The Logic of Assange’s EDVA Indictment Is Inconsistent with Mueller’s Apparent Logic on Assange’s Declination
As Emma Best has noted, shortly before GRU targeted John Podesta in a spear-phishing attack, WikiLeaks offered a reward for Hillary’s speech transcripts like the excerpts that were released as part of the John Podesta release.
Hours before Russian hacking operations targeted Hillary Clinton’s campaign in the spring of 2016, WikiLeaks discussed offering a monetary reward for transcripts of her speeches at Goldman Sachs. Soon after, Russian hackers launched a spear phishing campaign that resulted in John Podesta’s email account being compromised. Emails containing excerpts from the speeches were included in the first day of the Podesta email releases. A week later, emails containing the transcripts themselves were released. WikiLeaks heralded these transcripts as their “holy grail.”
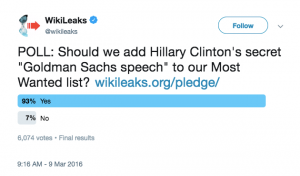
The story began on March 9, 2016, when WikiLeaks sent a tweet with a poll asking if they should add Hillary Clinton’s Goldman Sachs speeches to their ”Most Wanted” page for six figure rewards for materials. When the poll completed twenty four hours later, 93% of respondents said that WikiLeaks should offer a reward for the speeches. The Russian hackers at Fancy Bear may have been listening and been inspired by WikiLeaks’ comment. Unpublished targeting data collected by Secureworks shows the hacking campaign began earlier than the Mueller indictment reveals. A week and a half later, after dozens of attempts to penetrate the accounts of Podesta and other Clinton staffers and associates, Fancy Bear sent the phishing email that successfully tricked Podesta into compromising his account and the Goldman Sachs speeches along with it.
Secureworks’ unpublished breakdown of the Russian spear phishing and hacking effort, which AP described last year, shows that the campaign to penetrate the account began hours after WikiLeaks teased the possibility of offering a reward for the information. The tweet first mentioning the potential of a reward for the Goldman Sachs transcripts was sent at 8:16 P.M. Moscow time. At 11:56 AM the next day, less than sixteen hours later, Russian hackers began a campaign that would target “over 300 individuals affiliated with the Clinton Campaign, DCCC, and DNC.“ Podesta’s emails accounts were targeted in the days that followed and successfully compromised a week later, resulting in the exfiltration of nearly 60,000 emails.
Under what I’ve called Theory One of the superseding Julian Assange indictment, WikiLeaks’ publication of a wish list that was subsequently fulfilled would qualify it (or Julian Assange) for a conspiracy charge. Given what we’ve seen of Roger Stone’s actions, it might qualify him for a conspiracy charge as well (though we still don’t know via what means he contacted WikiLeaks).
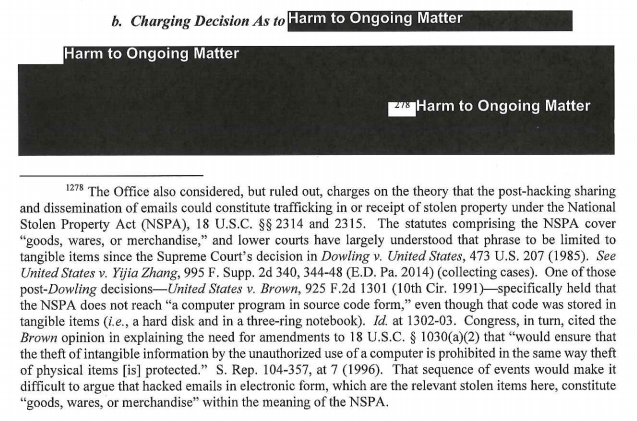
But this 2.5 page redaction in the Mueller Report appears to explain why they didn’t charge WikiLeaks (and so by association, Stone) in that conspiracy.
We don’t know what that redaction says, though the unredacted footnote makes it clear that in the case of emails stolen from Hillary, DOJ determined that sharing of stolen property does not constitute a crime.
We do, however, have a sense of how the Attorney General understands this declination, because he used it to exonerate Trump, even in spite of Trump’s active role in pushing Roger Stone to optimize the WikiLeaks releases for the campaign. In one of his explanations for the WikiLeaks declination — one that may more directly allude to Stone’s involvement — Bill Barr said that publication of stolen emails would not be criminal “unless the publisher also participated in the underlying hacking conspiracy.”
The Special Counsel also investigated whether any member or affiliate of the Trump campaign encouraged or otherwise played a role in these dissemination efforts. Under applicable law, publication of these types of materials would not be criminal unless the publisher also participated in the underlying hacking conspiracy. Here too, the Special Counsel’s report did not find that any person associated with the Trump campaign illegally participated in the dissemination of the materials.
In the case of election interference, then, Barr does not consider the publication of documents identified on a wish list that hackers subsequently steal to amount to joining a conspiracy.
But in the case of Chelsea Manning’s leak, his DOJ does.
There’s obviously a distinction: John Podesta’s risotto recipes are not classified, whereas much of the stuff (but not all) Manning leaked was. But the role of a wish list is not functionally different, and Russian officers were charged both for hacking and dissemination.
I’m still working on a post describing how unbelievably stupid the EDVA case is, both for the press and for DOJ’s hopes to lay a precedent.
But at least at a structural level, the prosecution is also inconsistent with the decisions DOJ made about WikiLeaks on the election year operation.
As I disclosed last July, I provided information to the FBI on issues related to the Mueller investigation, so I’m going to include disclosure statements on Mueller investigation posts from here on out. I will include the disclosure whether or not the stuff I shared with the FBI pertains to the subject of the post.