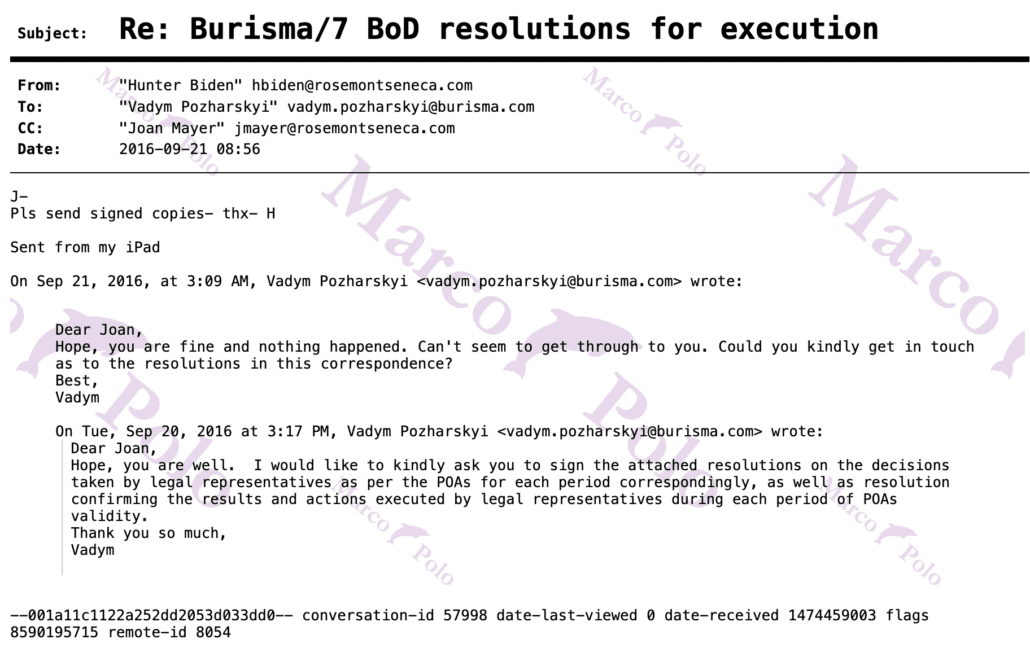
In one of many false claims Michael Shellenberger made (see this thread for another) in his Twitter Files thread purporting to address Twitter’s handling of the “Hunter Biden” “laptop” (but which focused a lot on non-Twitter material on the “laptop”), he made this claim about the deposition of FBI Assistant Agent in Charge Elvis Chan.
Chan was interviewed as part of the lawsuit filed by Eric Schmitt before Schmitt was elected to the Senate. The suit alleges that the government has violated the First Amendment rights of Americans by pressuring social media companies to take down misinformation. The bolded language below, from an address by George Washington, appears in the first paragraph of Schmitt’s complaint.
if Men are to be precluded from offering their sentiments on a matter, which may involve the most serious and alarming consequences, that can invite the consideration of Mankind; reason is of no use to us—the freedom of Speech may be taken away—and, dumb & silent we may be led, like sheep, to the Slaughter. [my emphasis]
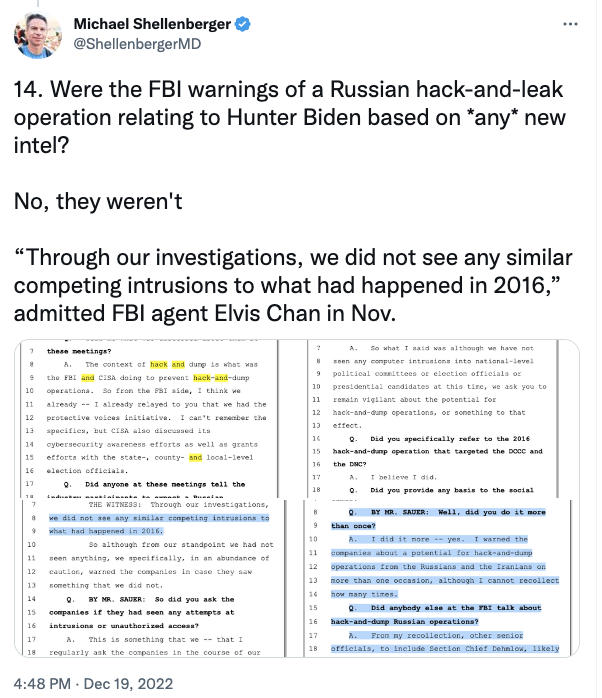
Shellenberger’s tweet is part of an argument that the FBI warned the social media companies specifically about Hunter Biden. Indeed, his tweet is premised on the claim that the FBI gave “warnings of a hack-and-leak operation relating to Hunter Biden.” [my emphasis]
In fact, though Hunter Biden came up in this deposition 36 times, Chan’s testimony was that Hunter Biden came up in just one briefing with social media companies, one in which someone from FBI’s Foreign Influence Task Force, Laura Dehmlow, refused to comment in response to a question from Facebook about the already-published NY Post story.
Q. BY MR. SAUER: Do you know that in 20– so you remember sometime in 2020 a Facebook analyst asked the FBI to comment on the status of the Hunter Biden investigation?
A. That’s correct.
Q. And you believe that this occurred after there had been, you know, a New York Post article about the contents of the laptop that you referred to — I think you referred to earlier you finding out about it that way, right?
A. Yeah, I only found out through news media. I have no internal knowledge of that investigation, and yeah, I believe that it was brought up after the news story had broke.
Q. And so the — what did the Facebook analyst ask Ms. Dehmlow? Did they ask, you know, “Hey, we have the story. Can you confirm it,” or what did they ask?
A. Yeah, they just — I can’t remember the exact question, but I believe the investigator asked if the FBI could provide any information about the Hunter Biden investigation.
Q. Did they refer to the laptop in particular that had been the subject of the news stories?
A. I can’t recall.
Q. And what did Ms. Dehmlow respond?
A. She said no comment. She said something to the effect that the FBI has no comment on this.
Q. Did she indicate why the FBI declined to comment?
A. Yes. It was because — at the time I do not believe that we had confirmed that it was an active — we had — at the time we had not confirmed that the FBI was actually investigating Hunter Biden. So she did not have the authority to say anything or to comment about it.
Q. Did she know at the time that the FBI had the laptop and that the contents had not been hacked?
MR. SUR: Objection; calls for speculation and gets into law enforcement privilege.
Q. BY MR. SAUER: To your knowledge?
A. I have no idea. I never asked her, and she never told me.
Q. Did Hunter Biden come up with any other social media platforms during 2020?
A. Not to my knowledge.
Q. Do you recall any mention of Hunter Biden at any meetings with any social media platforms?
A. No. It stood out because that Facebook meeting was the only one where an individual from one of the companies even asked about it.
Q. You’re confident that Hunter Biden did not come up at any other meetings between federal government officials and social media platforms in 2020?
A. I was confident that I was not a party to any meeting with social media companies where Hunter Biden was discussed outside of the one incident that I told you about.
Q. That was the one where it was a FITF Facebook meeting where the analyst asked Ms. Dehmlow and she refused to comment, correct?
A. That is correct. That is correct.
Note that Twitter Files propagandists often refer to Dehmlow’s actions in 2020 and describe that she was in charge of the entire FITF effort, but at the time she was only in charge of the China unit. That has the effect of falsely suggesting she and all the other FITF warnings were focused primarily on Russia (Iran is similarly neglected from the focus of the Twitter Files propagandists).
In his deposition, Chan takes issue with former Twitter head of Trust and Safety Yoel Roth’s use, in a declaration explaining why Twitter took down links to the NY Post article, of the word, “expectation,” to describe FBI’s warnings to be on the lookout for hack-and-leak operations and notes that the FBI would have been the only federal law enforcement agency who offered such warnings; CISA, which organized other meetings with the FBI, is not a law enforcement agency (though the Twitter File propagandists have at times claimed it is). He also has to correct Schmitt’s lawyer when he treats Roth’s reference to the Infosec community’s response to the NY Post story to include the FBI, as opposed to the private sector Infosec community.
But Chen’s testimony — whether it accords with Twitter’s own records or not — is quite clear: while the FBI (and CISA and ODNI) were absolutely warning that there might be hack-and-leak operations in 2016, those warnings did not mention Hunter Biden. Rather than admitting that, Shellenberger instead states as fact that these warnings were “relating to Hunter Biden.”
And then he does something funnier. To prove that these warnings “relating to Hunter Biden” that weren’t related to Hunter Biden weren’t based on any new information, he points to Chan’s repeated comments that the FBI had not seen any intrusions like the 2016 ones.
Q. You said that there might be a Russian hack-and-dump operation?
A. So what I said was although we have not seen any computer intrusions into national-level political committees or election officials or presidential candidates at this time, we ask you to remain vigilant about the potential for hack-and-dump operations, or something to that effect.
Q. Did you specifically refer to the 2016 hack-and-dump operation that targeted the DCCC and the DNC?
A. I believe I did.
Q. Did you provide any basis to the social media platforms for thinking that such an operation 20 might be coming?
A. The basis was — my basis was it had happened once, and it could happen again.
Q. Did you have any other specific information other than it had happened four years earlier?
[snip]
THE WITNESS: Through our investigations, we did not see any similar competing intrusions to what had happened in 2016. So although from our standpoint we had not seen anything, we specifically, in an abundance of caution, warned the companies in case they saw something that we did not.
Q. BY MR. SAUER: So did you ask the companies if they had seen any attempts at intrusions or unauthorized access?
A. This is something that we — that I regularly ask the companies in the course of our meetings.
Q. Did you ask them in these meetings?
A. Not at every meeting, but I believe I asked them at some meetings.
Q. And did you repeatedly warn them at these meetings that you anticipated there might be hack-and-dump operations, Russian-initiated hack-and-dump operations?
[snip]
THE WITNESS: So repeatedly I would say — can you — can you ask your question like — what do you mean by “repeatedly”? Like times, five times?
Q. BY MR. SAUER: Well, did you do it more than once?
A. I did it more — yes. I warned the companies about a potential for hack-and-dump operations from the Russians and the Iranians on more than one occasion, although I cannot recollect how many times. [my emphasis]
But note that Chan specifically referenced hacks of “national-level political committees or election officials or presidential candidates.”
Hunter Biden is not and was not a national-level political committee.
Hunter Biden is not and was not an election official.
Hunter Biden is not and was not a presidential candidate.
Having misrepresented what Chan said about the extent of any discussions of Hunter Biden (whether it is accurate or not), Shellenberger then pointed to testimony about hacks of political candidates to disclaim the FBI had any information about hacks of someone who is not a political candidate.
And while it doesn’t show up in this deposition because Eric Schmitt doesn’t much care about Russian hacking, Chan’s reference to Russia and Iran is significant: because according to former CISA Director Chis Krebs’ January 6 Committee deposition, both did hack “election-adjacent systems” in 2020.
Q Are you able to form any conclusions as to whether there was a cyber intrusion in connection with the 2020 election?
A Yes. In fact, we released alerts on these things throughout. There were both Russian and Iranian actors that were able to gain access to election-adjacent systems. The Iranians, in one case, I think, had access to a voter registration database. But we’re not aware of any instance where they were in a system that would’ve been directly connected or, you know, involved in casting, counting, certifying of votes.
Indeed, Iran conducted the most notable information operation in 2020, emails to Democrats in Florida purporting to be Proud Boys providing disinformation about the election. So a good deal of the wailing about last minute warnings to social media companies in 2020 had to do, in part, with foreigners maligning far right militia members, not Hunter Biden. We haven’t heard anything about the FBI’s efforts to protect the reputation of the Proud Boys from Elmo’s propagandists, though.
Several more points about Chan’s responses on hack-and-leak campaigns are worth nothing. First, Chan said he kept raising the potential of a hack-and-leak campaign, “in case [the tech companies] saw something that we did not.” Russian denialists like Matt Taibbi — who espoused the Single Server fallacy until at least 2019 — don’t understand this, but when GRU engaged in a hack-and-leak campaign in 2016, tech companies were seeing the operation and attributing it to Russia in real time (though not Twitter, that I am aware of). Tech companies saw some parts of the attack before the FBI did. Yet in his deposition, Chan had to repeatedly explain to Schmitt’s lawyer that most of his interactions with social media companies involve hacks, not disinformation.
THE WITNESS: Yeah. The majority of my interaction with Facebook is not in the disinformation or malign-foreign-influence realm. It is actually for things related to my — to the Cyber Branch, which are specifically cyber investigations.
One time Chan even had to explain that “malign foreign influence” sometimes involves hacking (the Iranian campaign targeting the Proud Boys appears to have, for example). And Chan described several times that his team not only investigated part of the 2016 hack, but still had an active investigation into those actors. That’s important not only because he would have firsthand knowledge of the kinds of attribution social media companies (and Google and Microsoft) had in 2016, but for another reason: On October 19, 2020, DOJ indicted a bunch of GRU hackers, including one charged in the 2016 hack-and-leak campaign, for a variety of additional hacks, including the hack-and-leak targeting Emmanuel Macron. The Macron campaign, specifically, included both Google and Twitter components. So in the very same weeks when — right wingers complain — Elvis Chan was in close contact with Twitter about the ongoing election, he or his subordinates were likely working with prosecutors in Pittsburgh on an indictment implicating both Google and Twitter.
Emmanuel Macron is not mentioned in the Chan deposition.
Something else not mentioned in the Chan deposition — not once among the 36 mentions of Hunter Biden!!! — is Burisma Holdings. Mind you, it was not FBI that had attributed a 2019 hack of Burisma to the GRU, the very same actors under discussion, earlier in 2020, it was a Bay Area Infosec company, that same Infosec community that Yoel Roth had attributed some of his concerns about Hunter Biden to. We have no idea whether the FBI — whether a team under Chan’s direction, possibly! — similarly discovered that GRU had hacked Burisma in 2019. Chan was never asked. It’s one of the questions you’d have to ask, though, if you wanted to know whether the FBI had any knowledge that might lead them to believe that Hunter Biden — as distinct from “national-level political committees or election officials or presidential candidates” — had been targeted with a GRU info op during the 2020 presidential cycle.
So there are several things that you would want to ask Elvis Chan about whether he knew of things in 2020 that might have raised concerns that the NYPost article was part of a hack-and-leak campaign, including what hacks Russian and other foreign countries did do, his interactions with Bay Area companies Google and Twitter in those very same weeks in advance another indictment of the GRU, as well as his knowledge of the Bay Area attribution of a GRU campaign targeting Burisma. Eric Schmitt’s lawyer didn’t ask. Which is to say that nothing in this deposition addresses Shellenberger’s specific claims, which unsurprisingly didn’t stop him from claiming it did.
But at least we know he knows of the deposition, though from the looks of his screen cap, he may have mostly just searched it for isolated language that would confirm his priors.
Lee Fang, whose single entry in Twitter Files is the least dishonest, has also read it. He posted a screen cap reporting as “news” that the FBI weighs in on legislation that affects the FBI (which is tantamount to confessing that Fang knows next to nothing about how DC works; Fang did not retract his wildly erroneous article that was significantly debunked by Chan’s deposition).

In other words, two people associated with the Twitter Files have at least claimed familiarity with this deposition.
And yet, as recently as Friday, #MattyDickPics has continued to make grossly false claims about what FBI was doing.
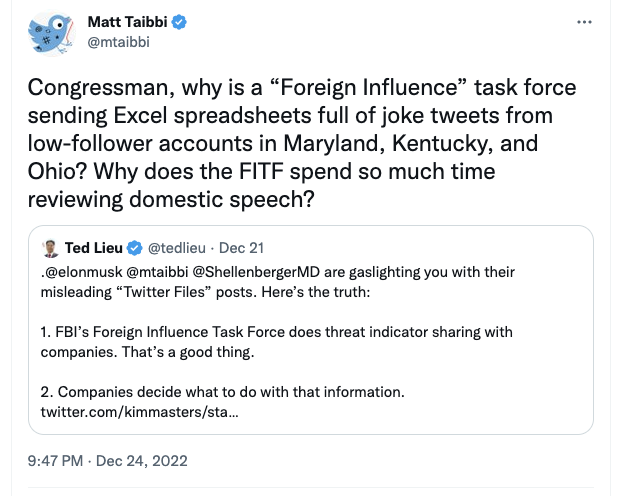
Over and over again, Matty has complained that the FBI sent Twitter URLs for tweets, including tweets written by Americans.
Some of the moderation decisions he reviewed in his first Twitter File thread focus on Tweets about the means and method of voting. He calls Tweets advertising an incorrect day for election day “silly numbers.”
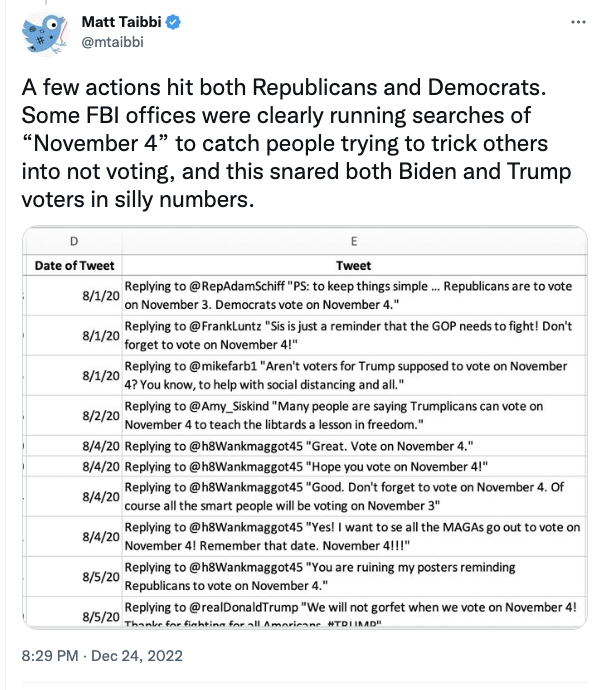
In short, Matt Taibbi has gone from being furious that Twitter removed non-consensually posted dick pics, some of which were the product of inauthentic campaign launched by Steve Bannon buddy Guo Wengui, to being outraged that the FBI shared Tweets advertising the wrong day for election day.
He has done so in spite of the fact that Chan’s deposition explains why the FBI was doing that: because sending false information that might lead someone to lose their opportunity to vote is a crime.
Q. But you received reports, I take it, from all over the country about disinformation about time, place and manner of voting, right?
A. That is — we received them from multiple field offices, and I can’t remember. But I remember many field offices, probably around ten to 12 field offices, relayed this type of information to us. And because DOJ had informed us that this type of information was criminal in nature, that it did not matter where the — who was the source of the information, but that it was criminal in nature and that it should be flagged to the social media companies. And then the respective field offices were expected to follow up with a legal process to get additional information on the origin and nature of these communications.
Q. So the Department of Justice advised you that it’s criminal and there’s no First Amendment right to post false information about time, place and manner of voting?
[snip]
A. That was my understanding.
Q. And did you, in fact, relay — let me ask you this. You say manner of voting. Were some of these reports related to voting by mail, which was a hot topic back then?
A. From my recollection, some of them did include voting by mail. Specifically what I can remember is erroneous information about when mail-in ballots could be postmarked because it is different in different jurisdictions. So I would be relying on the local field office to know what were the election laws in their territory and to only flag information for us. Actually, let me provide additional context. DOJ public integrity attorneys were at the FBI’s election command post and headquarters. So I believe that all of those were reviewed before they got sent to FBI San Francisco.
Q. So those reports would come to FBI San Francisco when you were the day commander at this command post, and then FBI San Francisco would relay them to the various social media platforms where the problematic posts had been made, right?
A. That is correct.
Q. And then the point there was to alert the social media platforms and see if they could be taken down, right?
A. It was to alert the social media companies to see if they violated their terms of service. [my emphasis]
I’ve got a request into the FBI but have not gotten a response about what crime this violated, but I believe the crime DOJ was relying on — Bill Barr’s DOJ! — was the Ku Klux Klan Act, which was passed in 1871 to prevent racists from conspiring to deprive former slaves from voting. This is the same crime that Douglass Mackey was charged with for allegedly conducting a more systematic campaign to misinform black voters about when to vote in 2016 (Mackey has pled not guilty and is vigorously contesting the constitutionality of the statute).
In other words, after complaining that Twitter chose to take down revenge porn targeting Joe Biden’s son, Taibbi is now complaining that DOJ enforced a law designed to protect Black people’s right to vote.
And his fellow Twitter File propagandists, at least two of whom claim familiarity with Elvis Chan’s deposition that explains this, are letting him continue to grossly misrepresent an effort to protect the right to vote.