 Keith Alexander had a really bizarre response to a question from Mazie Hirono in Tuesday’s hearing.
Keith Alexander had a really bizarre response to a question from Mazie Hirono in Tuesday’s hearing.
SEN. HIRONO: I have one more question, Mr. Chairman. General Alexander, is PRISM the only intelligence program NSA runs under FISA Section 702?
GEN. ALEXANDER: Well, PRISM was (the statement ?), but, yes. Essentially, the only program was that — that, you know, is PRISM under 702, which under — operates under that authority for the court. But we also have programs under 703, 704 and 705.
Perhaps he was confused by her question (which came in the context of questions about the NYT’s report on the construction of dossiers, potentially on Americans). But he seems to have claimed that PRISM — the collection of Internet content from Internet providers under Section 702 — is the only way the NSA uses FISA Amendments Act to collect content.
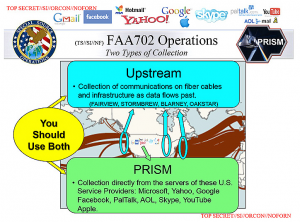
Not only does the PRISM slide above belie that (and there’s also phone content that is not covered under PRISM).
But the government itself released the October 3, 2011 John Bates FISC opinion (and other related documents) which describes the government’s collection of Internet transactions directly from the phone company switches (see footnote 24 where Bates distinguishes between the two kinds of Section 702 Internet collection). In an attempt to spin this collection as a big mistake last week, Dianne Feinstein even confirmed that this “upstream” collection comes from the backbone operated by the phone companies.
In mid 2011, NSA notified the DOJ, the DNI, and the FISA court, and House and Senate Intelligence Committees, of a series of compliance incidents impacting a subset of NSA collection under Section 702 of FISA, known as upstream collection.
This comprises about 10 percent of all collection that takes place under 702, and occurs when NSA obtains Internet communications, such as e-mails, from certain U.S. companies that operate the Internet background;[sic] i.e., the companies that own and operate the domestic telecommunication lines over which Internet traffic flows.
So there’s PRISM, there’s phone content collection, and there’s the upstream Internet collection from the phone companies’ switches. All operated, per the 2011 Bates memo, under Section 702 (and therefore overseen by the FISA Court and Congress).
Which is why I’ve been pondering this chart and related explanation, from NSA’s internal review of compliance incidents for the first quarter of 2012.
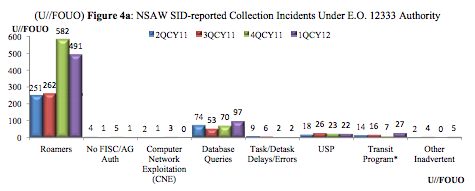
The chart shows all the violation incidents NSA discovered under programs authorized under Executive Order 12333 — the EO that covers entirely foreign collection, over which FISC and Congress exercise much less oversight than FISA. And what NSA calls “Transit Program” violations appear in the EO 12333, not the FISA, chart. In the first quarter of 2012 (the first quarter after the government started to resolve the 702 upstream collection problems laid out in the Bates memo), Transit Program violations went up from 7 in a quarter to 27.
NSA describes Transit Program violations this way.
(TS//SI//REL TO USA, FVEY) International Transit Switch Collection*: International Transit switches, FAIRVIEW (US-990), STORMBREW (US-983), ORANGEBLOSSOM (US-3251), and SILVERZEPHYR (US-3273), are Special Source Operations (SSO) programs authorized to collect cable transit traffic passing through U.S. gateways with both ends of the communication being foreign. When collection occurs with one or both communicants inside the U.S., this constitutes inadvertent collection. From 4QCY11 to 1QCY12, there was an increase of transit program incidents submitted from 7 to 27, due to the change in our methodology for reporting and counting of these types of incidents,
That is, these “Transit Program” violations reflect the collection of US person data in upstream collection, the very same problem described in the Bates opinion.
As I’ve been puzzling through why Transit Program violations would appear under EO 12333 rather than FISA, I wondered whether NSA collects off switches under both authorities — some content that the telecoms provide after doing an initial screening (as described in this WSJ article and backhandedly confirmed by the DNI), and some programs that the NSA collects and sorts off undersea cables itself. Both FAIRVIEW and STORMBREW show up — seemingly as Section 702 collection — on the PRISM slide above, but ORANGEBLOSSOM and SILVERZEPHYR don’t (WSJ also lists OAKSTAR and LITHIUM).
If so, though, you’d expect NSA to be finding violations under both authorities, because we know the government collects US person data under the 702 authorized upstream collection (they call this unintentional but Bates deemed it intentional).
This is all the more confusing given the way former Assistant Attorney General David Kris discusses “vacuum cleaner” collection taking place under EO 12333. His paper is on metadata collection, not content, but the vacuum cleaner (that is, dragnet) collection collects content as well (and the distinction may get distorted in discussions of Internet packets).
I don’t, yet, know the answer to this question, but the question itself raises several others:
- Given that there’s not a 702-authorized Transit Program violation category, does that mean NSA wasn’t and may still not be tracking it? That doesn’t make sense, because there are greater mandates to track these things under 702.
- If there wasn’t a 702-authorized Transit Program violation category before the revelations to John Bates, is it possible NSA instead treated upstream collection as authorized by 12333 so as not to have to report these violations?
- Are these known violations being reported now? Are they getting reported to Congress and the Court? Or has the NSA simply decided they’re not violations since Bates has okayed them, sort of, as intentional collection?
- If some of the upstream collection yielding US person content operates under 12333, does it have to be treated under any minimization rules?
- What do the 7 and 27 violation numbers reflect in relation to the figures of 10,000 SCT and 46,000 MCT estimates involving US persons provided to Bates?
- Did these violations ever get reported to Congress and the FISC?
In short, either all this upstream collection falls under 702, in which case there’s a big question why NSA tracks it as 12333 collection. Or the NSA’s ability to operate upstream collection under both authorities raises real questions about the protections it accords US person data collected under the 12333 collection.
Update: Two more things on this.
First, remember back in 2001, John Yoo pixie dusted EO 12333, basically holding the President could change the content of it without changing the language of it publicly. That was done, according to Sheldon Whitehouse, to permit the government to “wiretap Americans traveling abroad.” But I suspect it was done to permit the government to “wiretap Americans’ communications traveling abroad” — that is, American Internet traffic that transits foreign switches.
That said, I suspect the 2010 OLC memo on using 2511(2)(f) for collection was meant to clean up some of that (and also Yoo’s reliance on claiming the Fourth Amendment didn’t apply in DOD searches of entire apartment buildings if they were searching for terrorists).
Also, remember that the language of the 2008 Yahoo opinion makes it clear that the Protect America Act — Section 702’s predecessor — relied on 12333 for particularity. While we should soon learn more (FISC is releasing much more of this opinion and underlying documents), it seems that PAA was treated as a nested program within 12333.