USA Freedumber Will Not Get Better in the “Prosecutors” Committee
Having been badly outmaneuvered on USA Freedumber — what was sold as reform but is in my opinion an expansion of spying in several ways — in the House, civil liberties groups are promising a real fight in the Senate.
“This is going to be the fight of the summer,” vowed Gabe Rottman, legislative counsel with the American Civil Liberties Union.
If advocates are able to change the House bill’s language to prohibit NSA agents from collecting large quantities of data, “then that’s a win,” he added.
“The bill still is not ideal even with those changes, but that would be an improvement,” Rottman said.
[snip]
“We were of course very disappointed at the weakening of the bill,” said Robyn Greene, policy counsel at the New America Foundation’s Open Technology Institute. “Right now we really are turning our attention to the Senate to make sure that doesn’t happen again.”
[snip]
One factor working in the reformers’ favor is the strong support of Senate Judiciary Chairman Patrick Leahy (D-Vt.).
Unlike House Judiciary Chairman Bob Goodlatte (R-Va.), who only came to support the bill after negotiations to produce a manager’s amendment, Leahy was the lead Senate sponsor of the USA Freedom Act.
The fact that Leahy controls the committee gavel means he should be able to guide the bill through when it comes up for discussion next month, advocates said.
“The fact that he is the chairman and it’s his bill and this is an issue that he has been passionate about for many years” is comforting, Greene said.
I hope they prove me wrong. But claims this will get better in the Senate seem to ignore the recent history of the Senate Judiciary Committee’s involvement in surveillance bills, not to mention the likely vote counts.
It is true Pat Leahy wants real reform. And he has a few allies on SJC. But in recent years, every surveillance-related bill that came through SJC has been watered down when Dianne Feinstein offered an alternative (which Leahy sometimes adopted as a manager’s amendment, perhaps realizing he didn’t have the votes). After DiFi offered reform, Sheldon Whitehouse (who a number of less sophisticated SJC members look to as a guide on these issues) enthusiastically embraced it, and everyone fell into line. Often, a Republican comes in and offers a “bipartisan reform” (meaning conservative Republicans joining with the Deep State) that further guts the bill.
This is how the Administration (shacking up with Jeff Sessions) defeated an effort to rein in Section 215 and Pen Registers in 2009.
This is how DiFi defeated an effort to close the backdoor loophole in 2012.
As this was happening in 2009, Russ Feingold called out SJC for acting as if it were the “Prosecutors Committee,” rather than the Judiciary Committee.
(Note, in both of those cases as well as on the original passage of Section 702, I understood fairly clearly what the efforts to stymie reform would do, up to 4 years before those programs were publicly revealed; I’ve got a pretty good record on this front!)
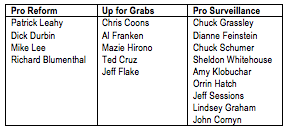
And if you don’t believe this is going to happen again, tell me why this whip count is wrong:
If my read here is right, the best case scenario — short of convincing Sheldon Whitehouse some of what the government wants to do is unconstitutional, which John Bates has already ruled that it is — is relying on people like Ted Cruz (whose posturing on civil liberties is often no more than that) and Jeff Flake (who was great on these issues in the House but has been silent and absent throughout this entire debate). And that’s all to reach a 9-9 tie in SJC.
Which shouldn’t be surprising. Had Leahy had the votes to move USA Freedom Act through SJC, he would have done so in October.
That was the entire point of starting in the House: because there was such a large number of people (albeit, for the most part without gavels) supporting real reform in the House. But because reformers (starting with John Conyers and Jerry Nadler) uncritically accepted a bad compromise and then let it be gutted, that leverage was squandered.
Right now, we’re looking at a bill that outsources an expanded phone dragnet to the telecoms (with some advantages and some drawbacks), but along the way resets other programs to what they were before the FISC reined them in from 2009 to 2011. That’s the starting point. With a vote count that leaves us susceptible to further corruption of the bill along the way.
Edward Snowden risked his freedom to try to rein in the dragnet, and instead, as of right now it looks like Congress will expand it.
Update: I’ve moved Richard Blumenthal into the “pro reform” category based on this statement after the passage of USA Freedumber. Thanks to Katherine Hawkins for alerting me to the statement.