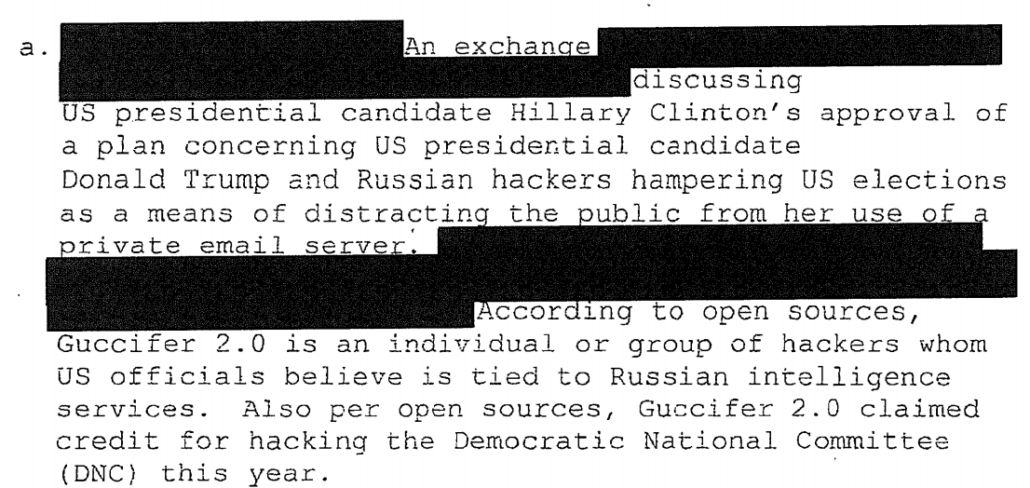
The Guy Investigating the Claimed Politicized Hiring of a Special Counsel Insists that the Hiring of a Special Counsel Cannot Be Political
On Monday, both John Durham and Michael Sussmann submitted their motions in limine, which are filings to argue about what can be admitted at trial. They address a range of issues that I’ll cover in several posts:
Sussmann:
- Asks Judge Cooper to immunize Rodney Joffe or dismiss the case (addressed in this post)
- Asks to prohibit introduction of privilege logs (addressed in an update to this post predicting something similar would happen)
- Argues that Bill Priestap and Trisha Anderson’s notes are inadmissible hearsay and unreliable (this post demonstrates similarities between these notes and those altered in the Mike Flynn docket)
- Asks to exclude allegations about the reliability of the DNS data or claims about Christopher Steele (see this post)
Durham wants to:
- Admit witnesses’ contemporaneous notes of conversations with the FBI General Counsel
- Admit emails referenced in the Indictment and other, similar emails (see this post)
- Admit certain acts and statements (including the defendant’s February 2017 meeting with a government agency, his December 2017 Congressional testimony, and his former employer’s October 2018 statements to the media) as direct evidence or, alternatively, pursuant to Federal Rule of Evidence 404(b)
- Exclude evidence and preclude argument concerning allegations of political bias on the part of the Special Counsel (addressed in this post)
- Admit an October 31, 2016 tweet by the Clinton Campaign
I will link my discussions in serial fashion.
Here’s how John Durham moved to exclude any evidence that his team was ordered to produce results in time for the 2020 election, bullied witnesses, or treated Hillary Clinton as a more dangerous adversary than Russia.
The Government expects that defense counsel may seek to present evidence at trial and make arguments that depict the Special Counsel as politically motived or biased based on his appointment by the prior administration. Notwithstanding the patently untrue nature of those allegations, such matters are irrelevant to this case and would create a substantial danger of unfair prejudice, confusion, and delay. In particular, the government seeks to preclude the defendant from introducing any evidence or making any argument concerning the circumstances surrounding the appointment of the Special Counsel and alleged political bias on the part of the Special Counsel’s Office. Indeed, the defendant has foreshadowed some of these arguments in correspondence with the Special Counsel and others, and their assertions lack any valid basis.
Only relevant evidence is admissible at trial. Fed. R. Evid. 402. The definition of relevance is inclusive, see Fed. R. Evid. 401(a), but depends on the possibility of establishing a fact that “is of consequence in determining the action,” Fed. R. Evid. 401(b). Evidence is therefore relevant only if it logically relates to matters that are at issue in the case. E.g., United States v. O’Neal, 844 F. 3d 271, 278 (D.C. Cir. 2016); see Sprint/United Management Co. v. Mendelsohn, 552 U.S. 379, 387 (2008). The party seeking to introduce evidence bears the burden of establishing relevancy. Dowling v. United States, 493 U.S. 342, 351 n.3 (1990).
Here, the defendant is charged with making a false statement to the FBI General Counsel in violation of 18 U.S.C. § 1001. A jury will have to decide only whether the defendant knowingly and willfully made a materially false statement to the FBI General Counsel. Nothing more, nothing less. Baseless political allegations are irrelevant to the crime charged. See, e.g., United States v. Regan, 103 F. 3d 1072, 1082 (2d Cir. 1997) (claims of Government misconduct are “ultimately separate from the issue of [a defendant’s] factual guilt”); United States v. Washington, 705 F. 2d 489, 495 (D.C. Cir. 1983) (similar). Evidence or argument concerning these issues should therefore be excluded. See Fed. R. Evid. 402; see, e.g., O’Neal, 844 F,3d at 278; United States v. Stone, 19 CR 18 (D.D.C. Sept. 26, 2019) ECF Minute Order (granting the government’s motion in limine to exclude evidence or argument regarding alleged misconduct in the government’s investigation or prosecution of Roger Stone).
The only purpose in advancing these arguments would be to stir the pot of political polarization, garner public attention, and, most inappropriately, confuse jurors or encourage jury nullification. Put bluntly, the defense wishes to make the Special Counsel out to be a political actor when, in fact, nothing could be further from the truth.11 Injecting politics into the trial proceedings is in no way relevant and completely unjustified. See United States v. Gorham, 523 F. 2d 1088, 1097-1098 (D.C. Cir. 1975) (upholding trial court’s decision to preclude evidence relevant only to jury nullification); see also United States v. Rushin, 844 F. 3d 933, 942 (11th Cir. 2016) (same); United States v. Castro, 411 Fed. App’x 415, 420 (2d Cir. 2011) (same); United States v. Funches, 135 F.3d 1405, 1408-1409 (11th Cir. 1998) (same); United States v. Cropp, 127 F.3d 354, 358-359 (4th Cir. 1997). With respect to concerns about jury nullification, this Circuit has opined:
[Defendant’s] argument is tantamount to the assertion that traditional principles concerning the admissibility of evidence should be disregarded, and that extraneous factors should be introduced at trial to become part of the jury’s deliberations. Of course a jury can render a verdict at odds with the evidence and the law in a given case, but it undermines the very basis of our legal system when it does so. The right to equal justice under law inures to the public as well as to individual parties to specific litigation, and that right is debased when juries at their caprice ignore the dictates of established precedent and procedure.
Gorham, 523 F.2d at 1098. Even if evidence related to the defendant’s anticipated allegations had “marginal relevance” to this case (which it does not), the “likely (and presumably intended) effect” would be “to shift the focus away from the relevant evidence of [the defendant’s] wrongdoing” to matters that are, at most, “tangentially related.” United States v. Malpeso, 115 F. 3d 155, 163 (2d Cir. 1997) (upholding exclusion of evidence of alleged misconduct by FBI agent). For the foregoing reasons, the defendant should not be permitted to introduce evidence or make arguments to the jury about the circumstances surrounding the appointment of the Special Counsel and alleged political bias on the part of the Special Counsel.
11 By point of fact, the Special Counsel has been appointed by both Democratic and Republican appointed Attorneys General to conduct investigations of highly-sensitive matters, including Attorneys General Janet Reno, Michael Mukasey, Eric Holder, Jeff Sessions and William Barr. [my emphasis]
Durham stuck the section between an extended section arguing that Judge Christopher Cooper should treat the interlinked investigations — by those working for the Hillary campaign and those, working independently of the campaign, who believed Donald Trump presented a grave risk to national security — into Trump’s ties to Russia as a unified conspiracy and another section asking that Clinton Campaign tweets magnifying the Alfa Bank allegations be admitted, even though the argument to include them is closely related.
Even ignoring how Durham pitches this issue, the placement of this argument — smack dab in the middle of an effort to treat protected political speech he admits is not criminal like a criminal conspiracy — seems like a deliberate joke. All the more so coming from prosecutors who, with their conflicts motion,
stir[red] the pot of political polarization, garner[ed] public attention, and, most inappropriately, confuse[d potential] jurors
It’s pure projection, presented in the middle of just that kind of deliberately polarizing argument. From the moment the Durham team — which relied heavily on an FBI Agent who reportedly sent pro-Trump texts on his FBI phone — tried to enhance Kevin Clinesmith’s punishment for altering documents because he sent anti-Trump texts on his FBI phone, Durham has criminalized opposition to Trump.
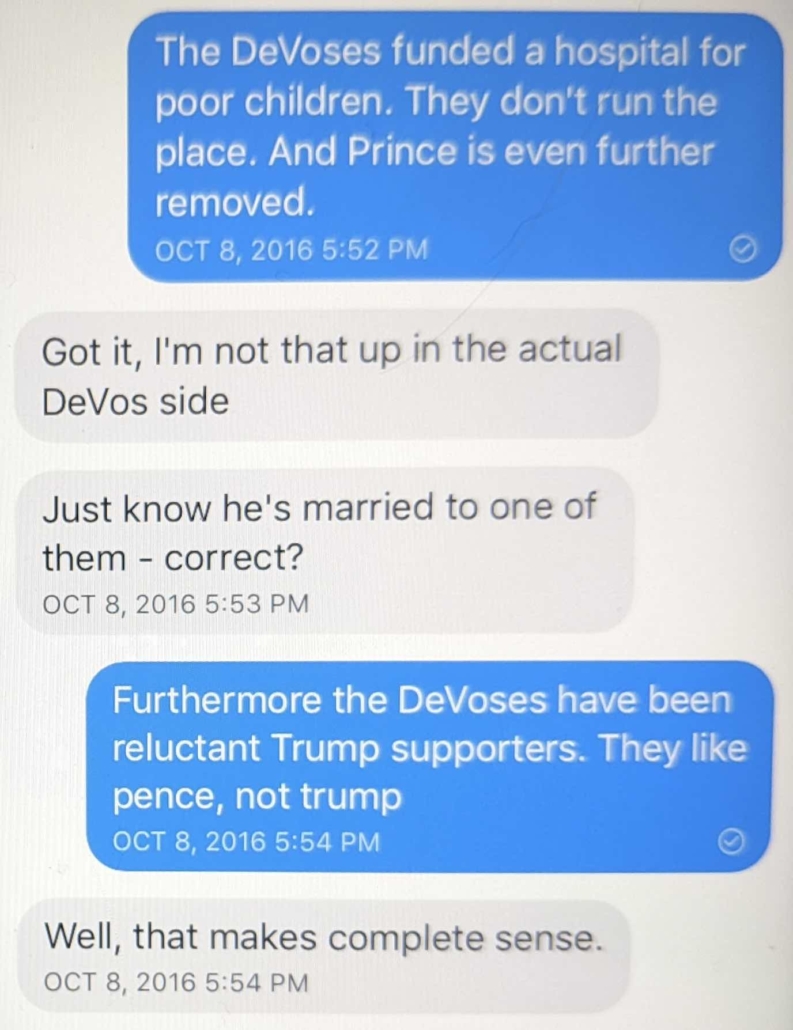
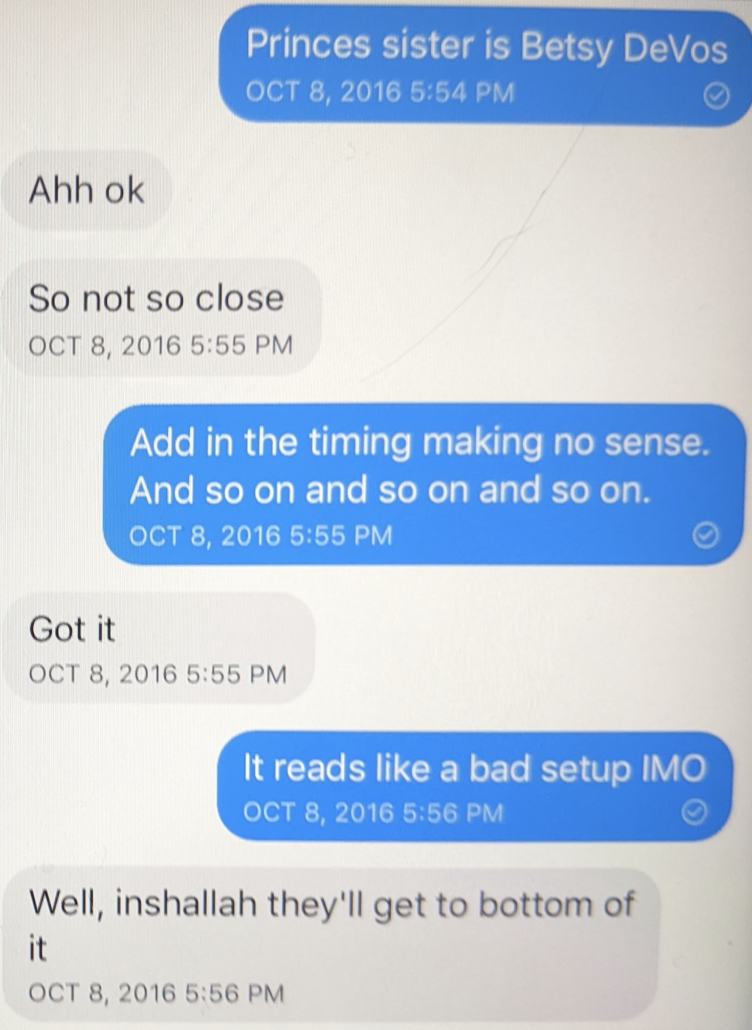
And Durham himself made his hiring an issue by claiming that the guy who misrepresented his conflicts motion by using it to suggest that Sussmann and Rodney Joffe should be executed, Donald Trump, is a mere third party and not the guy who made him a US Attorney.
But it’s also misleading, for multiple reasons.
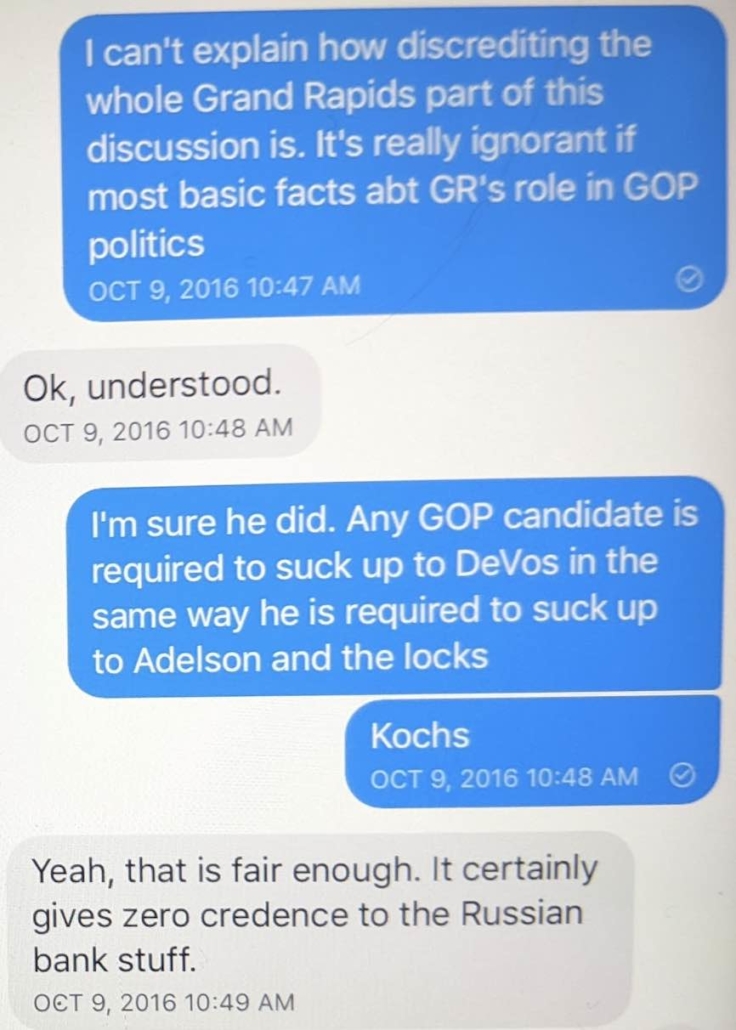
The initial bias in question pertains to covering up for Russia, not helping Republicans
Sussmann’s likely complaints at trial have little to do with the fact that Durham was appointed by a Republican. Rather, a key complaint will likely have to do with the fact that Durham was appointed as part of a sustained campaign to misrepresent the entire set of events leading up to the appointment of his predecessor as Special Counsel, Robert Mueller, by a guy who auditioned for the job of Attorney General based on his claims — reflecting his warped Fox News understanding of the investigation — that the confirmed outcome of that investigation was false.
You cannot separate Durham’s appointment from Billy Barr’s primary goal in returning as Attorney General to undermine the evidence of improper Trump ties to Russia. You cannot separate Durham’s appointment, in the same days as Mueller acquired key evidence in two investigations (the Egyptian bank donation and Roger Stone) that Barr subsequently shut down, from Barr’s attempt to undermine the past and ongoing investigation. You cannot separate Durham’s appointment from what several other DC District judges (Reggie Walton, Emmet Sullivan, and Amy Berman Jackson — the latter, twice) have said was Barr’s improper tampering in the Russian investigation.
That is, Durham was appointed to cover-up Trump’s confirmed relationship with Russia, not to attack Democrats. But in order to cover up for Russia, Durham will, and has, attacked the Democrats who were first victimized by Russia for viewing Russia as a threat (though I believe that Republicans were victimized, too).
That bias has exhibited in the following ways, among others:
- Treating concern about Trump’s solicitation of further hacks by Russia and his confirmed ties to Russian money laundering as a partisan issue, and not a national security issue (something Durham continues with this filing)
- Treatment, in the Danchenko case, of Charles Dolan’s involvement in the most accurate report in the Steele dossier as more damning that the likely involvement of Dmitri Peskov in the most inflammatory reports that paralleled the secret communications with Dmitry Peskov that Trump and Michael Cohen lied to cover up
- Insinuations from Andrew DeFilippis to Manos Antonakakis that it was inappropriate for DARPA to ask researchers to investigate ongoing Russian hacks during an election
- A prosecutorial decision that risks making sensitive FISA information available to Russia that will, at the same time, signal that the FBI won’t protect informants against Russia
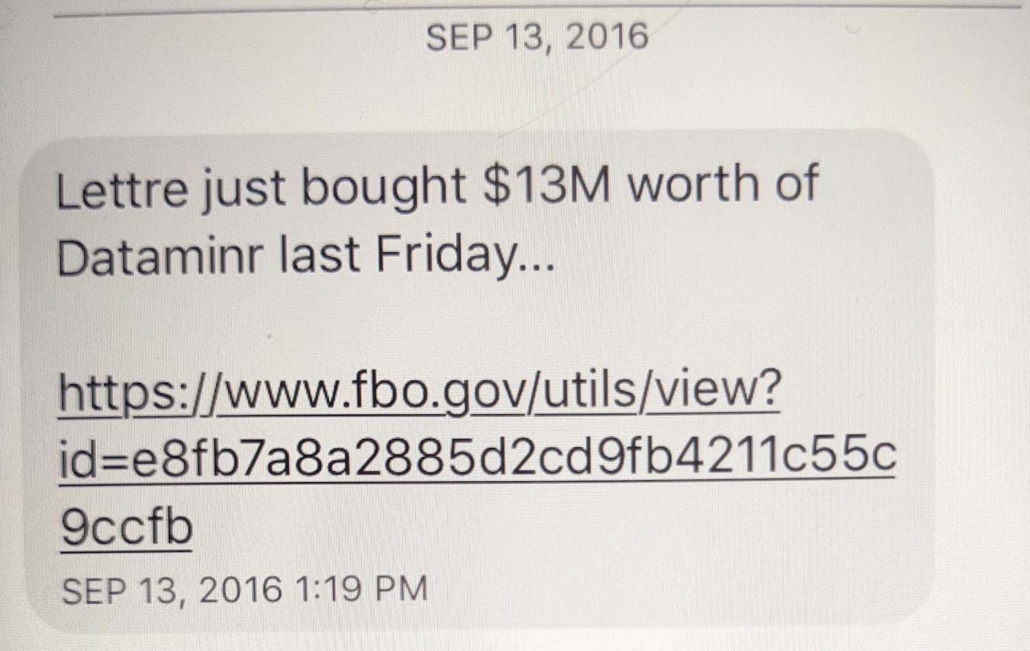
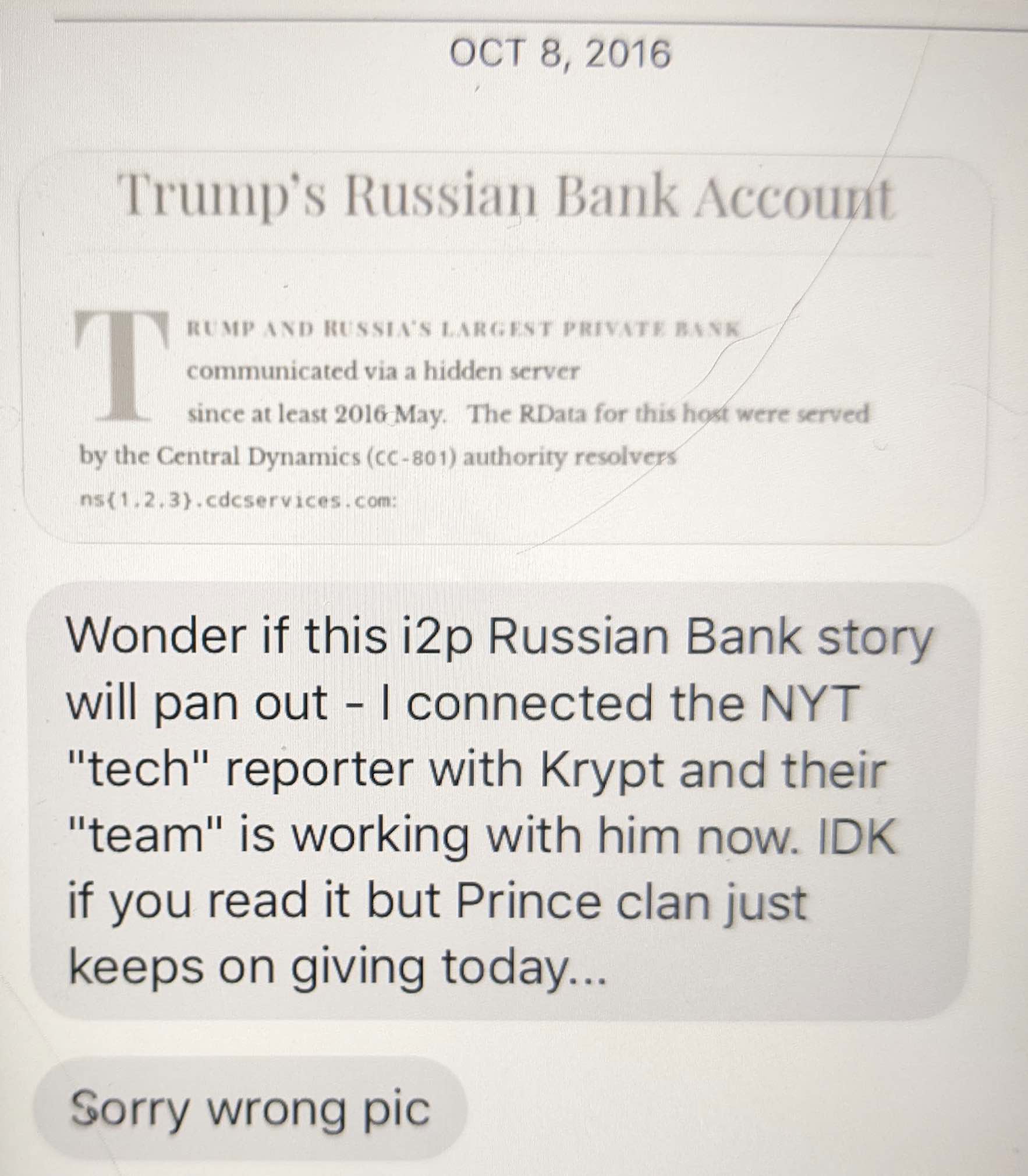
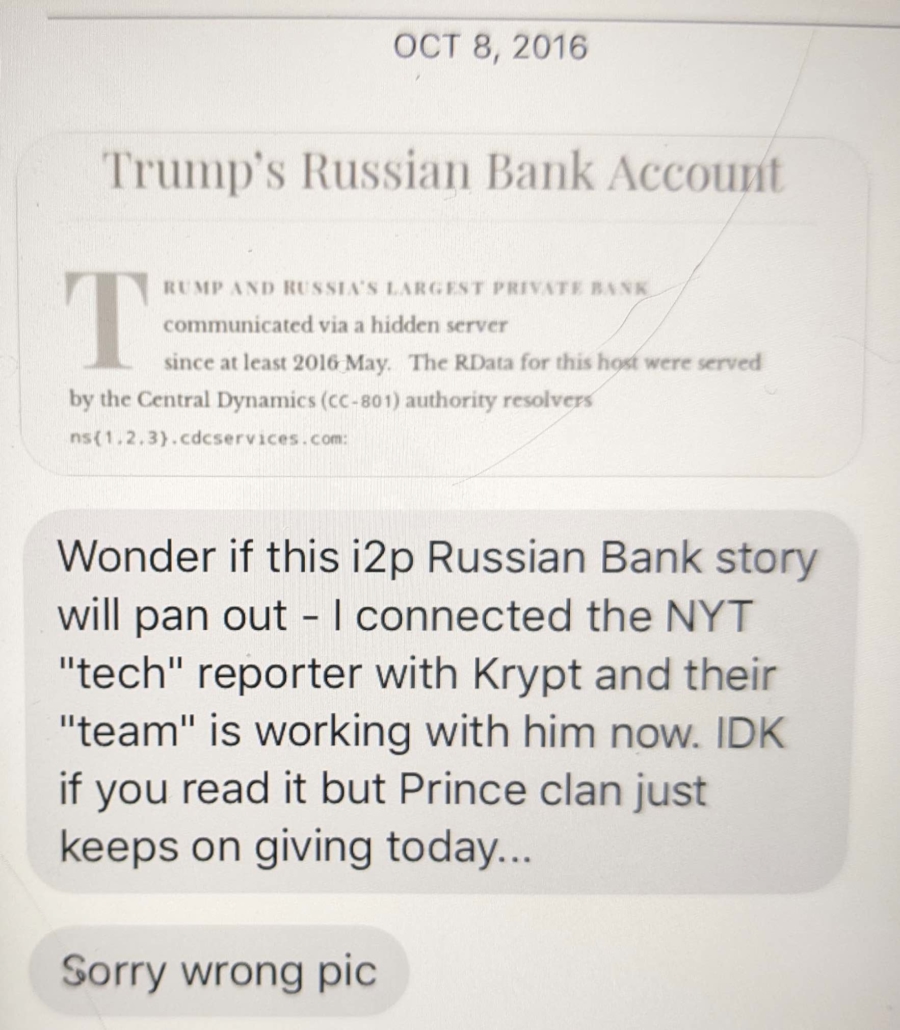
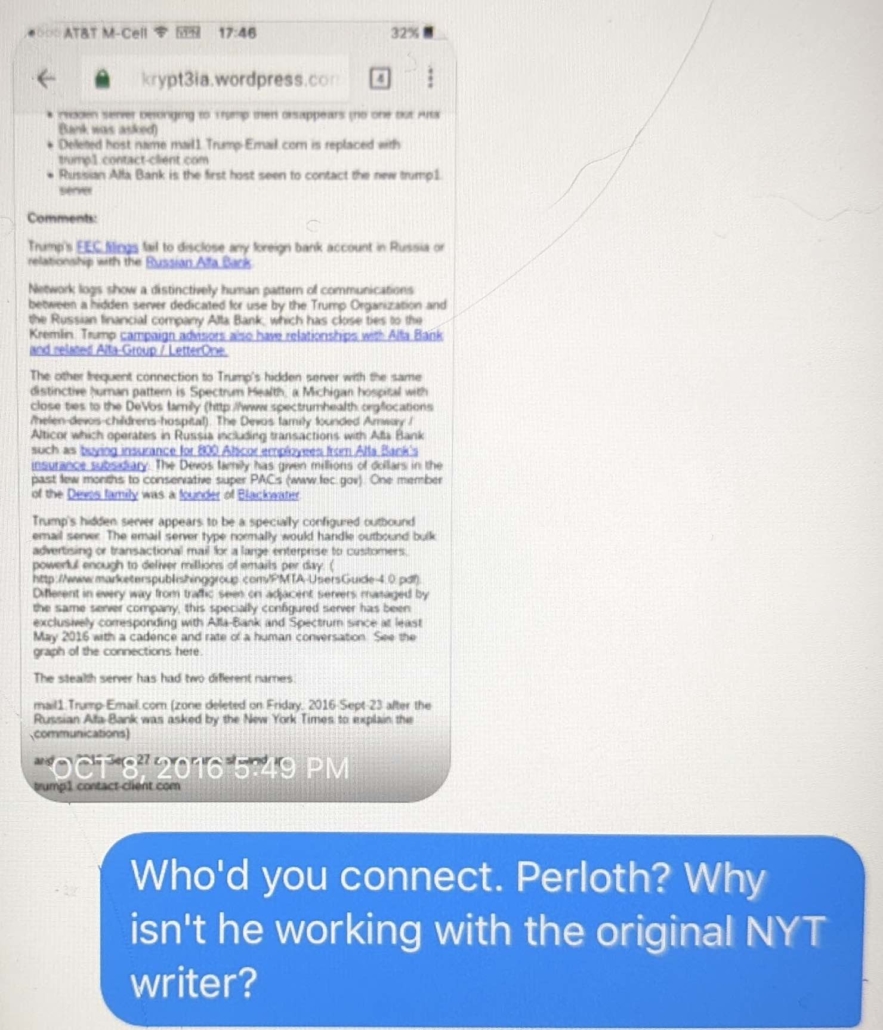
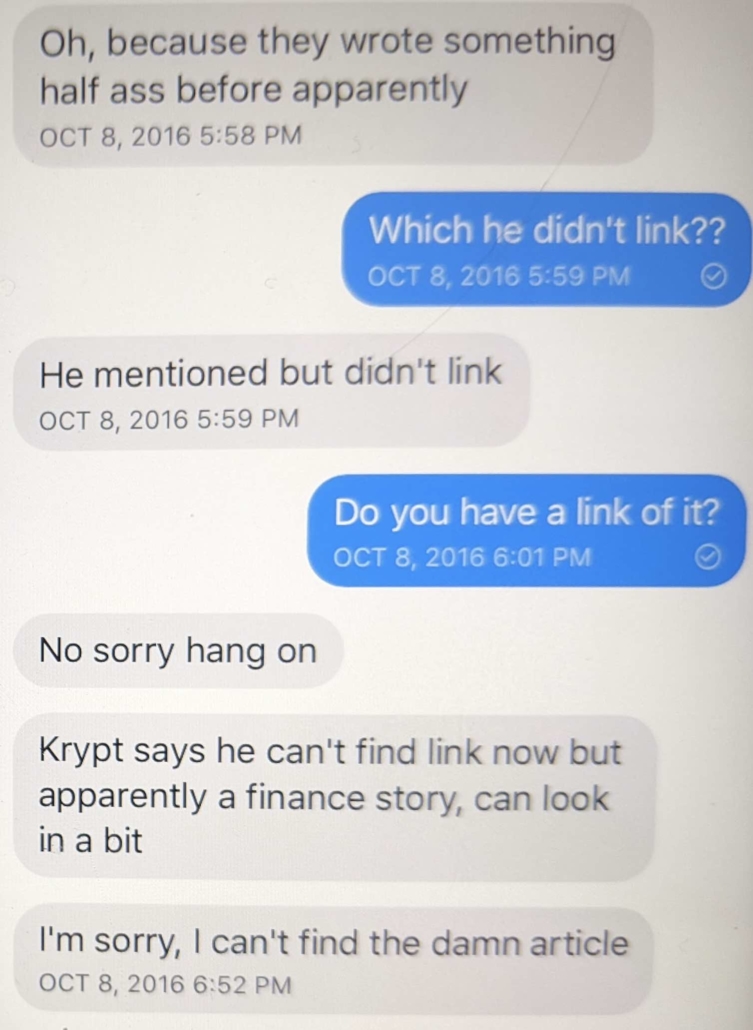
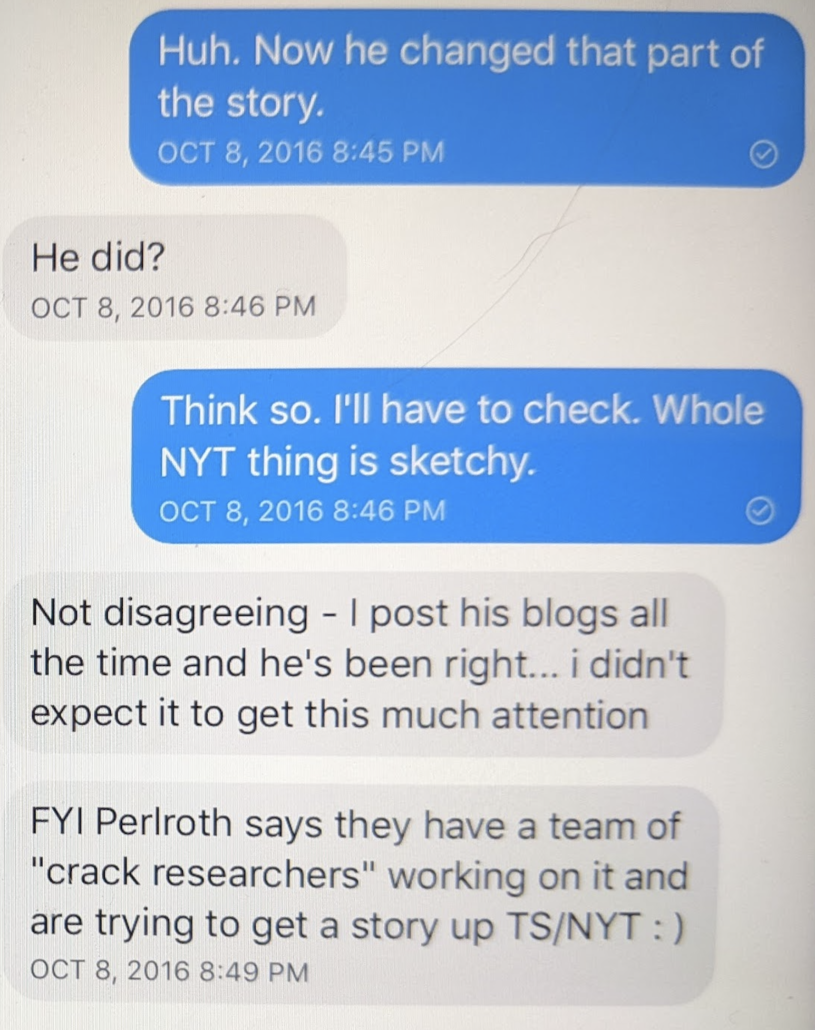
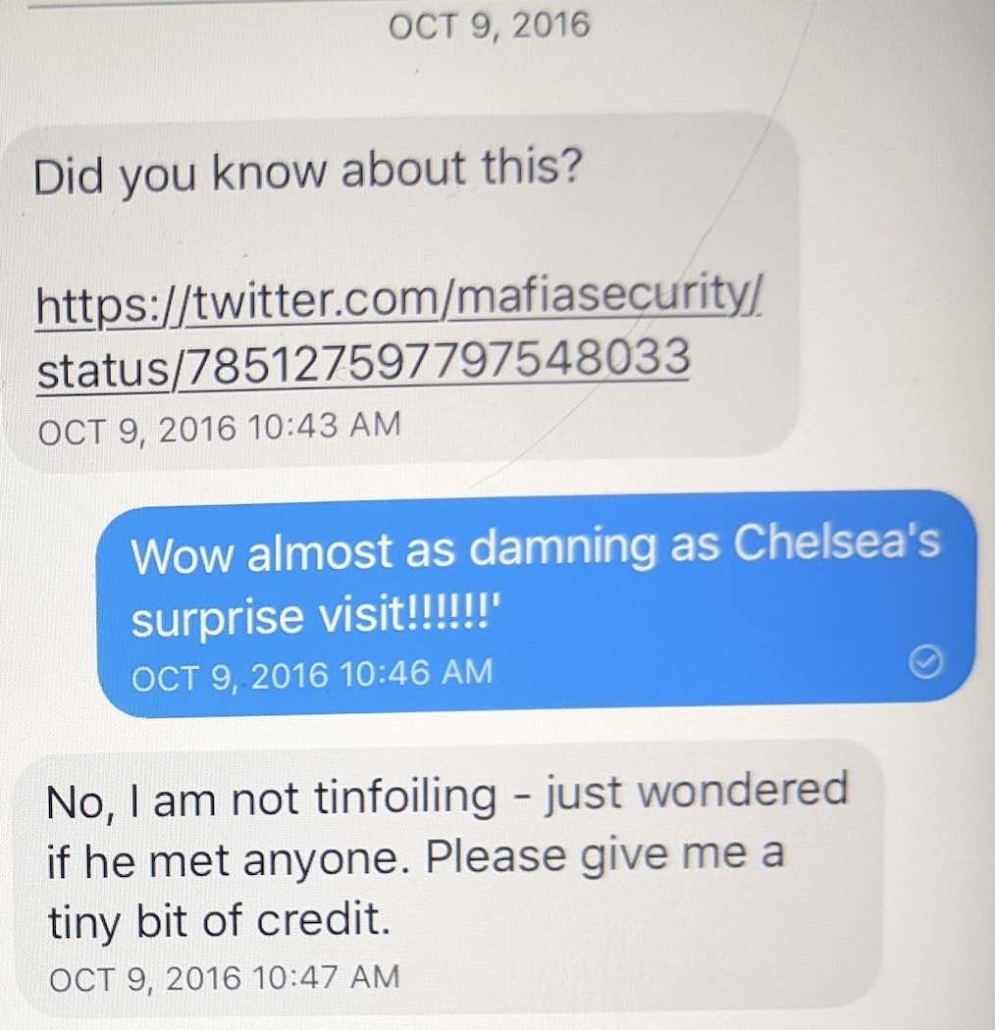
There are other indications that Durham has taken probable Russian disinformation that implicates Roger Stone as instead reliable evidence against Hillary.
Durham’s investigation into an investigation during an election was a key prop during an investigation
Another thing Durham may be trying to stave off is Sussmann calling Nora Dannehy as a witness to explain why she quit the investigation just before the election. Even assuming Durham could spin concerns about pressure to bring charges before an election, that pressure again goes to Billy Barr’s project.
When Durham didn’t bring charges, some of the same documents Durham was reviewing got shared with Jeffrey Jensen, whose team then altered several of them, at least one of them misleadingly, to present a false narrative about Trump’s opponent’s role in the investigation. Suspected fraudster Sidney Powell seems to have shared that false narrative with Donald Trump, who then used it in a packaged attack in the first debate.
This is one of the reasons why Durham’s submission of Bill Priestap’s notes in such a way as to obscure whether those notes have some of the same indices of unreliability as the altered filings in the Mike Flynn case matters.
In other words, Durham is claiming that scrutinizing the same kind of questions that Durham himself has been scrutinizing for years is improper.
The bullying
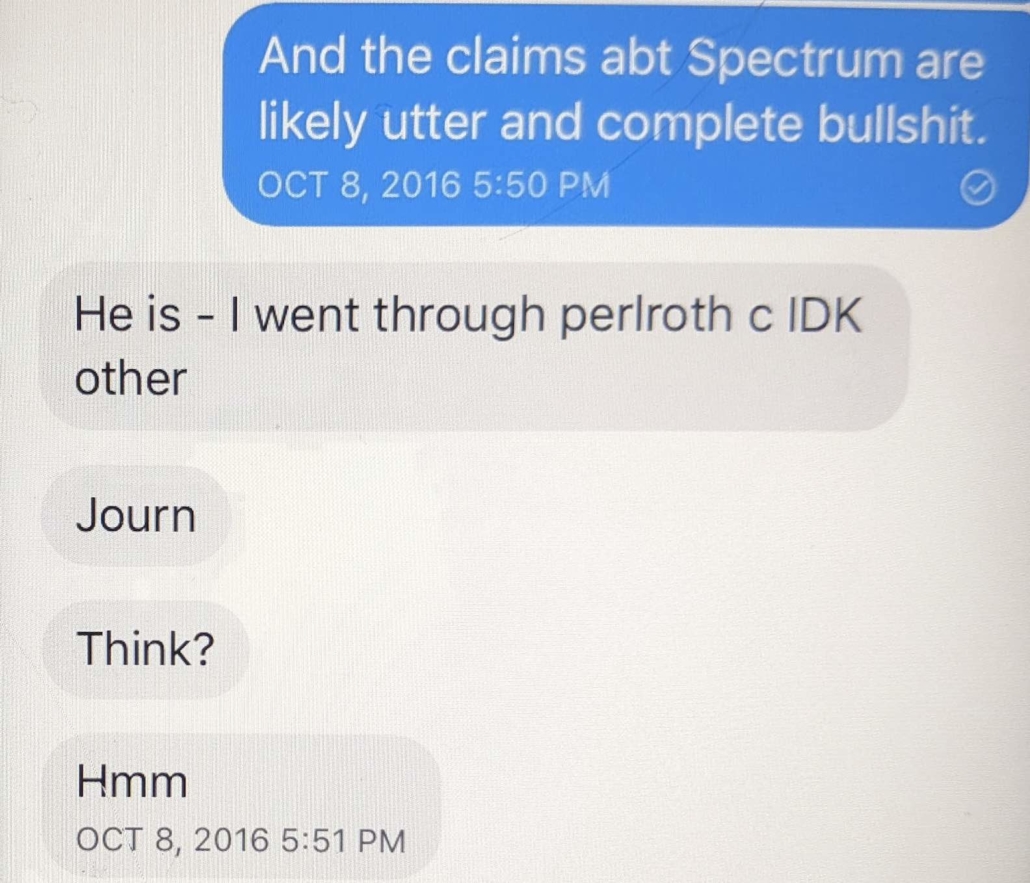
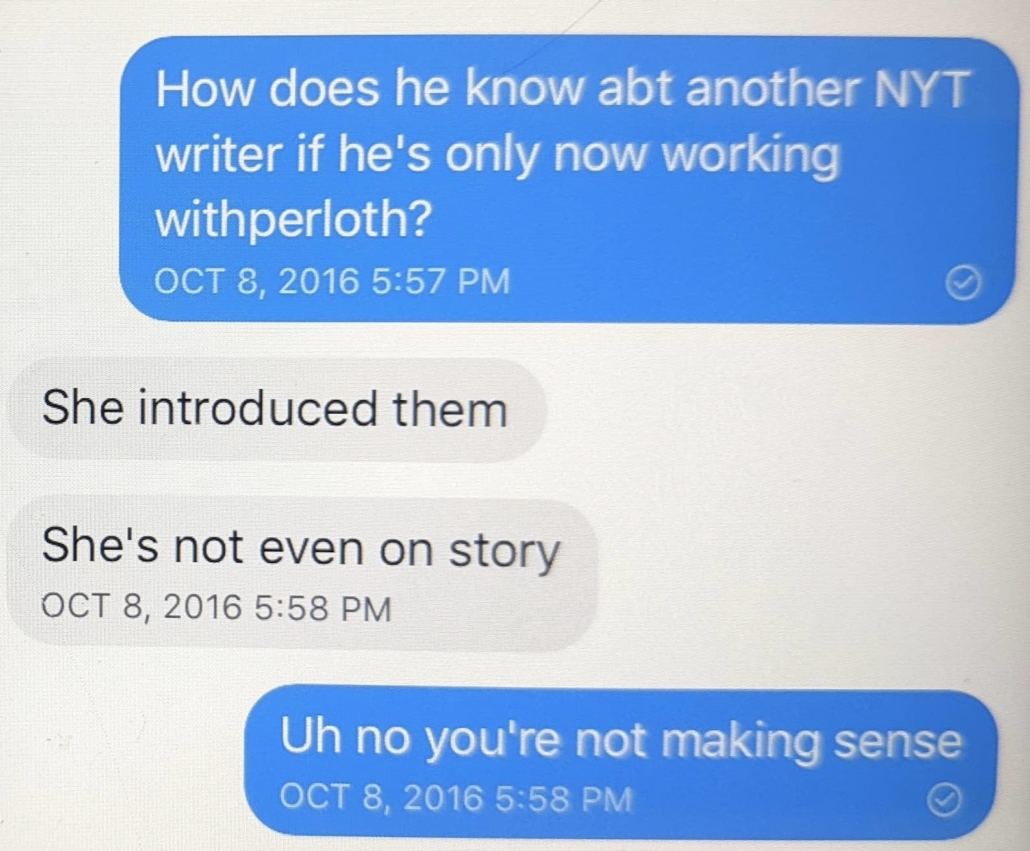
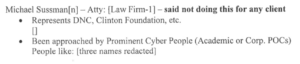
I find it interesting that Durham claims that, “the defendant has foreshadowed some of these arguments in correspondence with the Special Counsel and others,” without citing any. That’s because the only thing in the record is that Sussmann asked for evidence of Durham bullying witnesses to alter their testimony — in response to which Durham provided communications with April Lorenzen’s attorneys.
On December 10, 2021, the defense requested, among other things, all of the prosecution team’s communications with counsel for witnesses or subjects in this investigation, including, “any records reflecting any consideration, concern, or threats from your office relating to those individuals’ or their counsels’ conduct. . . and all formal or informal complaints received by you or others” about the conduct of the Special Counsel’s Office.” Although communications with other counsel are rarely discoverable, especially this far in advance of trial, the Government expects to produce certain materials responsive to this request later this week. The Government notes that it is doing so despite the fact that certain counsel persistently have targeted prosecutors and investigators on the Special Counsel’s team with baseless and polemical attacks that unfairly malign and mischaracterize the conduct of this investigation. For example, certain counsel have falsely accused the Special Counsel’s Office of leaking information to the media and have mischaracterized efforts to warn witnesses of the consequences of false testimony or false statements as “threats” or “intimidation.”
And this set of filings reveals that Durham is still trying to force Rodney Joffe to testify against Sussmann, even though Joffe says his testimony will actually help Sussmann.
In other words, this may be a bid by Durham to prevent evidence of prosecutorial misconduct under the guise of maintaining a monopoly on the right to politicize the case.
Normally, arguments like this have great merit and are upheld.
But by making the argument, Durham is effectively arguing that the entire premise of his own investigation — an inquiry into imagined biases behind an investigation and later appointment of a Special Counsel — is illegitimate.
As we’ll see, what Judge Christopher Cooper is left with is nothing more than competing claims of conspiracy.