Donald Trump Agrees He Is Living By Barack Obama’s Rules
I’ve been waiting for something like this: the moment where Donald Trump concedes that Barack Obama — Hawaiian birth certificate and all — will play a key role in decisions about his ridiculous claims about hoarding classified documents.
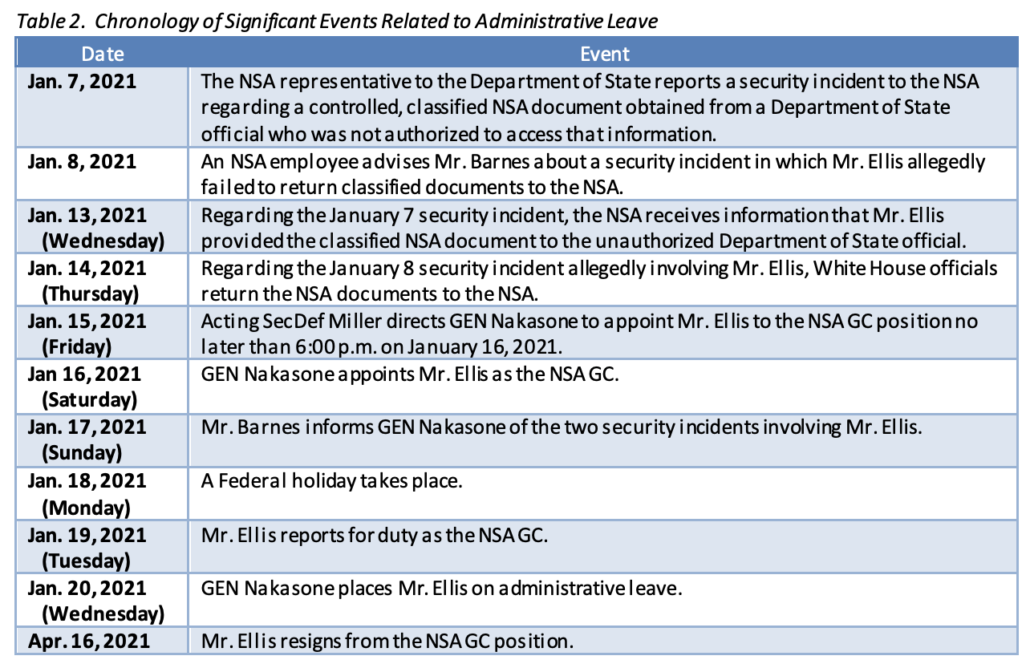
Midway through Trump’s bid to convince Aileen Cannon to reject DOJ’s motion for a stay of her injunction against using the documents marked with classification marks seized from Trump’s beach resort, he notes that the only power he ever had to classify and declassify documents was governed by an Executive Order signed by Barack Obama on December 29, 2009.
The Government does not contest—indeed, it concedes—that the President has broad authority governing classification of, and access to, classified documents. [ECF No. 69 at 10, 18 (quoting Dep’t of Navy v. Egan, 484 U.S. 518, 529 (1988))]. In fact, the Government advocates that “the protection of classified information must be committed to the broad discretion of the agency responsible, and this must include broad discretion to determine who may have access to it.” [ECF No. 69 at 18 (quoting Egan, 484 U.S. at 529)]. Congress provided certain parameters for controlling classified information but primarily delegated to the President how to regulate classified information. 50 U.S.C. § 3161. At the same time, Congress exempted the President from complying with such requirements. See id. § 3163 (“Except as otherwise specifically provided, the provisions of this subchapter shall not apply to the President . . .”).
President Obama enacted the current Executive Order prescribing the parameters for controlling classified information in 2009. See Exec. Order 13526 (Dec. 29, 2009). That Executive Order, which controlled during President Trump’s term in office, designates the President as an original classification authority. See id. § 1.3(a)(1). In turn, the Executive Order grants authority to declassify information to either the official who originally classified the information or that individual’s supervisors—necessarily including the President. § 3.1(b)(1), (3). Thus, assuming the Executive Order could even apply to constrain a President, cf. 50 U.S.C. § 3163, the President enjoys absolute authority under the Executive Order to declassify any information. There is no legitimate contention that the Chief Executive’s declassification of documents requires approval of bureaucratic components of the executive branch. Yet, the Government apparently contends that President Trump, who had full authority to declassify documents, “willfully” retained classified information in violation of the law. See 18 U.S.C. § 793(e); [ECF No. 69 at 9].7 Moreover, the Government seeks to preclude any opportunity for consideration of this issue.
7 Of course, classified or declassified, the documents remain either Presidential records or personal records under the PRA. [ed: See this post for how Trump debunked this claim. My emphasis]
Donald Trump concedes that Executive Order 13526 governed the classification and declassification of information on December 29, 2009. It continued to govern the classification and declassification of information on January 20, 2017. It continued to govern the classification and declassification of information on January 20, 2021. It continues to govern the classification and declassification of information today.
Donald Trump agrees that he never altered this EO. He agrees that he is bound by it still, unless the lawful President, a guy named Joe Biden, decides to change it.
This is a virtual capitulation to the arguments DOJ is making, including that the classification review of the documents he stole, the review ongoing as we speak, will be determinative of the classification status of those documents.
But it’s also a concession that he is bound by everything in the EO. There’s a whole bunch of things Trump concedes when he concedes that point (including that classified information must be kept secure).
One of those things, however, is that former Presidents — and the propagandists who work for them — still must get waivers to bypass Need to Know restrictions on classified information.
Sec. 4.4. Access by Historical Researchers and Certain Former Government Personnel.
(a) The requirement in section 4.1(a)(3) of this order that access to classified information may be granted only to individuals who have a need to-know the information may be waived for persons who:
(1) are engaged in historical research projects;
(2) previously have occupied senior policy-making positions to which they were appointed or designated by the President or the Vice President; or
(3) served as President or Vice President.
(b) Waivers under this section may be granted only if the agency head or senior agency official of the originating agency:
(1) determines in writing that access is consistent with the interest of the national security;
(2) takes appropriate steps to protect classified information from unauthorized disclosure or compromise, and ensures that the information is safeguarded in a manner consistent with this order; and
(3) limits the access granted to former Presidential appointees or designees and Vice Presidential appointees or designees to items that the person originated, reviewed, signed, or received while serving as a Presidential or Vice Presidential appointee or designee. [my emphasis]
This part of the EO — an EO that Trump, who served but no longer serves as President, agreed he is bound by — does not say that such access must be waived. It says it may be.
May. Not must.
Moreover, this waiver requires that before waiving the Need to Know rule, agency heads first determine, in writing, that giving former Presidents and their propagandists access to classified information, “is consistent with the interest of national security.”
Right there, in the middle of his filing arguing that maybe the classification decisions Joe Biden’s Administration is making right now can be overridden by a Special Master, Donald Trump agrees that the Barack Obama order he says he is bound by means not even he gets access to this information without a waiver, and even then, only if the agency heads that own the information say it won’t make the country less safe.
In his bid to claw back classified information he stole, Donald Trump admits he’s still living by Barack Obama’s rules. And those rules, the rules Trump admits he is bound by, say he can only even access this information if Avril Haines and Paul Nakasone and William Burns and Chris Wray say he can.
Go to emptywheel resource page on Trump Espionage Investigation.



![[Photo: National Security Agency, Ft. Meade, MD via Wikimedia]](https://www.emptywheel.net/wp-content/uploads/2017/08/NationalSecurityAgency_HQ-FortMeadeMD_Wikimedia.jpg)