That Clinton Tweet Could Lead To a Mistrial (or Reversal on Appeal)
Thanks to those who’ve donated to help defray the costs of trial transcripts. Your generosity has funded the expected costs. If you appreciate the kind of coverage no one else is offering, we’re still happy to accept donations for this coverage — which reflects the culmination of eight months work.
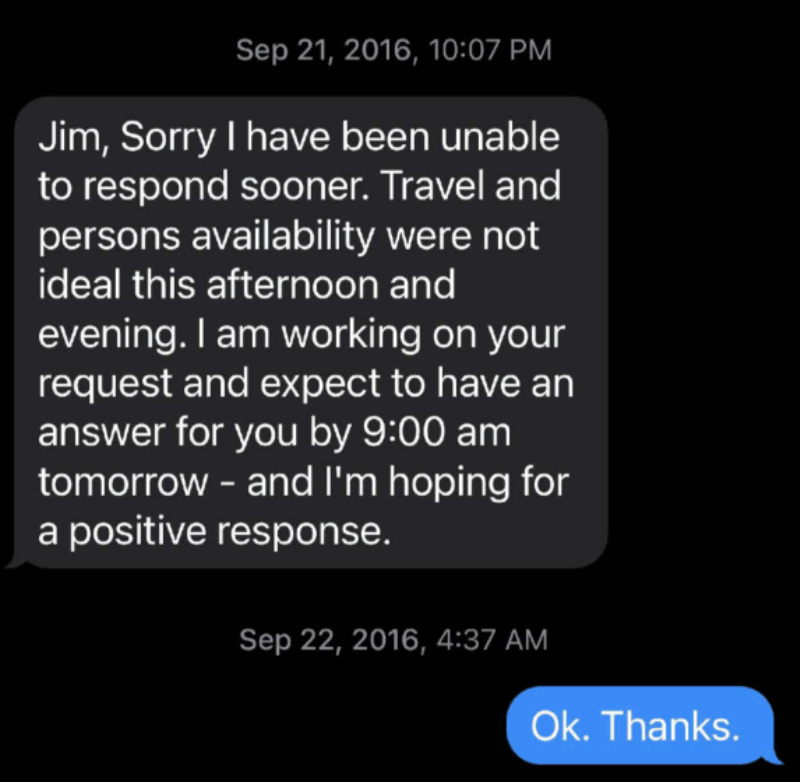
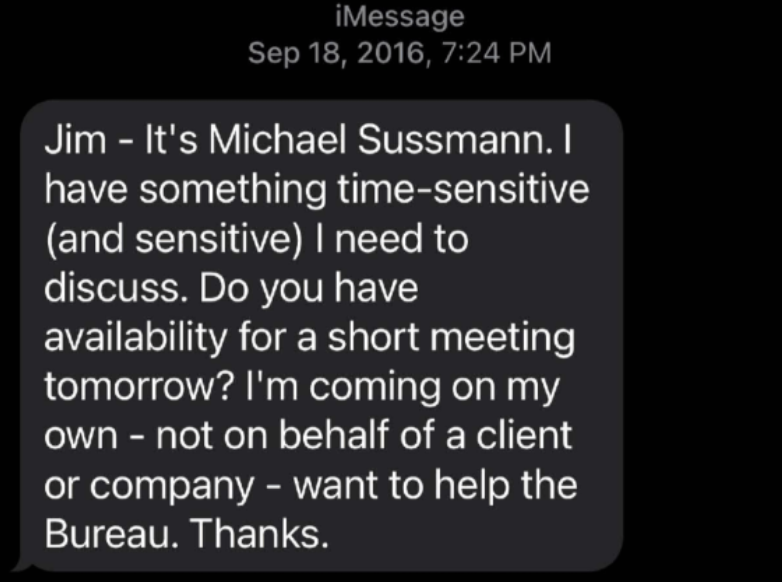
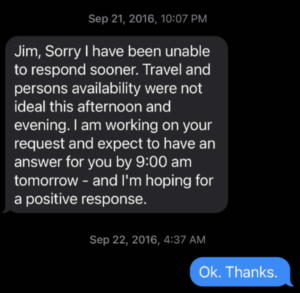
If you follow coverage of the Michael Sussmann trial anywhere but here and Politico, you would believe that the big news from Friday is that former Hillary campaign manager Robby Mook testified that Hillary personally approved of sharing the Alfa Bank story. As part of that coverage, virtually everyone is also covering the tweet admitted where Hillary focused attention on the Franklin Foer story after it came out.
Here’s how CNN covered it.
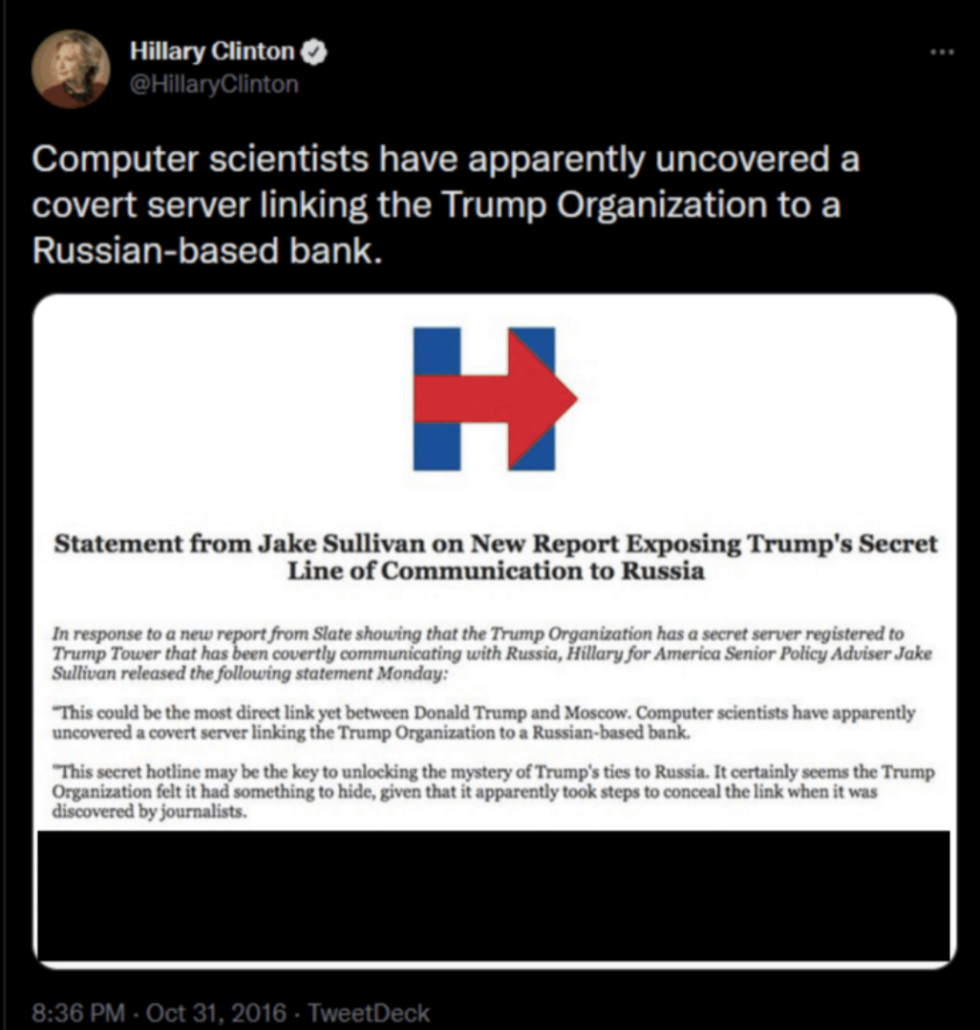
Slate published a story on October 31, 2016, raising questions about the odd Trump-Alfa cyber links. After that story came out, Clinton tweeted about it, and posted a news release that said, “This secret hotline may be the key to unlocking the mystery of Trump’s ties to Russia.”
[snip]
Inside the courtroom, prosecutors showed the jury Clinton’s tweet about the Trump-Alfa article from Slate, and Mook read aloud portions of the campaign’s news release about the story. The release was from Jake Sullivan, who is currently President Joe Biden’s national security adviser.
“We can only assume that federal authorities will now explore this direct connection between Trump and Russia as part of their existing probe into Russia’s meddling in our elections,” Sullivan said in the release on October 31, 2016, one week before Election Day.
The special counsel team has previously said that the Clinton campaign’s media blitz around the Slate story “is the very culmination of Mr. Sussmann’s work and strategy,” to allegedly gin up news coverage about the Trump-Alfa allegations and then get the FBI to start an investigation.
During the hearing, Twitter users recirculated Clinton’s old post. It caught the eye of billionaire Elon Musk, who has become increasingly vocal about political matters while he tries to buy Twitter, and recently announced his support for the Republican Party. He called the Trump-Alfa allegation “a Clinton campaign hoax” and claimed that Sussmann “created an elaborate hoax.” [my emphasis]
Obviously, the frothy right has made it the center of a frenzy to investigate Hillary herself. Surely it will also lead to an investigation of Jake Sullivan.
The thing is, legally, the part about investigating wasn’t supposed to come into the trial and will be something that, at the very least, Judge Christopher Cooper issues an instruction to the jury on.
This media frenzy was the predictable result of Andrew DeFilippis breaking Cooper’s rules. Again.
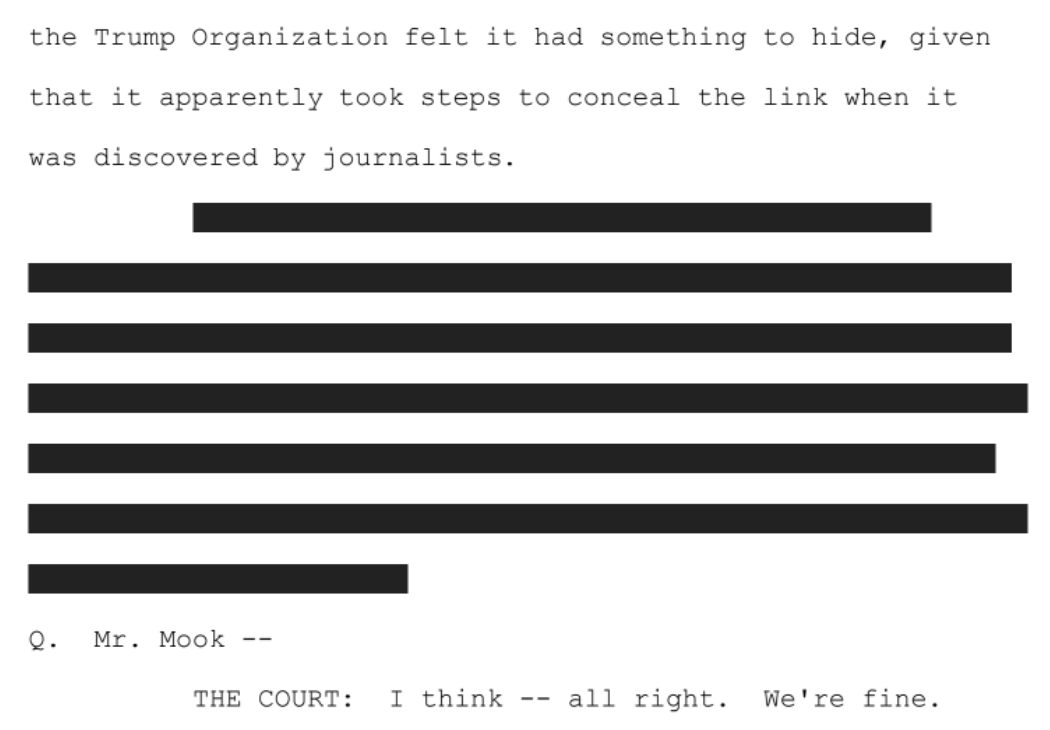
Here’s what the tweet, as sent to the jury will look like.
Here’s what the transcript looks like (though I don’t believe the transcript will be sent back to the jury).
Nevertheless, the jury heard it because — just minutes after being instructed not to include the language about the FBI investigation and not to read from the tweet!! — DeFilippis “accidentally” handed Robby Mook the unredacted copy to read, and coached him to continue to read the stuff that was redacted.
Q. And is there any reason why he would be the one to issue a statement like this?
A. You know, Jake’s a pretty highly regarded national security expert.
Q. Okay.
A. So it makes sense that he’s the voice on this.
Q. Could you just read the content of Mr. Sullivan’s statement.
A. Starting with “This could”?
Q. Yes.
A. “This could be the most direct link yet” —
Q. I’m sorry, start at the top.
A. “In response to a new report from Slate showing that the Trump Organization has a secret server registered to Trump Tower that has been covertly communicating with Russia, Hillary For America Senior Policy Advisor Jake Sullivan released the following statement Monday.” Keep going?
Q. Yes.
A. “This could be the most direct link yet between Donald Trump and Moscow. Computer scientists have apparently uncovered a covert server linking the Trump Organization to a Russian-based bank. “This secret hotline may be the key to unlocking the mystery of Trump’s ties to Russia. It certainly seems the Trump Organization felt it had something to hide, given that it apparently took steps to conceal the link when it was discovered by journalists. [my emphasis]
Here’s the bench conference that immediately preceded this exchange, in which DeFilippis made one last bid to enter the tweet into evidence. This language was redacted on first release of the transcript, but got unsealed overnight.
MR. DeFILIPPIS: Your Honor, could we have a quick call? (The following is a bench conference held outside the hearing of the jury)
MR. DeFILIPPIS: Your Honor, the government believes we’ve now laid an adequate foundation for probing into admissibility in connection with the Tweet and press statement that we’ve been talking about.
Mr. Mook has testified that the candidate herself approved a decision to send this to the media. The Tweet and press statement themselves refer to the FBI, and the defense admitted a Tweet during their examination of Mr. Baker.
We don’t think it’s, in light of this testimony, in any way prejudicial or cumulative because it addresses both the FBI issue and the issue of the decision to provide it to the media.
So we would ask that we be able to present the Tweet to Mr. Mook.
MR. BOSWORTH: Your Honor, we object. It remains the case that the — you know, Ms. Clinton is not on the witness stand. Jake Sullivan is not on the witness stand.
Jake Sullivan, weeks after Mr. Sussmann went to the FBI, issued a statement about the Slate article that was published that there’s no evidence that Mr. Sussmann had anything to do with. And that press statement goes into an area that goes beyond anything for which they’ve laid a foundation. And it’s highly prejudicial in that that statement doesn’t just say this is a serious story. It calls on the FBI to investigate.
That is incredibly prejudicial because it suggests that Mr. Sussmann was going to the campaign on their behalf, and there was literally zero evidence that the campaign knew Mr. Sussmann was going, including in Mr. Mook’s testimony today.
And second, that’s weeks after Mr. Sussmann went to the FBI. And the statement itself doesn’t say, “We’re so glad the FBI’s already investigating.” They’re steering far clear of any knowledge they could have even conceivably had about the investigation.
So we think Your Honor’s prior ruling stands.
THE COURT: All right. I want to review the statement again for the information that you say is extraneous.
Generally, as I indicated, I think, earlier this week, this does complete the story, and a lot of this is subject to cross. I think it can be explained that — just because it has Ms. Clinton’s name on it and is a statement of the campaign and it completes the narrative that the government has tried to advance, but I am concerned about any other extraneous information of the Tweet that may not be pertinent. So let me take a look at it. Can you complete your cross, or shall we just take a break?
MR. DeFILIPPIS: Maybe take a break, Your Honor. (This is the end of the bench conference)
THE COURT: All right. Ladies and gentlemen, we’re going to take about a five-minute break, so if you could just — to resolve an evidentiary issue. So if you could just retire to the deliberation room, we’ll call you when we’re ready. (Jury exits courtroom)
[snip]
THE WITNESS: Yes, Your Honor.
MR. BOSWORTH: Your Honor, do you want me to pass it up?
THE COURT: Yes, if you can pass it up. We have it back in chambers, but let me…
THE COURTROOM DEPUTY: Everyone can be seated.
THE COURT: Please be seated. And I’ll tell you what, just give me five minutes. (Recess taken)
THE COURT: All right. Mr. DeFilippis, if you can lay a foundation that he had knowledge that a story had come out and that the campaign decided to issue the release in response to the story, I’ll let you admit the Tweet. However, the last paragraph, I agree with the defense, is substantially more prejudicial than it is probative because he has testified that had neither — he nor anyone at the campaign knew that Mr. Sussmann went to the FBI, no one authorized him to go to the FBI, and there’s been no other evidence admitted in the case that would suggest that that took place. And so this last paragraph, I think, would unfairly suggest to the jury, without any evidentiary foundation, that that was the case. All right?
MR. DeFILIPPIS: Your Honor, just two brief questions on that.
THE COURT: Okay.
MR. DeFILIPPIS: Can we — so can we use — depending on what he says about whether he was aware of the Tweet or the public statement, may we use it to refresh him?
THE COURT: Sure. Sure.
MR. DeFILIPPIS: Okay. And then, as to the last paragraph, could it be used for impeachment or refreshing purposes as well in terms of any dealings with the FBI?
THE COURT: You can use anything to refresh.
MR. DeFILIPPIS: Okay.
THE COURT: But we’re not going to publish it to the jury. We’re not going to read from it. And let’s see what he says.
DeFilippis wasn’t even supposed to read it!! But he ignored Cooper’s orders, issued minutes earlier, and predictably set off a firestorm.
After Mook left the stand, Judge Cooper acknowledged that the FBI paragraph shouldn’t have come in. He acknowledged that DeFilippis had used it as hearsay to admit it for the truth. Sussmann’s lawyer Michael Bosworth graciously pretended DeFilippis’ actions were not intentional.
THE COURT: All right. Please be seated. Just for the record, in addition to the 403 grounds for the last paragraph of the press statement, it’s also hearsay from Mr. Sullivan for the truth — or whether it’s being offered for the truth, certainly it’s likely to be received for the truth that the campaign wished the FBI to investigate or had some hand in the FBI investigation. So that section of the Tweet, consistent with the Court’s prior ruling, is inadmissible as hearsay as well.
MR. BERKOWITZ: Thank you, Your Honor. Just briefly?
THE COURT: Yes.
MR. BERKOWITZ: Mr. DeFilippis, I’m sure, didn’t intend it, but he gave him the unredacted Tweet to perhaps refresh his recollection. He read probably two sentences, and we would ask that you strike from the record his reading of that. I know that —
THE COURT: The Court will strike those two sentences, and we’ll specify it for the court reporter. And obviously let’s make sure that the redacted copy is included in the exhibits that go to the jury.
MR. DeFILIPPIS: Yes, we will, Your Honor.
But DeFilippis did more than “accidentally” give Mook the unredacted tweet! He also had him read it, which he had just been told not to do.
Worse still, the record shows that neither Mook nor Hillary would have known about this tweet. It surely had high level press involvement, but this was presented as the words of Hillary when it was explicitly anything but.
And this is precisely what Sussmann’s team warned would happen when, in a pretrial hearing, Cooper floated reversing his past decision to exclude the tweet.
So the more I sort of dug into each side’s sort of theories of relevance over the weekend as we finalized the last motions in limine ruling, which you obviously got, I thought I might revisit one issue. And that is the Clinton campaign press release from October, late October, I guess.
I provisionally ruled that that would not be admissible based on the submissions that you all made. And I ruled from the bench without really getting any argument on that issue. And my previous understanding was that it was being offered to show a direct attorney-client relationship between Mr. Sussmann and the campaign as well as potentially the effect on the listener under a hearsay exception.
But I guess my question, as I have thought more about this, given the sort of two competing theories of the case and two narratives laid out in the Court’s ruling on the motion in limine, is whether it is relevant not for the truth, but to show the campaign’s connection to the alleged public relations effort to play stories regarding the Alfa-Bank data with the press and that therefore it of context for the Government’s motive theory, that Mr. Sussmann sought to conceal that effort, as well campaign’s general connection to that effort.
So, Mr. Berkowitz, please address that if want.
MR. BERKOWITZ: Yes, your Honor. Thank you for raising the issue.
THE COURT: Yes. And I will also say that I’ve never introduced a tweet at a trial. And there are certain evidentiary issues with what a tweet is and who it is sent by. I would like to avoid those issues. But there is a separate press release, which I’m not quite sure I appreciated when I ruled from the bench a week and a half ago.
MR. BERKOWITZ: So let me try and address the contextualized issue, your Honor.
With respect to the campaign’s involvement or PR connection to the Alfa-Bank story, we expect there will be testimony or other evidence that ties that together. And I know that in your motion in limine ruling, you assumed without saying we conceded it that we were taking the position that Mr. Sussmann was not acting on behalf of Hillary for America.
We’re not going to be taking the position that he was not counsel for Hillary for America in connection with various efforts and communications; and we will obviously address that at trial. But I don’t know that the connection between the campaign and PR efforts, opposition research to get the story of Alfa-Bank out there is going to be something that’s in dispute.
And I would ask that you, as you think about this issue, which is somewhat inflammatory because it gets the candidate — it’s a month after; it’s a different newspaper issue; and there’s no connection between Mr. Sussmann and that tweet to suggest that he was involved in that or was otherwise doing it.
And so as what else is coming is more prejudicial relates to a number it’s evaluated, I think contextualizing into evidence, I think that that tweet than it would be probative. It also of other issues that you note from an evidentiary standpoint.
So we don’t think that the tweet itself for all the reasons in our motion, but also because it’s not — it would be cumulative, I think, of the other evidence related to whether there was a connection at the time about that. Without getting into too much work product or issues, there were updates to the campaign related to, for example, the possibility of a New York Times story coming out. And I think that that will be what’s relevant as opposed to the larger issue of, you know, whether they continue to try and press that after the meeting.
THE COURT: I appreciate that. But there were a couple double negatives in there.
MR. BERKOWITZ: Please correct me or ask me to refocus it.
THE COURT: Did I understand you to say that the defense will not be contesting that he was representing the campaign in connection with some of the media outreach that was going on?
MR. BERKOWITZ: Correct.
THE COURT: Mr. DeFilippis?
MR. DeFILIPPIS: Yes, your Honor. Let me just briefly say that I think it’s plain from the contents of the tweet and the press statements themselves that the Government is not offering those for their truth. So I think your Honor, it seems, agrees that they’re not hearsay. It’s more of a relevance/probity thing.
And while I don’t have it in front of me, your Honor, when you read the contents both of the press statement and the tweet, the thrust of them is the very culmination of Mr. Sussmann’s work and strategy, which was twofold: First, the strategy, as the Government will argue at trial, was to create news stories about this issue, about the Alfa-Bank issue; and second, it was to get law enforcement to investigate it; and perhaps third, your Honor, to get the press to report on the fact that law enforcement was investigating it.
And we see all three things there reflected in the tweet and in the press statement. It says something to the effect of, Donald Trump has a secret channel with Russia and the FBI should look into this or we trust that the FBI is looking into this.
That is highly probative, your Honor, because it is, as I said, the culmination of everything the Defendant was trying to do as he billed work to the campaign.
And we expect to call at least currently, your Honor, the campaign manager of the Hillary Clinton campaign, who will say this was a conscious decision. After being briefed specifically on Mr. Sussmann’s efforts, the campaign made a conscious decision, authorized at the very highest levels of the campaign, to share the Alfa-Bank allegations with the media.
THE COURT: Well, if that’s going to be the case, and he’s not contesting that he was representing the campaign in connection with that effort, isn’t the tweet cumulative? It’s icing on the cake. Right?
MR. DeFILIPPIS: I don’t think so, your Honor, only because we will not have, your Honor — we will not call reporters to the stand who will in fact confirm that the campaign spoke to the media. We will not — we will have essentially the testimony of a campaign official.
And then the only way to show, your Honor, how the campaign actually capitalized on what it was that Mr. Sussmann did in the media is to — and it’s a very limited — as your Honor knows, it’s not long. It’s not particularly or really at all prejudicial, your Honor, because the contents of it are essentially just the candidate and one of her advisors adopting the allegation that Mr. Sussmann has been working on.So, your Honor, it’s really just context and the pure result of everything that Mr. Sussmann and the campaign were working on in this regard. And it’s not inflammatory. It simply states the allegation and it states that the campaign hopes the FBI’s looking into it.
We —THE COURT: I’ll reserve on it. Let’s see how the evidence comes in. And just don’t open on it.
MR. DeFILIPPIS: Okay. Thank you, your Honor.
MR. BERKOWITZ: Your Honor, I was also asking permission to approach, but I guess I don’t need to here.
Mr. DeFilippis in describing the relevance focused on the portion of the tweet that was different than you or I were talking about, that calling on the FBI to investigate. That in and of itself in our — from our perspective suggests that they are offering the tweet for the truth of the matter, that that’s what the campaign desired and wanted and that it was a accumulation of the efforts.
Number one, it’s not the truth; and in fact, it’s the opposite of the truth. We expect there to be testimony from the campaign that, while they were interested in an article on this coming out, going to the FBI is something that was inconsistent with what they would have wanted before there was any press. And in fact, going to the FBI killed the press story, which was inconsistent with what the campaign would have wanted.
And so we think that a tweet in October after there’s an article about it is being offered to prove something inconsistent with what actually happened.
This jury is not sequestered. It would take a great deal of diligence to avoid the shit storm this set off.
There is no way to undo the damage that this will do to the trial. And it happened because DeFilippis ignored not one but two parts of Cooper’s order — first, that the reference to the FBI be redacted, and second, that it not be read.
And it’s clear from the record that this has been the plan all along, just like using a self-described non-expert at DNS to offer an opinion about DNS. The truth is it’s Durham’s team, not Hillary, that had the plan to set off an October Surprise by manipulating the press all along.
Worse still, while there are legal measures to take, even then that would not undo the damage. Anything Cooper does to correct his own poor decision and DeFilippis’ worse flouting of Cooper’s orders would be blamed on him being an Obama appointment, not the law, and only further fuel the firestorm.
Even as the record sits right now, I believe there’s a great deal from which the jury would find reasonable doubt to convict. Given where I think Sussmann’s team is going to go from here, I think chances are good they get an acquittal.
But the Durham team just succeeded in a desperate bid to win this case using hearsay. Because hearsay is all they’ve got.