Bombshell “New[s]:” Jack Smith DID Consult about Timing before Adopting Post-SCOTUS Path
After I wrote this post laying out that Elie Honig was not only wrong about Jack Smith’s immunity briefing, but that it was very likely DOJ had decided not to take certain steps in August because of the election, I thought about sending the post to Jack Goldsmith, because he tends to make claims about Jack Smith violating DOJ guidelines with little understanding of the facts.
Whereas Honig dedicated just one paragraph to asserting that the problem here lay in “new” disclosures,
The immediate takeaway lies in the revelations contained in Smith’s oversize brief. (He asked the judge for, and received, permission to file a brief that was 180 pages long, four times the normal maximum.) We now have damning new details on Trump’s effort to pressure Vice-President Mike Pence to throw the election his way, Trump’s phone use and use of Twitter as the riot unfolded, and his conversations with family members about efforts to contest his electoral loss. The story’s structure is the same as we’ve long known, but the new details lend depth and dimension.
Goldsmith repeated his claim that there were “new” disclosures in Jack Smith’s immunity filing four times, starting in the lead paragraph.
Last week a judge unsealed a 165-page legal brief with damaging new revelations about President Donald Trump’s efforts to overturn the 2020 presidential election.
[snip]
The brief he filed last week sought to show that the election prosecution can continue despite the Supreme Court’s immunity ruling. It laid out the government’s case against Mr. Trump with what many media reports described as “bombshell” new details about his wrongdoing. The filing is in clear tension with the Justice Department’s 60-day rule, which the department inspector general has described as a “longstanding department practice of delaying overt investigative steps or disclosures that could impact an election” within 60 days of an election. However, the “rule” is unwritten and, as the inspector general made clear, has an uncertain scope.
[snip]
Perhaps the department thinks the new disclosures are marginal and won’t affect the election, or that the rule does not apply to litigation steps in previously indicted cases, even if they would affect the election.
[snip]
Because it didn’t need to disclose the new details now, and because it was foreseeable that the disclosures would cause approximately half the country to suspect the department’s motives, it is hard to understand any reason to go forward this close to the election other than to influence it — a motive that would clearly violate department policy.
New new new new.
Bombshell!
I’ll note, I was not among the allegedly “many media reports” that declared I had found “‘bombshell’ new details.” Nor was Brandi Buchman, in her new gig at HuffPo. Nor were Politico’s Kyle Cheney and Josh Gerstein. While a subhed of the WaPo story on the brief promised “new” details, the story itself describes that we knew most of this before.
Much of the evidence against Trump in the case had already become public, either through previous filings, news reports or an extensive congressional investigation into the events of Jan. 6.
Tellingly, while NYT devoted a section of their four takeaways piece to “new” evidence, they specifically said none of this was “game-changing.”
The prosecutor revealed new evidence.
The brief contained far more detail than the indictment and included many specific allegations that were not previously part of the public record of the events leading up to the attack on the Capitol by a mob of Trump supporters on Jan. 6, 2021.
None of the new details were game-changing revelations, but they add further texture to the available history. For example, part of the brief focuses on a social media post that Mr. Trump sent on the afternoon of the attack on the Capitol, telling supporters that Vice President Mike Pence had let them all down.
Mr. Trump was sitting alone in the dining room off the Oval Office at the time. According to the brief, forensic data shows he was using the Twitter app on his phone and watching Fox News. Fox had just interviewed a man who was frustrated that Mr. Pence was not blocking the certification and then reported that a police officer may have been injured and the protesters had breached the Capitol.
Mr. Trump posted to Twitter that Mr. Pence had lacked the “courage” to do what was right. The mob became enraged at the vice president, and the Secret Service took him to a secure location. An aide to Mr. Trump rushed in to alert him to the peril Mr. Pence was in, but Mr. Trump looked at the aide and said only, “So what?” according to the brief. [my emphasis]
And much of this isn’t new.
We learned prosecutors were going to rely on forensic data from an expert notice submitted in December. The original indictment revealed that Trump was alone in his dining room when he sent the Tweet targeting Mike Pence. The superseding indictment added to the existing description in the original indictment that Trump was “watch[ing] events unfold” that his TV was showing “live coverage.” If you couldn’t already guess that meant he was watching Fox News, the January 6 Committee told us that in hearings and their final report. The actual content shown on Fox News at that moment is new to court filings, but it is publicly available. The Tweet itself, of course, has been discussed in detail starting from Trump’s impeachment. The Nick Luna comment, “So what?”, is new, but simply a better sourced version of Cassidy Hutchinson’s far more damning hearsay testimony of Mark Meadows telling Pat Cipollone that Trump thought Pence “deserves it” even as his supporters chanted “hang Mike Pence.”
The CNN piece that Honig linked to substantiate his claim this was new described that the filing provided “fullest picture yet of [Jack Smith’s] 2020 election case,” not that these were bombshells. It described “new” details to include:
Trump’s frayed relationship with former Vice President Mike Pence; FBI evidence of Trump’s phone usage on January 6, 2021, when rioters overtook the US Capitol; and conversations with family members and others where the then-president was fighting his loss to Joe Biden.
Those details of Trump’s phone usage — as I noted above — were actually covered in earlier filings and even the indictments. The one new attribution to a conversation with Trump’s family members — the “fight like hell” claim — is important mostly because it echoed the very public exhortation in the January 6 speech we all saw four years ago. And virtually all the references in the brief about Trump’s frayed relationship with Pence are parallel sourced to Mike Pence’s book, published years ago.
What Goldsmith cites instead of the NYT, where his op-ed was published (which, many people complained, didn’t play up the brief enough), was this ABC story. It promises stuff that is new, but then lists a bunch of stuff we knew already.
Special counsel Jack Smith has outlined new details of former President Donald Trump and his allies’ sweeping and “increasingly desperate” efforts to overturn his 2020 election loss, in a blockbuster court filing Wednesday aimed at defending Smith’s prosecution of Trump following the Supreme Court’s July immunity ruling.
Trump intentionally lied to the public, state election officials, and his own vice president in an effort to cling to power after losing the election, while privately describing some of the claims of election fraud as “crazy,” prosecutors alleged in the 165-page filing.
And it doesn’t substantiate its claims that this stuff is new.
For example, the immunity filing explains how prosecutors know that Trump called Sidney Powell “crazy:” after Tucker Carlson ripped her to shreds, Trump let Dan Scavino and P7 — who may be Hope Hicks — listen to a conversation with Powell on speakerphone while he mocked her. That he called her crazy was included in the original indictment’s description of Powell.
One other thing some blow-ins to this story claimed was new — Mike Roman’s instruction to “Make them riot” — was also something already revealed in a December filing.
What Honig and Goldsmith are all worked up about is not new news, but editors who, trying to hype stories about this filing, felt the need to oversell the amount of new news in it.
Their concern arises out of click-bait, not the substance of the immunity filing itself.
And from that, Goldsmith scolds that Smith should have justified filing this brief in response to an order from Judge Chutkan.
[T]he department has not publicly justified its actions in the election prosecution, and its failure to do so in this highest-of-stakes context is a mistake.
Only, even Goldsmith’s claim that the department didn’t justify its actions is not entirely accurate.
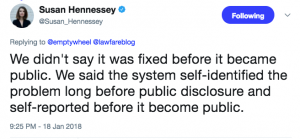
Jack Smith hasn’t told us what internal DOJ deliberations were. But he did publicly reveal that before he did anything in the wake of the SCOTUS remand, he spent most of a month “consult[ing] with other Department of Justice components” regarding DOJ “rules, regulations … and policies” about “the most appropriate schedule” moving forward.
The Government continues to assess the new precedent set forth last month in the Supreme Court’s decision in Trump v. United States, 144 S. Ct. 2312 (2024), including through consultation with other Department of Justice components. See 28 C.F.R. § 600.7(a) (“A Special Counsel shall comply with the rules, regulations, procedures, practices and policies of the Department of Justice,” including “consult[ing] with appropriate offices within the Department for guidance with respect to established practices, policies and procedures of the Department . . . .”). Although those consultations are well underway, the Government has not finalized its position on the most appropriate schedule for the parties to brief issues related to the decision.
DOJ is never going to reveal these deliberations (and Jack Goldsmith knows that better than most, given the number of far more important internal deliberations involving Goldsmith himself, dating to two decades ago, that we’ve never been allowed to and won’t ever be allowed to see).
But they did tell us they engaged in them. Jack Smith literally told us that he was spending weeks consulting about how to comply with DOJ policies regarding timing even before he superseded the indictment.
Only that detail — the one that they keep harping about — appears to be news to Honig and Goldsmith.
So chalk this up to yet another instance where the people complaining about what Jack Smith did, instead, only reveal they don’t know what Jack Smith did.
Update: Trump submitted, under seal, another request not to have any evidence released before the election. It cites both Honig and Goldsmith. Neither, of course, address the point Trump claims to be making.
President Trump maintains his objections, see ECF No. 248, based on overt and inappropriate election interference, violations of longstanding DOJ policy, the Office’s previous safety-related representations in this District and the Southern District of Florida, grand jury secrecy, and the influence on potential witnesses and jurors of prejudicial pretrial publicity—which predictably followed from the filing of the redacted “Motion for Immunity Determinations.”2
2 See, e.g., Ellie Honig, Jack Smith’s October Cheap Shot, N.Y. Magazine (Oct. 3, 2024), https://nymag.com/intelligencer/article/jack-smith-october-surprise-donald-trump.html; see also Jack Goldsmith, Jack Smith Owes Us an Explanation, N.Y. Times (Oct. 9, 2024), https://www.nytimes.com/2024/10/09/opinion/jack-smith-trump-biden.html.
Trump’s deadline to submit objections to Jack Smith’s proposed redactions is today at 5PM ET. Last time, when Trump made no substantive suggestions, Judge Chutkan released the file.










![[Photo: National Security Agency, Ft. Meade, MD via Wikimedia]](https://www.emptywheel.net/wp-content/uploads/2017/08/NationalSecurityAgency_HQ-FortMeadeMD_Wikimedia.jpg)