By my count, at least 14 people are known to have pled guilty to some kind of conspiracy on January 6, with four more cooperating against them. Another four were found guilty of one or more conspiracy in November’s Oath Keeper verdict. Eighteen people, in one way or another have been convicted of conspiring to prevent the peaceful transfer of power on January 6, most by obstructing the vote certification.
Trump played a key part in all those conspiracies.
Ronnie Sandlin, for example, first started planning to go, armed, to DC in response to Trump’s December 19 tweet, posting on December 23 that he planned to “stop the steal and stand behind Trump when he decides to cross the rubicon.” After he watched Trump’s speech on January 6, Sandlin did a live stream where he said, “I think it is time to take the Capitol.” Once he arrived at the Capitol, Sandlin and co-conspirator Nate DeGrave participated in tactically critical assaults on cops in two places, the East door and the door to the Senate gallery. After Sandlin helped him get into the gallery, Josiah Colt then rappelled from the gallery to the Senate floor.
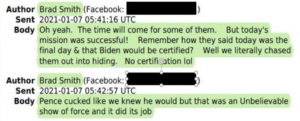
Like Sandlin, Brad Smith started arming himself and planning to come to DC in response to Trump’s December 19 tweet.
The call to action was put out to be in DC on January 6th from the Don himself. The reason is that’s the day pence counts them up and if the entire city is full of trump supporters it will stop the for sure riots from burning down the city at least for awhile.
By December 31, Smith predicted, “Militias will be there and if there’s enough people they may fucking storm the buildings and take out the trash right there.” Smith and his co-conspirator, Marshall Neefe, participated in an assault on cops using an 8′ by 10′ Trump sign. And after the attack he boasted that the mission was successful because “we literally chased them out into hiding. No certification lol.”
Trump played a slightly different role in the Oath Keepers conspiracy. The Oath Keepers — Stewart Rhodes above all — viewed Trump as a means to prevent Biden’s election, because as President he could invoke the Insurrection Act and with it (the Oath Keepers believed) make the militias a legal arm of the state, defending Trump. Rhodes repeatedly called on Trump to invoke the Insurrection Act — on November 9, December 12, December 23, and January 6.

He dictated a note to Trump after January 6 asking him to call on the militias as his army to stop Biden from taking power.
For the most part, none of the channels via which Rhodes tried to speak directly to Trump (including Kellye SoRelle’s attempt to work through Rudy Giuliani’s son) are known to have reached Trump.
One of his attempted interlocutors, though, undoubtedly had access to Trump: Roger Stone, on whose Friends of Stone list Rhodes was sharing his plans for insurrection shortly after the election.

DOJ has exploited at least four phones owned by members of the Friends of Stone list: Rhodes and SoRelle, Owen Shroyer, and Enrique Tarrio. Probably DOJ asked for content from Ali Alexander as well (though he disclaimed having any Signal texts to the January 6 Committee).
While a jury found all the Oath Keepers guilty of obstructing the vote certification, with the key exception of Kelly Meggs (who was also in contact separately with the Proud Boys, Roger Stone, Ali Alexander, and alleged 3 Percenter Jeremy Liggett, who in turn had ties to the MAGA Bus Tour) as well as Jessica Watkins, it found the greater part of their conspiracy either overthrowing the government or interfering with with official duties: not obstructing the vote count. Their larger plan to keep Trump in power used different means than Trump used.
That’s not true of the Proud Boy Leaders, who are three days into their trial.
Not only did the Proud Boys allegedly pursue the same plan that Trump was pursuing — obstructing the vote certification on January 6 — but they were in communication with people who were in communication, and central to, Trump’s plan: most notably, Alex Jones, Ali Alexander, and Roger Stone. They were in communication with people who were in communication with people close to Trump during the attack.
Even their telephony records show that Enrique Tarrio, Joe Biggs, and Ethan Nordean were in contact with Alex Jones and Owen Shroyer during the period.
Records for Enrique Tarrio’s phone show that while the attack on the Capitol was ongoing, he texted with Jones three times and Shroyer five times.124 Ethan Nordean’s phone records reflect that he exchanged 23 text messages with Shroyer between January 4th and 5th, and that he had one call with him on each of those days.125 Records of Joseph Biggs’s communications show that he texted with Shroyer eight times on January 4th and called him at approximately 11:15 a.m. on January 6th, while Biggs and his fellow Proud Boys were marching at and around the Capitol.126
Given the known communication habits of the men, it’s possible there are Signal or Telegram communications that were unavailable to the J6C as well.
Alex Jones and Ali Alexander knew in advance they would lead the mob to the Capitol (the January 6 Report offers an unpersuasive explanation that the request came exclusively from Caroline Wren). Roger Stone had planned to join them, probably until he got cranky about being denied a speaking role on the morning of January 6. Mike Flynn wanted to latch on, as well, until the General got too cold and had to go back to his posh hotel room. “Hell no,” he said, according to Caroline Wren. “It’s freezing.”
Meanwhile, even as Shroyer was in touch with Biggs, Alexander was in touch with Caroline Wren, who remained at the Ellipse, and asked for 5-minute updates on the Trump’s progress to the Capitol (the text in question appears to have come from Wren, but may not have been provided in Alexander’s production).
The communication between Proud Boys and Jones in real time is critical because once the riot police showed up and slowed the attack, the Proud Boy leaders pulled up, effectively waiting until Jones appeared. And after Jones did appear, he told the mob following him that Trump was coming to give another speech — something Alexander, and so almost certainly Jones — knew to be false because Wren had told Alexander. Nevertheless, Jones led his mob to the East steps, riled them up with a 1776 chant, and left them there, where they were soon joined by the Oath Keepers (led by Kelly Meggs, who also was in touch with Alexander) and Joe Biggs and some other Proud Boys (including one who had been directing traffic). That collective mob breached the East door of the Capitol, opening a second major front on the Capitol and adding to the invasion of the Senate chamber.
There are rioters who were sentenced to two months in jail because they followed Alex Jones credulously to the top of those steps and joined the mob storming the Capitol.
And it wasn’t just Jones and Alexander who were in touch with Trump’s handlers.
Mark Meadows was, per Cassidy Hutchinson, in communication with Stone about his plans for January 6, at a time when Stone still planned to march to the Capitol with Jones and Alexander.
LIZ CHENEY: Thank you, Mr. Chairman. Before we turn to what Ms. Hutchinson saw and heard in the White House during the violent attack on the Capitol on January 6th, let’s discuss certain communications White House Chief of Staff Mark Meadows had on January 5th. President Trump’s associate, Roger Stone, attended rallies during the afternoon and the evening of January 5th in Washington, DC On January 5th and 6th, Mr. Stone was photographed with multiple members of the Oath Keepers who were allegedly serving as his security detail.
As we now know, multiple members of that organization have been charged with or pled guilty to crimes associated with January 6th. Mr. Stone has invoked his Fifth Amendment privilege against self-incrimination before this committee. General Michael Flynn has also taken the Fifth before this committee. Mr. Stone previously had been convicted of other federal crimes unrelated to January 6th.
General Flynn had pleaded guilty to a felony charge, also predating and unrelated to January 6th. President Trump pardoned General Flynn just weeks after the Presidential election, and in July of 2020, he commuted the sentence Roger Stone was to serve.
The night before January 6th, President Trump instructed his Chief of Staff Mark Meadows to contact both Roger Stone and Michael Flynn regarding what would play out the next day. Ms. Hutchinson, Is it your understanding that President Trump asked Mark Meadows to speak with Roger Stone and General Flynn on January 5th?
CASSIDY HUTCHINSON: That’s correct. That is my understanding.
LIZ CHENEY: And Ms. Hutchinson, is it your understanding that Mr. Meadows called Mr. Stone on the 5th?
CASSIDY HUTCHINSON: I’m under the impression that Mr. Meadows did complete both a call to Mr. Stone and General Flynn the evening of the 5th.
In an earlier interview, when she was still represented by Stefan Passantino, she had attributed the idea for this call to Peter Navarro or a Navarro staffer; the Navarro staffer who had let Mike Flynn into the White House on December 18, Garrett Ziegler, was another White House contact of Ali Alexander’s, in addition to Wren.
All this matters because of the way conspiracy law works, as laid out in the bullet points from Elizabeth de la Vega that I always rely on.
CONSPIRACY LAW – EIGHT THINGS YOU NEED TO KNOW.
One: Co-conspirators don’t have to explicitly agree to conspire & there doesn’t need to be a written agreement; in fact, they almost never explicitly agree to conspire & it would be nuts to have a written agreement!
Two: Conspiracies can have more than one object- i.e. conspiracy to defraud U.S. and to obstruct justice. The object is the goal. Members could have completely different reasons (motives) for wanting to achieve that goal.
Three: All co-conspirators have to agree on at least one object of the conspiracy.
Four: Co-conspirators can use multiple means to carry out the conspiracy, i.e., releasing stolen emails, collaborating on fraudulent social media ops, laundering campaign contributions.
Five: Co-conspirators don’t have to know precisely what the others are doing, and, in large conspiracies, they rarely do.
Six: Once someone is found to have knowingly joined a conspiracy, he/she is responsible for all acts of other co-conspirators.
Seven: Statements of any co-conspirator made to further the conspiracy may be introduced into evidence against any other co-conspirator.
Eight: Overt Acts taken in furtherance of a conspiracy need not be illegal. A POTUS’ public statement that “Russia is a hoax,” e.g., might not be illegal (or even make any sense), but it could be an overt act in furtherance of a conspiracy to obstruct justice.
Co-conspirators don’t all have to meet in a room together and agree to enter a conspiracy. That can happen (and did, in the Oath Keepers’ case) via a series of communications which networks everyone.
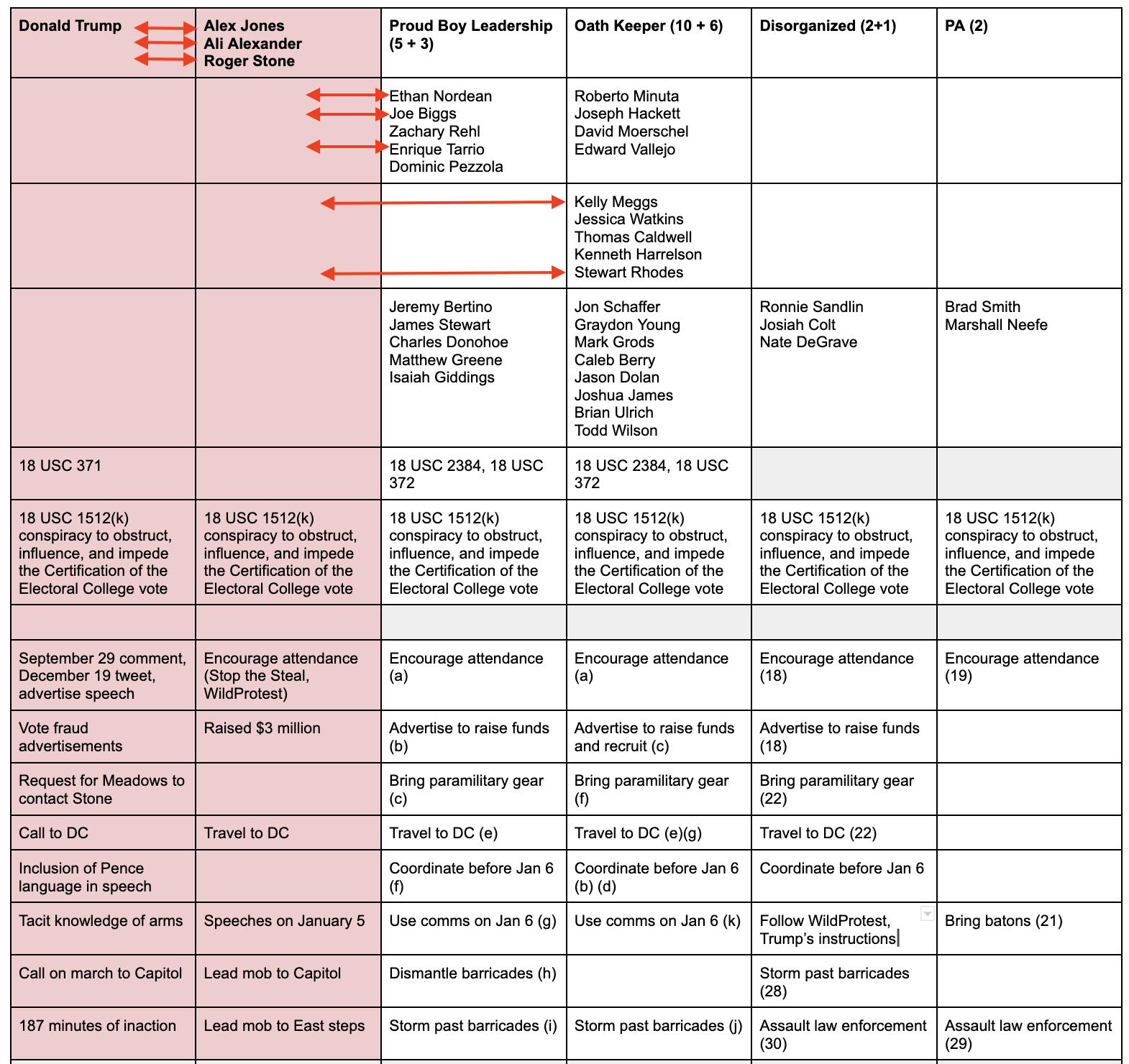
The demonstrative exhibit prosecutors used in the Oath Keeper trials showed how the various communications channels included everyone, even if some members of the conspiracy only interacted with a limited group of other co-conspirators.

I circled Rhodes and SoRelle in pink to show that even in the Oath Keeper trial, prosecutors treated the Friends of Stone list part of the communications infrastructure of the conspiracy.
Here’s what the larger conspiracy looks like, reflecting the known communications between Rhodes, Meggs, Tarrio, Biggs, and Nordean and Jones and Stone, and the known communications between Jones and Stone and Alexander with Trump or his handlers, like Meadows, Wren, and Ziegler by way of Navarro.
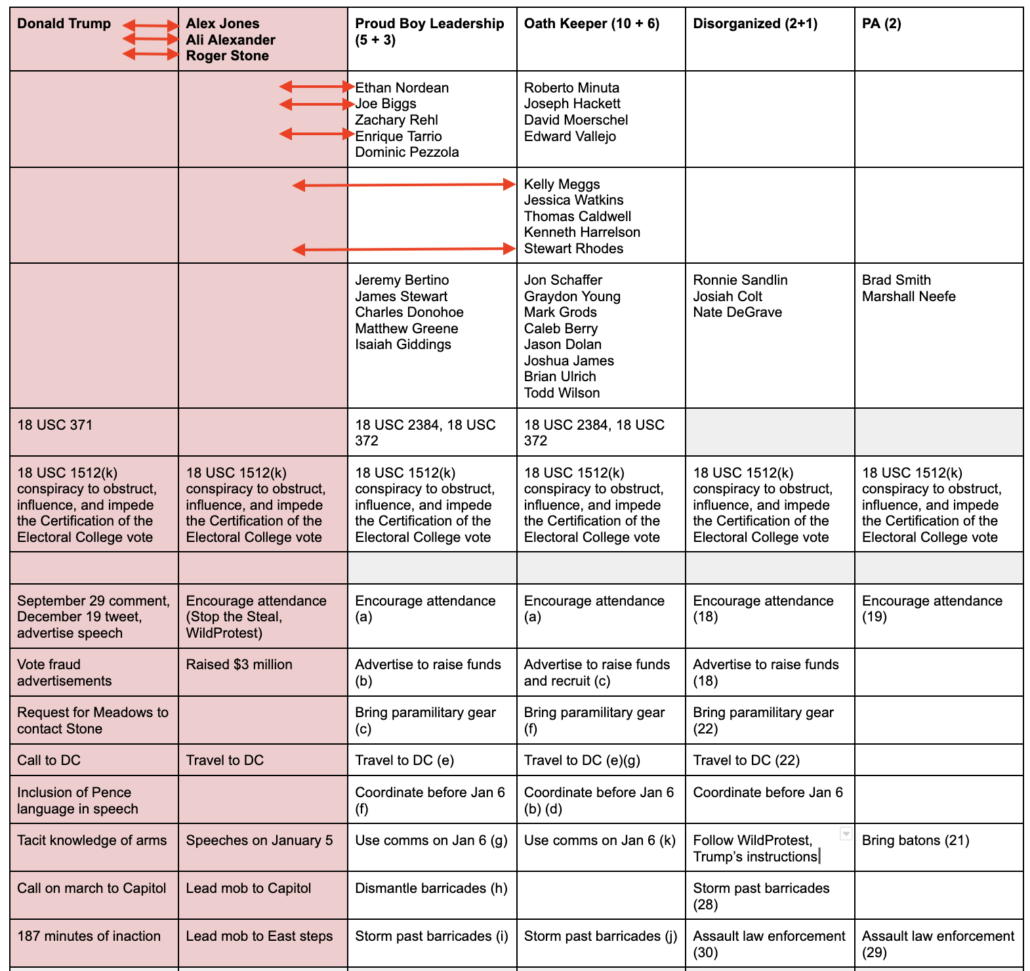
The numbers and letters in parentheses come from one or another of the indictments charging conspiracy. As you can see, Trump’s known actions map onto the known, charged overt acts of various conspiracies to obstruct the vote count like a mirror.
Obviously, the pink part of this table has not been charged (yet). And it may not be unless prosecutors win guilty verdicts in the Proud Boys case. It also may not be if the obstruction charge gets narrowed on appeal.
For reasons I laid out here, the Proud Boys trial is far more complex than the Oath Keepers trial. And in the Proud Boys trial, like the Oath Keepers trial, prosecutors don’t have a clear map showing that the plan was to occupy the Capitol; instead they have testimony that Biggs and Nordean kept consulting, and everyone took orders from them, and those orders had the effect of sending cells of Proud Boys off to breach parts of the building. So it is not at all certain that prosecutors will win convictions of the men — Tarrio, Biggs, and Nordean — who were working with people who were working with Trump and his handlers.
But this is one of the means via which DOJ has been working to hold Trump accountable since just months after the attack (I first laid this out in July 2021, long before most commentators understood how DOJ was using obstruction).
Even with the disorganized conspiracy (Sandlin and friends), prosecutors have carefully shown how the men took Trump’s December 19 tweet as an explicit instruction, took instructions from a WildProtest flyer put out by Ali Alexander, believed Trump had ordered them to march to the Capitol. There are hundreds more rioters who took Trump’s December 19 tweet as an instruction, though in the case of Sandlin and his co-conspirators, they took steps that were critical to the occupation of the Capitol and the Senate chamber in response.
But with the Proud Boys, to an extent thus far only seen with Oath Keeper Kelly Meggs, the communication ties, via a two step network, to Trump’s own actions and directions. And with the Proud Boys, that coordination builds off years-long relationships, particularly between Biggs and Jones and Stone, and through them, to Trump.
Everyone was working towards the same goal: to prevent Congress from certifying Joe Biden’s victory. There were, in various places, explicit agreements made. There were, as with Trump’s Stand Back and Stand By comment that prosecutors used to kick off this trial, more implicit agreements as well.
And DOJ is now at the point where it is beginning to show how those agreements, explicit and implicit, all worked together to make the assault on the Capitol successful.
Conspiracy guilty verdicts
Oath Keepers Stewart Rhodes, Kelly Meggs, Jessica Watkins, Kenneth Harrelson, Kelly Meggs, Mark Grods, Caleb Berry, James Dolan, Joshua James, Brian Ulrich, Todd Wilson (11 conspiracy verdicts)
Proud Boys Matthew Greene, Charles Donohoe, Jeremy Bertino, with Isaiah Giddings, Louis Colon, and James Stewart cooperating (3 known conspiracy verdicts)
Disorganized Militia Ronnie Sandlin, Nate DeGrave, with Josiah Colt cooperating (2 conspiracy verdicts)
“Patriots” Marshall Neefe and Charles Smith (2 conspiracy verdicts)