A New Emphasis on Threats of Violence in the Latest January 6 Conspiracy Indictment
As I laid out the other day, the government charged six Three Percenters from California — American Phoenix Project founder Alan Hostetter, Russell Taylor, Erik Warner, Tony Martinez, Derek Kinnison, and Ronald Mele — with conspiracy. As I described, the indictment was notable in that just one of the men, Warner, actually entered the Capitol. But it was also notable for the way it tied Donald Trump’s December 19 call for a big protest on January 6 with their own public calls for violence, including executions, as well as an explicit premeditated plan to “surround the capital” [sic].
That’s one reason I find the slight difference in the way this conspiracy got charged to be of interest.
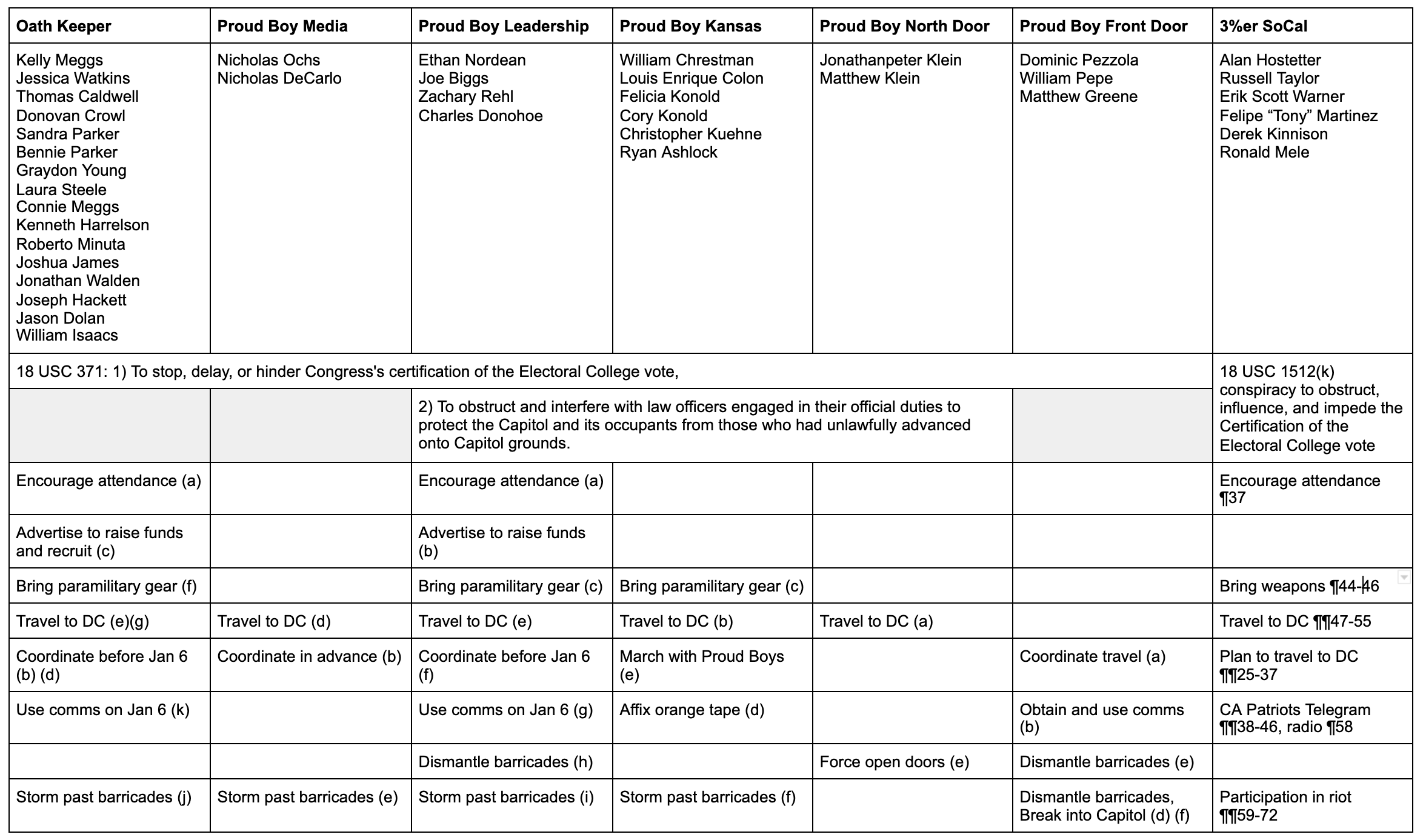
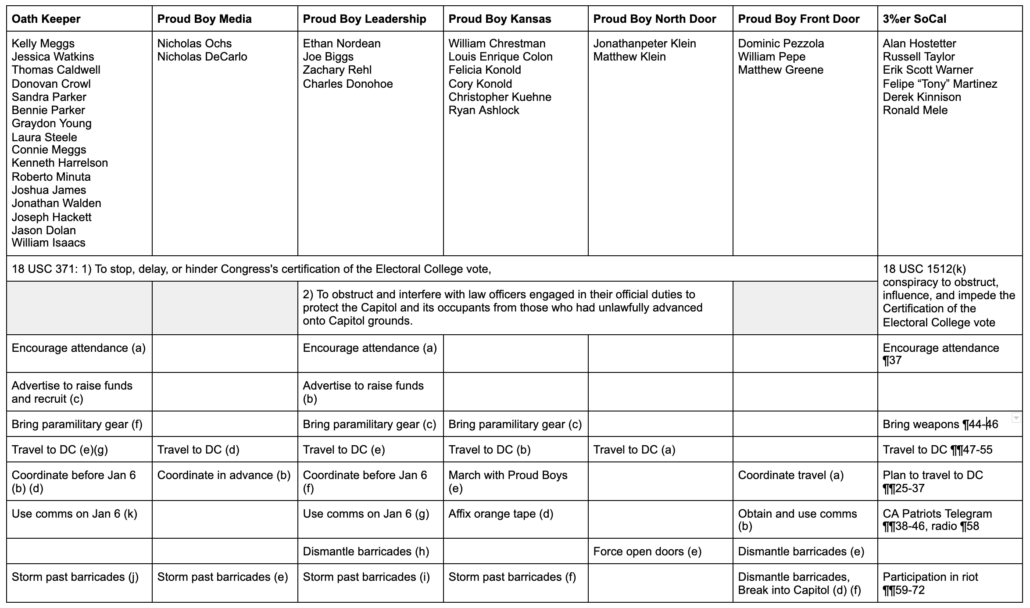
As I’ve been tracking over time, the now-seven militia conspiracies are structured very similarly, with each including coordinated plans to get to DC, some kind of plans to kit out for war, and some coordinated effort to participate in the assault on the Capitol. These conspiracies intersect in multiple ways we know of:
- Thomas Caldwell’s communication with multiple militia to coordinate plans
- Kelly Meggs’ formation of an alliance between Florida militias
- Joe Biggs’ decision to exit the Capitol after the first breach, walk around it, and breach it again with two other Proud Boys in tow just ahead of the Oath Keeper stack
- The attendance of James Breheny (thus far only charged individually), apparently with Stewart Rhodes (thus far not charged), at a leadership meeting of “multiple patriot groups” in Quarryville, PA on January 3, which Breheny described as “the day we get our comms on point with multiple other patriot groups”
All three militias mingled in interactions they’ve had with Roger Stone, as well, but thus far Stone only shows up in the Oath Keepers’ conspiracy.
In other words, while these represent seven different conspiracies (along with around maybe 15 to 20 identified militia members not charged in a conspiracy), they’re really one networked conspiracy that had the purpose of preventing the democratic replacement of Donald Trump.
Of particular note, what is probably the most serious case of assault charged against a militia member, that charged against Proud Boy Christopher Worrell, has not been included in any conspiracy. So while individual members of these conspiracies — including Joshua James, Dominic Pezzola, and William Isaacs, have been charged for their own physical resistance to cops — the conspiracies as a whole don’t yet hold conspirators accountable for the violence of their co-conspirators. The conspiracies only allege shared responsibility for damage to the Capitol, not violence against cops.
That said, the purpose and structure of the Three Percenter conspiracy is slightly different than the other six. The other six (Oath Keeper, Proud Boy Media, Proud Boy Leadership, Proud Boy Kansas City, Proud Boy North Door, Proud Boy Front Door) are all charged under 18 U.S.C. §371, conspiracy against the US. While the timeline of each conspiracy varies and while some of the Proud Boy conspiracies also include the goal of impeding the police, all six include language alleging the conspirators,
did knowingly combine, conspire, confederate, and agree with each other and others known and unknown, to commit an offense against the United States, namely, to corruptly obstruct, influence, and impede an official proceeding, that is, the Certification of the Electoral College vote, in violation of Title 18, United States Code, Section 1512(c)(2).
The purpose of the conspiracy was to stop, delay, and hinder the Certification of the Electoral College vote.
That is, those six conspiracies are charged (at least) as a conspiracy to violate the obstruction statute.
The Three Percenter SoCal conspiracy, however, is charged under the obstruction itself, 18 U.S.C. §1512(k).
Between December 19, 2020 and January 6, 2021, within the District of Columbia and elsewhere, the defendants … together with others, did conspire to corruptly obstruct, influence, and impede an official proceeding, to wit: the Certification of the Electoral College vote.
The object is the same — to impede the vote certification. But it is charged differently.
I’m still thinking through what the difference might mean. It might mean nothing, it might reflect the preference of the prosecutors, or it may reflect a rethinking at DOJ.
Nick Smith claims there’s no evidence Ethan Nordean corruptly influenced anyone else to violate their duty
But there are two things that may factor into it. First, since the government first started structuring its conspiracies this way, some defense attorneys have started challenging the applicability of the obstruction statute to the vote certification at all. For this discussion, I’ll focus on the argument as Nick Smith laid it out in a motion to throw out the entire indictment against Ethan Nordean. Smith makes two arguments regarding the conspiracy charge.
First, Smith argues that Congress only intended the obstruction statute to apply to proceedings that involve making factual findings, and so poor Ethan Nordean had no way of knowing that trying to prevent the vote certification might be illegal.
As indicated above, § 1512(c)(2) has never been used to prosecute a defendant for the obstruction of an “official proceeding” unrelated to the administration of justice, i.e., a proceeding not charged with hearing evidence and making factual findings. Moreover, there is no notice, much less fair notice, in § 1512(c)(2) or in any statute in Chapter 73 that a person may be held federally liable for interference with a proceeding that does not resemble a legal tribunal.
Of course, that argument ignores that Ted Cruz and the other members who challenged the vote claim they were making factual findings — so Nordean’s co-conspirators may sink this legal challenge.
Smith also argues that the obstruction charge fails under the findings of US v. Poindexter, in which John Poindexter’s prosecution for lying to Congress about his role in Iran-Contra was reversed, in part, because the word “corruptly” as then defined in the obstruction statute was too vague to apply to Poindexter’s corrupt failure to do his duty. Smith argues that the language remains too vague based on his claim that the government is trying to prosecute Nordean for his “sincerely held political belief that the 2020 presidential election was not fairly decided,” which prosecutors have no business weighing.
Here, the FSI’s construction on § 1512(c)’s adverb “corruptly” fails this Circuit’s Poindexter test. First, the FSI does not allege that Nordean obstructed the January 6 joint session “to obtain an improper advantage for himself or someone else. . .” Poindexter, 951 F.2d at 386. Instead, it contends he allegedly obstructed the session in support of the sincerely held political belief that the 2020 presidential election was not fairly decided. Such an interpretation of § 1512(c) is unconstitutionally vague because it leaves to judges and prosecutors to decide which sincerely held political beliefs are to be criminalized on an ad hoc basis. Dimaya, 138 S. Ct. at 1223-24. Second, the FSI neither alleges that Nordean influenced another person to obstruct the January 6 proceeding in violation of their legal duty, nor that Nordean himself violated any legal duty by virtue of his mere presence that day.
As I noted in my post on this challenge, this might be a nifty argument for a defendant who hadn’t — as Nordean had — started calling for revolution on November 27, well before the state votes were counted. But Nordean had already made his intent clear even before the votes were counted, so Smith’s claims that Nordean was reacting to the election outcome is fairly easily disproven. (As with this entire challenge, it might work well for other defendants, but for a long list of reasons, it is far less likely to work with Nordean.)
There’s another, far more important, aspect to this part of the argument though. Smith claims, without any discussion, that Nordean didn’t “influence” any other person to violate their legal duty. Smith wants Judge Timothy Kelly to believe that Nordean did not mean to intimidate Congress by assembling a violent mob and storming the Capitol and as a result of intimidation to fail to fulfill their duty as laid out in the Constitution, whether by refusing to certify Joe Biden as President, or by running away in terror and simply failing to complete the task.
Unlike conspiracy, obstruction has a threat of violence enhancement
As I understand it (and I invite actual lawyers to correct me on this), the other difference between charging this conspiracy under 18 USC 371 and charging it under 1512(k) is the potential sentence. While defendants can be sentenced to 20 years under their individual obstruction charges (the actual sentence is more likely to be around 40 months, or less if the defendant pleads out), 18 USC 371 has a maximum sentence of five years.
If two or more persons conspire either to commit any offense against the United States, or to defraud the United States, or any agency thereof in any manner or for any purpose, and one or more of such persons do any act to effect the object of the conspiracy, each shall be fined under this title or imprisoned not more than five years, or both.
But 18 USC 1512(k) says that those who conspire to obstruct shall be subject to the same penalty as they’d face for the actual commission of the offense.
(k)Whoever conspires to commit any offense under this section shall be subject to the same penalties as those prescribed for the offense the commission of which was the object of the conspiracy.
And obstruction has special penalties tied to murder, attempted murder, and the threat of physical force.
(3) The punishment for an offense under this subsection is—
(A) in the case of a killing, the punishment provided in sections 1111 and 1112;
(B) in the case of—
(i) an attempt to murder; or
(ii) the use or attempted use of physical force against any person;
imprisonment for not more than 30 years; and
(C) in the case of the threat of use of physical force against any person, imprisonment for not more than 20 years.
Thus, anyone charged along with a co-conspirator who threatened to kill someone may be exposed to twenty or even thirty years in prison rather than just five years.
As noted, there are several things about the overt acts charged in the Three Percenter conspiracy that differentiate it from the other militia conspiracies. They were even more explicit about their intent to come armed to the Capitol than the Oath Keepers were with their QRF (and their stated excuses to be armed relied even less on what I call the Antifa foil, the claim they had to come armed to defend against people they fully planned to incite).
And Hostetter twice publicly threatened to execute people. He posted a YouTube on November 27 in which he said, “some people at the highest levels need to be made an example of with an execution or two or three.” And he gave a speech on December 12 in which he demanded, “There must be long prison terms, while execution is the just punishment for the ringleaders of the coup.”
In other words, I think by charging this conspiracy under the obstruction statute rather than the conspiracy one, the government has exposed all of Hostetter’s co-conspirators, along with Hostetter himself, to far longer sentences because he repeatedly threatened to execute people.
The Three Percenter conspiracy makes threats to intimidate Mike Pence and members of Congress an object of the conspiracy
My guess is that the government is going to argue that, of course, Nordean was trying to corruptly influence others to violate their legal duty to certify the electoral results. Every single militia includes at least one member who made explicit threats against Mike Pence or Nancy Pelosi, and the Proud Boys, especially, have no recourse by claiming they showed up to listen to Donald Trump, since instead of attending his speech, they were assembling a violent mob to march on the place where Mike Pence was going to enact his official duties.
The Proud Boys were there to intimidate Mike Pence and members of Congress in hopes they would fail to fulfill their duty as laid out in the Constitution. If these charges make it to trial, I think prosecutors will be able to make a very compelling argument that assembling a mob in anticipation of Pence’s official acts was designed to intimidate him corruptly.
But, if I’m right about the criminal penalties, with the Three Percenter conspiracy, the government is going one step further. This conspiracy is structured to hold each member of the conspiracy accountable for the threats of murder made by Hostetter, the threat posed by planning to be armed at the Capitol, as well as the violence of others in their networked conspiracy. And even for those who didn’t enter the Capitol but instead egged on violence from some rally stage or behind some bullhorn, this conspiracy seems to aspire to expose co-conspirators accountable to a twenty year sentence for their (unsuccessful) efforts to intimidate Mike Pence to renege on his duty.
Update: I should add that someone with no prior convictions who goes to trial and is found guilty would face closer to 7-9 years with a full threats of violence enhancement. It would not be the full 20 years.
Update: Thanks to harpie for helping me count to seven (I had the wrong total number originally).