In this series, it feels like time is marked by big Russian meetings and key firings.
I’m talking, of course, about my efforts to use the Mueller questions as imagined by Jay Sekulow to map out what the structure of the investigation (at least as it pertains to Trump personally) might be. Thus far, I’ve shown:
- Russians, led by the Aras Agalarov and his son, cultivated Trump for years by dangling two things: real estate deals and close ties with Vladimir Putin.
- During the election, the Russians and Trump appear to have danced towards a quid pro quo agreement, with the Russians offering dirt on Hillary Clinton in exchange for a commitment to sanctions relief, with some policy considerations thrown in.
- During the transition period, Trump’s team took a series of actions that moved towards consummating the deal they had made with Russia, both in terms of policy concessions, particularly sanctions relief, and funding from Russian sources that could only be tapped if sanctions were lifted. The Trump team took measures to keep those actions secret.
- Starting in January 2017, Trump came to learn that FBI was investigating Mike Flynn. His real reasons for firing Flynn remain unreported, but it appears he had some concerns that the investigation into Flynn would expose him personally to investigation.
- After a failed attempt to quash the investigation into his Administration by firing Flynn, Trump grew increasingly angry that Jim Comey wouldn’t provide a quick exoneration without conducting an investigation first, leading to his firing.
May 10, 2017: What did you mean when you told Russian diplomats on May 10, 2017, that firing Mr. Comey had taken the pressure off?
Trump fired Comey just in time to report to Russian Ambassador Sergey Kislyak and Foreign Minister Sergey Lavrov in a meeting the next day that doing took the pressure off he felt because of Russia.
“I just fired the head of the F.B.I. He was crazy, a real nut job. I faced great pressure because of Russia. That’s taken off.” Remarkably, he also felt the need to reassure the Russians that, “I’m not under investigation.”
The reports that Trump’s lawyers need to have clearance because of the inclusion of this meeting in the list of questions suggests Mueller wants to learn more about the meeting beyond the public reports. That may include Trump’s sharing of classified information provided by the Israelis.
May 11, 2017: What did you mean in your interview with Lester Holt about Mr. Comey and Russia?
The day after meeting with the Russians, he told Lester Holt he was going to fire Comey regardless of what Rod Rosenstein recommended. [These are excerpts and a little rough; here’s a partial transcript that leaves out a lot of the Russian comments]
He’s a showboat, he’s a grand-stander, the FBI has been in turmoil, you know that. I know that. Everybody knows that. You take a look at the FBI a year ago, it was in virtual turmoil. Less than a year ago. It hasn’t recovered from that.
[in response to a question about Rosenstein’s recommendation] What I did was I was going to fire Comey. My decision. I was going to fire Comey. There’s no good time to do it, by the way. I was going to fire regardless of recommendation. [Rosenstein] made a recommendation, he’s highly respected. Very good guy, very smart guy. The Democrats like him. The Republicans like him. But regardless of recommendation I was going to fire Comey. Knowing there was no good time to do it.
And in fact when I decided to just do it, I said to myself, I said you know, this Russia thing with Trump and Russia is a made-up story, it’s an excuse by the Democrats for having lost an election that they should have won. And the reason they should have won it is the electoral college is almost impossible for a Republican to win. Very hard. Because you start off at such a disadvantage. So everybody was thinking, they should have won the election. This was an excuse for having lost an election.
I just want somebody that’s competent. I’m a big fan of the FBI. I love the people of the FBI.
As far as I’m concerned, I want that [investigation] to be absolutely done properly. When I did this now, I said I’ll probably, maybe confuse that. Maybe I’ll expand that, you know, lengthen the time because it should be over with, in my opinion, should have been over with a long time ago. ‘Cause all it is, is an excuse but I said to myself, I might even lengthen out the investigation, but I have to do the right thing for the American people.
[in response to question about why he put he was not under investigation in his termination letter] Because he told me that, I mean he told me that. I’ve heard that from others. I had a dinner him, he wanted to have dinner because he wanted to stay on, we had a very nice dinner at the White House very early on. [He asked to have dinner?] A dinner was arranged. I think he asked for the dinner. And he wanted to stay on as the FBI head. And I said, I’ll consider, we’ll see what happens. We had a very nice dinner. And at that time he told me you’re not under investigation. I knew anyway. First of all, when you’re under investigation, you’re giving all sorts of documents and everything. I knew I wasn’t under — and I heard it was stated at the committee, at some committee level, number one. Then during the phone call he said it, then during another phone call he said it. He said it at dinner, and then he said it twice during phone calls.
In one case I called him, in one case he called me.
I actually asked him, yes. I said, if it’s possible, would you let me know, am I under investigation? He said you are not under investigation. All I can tell you is that I know that I’m not under investigation. Personally. I’m not talking about campaigns, I’m not talking about anything else. I’m not under investigation.
[did you ask him to drop the investigation] No. Never. I want the investigation speeded up. Why would we do that? Iw ant to find out if there was a problem with an election having to do with Russia, or anyone else, any other country, I want it to be so strong and so good.
I want somebody that’s going to do a great job.
I think that looking into me and the campaign, I have nothing to do, his was set up by the Democrats. There’s no collusion between me and my campaign and the Russians. The other things is the Russians did not affect the vote.
If Russia hacked, If Russia had to anything to do with our election, I want to know about it. If Russia or anybody elseis trying to interfere with our elections I want to make sure that will never ever happen
[wiretapping] I was surprised [Comey said no spying] but I wasn’t angry. There’s a big thing going on right now, spying, to me that’s the big story.
I want a great FBI Director. I expect that [they will continue investigation].
[Flynn’s access to secrets] My White House Counsel it did not sound like an emergency. She didn’t make it sound that way either in the hearings the other day. It didn’t sound like it had to be done immediately. This man has served for many years. He’s a general. In my opinion a very good person. It would be very unfair to hear from someone we don’t even know to immediately run out and fire a general. We ultimately fired, but we fired for a different reason. Everything plays into it. We fired him because he said something to the Vice President that wasn’t true. He had clearance from the Obama Administration. I think it’s a very unfair thing that the media doesn’t talk about that.
I just sent a letter from one of the most prestigious law firms in the country that I have nothing to do with Russia, I have no investments in Russia, I don’t have property in Russia. I’m in total compliance in every way.
I had the Miss Universe Pageant in Moscow a long time ago. I have a certified letter. I’m not just saying that. I assume he’s gonna give the letter out. No loans, no nothing.
I never thought about it [optics of Lavrov meeting]. What difference does it make.
When I spoke with Putin he asked me whether I’d see Lavrov. I think we had a great discussion having to do with Syria, having to do with the Ukraine. Maybe that discussion will lead to peace.
Ultimately, Trump said several things here (aside from putting into the public record the meetings with Comey, though he got details that can almost certainly be proved wrong wrong). He differentiated between an investigation into himself personally and others, denied asking to halt the investigation into Flynn, provided his bogus self-exoneration claim of not having business ties with Russians. He also reiterated the claim he had been spied on.
May 12, 2017: What was the purpose of your May 12, 2017, tweet?
By this point, Trump and Comey were in a war of credibility. And Trump suggested that he might have tapes of his meetings with Comey.
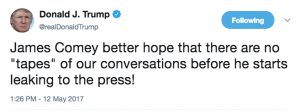
The White House answers about whether there were tapes have dodged some, so it’s possible.
May 17, 2017: What did you think and what did you do in reaction to the news of the appointment of the special counsel?
In the wake of reporting that Comey had documented a request from Trump to halt the investigation into Flynn, on May 17, Rod Rosenstein appointed Robert Mueller to investigate any links between the Russian government and individuals associated with Trump’s campaign and “any matters that arose or may arise directly from the investigation.” The latter phrase made it clear that by firing Comey, Trump had put himself under investigation for obstructing the investigation in chief.
In the middle of a meeting with Sessions, Don McGahn, Mike Pence, and several others on replacing Comey, Rosenstein called McGahn and told him he had appointed Mueller. Trump took it out on Sessions, calling him an idiot and telling him he should resign. Sessions left and sent a resignation letter, but Pence, Steve Bannon, and Reince Priebus convinced him to hold off on accepting it. This piece describes Priebus’ side of that story.
May 31, 2017: Why did you hold Mr. Sessions’s resignation until May 31, 2017, and with whom did you discuss it?
Mueller has received testimony from most of the people who counseled Trump not to fire Sessions, including McGahn, Bannon, and Priebus (but not Pence). He has also gotten Sessions’ testimony on this point.
I’m particularly interested in whether Trump consulted with people not listed in the NYT story on this, such as Jared Kushner and Stephen Miller (who had counseled him to fire Comey in the first place). I also suspect that Trump had already reached out Flynn by this point to talk pardons.
June 8, 2017: What did you think about Mr. Comey’s June 8, 2017, testimony regarding Mr. Flynn, and what did you do about it?
On June 8, Comey testified to SSCI. The night before, he released a statement that reviewed much of what appeared in his memos. The hearing consisted of senators from each party trying to spin Comey’s report of being asked to drop the Flynn investigation, with little news — though Comey did make clear the investigation covered false statements.
BLUNT: On the Flynn issue specifically, I believe you said earlier that you believe the president was suggesting you drop any investigation of Flynn’s account of his conversation with the Russian ambassador. Which was essentially misleading the vice president and others?
COMEY: Correct. I’m not going to go into the details but whether there were false statements made to government investigators, as well.
Comey refuted Trump’s claim that he didn’t ask him to stop the investigation into Flynn.
KING: In his press conference May 18th, the president responded, quote, no, no, when asked about asking you to stop the investigation into general Flynn. Is that a true statement?
COMEY: I don’t believe it is.
Comey said he viewed the Flynn investigation and the Russian one as touching, but separate, though raised the possibility of flipping Flynn.
KING: Back to Mr. Flynn. Would the — would closing out the Flynn investigation have impeded the overall Russian investigation?
COMEY: No. Well, unlikely, except to the extent — there is always a possibility if you have a criminal case against someone and squeeze them, flip them and they give you information about something else. But I saw the two as touching each other but separate.
Comey also revealed that he had shared memos memorializing his conversations with Trump with a friend.
BLUNT: You said something earlier and I don’t want to fail to follow up on, you said after dismissed, you gave information to a friend so that friend could get that information into the public media.
COMEY: Correct.
BLUNT: What kind of information was that? What kind of information did you give to a friend?
COMEY: That the — the Flynn conversation. The president had asked me to let the Flynn — forgetting my exact own words. But the conversation in the Oval Office.
Much of the hearing covered Sessions’ non-involvement. Comey deferred a number of questions to the closed session.
Trump used the Comey hearing — and his confirmation that at the time he left the president wasn’t under investigation — to have Marc Kasowitz make a statement claiming Trump never impeded the investigation and never demanded loyalty.
I am Marc Kasowitz, Predisent Trump’s personal lawyer.
Contrary to numerous false press accounts leading up to today’s hearing, Mr. Comey has now finally confirmed publicly what he repeatedly told the President privately: The President was not under investigation as part of any probe into Russian interference. He also admitted that there is no evidence that a single vote changed as a result of any Russian interference.
Mr Comey’s testimony also makes clear that the President never sought to impede the investigation into attempted Russian interference in the 2016 election, and in fact, according to Mr. Comey, the President told Mr. Comey “it would be good to find out” in that investigation if there were “some ‘satellite’ associates of his who did something wrong.” And he did not exclude anyone from that statement. Consistent with that statement, the President never, in form or substance, directed or suggested that Mr. Comey stop investigating anyone, including suggesting that that Mr. Comey“let Flynn go.” As he publicly stated the next day, he did say to Mr. Comey, “General Flynn is a good guy, he has been through a lot” and also “asked how is General Flynn is doing.”
Admiral Rogers testified that the President never “directed [him] to do anything . . . illegal, immoral, unethical or inappropriate” and never “pressured [him] to do so.” Director Coates said the same thing. The President likewise never pressured Mr. Comey. .
The President also never told Mr. Comey, “I need loyalty, I expect loyalty” in form or substance. Of course, the Office of the President is entitled to expect loyalty from those who are serving in an administration, and, from before this President took office to this day, it is overwhelmingly clear that there have been and continue to be those in government who are actively attempting to undermine this administration with selective and illegal leaks of classified information and privileged communications.
Kasowitz also accused Comey of leaking in order to lead to a special counsel investigation.
Mr. Comey has now admitted that he is one of these leakers. Today, Mr. Comey admitted that he unilaterally and surreptitiously made unauthorized disclosures to the press of privileged communications with the President. The leaks of this privileged information began no later than March 2017 when friends of Mr. Comey have stated he disclosed to them the conversations he had with the President during their January 27, 2017 dinner and February 14, 2017 White House meeting. Today, Mr. Comey admitted that he leaked to friends his purported memos of these privileged conversations, one of which he testified was classified. He also testified that immediately after he was terminated he authorized his friends to leak the contents of these memos to the press in order to “prompt the appointment of a special counsel.” Although Mr. Comey testified he only leaked the memos in response to a tweet, the public record reveals that the New York Times was quoting from these memos the day before the referenced tweet, which belies Mr. Comey’s excuse for this unauthorized disclosure of privileged information and appears to entirely retaliatory. We will leave it the appropriate authorities to determine whether this leaks should be investigated along with all those others being investigated. .
In sum, it is now established that there the President was not being investigated for colluding with the or attempting to obstruct that investigation. As the Committee pointed out today, these important facts for the country to know are virtually the only facts that have not leaked during the long course of these events.
This sort of kicked off the official campaign to discredit Comey and those who would back his story.
June 12, 2017: What did you think and do in reaction to the news that the special counsel was speaking to Mr. Rogers, Mr. Pompeo and Mr. Coats?
Public reports date Rogers and Coats’ interviews with Mueller to the week of June 12, 2017, so Pompeo’s must have been around that same time. Rogers and Coats, at least, testified that Trump tried to get them to state publicly that there was no collusion. They said the interaction was odd and uncomfortable, but that he did not order them to interfere.
Clearly, Trump responded to public reports of their being called as witnesses, though we don’t know what the response was. It’s possible that’s when Trump threatened to fire Mueller, only to back off when Don McGahn threatened to quit.
July 7, 2017: What involvement did you have in the communication strategy, including the release of Donald Trump Jr.’s emails?
I’ve laid out that I believe the evolving June 9 story is a limited hangout orchestrated by Agalarov lawyer Scott Balber. The strategy would have begun when Jared Kushner wrestled with the need to disclose the meeting, both in response to congressional investigations and for his clearance. Manafort, too, turned over emails backing the event about a month before the story came out publicly. This post talks about the response the weekend of the G-20 in Hamburg, including Ivanka sitting in on a meeting so Trump could strategize, and Hope Hicks suggesting the emails would never come out.
As a reminder, on the same day Trump had a second hour long meeting with Putin, he dictated Putin’s propaganda line that the meeting pertained to adoptions. Importantly, he hid what I’ve suggested was the quo in the quid pro quo, sanctions relief. Mueller undoubtedly would like to know if Putin helped him come up with that message, which would be really damning.
Mueller also wants to know about the decision to leak Don Jr’s emails. Bannon suspects that a Jared aide leaked the emails (his then lawyer Jamie Gorelick would cut back her work with him shortly thereafter). But remember: in a DM, Assange proposed that he give Wikileaks the email.
There’s clearly far more back story to the leaked email we don’t know yet.
If Trump’s involvement here involves coordination with Russians (like the Agalrovs, to say nothing of Putin) or Assange, it would provide damning evidence not of obstruction, but of collusion, an effort to coordinate a story about a key meeting. Trump’s lawyers have always suggested questions about Trump’s role in this statement are improper, which is itself a telling indicator that they don’t understand (or want to spin) the risk of the original June 9 meeting.
July 20, 2017: After the resignations, what efforts were made to reach out to Mr. Flynn about seeking immunity or possible pardon?
Mike Flynn tried to get Congressional immunity in March 2017, with Trump’s backing the effort in a tweet.
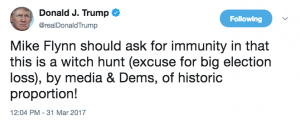
Mueller’s question seems to suggest even at that earlier period, someone from Trump’s camp reached out and discussed immunity with Flynn. Shortly before April 25, Trump also sent Flynn a message to “stay strong.” (h/t TC)
On July 20, the WaPo reported that Trump’s team was researching pardons. The NYT report first revealing that Trump offered pardons to Mike Flynn (and Manafort, who is curiously not mentioned in this question) describes it happening after John Dowd took over, in the wake of the revelation of the June 9 meeting and the Kasowitz firing. Dowd denied any such thing was happening on July 21, which is probably a good sign such discussions were taking place.
July 25, 2017: What was the purpose of your July 2017 criticism of Mr. Sessions? What discussions did you have with Reince Priebus in July 2017 about obtaining the Sessions resignation? With whom did you discuss it?
In late July, 2017, Trump accused Sessions of several sins: failing to crack down on leaks, failing to prosecute Hillary, and failing to fire Andrew McCabe. That must be the same time when Trump ordered Priebus to get Sessions’ resignation, which he dodged by stalling, which probably answers the “what was the purpose” question: to lay predicate to fire Sessions.
I’m particularly interested in the question about who Trump discussed this with, particularly given the provocative timing — the days before George Papadopoulos’s July 26 arrest and Paul Manafort’s July 27 condo search (using a warrant that, unlike a warrant from a May 27 storage unit search, invoked the June 9 meeting). It’s possible Trump had advance knowledge of this stuff (which would be alarming), but likely it’s a coincidence.
In any case, Mueller clearly has reason to believe Trump learned something about the investigation and discussed it with people that led him to try, again, to stop it by firing someone.
What was the purpose of the September and October 2017 statements, including tweets, regarding an investigation of Mr. Comey?
On September 1, Trump responded to reports that because Comey had a declination written before interviewing Hillary, he rigged the outcome of the investigation. In mid-October, in the wake of the Manafort indictment and George Papadopoulos plea, Trump returned to this attack. Rudy Giuliani has renewed this attack in recent days, which is presumably an attempt to undercut Comey’s credibility.
What discussions did you have regarding terminating the special counsel, and what did you do when that consideration was reported in January 2018?
The NYT report that Trump tried to fire Mueller in June 2017 made it clear that Mueller had received testimony about it (presumably from McGahn and others). Clearly, Mueller has reason to know that Trump did something else in response. Note that this report came out in the wake of the Michael Wolff book, which would give Mueller an excuse to call several of the relevant witnesses (such as Mark Corallo and Steve Bannon) as witnesses. This time period also closely follows the increasingly aggressive response in Congress.
What is the reason for your continued criticism of Mr. Comey and his former deputy, Andrew G. McCabe?
The assumption is that Trump continues to attack Comey and McCabe because doing so might harm their credibility with regards to an obstruction investigation, and that’s surely true (made all the worse by McCabe’s firing and his criminal referral).
But I increasingly believe (particularly given that the other contemporaneous witnesses to Comey’s concerns, like James Baker, are not named) that’s not the only reason Trump is doing this. My guess is it’s an attempt to undermine their decision to investigate Flynn. We now know, for example, that McCabe set up the interview with Flynn on Comey’s direction. So in addition to discrediting key witnesses against him, it seems possible that Trump is also trying to discredit the decision, at a time when FBI was about to close a counterintelligence investigation into Flynn, to instead interview him, leading to the exposure of Trump’s efforts to undermine US policy during the transition period.
RESOURCES
These are some of the most useful resources in mapping these events.
Mueller questions as imagined by Jay Sekulow
CNN’s timeline of investigative events
Majority HPSCI Report
Minority HPSCI Report
Trump Twitter Archive
Jim Comey March 20, 2017 HPSCI testimony
Comey May 3, 2017 SJC testimony
Jim Comey June 8, 2017 SSCI testimony
Jim Comey written statement, June 8, 2017
Jim Comey memos
Sally Yates and James Clapper Senate Judiciary Committee testimony, May 8, 2017
NPR Timeline on Trump’s ties to Aras Agalarov
George Papadopoulos complaint
George Papadopoulos statement of the offense
Mike Flynn statement of the offense
Internet Research Agency indictment
Text of the Don Jr Trump Tower Meeting emails
Jared Kushner’s statement to Congress
Erik Prince HPSCI transcript
THE SERIES
Part One: The Mueller Questions Map Out Cultivation, a Quid Pro Quo, and a Cover-Up
Part Two: The Quid Pro Quo: a Putin Meeting and Election Assistance, in Exchange for Sanctions Relief
Part Three: The Quo: Policy and Real Estate Payoffs to Russia
Part Four: The Quest: Trump Learns of the Investigation
Part Five: Attempting a Cover-Up by Firing Comey