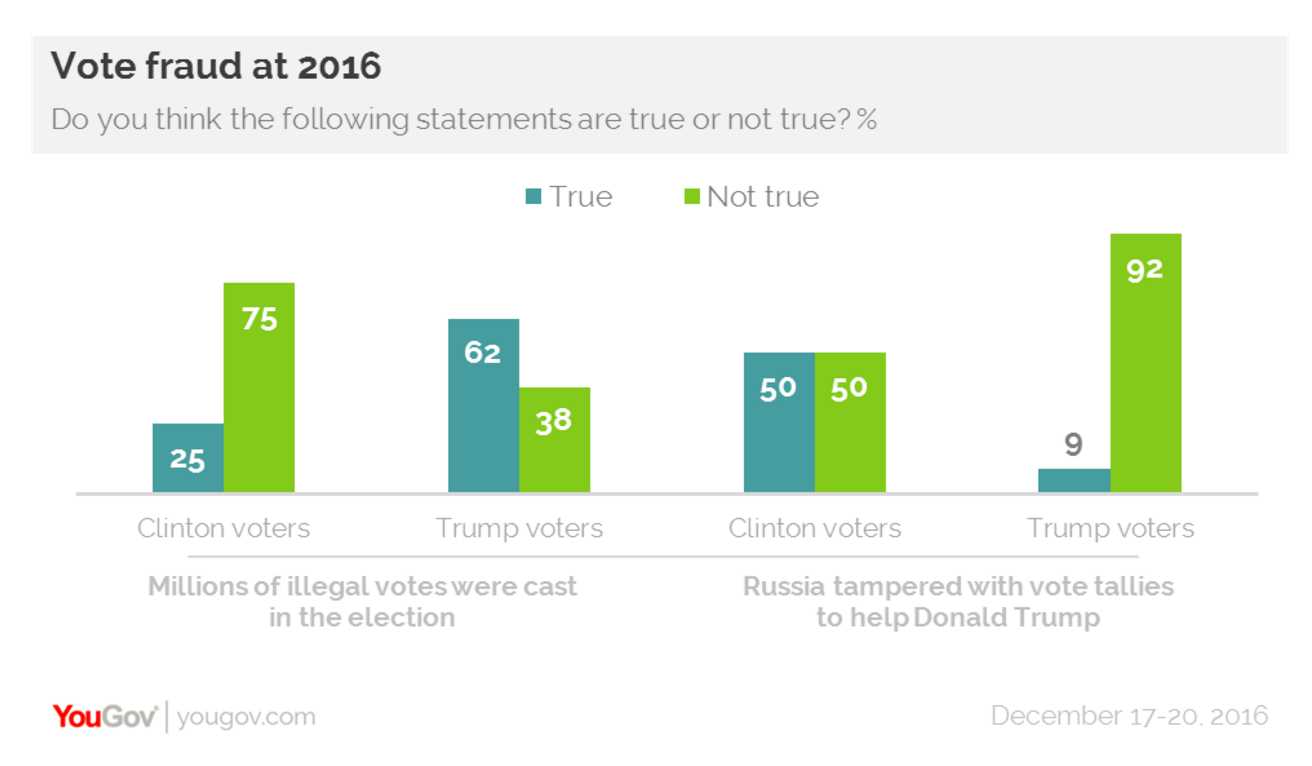
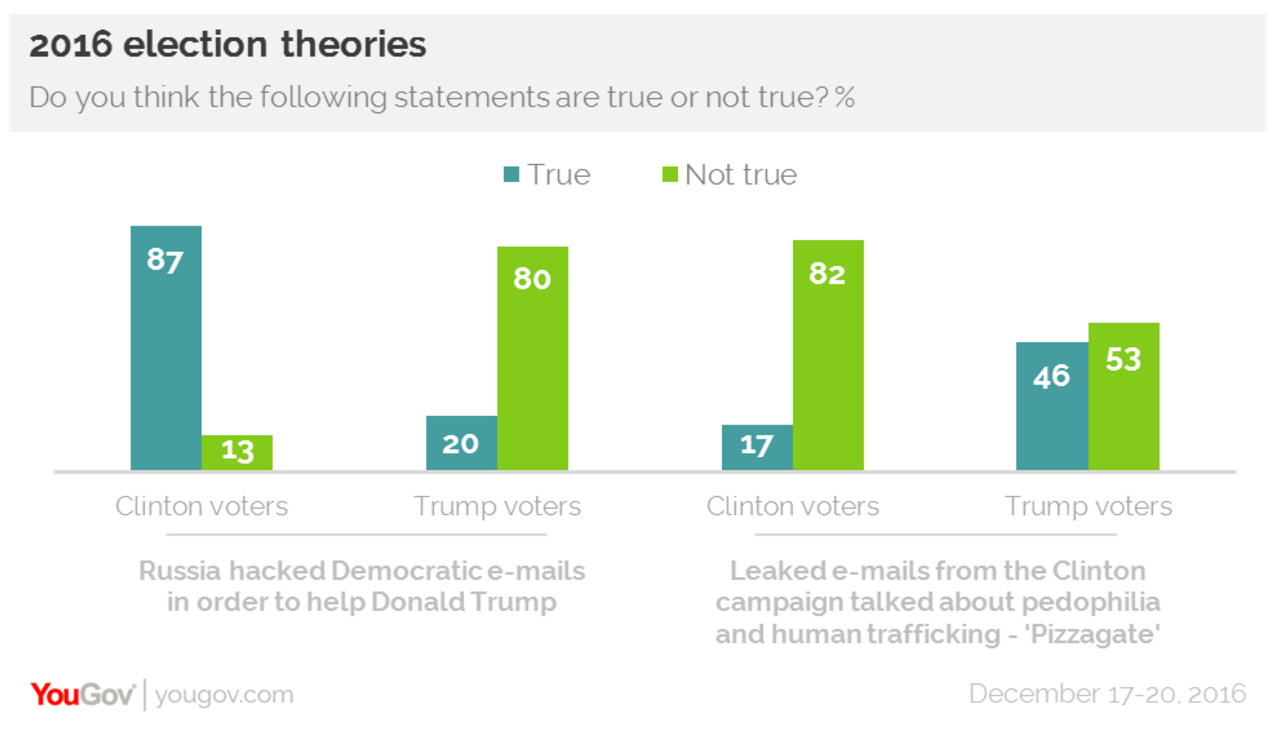
The Significance of the December 13 Trump Dossier Report
John Brennan and Donald Trump are in a fight.
In his press conference last week, Trump called out the intelligence community for “allowing … information that turned out to be so false and fake” out, likening the leak to something that would happen in Nazi Germany.
I think it was disgraceful, disgraceful that the intelligence agencies allowed any information that turned out to be so false and fake out. I think it’s a disgrace. And I say that and I say that.
And that’s something that Nazi Germany would have done and did do. It’s a disgrace. That information that was false and fake and never happened got released to the public, as far as BuzzFeed, which is a failing pile of garbage, writing it, I think they’re going to suffer the consequences.
Over the weekend, Brennan went on Fox News to scold Trump for the Nazi analogy. At that appearance, he said this about the release of the dossier.
I think as the Director of National Intelligence said in his statement, this is information that’s been out there, circulating, for many months. So it’s not a question of the intelligence community leaking or releasing this information. It was already out there.
[snip]
There is no basis for Mr. Trump to point fingers at the intelligence community for leaking information that was already available publicly.
In response to Brennan’s appearance (and his suggestion Trump didn’t know what the fuck he was doing in Syria and Russia), Trump insinuated that Brennan may have leaked the dossier.
Let’s unpack this. Because while I have no idea who leaked the document (though I highly doubt Brennan would have done so personally), the intelligence community’s claims are really suspect.
As I noted last week, the James Clapper statement rather bizarrely claimed the IC was the last to know about the document. The dossier, according to Clapper, was “widely circulated in recent months among the media, members of Congress and Congressional staff even before the IC became aware of it.”
That (as some people have pointed out) cannot be true.
The stories about what Christopher Steele did when have been evolving. But David Corn’s description, based off a conversation that occurred before the IC started making public claims, strongly suggests that Steele started sharing documents with the FBI “soon” after “the end of June.”
By the end of June, he was sending reports of what he was finding to the American firm.
The former spy said he soon decided the information he was receiving was “sufficiently serious” for him to forward it to contacts he had at the FBI. He did this, he said, without permission from the American firm that had hired him. “This was an extraordinary situation,” he remarked.
Some other reports, based off claims made after the Clapper statement, put this date later — maybe August — even while the implication has always been that the FBI request for a FISA warrant in June stems from these reports.
Even if that information sharing dates to August, however, it would mean the FBI — a member of the IC — had regular updates from the dossier at least by then, if not by June. Sure, you might claim that FBI investigative teams are not part of the IC, but given that this would be a counterintelligence investigation, that’d be a laughable claim.
In other words, even assuming the claims about where the dossier came from and who paid for it are true, the IC was not the last to know, but one of the first.
There are two other dates of note that go into the claim the dossier was widely circulated before it got briefed to Trump this month. We know that the IC briefed the Gang of Eight on this dossier in October. Shortly thereafter, Corn received a copy of the dossier and wrote about it (though he has not revealed who gave it to him). Then in December, John McCain got a copy from Sir Andrew Wood. According to a Guardian article published around 9AM on the same day as the Clapper statement, McCain had not only received the dossier, but handed it over — yet another copy — to the FBI on December 9.
Senator John McCain, who was informed about the existence of the documents separately by an intermediary from a western allied state, dispatched an emissary overseas to meet the source and then decided to present the material to Comey in a one-on-one meeting on 9 December, according to a source aware of the meeting. The documents, which were first reported on last year by Mother Jones, are also in the hands of officials in the White House.
McCain, in a statement released midday on the day of the Clapper statement, is more vague about the hand-off date, describing it only as “late last year.”
I’m working on the specific times, but it is significant that the Guardian with the exact date came out in the morning on January 11, the vague McCain statement came out mid-day sometime, and Clapper’s statement came out that evening.
That’s significant because some people assume that McCain is the one who released the dossier — the dossier he received on December 9.
If that date is correct, the dossier couldn’t have come from McCain, because the last report in the dossier is dated four days later, December 13.
Very significantly, this last report, which talks about the Russian cover-up of the hack, alleges “the operatives involved had been paid by both TRUMP’s team and the Kremlin.” This is, in my opinion, one of the most incendiary claims in the entire dossier — that Trump not only encouraged Russia’s campaign, but paid operatives involved in it.
Just as significantly, the date completely undermines the substance of Brennan’s defense. When he says, “this is information that’s been out there, circulating, for many months. … It was already out there. … There is no basis for Mr. Trump to point fingers at the intelligence community for leaking information that was already available publicly,” he’s wrong. The full set of information released to BuzzFeed — including the allegation Trump paid for this operation — actually hasn’t been out there, because it post-dates all known circulation of the document.
Also remember that journalists have suggested they got copies of the dossier that redacted all the sources. This one didn’t. At least one likely source named in the report has died in curious circumstances since the release of the report.
I really have no idea where the dossier got leaked from — that is one reason I’m so interested in artifacts in the document that may raise questions about the provenance of the released dossier. I also wouldn’t, at this point, be surprised if Trump were getting his own stream of intelligence, possibly even from Russia, about where and how it got released.
But thus far, the IC’s claims about the dossier are even more dodgy than Trump’s, which is saying something.