Clarence Thomas’ Non-Recusal Might Have Also Hidden the Missing Mark Meadows Texts
As folks were discussing in comments, yesterday WaPo and CBS revealed damning details about communications between Ginni Thomas and Mark Meadows leading up to the insurrection. About 1% of the texts Meadows turned over to the January 6 Committee involved Ms. Thomas.
The messages, which do not directly reference Justice Thomas or the Supreme Court, show for the first time how Ginni Thomas used her access to Trump’s inner circle to promote and seek to guide the president’s strategy to overturn the election results — and how receptive and grateful Meadows said he was to receive her advice. Among Thomas’s stated goals in the messages was for lawyer Sidney Powell, who promoted incendiary and unsupported claims about the election, to be “the lead and the face” of Trump’s legal team.
The text messages were among 2,320 that Meadows provided to the House select committee investigating the Jan. 6 attack on the U.S. Capitol. The content of messages between Thomas and Meadows — 21 sent by her, eight by him – has not previously been reported. They were reviewed by The Post and CBS News and then confirmed by five people who have seen the committee’s documents.
[snip]
It is unknown whether Ginni Thomas and Meadows exchanged additional messages between the election and Biden’s inauguration beyond the 29 received by the committee. Shortly after providing the 2,320 messages, Meadows ceased cooperating with the committee, arguing that any further engagement could violate Trump’s claims of executive privilege. Committee members and aides said they believe the messages may be just a portion of the pair’s total exchanges.
As WaPo notes, after November 24, there are no more texts provided to the Committee until after the riot.
The text exchanges with Thomas that Meadows provided to the House select committee pause after Nov. 24, 2020, with an unexplained gap in correspondence. The committee received one additional message sent by Thomas to Meadows, on Jan. 10, four days after the “Stop the Steal” rally Thomas said she attended and the deadly attack on the Capitol.
You can click through to read what a nutjob Ms. Thomas is. But for this post, I’m interested in the how the texts that got turned over or did not relate to Justice Thomas’ decision, on January 19, not just not to recuse from the decision on whether Trump’s invocation of privilege over materials at the Archives, but to cast the single vote to uphold Trump’s privilege claim. Thomas’ participation in that decision may have had the effect of making a decision that would have — if four other Justices agreed with him — had the effect of shielding damning communications involving his spouse.
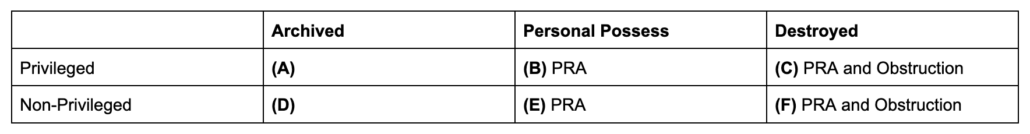
This table is just a sketch, but one I hope helps the discussion among those who know the law and the details of the various requests better than I. This table shows that had Thomas’ decision been successful, it probably would have prevented damning texts from his spouse from being shared with the Committee (or, ultimately, DOJ’s criminal investigators), but just as importantly would have hidden the absence and possible destruction of some records that would be covered both by the Presidential Records Act (marked as PRA in the table) and relevant to the by-then ongoing grand jury investigation (marked as obstruction).
Several factors affect the legal status of any texts that should have been covered by Justice Thomas’ participation:
- Trump’s claims of privilege were absurdly broad, covering things like visitor logs that under other Presidents are routinely released
- While Mark Meadows’ claims of privilege were not as absurd as (say) Steve Bannon’s, it seems likely he, too, took an expansive approach to privilege claims
- All of Trump’s flunkies (including Meadows and Bannon) were using Trump’s claims of privilege to justify withholding purportedly privileged in their own possession
- Anything Meadows claimed was covered by privilege would be covered by the Presidential Records Act and so should have been — but in Meadows’ case, because he did White House business on his personal email and phone, often were not — shared with the Archives
- Mark Meadows replaced his phone after the time multiple grand juries had started an investigation into January 6; replacing his phone had the likely effect of destroying any communications not otherwise stored in or backed up to the cloud; the risk he destroyed Signal texts is particularly high
Justice Thomas’ decision would have covered everything in the first line: privileged comms that were properly archived, privileged stuff that Meadows didn’t archive, and privileged stuff that got destroyed. The scenario I’m seeing a lot of people address is just box (A), with the logic being, what if there were comms that were actually archived involving Ginni that were deemed privileged, what if those comms were especially damning?
But the decision that such comms are not privileged means the Committee and DOJ can now address stuff in Meadows’ possession and/or that have been destroyed. As it happened, the Committee has been able to identify Meadows comms in box (E) and possibly even in box (F) via his production: things that should have been archived but were not (this post and this post address the kinds of communications described in Meadows’ contempt referral are in box (E)). It is virtually certain there are a bunch of comms in box (B): stuff Meadows treated as privileged that were not properly archived. Now both the Committee and DOJ can claim those are covered by his contempt. In the process, the Committee or, more likely, DOJ may discover communications involving the former President that should have been archived, proof not just that Meadows is in contempt, but also that he violated the PRA.
The real risk to Meadows, though — and the place where Justice Thomas’ ethical violations could turn into something else — comes in box (C): with comms that, because of the broadness of the original privilege claims, would be treated under Trump’s now defeated privilege claim, but comms that, because Meadows replaced his phone during an ongoing grand jury investigation, the destruction of which might amount to obstruction of that investigation.
What DOJ is doing with other criminal subjects in the January 6 investigation is identifying Signal and Telegram texts that got destroyed on one phone by seizing the phones of others who did not destroy their side of the communication. In the case of Meadows, for example, we’ve already identified a Signal text that seems to remain in Jim Jordan’s custody but that Meadows may no longer have.
Justice Thomas’ failed attempt to uphold Trump’s (and therefore Meadows’) insanely broad privilege claims might have had the effect of making it clear that Meadows had destroyed privileged communications that would be covered by the ongoing January 6 grand jury investigation.
It’s not just embarrassing texts involving his spouse that Justice Thomas could have covered up with his participation in that decision. It is also potential criminal obstruction exposure because Meadows replaced his phone.
Particularly given the big gap in texts in what Meadows turned over between November 24 and January 10, those might be far more important than the crazypants things Ginni said.