Hiding the 215 Index from Defendants, Too
Adam Liptak reviews one of the issues I laid out in this post and the ACLU first laid out here. The government is reneging on multiple promises made over the course of the Amnesty v. Clapper case — including to SCOTUS itself — to make sure defendants could challenge evidence collected under “the program” (then defined as Section 702 of the FISA Amendments Act).
But I’m particularly interested in Liptak’s focus on the government’s use of “derived from” here.
If the government wants to use information gathered under the surveillance program in a criminal prosecution, [Solicitor General Don Verrilli] said, the source of the information would have to be disclosed. The subjects of such surveillance, he continued, would have standing to challenge the program.
Mr. Verrilli said this pretty plainly at the argument and even more carefully in his briefs in the case.
In one brief, for example, he sought to refute the argument that a ruling in the government’s favor would immunize the surveillance program from constitutional challenges.
“That contention is misplaced,” he wrote. “Others may be able to establish standing even if respondents cannot. As respondents recognize, the government must provide advance notice of its intent to use information obtained or derived from” the surveillance authorized by the 2008 law “against a person in judicial or administrative proceedings and that person may challenge the underlying surveillance.” (Note the phrase “derived from.”)
In February, in a 5-to-4 decision that split along ideological lines, the Supreme Court accepted Mr. Verrilli’s assurances and ruled in his favor. Justice Samuel A. Alito Jr., writing for the majority in the case, Clapper v. Amnesty International, all but recited Mr. Verrilli’s representation.
“If the government intends to use or disclose information obtained or derived from” surveillance authorized by the 2008 law “in judicial or administrative proceedings, it must provide advance notice of its intent, and the affected person may challenge the lawfulness of the acquisition.” (Again, note the phrase “derived from.”)
What has happened since then in actual criminal prosecutions? The opposite of what Mr. Verrilli told the Supreme Court. [my emphasis]
It’s time to broaden the focus of this discussion, finally. It’s time to include both Section Section 215 collection (metadata) and 702 collection (content) in this discussion together.
As I have noted, the government has claimed these are “distinct issues” and that 215 metadata collection is not part of the 702 content creation.
But in an interview, Edward Snowden claims the metadata is used to identify and pull content.
In most cases, content isn’t as valuable as metadata because you can either re-fetch content based on the metadata or, if not, simply task all future communications of interest for permanent collection since the metadata tells you what out of their data stream you actually want.
And James Clapper described metadata as a kind of Dewey Decimal system that allows the government to pull selected conversations from its giant library of all conversations.
ANDREA MITCHELL: At the same time, when Americans woke up and learned because of these leaks that every single telephone call in this United States, as well as elsewhere, but every call made by these telephone companies that they collect is archived, the numbers, just the numbers, and the duration of these calls. People were astounded by that. They had no idea. They felt invaded.
JAMES CLAPPER: I understand that. But first let me say that I and everyone in the intelligence community all– who are also citizens, who also care very deeply about our– our privacy and civil liberties, I certainly do. So let me say that at the outset. I think a lot of what people are– are reading and seeing in the media is a lot of hyper– hyperbole.
A metaphor I think might be helpful for people to understand this is to think of a huge library with literally millions of volumes of books in it, an electronic library. Seventy percent of those books are on bookcases in the United States, meaning that the bulk of the of the world’s infrastructure, communications infrastructure is in the United States.
There are no limitations on the customers who can use this library. Many and millions of innocent people doing min– millions of innocent things use this library, but there are also nefarious people who use it. Terrorists, drug cartels, human traffickers, criminals also take advantage of the same technology. So the task for us in the interest of preserving security and preserving civil liberties and privacy is to be as precise as we possibly can be when we go in that library and look for the books that we need to open up and actually read.
You think of the li– and by the way, all these books are arranged randomly. They’re not arranged by subject or topic matter. And they’re constantly changing. And so when we go into this library, first we have to have a library card, the people that actually do this work.
Which connotes their training and certification and recertification. So when we pull out a book, based on its essentially is– electronic Dewey Decimal System, which is zeroes and ones, we have to be very precise about which book we’re picking out. And if it’s one that belongs to the– was put in there by an American citizen or a U.S. person.
We ha– we are under strict court supervision and have to get stricter– and have to get permission to actually– actually look at that. So the notion that we’re trolling through everyone’s emails and voyeuristically reading them, or listening to everyone’s phone calls is on its face absurd. We couldn’t do it even if we wanted to. And I assure you, we don’t want to.
ANDREA MITCHELL: Why do you need every telephone number? Why is it such a broad vacuum cleaner approach?
JAMES CLAPPER: Well, you have to start someplace. If– and over the years that this program has operated, we have refined it and tried to– to make it ever more precise and more disciplined as to which– which things we take out of the library. But you have to be in the– in the– in the chamber in order to be able to pick and choose those things that we need in the interest of protecting the country and gleaning information on terrorists who are plotting to kill Americans, to destroy our economy, and destroy our way of life.
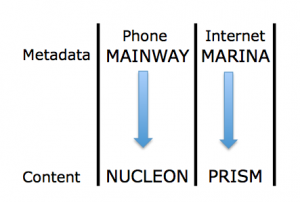
And according to William Arkin, the 215 metadata database, called MAINWAY, is considered a “signals navigation database.”
In other words, the 215 database is at least sometimes used as a roadmap to all the other collections the NSA gathers.
As I’ll show in a follow-up post, how that roadmap is used may go to the heart of the legitimacy of investigations into American.
I’m not entirely sure what discovery obligations the government thinks it has with this tool. But given that it’s a moment where the government claims to be exercising reasonable cause analysis (in secret) it sure ought to be disclosed.