Jensen described was the emailed receipt JPMI sent Hunter Biden’s publicly identifiable email account on April 17, 2019, which is utterly and completely useless to validate the laptop. Jensen further described that she didn’t review any emails beyond a small handful prosecutors gave her. The file did not include the kind of metadata that would be necessary to assess its usefulness.
The investigative team had never validated whether anything had been added to the laptop before October 20, 2020. No one made an index before handing over the data in discovery to Hunter Biden’s team.
While everyone was focusing on Jensen’s testimony yesterday, Zoe Kestan actually gave far more interesting — and useful, for assessing the reliability of his data — testimony about Hunter’s digital life. She described, for example, that fairly early in their relationship, Hunter “sent me images of his credit card and asked me to call hotels and find somewhere for us to stay that night.” Kasten described that Hunter would get 5-minute codes and send them to her and to drug dealers so they could pull money from his ATM without his ATM card. She described how, sometime around March 2018, the two went together to drop broken devices off at an Apple store, but he left and she finished that process.
We went out for dinner one night, we went to the Apple store because his phone and his computer were broken, and he had to leave in the middle, so I dropped off, and you know, submitted his phone and laptop at the Apple store for him.
She testified he lost maybe 5 or 6 phones in the period they were in a relationship, a period intermittently spanning a year (though I think this might be high). She described trying to locate him once by logging into his bank account (the credentials for which were on her machine) to see where he was withdrawing money from an ATM. She described that he would do his business from her laptop.
This is just one person! And she had the means to totally pwn his life. As, too, undoubtedly, some of the drug dealers who supported his habit.
This is the kind of thing I’ve focused on for a long time. In the depths of his addiction, Hunter Biden exercised almost no digital security, meaning his girlfriends, his drug dealers, his sex workers, and even the junkies he partied with all had easy means to compromise his devices. And every time Hunter lost a device — the five to six Kasten testified to, the seven or so laptops he had over that year, two more phones she wouldn’t have known about — every single time, it would present the opportunity for someone to take over his digital identity as a bunch of right wing Trump supporters have since and tamper with it.
With all that said, I want to address all the reasons why no one should be admitting Hunter Biden’s digital data into a criminal trial without proving the provenance of each message.
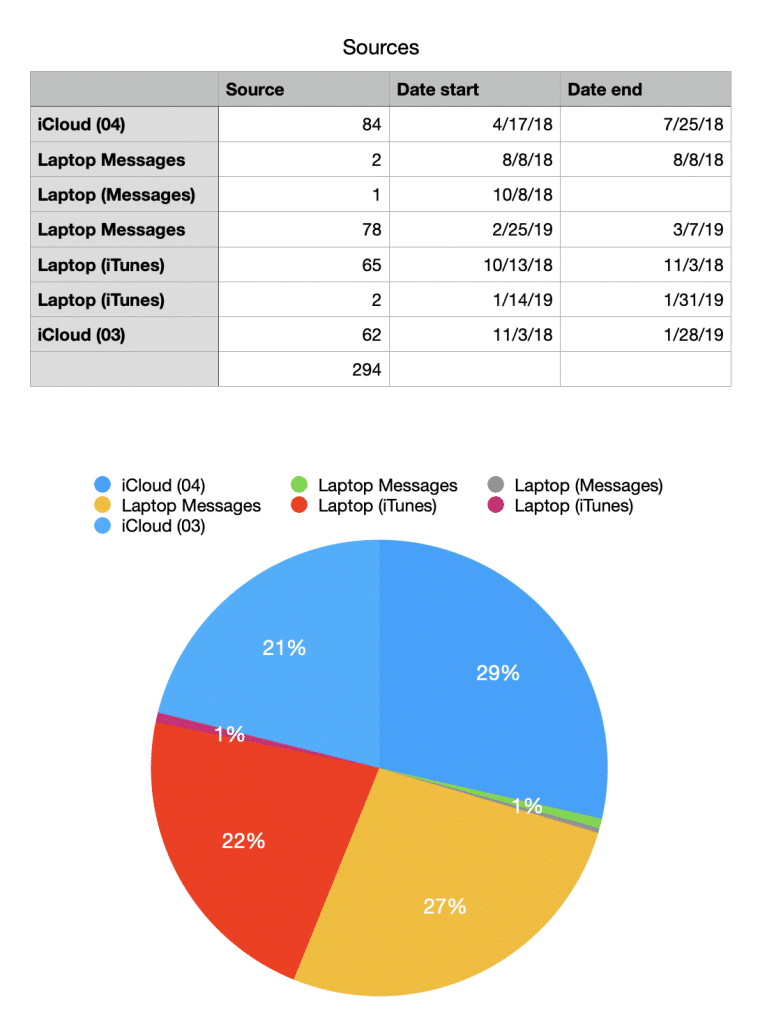
Start with his iCloud. Contrary to widespread belief — belief sown by false claims from prosecutors parroted by credulous journalists — it is not true that all the data on the laptop was backed up to Hunter’s iCloud account.
As I have shown, only half the messages admitted in the trial came from one of two device backups saved to iCloud (these numbers are based off an early draft of the summary).
But there’s a mistaken belief that everything on his iCloud had to be authentic.
That’s because people like Kasten — and people who undoubtedly have a lot less affection for Hunter Biden — have devices that include the login data for Hunter’s iCloud or for phones that were set to back up automatically to iCloud. People with his devices might also be able to access his two main Gmail accounts, his RosemontSeneca one (which frequently suffered what Google believed to be compromises but which might just be Hunter trying to get in), or the droidhunter account he used for adult entertainment (which was accessed by a burner phone in a period when the droidhunter account had access to his iCloud during the period his digital life was packed onto to the laptop that would end up at the FBI).
The reason Hunter’s cloud data was vulnerable to tampering stems from the way he kept his own — and, per Kasten, his associates’ — laptops. We know from the hard drives shared publicly that that laptop included means to access Hunter’s iCloud, an iPad backed up exclusively to the laptop, the phone from which the most important texts used in his trial were extracted (protected by password), and the cookies and passwords to get into much of the rest of his digital life.
What everyone knows as the [multiple hard drives] copied from the laptop is better thought of as a set of a significant chunk of Hunter’s digital activity (much of it unavailable elsewhere), as well as keys that a sophisticated actor could use to access what was stored in the cloud.
And a whole lot of dick pics.
If we believe John Paul Mac Isaac, then he delivered that entire package of Hunter Biden’s digital life plus another two laptops,to the Mac Shop on April 12, 2019. (Remember that there’s another laptop in the wild, which purportedly was left at Keith Ablow’s guest cottage during the period some of this data was being assembled.)
Whether you believe that part of the story or not is not actually all that important. Except insofar as it raises the chances that what went into JPMI’s store was packaged up to maximal damage. Except insofar as right wingers and gossip columnists posing as journalists claim it gives them license to do anything they want with the data. Indeed, the way that story has been used as license to do something grotesque is about all that story does, whether true or not.
Which may be the point.
JPMI has made it clear he started snooping long before he claims his terms and conditions gave him property rights over the device (even if that extended to the data on the device, which Hunter’s team argues it does not). JPMI’s claims about what alarmed him enough to reach out the FBI and Congress and Donald Trump’s personal lawyer aren’t backed by the documents on the laptop. JPMI’s claims about what laptops he received that day don’t match the laptop shared with the FBI.
In other words, there are gaping holes all over JPMI’s story, which differs from the FBI’s story about what they did with the laptop in key ways.
And yet, that didn’t lead the FBI to validate the laptop associated with the iCloud account of the (then) former Vice President’s son beyond confirming that some but not all of the data matched what was in Hunter’s iCloud.
Whether you believe JPMI or not, he has copped to giving Rudy Giuliani, members of Congress, and through them, the whole world, the gateway to Hunter Biden’s digital life. There’s no defense of that, and yet virtually the entire DC press corps likes to pretend they’re doing ethical journalism if they whitewash it.
There’s not much, yet, to add to the discussion above of how David Weiss used the laptop. As noted above, the FBI never did real due diligence on this laptop.
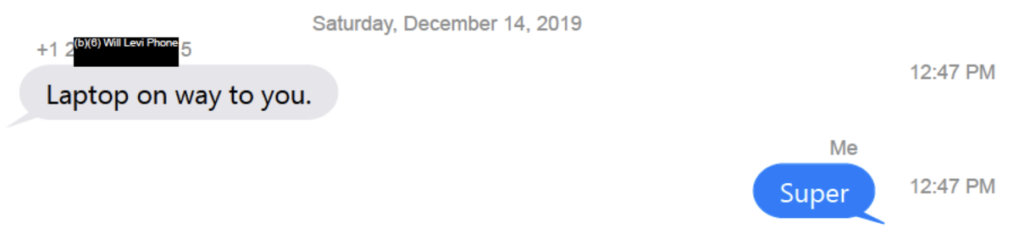
There’s a lot yet to learn — including whether there was a connection between FBI getting a warrant on the laptop and then DOJ Chief of Staff Will Levi’s text to Bill Barr the next day, “laptop on way to you.”
We do know that the (known) December 2019 warrant only permitted the search of the laptop for the three tax crimes charged against Hunter Biden in Los Angeles (which seems inconsistent with the subpoena that described money laundering). The FBI did not have authority to search the laptop or data from Hunter’s iCloud for gun related evidence until December (though Agent Jensen’s summary of the evidence submitted at trial cited earlier warrants for reasons that have not been aired at trial).
The [hard drive containing the contents of the] laptop is not the same thing as the laptop entered into evidence this week.
That’s something about a bazillion trolls who responded to something I said in 2023, about the disseminated laptop: that it had been tampered with.
It has.
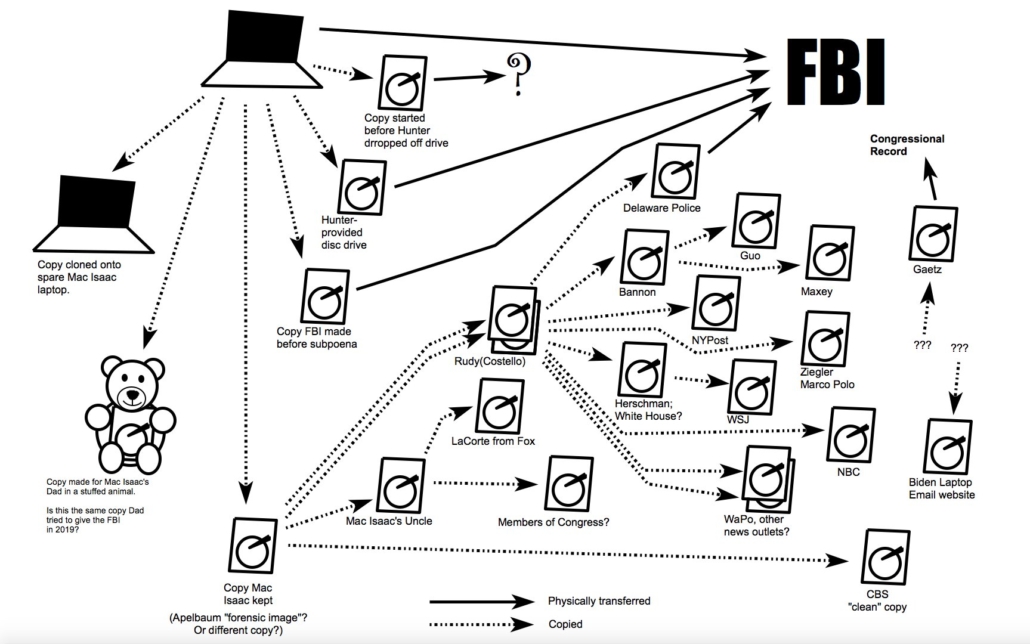
There are known (albeit minor) alterations on the content of the hard drive that Rudy Giuliani shared with the NYPost and, after that, the entire world. There are reportedly more significant compromises, which we might learn about if Rudy’s bankruptcy doesn’t entirely kill Hunter Biden’s lawsuit of Rudy. There was far more significant alteration done on two other sets of data: one, disseminated by Guo Wengui (including some of the files taken down by Twitter in October 2020), and another, released by Jack Maxey.
And there were different public and non-public means of using the hard drives passed on from JPMI to access further Hunter Biden data. Garrett Ziegler, for example, fully admits he compromised the encryption of the iPhone backed up to iTunes on the laptop (though in his response to Hunter Biden’s lawsuit, claims it was legal because the drive he hacked had never belonged to Hunter). Vish Burra is more outspoken about having hacked Hunter Biden.
Many many many of the people who froth over content from the laptop — and journalists who whitewash the hit job against Hunter — don’t know there are multiple versions of altered laptops that relied on multiple means to access (or create) the data.
Many — including many journalists — have just decided Hunter must a horrible person so they are not obligated to care what really happened here.
Hunter Biden’s laptop is not any one thing. It’s not real or authentic or not. It is, rather, the shoddy state of affairs when an entire country enthusiastically exploits the fact that an addict’s digital life was in a permanent state of half-compromise for most if not all of the time of his addiction.
Update: Corrected spelling of Kestan’s last name.
Update: Fixed the super confusing reference about why the FBI didn’t respond differently to the compromise of Biden’s son.