About the Timing of the Binney Meeting
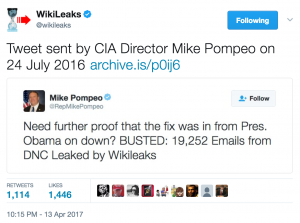
The Intercept is reporting that, on Trump’s orders, Mike Pompeo met with Bill Binney on October 24 to understand his theory arguing that the DNC hack was in fact a leak.
In an interview with The Intercept, Binney said Pompeo told him that President Donald Trump had urged the CIA director to meet with Binney to discuss his assessment that the DNC data theft was an inside job. During their hour-long meeting at CIA headquarters, Pompeo said Trump told him that if Pompeo “want[ed] to know the facts, he should talk to me,” Binney said.
[snip]
Binney said that Pompeo asked whether he would be willing to meet with NSA and FBI officials to further discuss his analysis of the DNC data theft. Binney agreed and said Pompeo said he would contact him when he had arranged the meetings.
I’ve got a few comments about this.
First, I’m particularly intrigued in the timing. on Twitter, Jim Sciutto said Trump had been pushing for Pompeo to meet with Binney for several weeks.
Pompeo took the meeting at the urging of President Trump over weeks. Pompeo told Binney: “The president told me I should talk to you”
I’ve been told the meeting was set up by October 14, which means Trump has been pushing for this meeting for over a month. That dates it to around the same time as reports that Chief of Staff John Kelly was preventing Dana Rohrabacher from meeting Trump to pass on Julian Assange’s claims explaining how the emails he received didn’t come from Russia, though that scheme went back further, to mid-August.
Effectively, though, that means Trump has been trying to find some way to magnify theories that argue culprits besides Russia did the hack. The guy who begged Russia to hack Hillary’s emails in the middle of last summer is looking for some alternative narrative to push, and it’s not clear whether he cares what that narrative is.
Though, as I noted in my post on these theories, now that we know the files Guccifer 2.0 leaked were from Podesta and as-yet unidentified sources, it makes all the arguments focusing on Guccifer beside the point (and disrupts Craig Murray’s claims).
On top of a lot of other implications of this, it shifts the entire debate about whether Guccifer 2.0 was WikiLeaks’ source, which has always focused on whether the documents leaked on July 22 came from Guccifer 2.0. Regardless of what you might conclude about that, it shifts the question to whether the Podesta emails WikiLeaks posted came from Guccifer 2.0, because those are the ones where there’s clear overlap. Russia’s role in hacking Podesta has always been easier to show than its role in hacking the DNC.
It also shifts the focus away from whether FBI obtained enough details from the DNC server via the forensic image it received from Crowdstrike to adequately assess the culprit. Both the DNC and Hillary (as well as the DCCC) servers are important. Though those that squawk about this always seem to miss that FBI, via FireEye, disagreed with Crowdstrike on a key point: the degree to which the two separate sets of hackers coordinated in targeted servers; I’ve been told by someone with independent knowledge that the FBI read is the correct one, so FBI certainly did their own assessment of the forensics and may have obtained more accurate results than Crowdstrike (I’ve noted elsewhere that public IC statements make it clear that not all public reports on the Russian hacks are correct).
In other words, given that the files that Guccifer 2.0 first leaked actually preempted WikiLeaks’ release of those files by four months, what you’d need to show about the DNC file leaks is something entirely different than what has been shown.
Binney and the other skeptics aren’t even arguing the right issue anymore.
Moreover, there’s a newly public detail that may moot two key strands of the argument. Last week the WSJ (here’s the Reuters version) reported that DOJ is thinking of charging 6 Russian officials in the hack of the DNC. I get it. People are skeptical that the FBI has any better data than the NSA (though I know others, outside of the FBI, believe they’ve pinpointed hackers by name). But as part of that story, they described the four districts where the investigation into the hack (as distinct from Mueller’s investigation into the election tampering) live.
The U.S. Justice Department has gathered enough evidence to charge six members of the Russian government in the hacking of Democratic National Committee computers before the 2016 U.S. presidential election, the Wall Street Journal reported on Thursday, citing people familiar with the investigation.
Federal agents and prosecutors in Washington, Philadelphia, Pittsburgh and San Francisco have been cooperating on the DNC investigation and prosecutors could bring the case to court next year, it said.
[snip]
The hacking investigation, conducted by cybersecurity experts, predates the appointment in May of federal special counsel Robert Mueller to oversee the probe of alleged Russian meddling in the 2016 election and possible collusion with President Donald Trump’s campaign.
Mueller and the Justice Department agreed to allow the technical cyber investigation to continue under the original team of agents and prosecutors, the Journal said.
I’m not sure the report is 100% accurate; for example, I know of a non-political witness in the election-related hack being interviewed by Mueller’s people.
But it includes a little-noticed detail that I know to be accurate — and important to rebut the claim that the copying speed claimed by Forensicator requires a conclusion incompatible with Russia carrying out the hack. Part of the investigation is in Philadelphia.
When Reuters first reported a tripartite structure of the investigation in February, it included San Francisco (the Guccifer 2.0 investigation), Pittsburgh (the Russian side, probably focused on known APTs), and DC (the counterintelligence side — though that would significantly be Mueller’s investigation).
Philadelphia was not included. I only know a bit about the Philadelphia side of the investigation, but I do know that part of the investigation is located there because of a server in the district. So one way or another, we know that the FBI is conducting an investigation in an Eastern city as part of the hacking investigation based on the use of a server in the district. That doesn’t necessarily mean they’re investigating Russians. But it means even if you account for a server in the eastern time zone, you still have FBI preparing to charge Russians for the hack.
Which brings us to the last line of the Intercept article.
Binney said that since their meeting, he has not heard from Pompeo about scheduling follow-up meetings with the NSA and FBI.
Granted, it has only been two weeks. But in that time, not even Pompeo’s prodding has made the FBI (more likely) or the NSA (which still has bad blood with Binney) remotely curious about these theories.