Laura Poitras has another piece in Spiegel laying out NSA’s spying on diplomats — this time focusing on how NSA acquired blueprints of the new EU building in NYC to facilitate tapping it all.
To a significant degree, Poitras lays out how the NSA does what other countries at least try to do as well. While the US has certain advantages in conducting such spying (like having the UN headquartered in NYC and dominating telecom infrastructure), in principle it is assumed spy agents will spy on senior people from other countries.
But a key point of Poitras’ piece is that top officials — up to and including President Obama — have led the American people to believe all this spying focuses only terrorism. Indeed, she points to a line of the speech Obama gave a few weeks back that suggested terrorism was the only reason the government conducted this dragnet (this is the full quote — Poitras breaks up the quote into two; I think it is slightly more ambiguous but at the same time more assertive like this).
I think the main thing I want to emphasize is I don’t have an interest and the people at the NSA don’t have an interest in doing anything other than making sure that where we can prevent a terrorist attack, where we can get information ahead of time, that we’re able to carry out that critical task. We do not have an interest in doing anything other than that.
This was a response to a journalists’ question, not part of Obama’s prepared speech. Nevertheless, the President stood up publicly and claimed that the NSA does not “have an interest in doing anything other than … prevent[ing] a terrorist attack.”
That is a false statement.
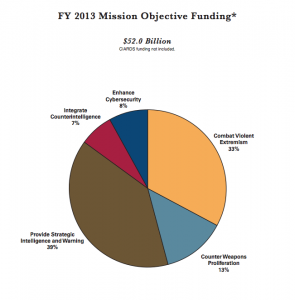
Had Obama said preventing terrorism was one of several primary goal, the reported sole focus of the US person phone records dragnet, had he said that he and the NSA have other interests, it might be a fair comment. But it is not the case that the only interest of the NSA is to find advance intelligence on potential terrorist attacks.
And, as Poitras also points out, Obama made these comments in an effort to make people trust the dragnet. The comment came in direct response to a question about trust.
I wanted to ask you about your evolution on the surveillance issues. I mean, part of what you’re talking about today is restoring the public trust. And the public has seen you evolve from when you were in the U.S. Senate to now. And even as recently as June, you said that the process was such that people should be comfortable with it, and now you’re saying you’re making these reforms and people should be comfortable with those. So why should the public trust you on this issue, and why did you change your position multiple times?
And it came in a speech where Obama talked about trust a number of times, including offering his asinine dishwashing metaphor.
Q Can you understand, though, why some people might not trust what you’re saying right now about wanting to —
THE PRESIDENT: No, I can’t.
Q — that they should be comfortable with the process?
THE PRESIDENT: Well, the fact that I said that the programs are operating in a way that prevents abuse, that continues to be true, without the reforms. The question is how do I make the American people more comfortable.
If I tell Michelle that I did the dishes — now, granted, in the White House I don’t do the dishes that much — (laughter) — but back in the day — and she’s a little skeptical, well, I’d like her to trust me, but maybe I need to bring her back and show her the dishes and not just have her take my word for it.
And so the program is — I am comfortable that the program currently is not being abused. I’m comfortable that if the American people examined exactly what was taking place, how it was being used, what the safeguards were, that they would say, you know what, these folks are following the law and doing what they say they’re doing.
But it is absolutely true that with the expansion of technology — this is an area that’s moving very quickly — with the revelations that have depleted public trust, that if there are some additional things that we can do to build that trust back up, then we should do them. [my emphasis]
Obama suggests Snowden’s revelations — and not his, James Clapper’s, and Keith Alexander’s lies about the programs — have chipped away at trust. In a press conference in which Obama falsely claimed this was solely about terrorism.
If Obama and everyone else want to start rebuilding credibility, they need to stop lying, and get rid of the more substantive liars like Clapper and Alexander. But they also need to square with the American people about what this dragnet is for. Congress has repeatedly rejected internet-based surveillance to protect Hollywood IP and to socialize the private cybersecurity risk of corporate owners of critical infrastructure. Even Congress doesn’t approve the use of this technology for some applications.
And until the government stops pretending this is exclusively about terrorism, and stops pretending that terrorism is an existential threat or even the country’s greatest one, it will continue to lose credibility.