Hal Martin Manages to Obtain a Better Legal Outcome than Reality Winner, But It Likely Doesn’t Matter
I’d like to comment on what I understand happened in a Hal Martin order issued earlier this month. In it, Judge Richard Bennett denied two requests from Martin to throw out the warrants for the search of his house and cell site tracking on his location, but granted an effort to throw out his FBI interrogation conducted the day they raided his house.
Hal Martin did not tweet to Shadow Brokers
The filing has received a bit of attention because of a redaction that reveals how the government focused on Martin so quickly: a Tweet (apparently a DM) he had sent hours before the Shadow Brokers files were first dropped on August 13, 2016.
The passage has been taken to suggest that Martin DMed with Shadow Brokers before he published any files.
That’s impossible, for two reasons.
First, it is inconsistent with Shadow Brokers’ known timeline. Shadow Brokers didn’t set up a Twitter account until after the first batch of files were initially posted. And both the Martin warrant — dated August 25 — and the search — which took place the afternoon of August 27 — preceded the next dump from Shadow Brokers on August 28.
But it’s also impossible for how Bennett ruled.
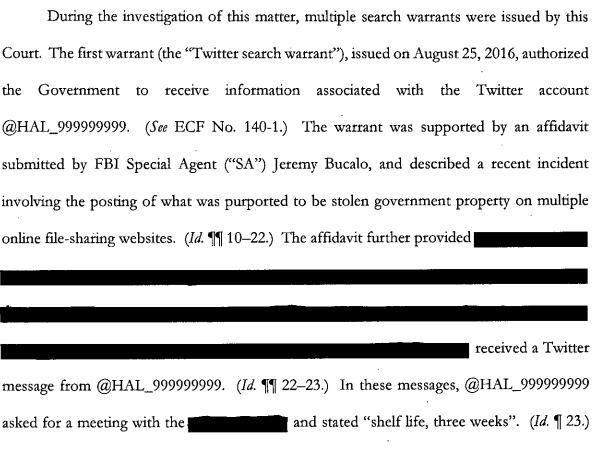
While the underlying motion remains sealed (like virtually everything else in this case), Martin was arguing the warrant used to obtain his Twitter content and later search his house was totally unreasonable under the Fourth Amendment. It’s clear from a letter Martin sent the judge asking for his social media accounts as they actually appeared that he believes the FBI read the content of his Tweet out of context. And the judge actually considered the argument that the search was unreasonable to have merit, and in ruling that the FBI did have substantial basis for the search warrant, conceded that in another context the Tweet would not appear to be so damning.
Significantly, the Fourth Amendment exclusionary rule does not bar the admission of evidence obtained by officers acting in reasonable reliance on a search warrant issued by a magistrate later,found to be invalid. United States v. Leon, 468 U.S. 897,913-14 (1984). The evidence will be suppressed only if (1) the issuing judge was misled by information that the affiant knew or should have known was false, (2) the judge “wholly abandoned” her neutral role, (3) the affidavit was “so lacking in indicia of probable cause as to render official belief in its existence entirely unreasonable,” or (4) the warrant is so facially deficient that no reasonable officer could presume it to be valid. !d. at 923 (citations omitted).
[snip]
In this case, there was a substantial basis for the Magistrate’s fInding of probable cause to issue the search warrant for information associated with the Defendant’s Twitter account. See Upton, 466 U.S. at 728. The affIdavit provides that the Defendant’s Twitter messages [redacted] in which he requested a meeting [redacted] and stated “shelf life, three weeks” – were sent just hours before what was purported to be stolen government property was advertised and posted on multiple online content-sharing sites, including Twitter. (ECF No. 140-1 ~~ 14-23.) Further, and signifIcantly,the affIant averred that the Defendant was a former government contractor who had accessto the information that appeared to be what was purported to be stolen government property that was publicly posted on the Internet. (Id. ~~ 25-27.) Thus, although the Defendant’s Twitter messages could have had any number of innocuous meanings in another setting, these allegations regarding the context of Defendant’s messages provide a substantial basis for the Magistrate’s conclusion that there was a “fair probability” that evidence of the crime of Theft of Government Property, in violation of 18 U.S.c. ~ 641, would be found in information associated with the Defendant’s Twitter account. See Gates, 462 U.S. at 238.
You would never see language like this if Martin really were tweeting with Shadow Brokers, particularly not given the timeline (as it would suggest that he knew of Shadow Brokers before he ever posted). The warrant would, in that case, not be a close call at all. Indeed, the language is inconsistent with Martin’s interlocutor having anything to do with Shadow Brokers.
What appears to have happened is that the FBI totally misunderstood what it was looking at (assuming, as the context seems to suggest, that this is a DM, it would be an account they were already monitoring closely), and panicked, thinking they had to stop Martin before he dropped more NSA files.
Hal Martin got a similar FBI interrogation to Reality Winner’s thrown out
The sheer extent of FBI’s panic is probably what made Martin’s effort to get his FBI interrogation thrown out more successful than Reality Winner’s effort.
Their interrogations were similar. Ten FBI Agents came to Winner’s house, whereas nine SWAT team members, plus eight other FBI Agents, and a few Maryland State Troopers came to Martin’s. In both cases, the FBI segregated the NSA contractors in their home while Agents conducted a search. In Winner’s case, they also segregated her from her pets. In Martin’s case, they segregated him from his partner, Deborah Shaw, and when they did finally let him talk to her, they told Martin “you can’t touch her or any of that stuff.” When the NSA contractors wanted to get something from another part of their home, the FBI accompanied them.
Aside from the even greater number of FBI Agents and that Martin had a partner to be separated from, the biggest difference in Martin’s case is that that they set off a flash-bang device to disorient Martin, and the FBI originally put him face down on the ground and handcuffed him. Those factors, Bennett judged, meant it was reasonable for Martin to believe he was under arrest, and therefore the FBI should have given him a Miranda warning.
That is, on the afternoon of the interrogation, approximately 17-20 law enforcement officers swarmed the Defendant’s property. The Defendant was initially approached by nine armed SWAT agents, handcuffed, and forced to lay on the ground. During the four-hour interrogation, the Defendant was isolated from his partner, his freedom of movement was significantly restricted, and he was confronted with incriminating evidence discovered on his property. In this police dominated environment, a reasonable person in the Defendant’s position would have believed he was not free to leave, notwithstanding the agents’ statements to the contrary.
So unlike Winner, Martin will have his interrogation (in which he admitted to taking files home from his job as a contractor and explained how he did so) thrown out.
But it probably won’t matter.
As a reminder, the FBI charged Martin with taking home 20 highly classified files in February 2017, but they included no allegation that he (willfully) served as a source for Shadow Brokers. It’s possible they know he was an inadvertent source for Shadow Brokers (unlike Nghia Pho, who was likely also a source for Shadow Brokers, they charged Martin for 20 files, larding on the legal exposure; they charged Pho with taking home just one file, while getting him to admit that he could have been charged for each individually). But an earlier opinion in this case ruled that the government only has to prove that by taking hordes of files from of his employers that included National Defense Information, he knowingly possessed the ones he got charged for.
In any case, Martin has already been in jail for 28 months, almost half the amount of time that Pho will serve for doing the same thing, and his trial is not due to start on June 17, a full 34 months after he was arrested. As with Winner, the delay stems from the Classified Information Protection Act process, which ensures that — once the government successfully argues that the secrets in your head make it impossible to release you on bail for fear a foreign intelligence agency will steal those secrets — you serve the equivalent of a sentence before the government even has to prove your guilt.
Again, it may be that Martin unwittingly served as a source for Shadow Brokers. But if he didn’t, then the heavy hand they’re taking with him appears to stem from sheer embarrassment at fucking up with the initial panicked pursuit of him.
Update: Corrected the post to reflect that the search actually preceded the August 28 dump.









![[Photo: National Security Agency, Ft. Meade, MD via Wikimedia]](https://www.emptywheel.net/wp-content/uploads/2017/08/NationalSecurityAgency_HQ-FortMeadeMD_Wikimedia.jpg)