Carrie Cordero’s Counterintelligence Complaints
I wasn’t going to respond to Carrie Cordero’s Lawfare piece on my and Jason Leopold’s story on NSA’s response to Edward Snowden’s claims he raised concerns at the agency, largely because I think her stance is fairly reasonable, particularly as compared to other Snowden critics who assume his leaks were, from start to finish, an FSB plot. But a number of people have asked me to do so, so here goes.
Let’s start with this:
As far as we know – even after this new reporting – Snowden didn’t lodge a complaint with the NSA Inspector General. Or the Department of Defense Inspector General. Or the Intelligence Community Inspector General. He didn’t follow up with the NSA Office of General Counsel. He didn’t make phone calls. He didn’t write letters. He didn’t complain to Members of Congress who would have been willing to listen to his concerns.
Now here’s the rub: do I think that had he done all these things, the programs he questioned would have been shut down and there would have been the same effect as his unauthorized disclosures? No. He probably would have been told that more knowledgeable lawyers, leadership officials, congressmen and dozens of federal judges all assessed that the activities he questioned were legal.
Without noting the parts of the article that show that, nine months into the Snowden leaks and multiple hearings on the subject, Keith Alexander still didn’t know how contractors might raise complaints, and that the NSA editing of its Q&A on Snowden show real questions about the publicity and viability of reporting even to the IG, especially for legal violations, Cordero complains that he did not do so. Then she asserts that had Snowden gone to NSA’s IG (ignoring the record of what happened to Thomas Drake when he did the same), the programs would not have changed.
And yet, having taken a different approach, some of them have changed. Some of the programs — notably Section 215, but also tech companies’ relationship with the government, when exposed to democratic and non-FISA court review, and FISA court process itself — did get changed. I think all but the tech company changes have largely been cosmetic, Cordero has tended to think reforms would go too far. But the record shows that Snowden’s leaks, along with whatever else damage critics want to claim they caused, also led to a democratic decision to shift the US approach on surveillance somewhat. Cordero accuses Snowden of doing what he did because of ego — again, that’s her prerogative; I’m not going to persuade people who’ve already decided to think differently of Snowden — but she also argues that had Snowden followed the already problematic methods to officially report concerns, he would have had less effect raising concerns than he had in fact. Some of what he exposed may have been legally (when argued in secret) sustainable before Snowden, but they turned out not to be democratically sustainable.
Now let’s go back to how Cordero characterizes what the story showed:
Instead, the report reveals:
- An NSA workforce conducting a huge after-action search for documents seeking to affirm or refute Snowden’s claim that he had raised red flags internally before resorting to leaking classified documents;
- Numerous officials terrified that they would miss something in the search, knowing full-well how easily that could happen in NSA’s giant and complex enterprise; and
- The NSA and ODNI General Counsels, and others in the interagency process –doing their job.
The emails in the report do reveal that government officials debated whether to release the one document that was evidence that Snowden did, in fact, communicate with the NSA Office of General Counsel. It’s hard to be surprised by this. On one hand, the one email in and of itself does not support Snowden’s public claim that he lodged numerous complaints; on the other hand, experienced senior government officials have been around the block enough times to know that as soon as you make a public statement that “there’s only one,” there is a very high likelihood that your door will soon be darkened by a staff member telling you, “wait, there’s more.” So it is no wonder that there was some interagency disagreement about what to do.
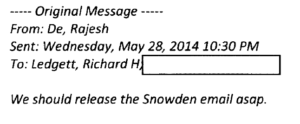
For what it’s worth, I think the emails show a mixed story about how well various participants did their job. They make Admiral Rogers look great (which probably would have been more prominently noted had the NSA not decided to screw us Friday night, leading to a very rushed edit job). They make Raj De, who appears to have started the push to release the email either during or just as Snowden’s interview with Brian Williams finished airing (it aired at 10:00 PM on May 28; though note the time stamps on this string of De emails are particularly suspect), look pretty crummy, and not only for that reactive response. (I emailed De for comment but got no response.)
Later on, Cordero admits that, in addition to the OGC email, the story reported for the first time that there had also been a face-to-face conversation with one of the people involved in responding to that email.
The Vice report reveals that Snowden did do at least these things related to his interest in legal authorities and surveillance activities: (i) he clicked on a link to send a question to NSA OGC regarding USSID 18 training, which resulted in an emailed response from an NSA attorney; and (ii) he had a personal interaction (perhaps a short conversation) with a compliance official regarding questions in a training module. But according to the report, in his public statements, “Snowden insisted that he repeatedly raised concerns while at the NSA, and that his concerns were repeatedly ignored.”
(Note Cordero entirely ignores that interviews with Snowden’s colleagues — the same people whom she characterized as terrified they’d miss something in the media response but doesn’t consider whether they would be even more terrified conversations about privacy with Snowden might be deemed evidence of support for him — found a number of them having had conversations about privacy and the Constitution).
She doesn’t get into the chronology of the NSA’s treatment of the face-to-face conversation, though. What the story lays out is this:
- Released emails show NSA now asserts that Snowden complained about two training programs within the span of a week, possibly even on the same day, with Compliance being involved in both complaints (Snowden would have known they were involved in the OGC response from forwarded emails)
- Given the record thus far, it appears that there is no contemporaneous written record of the face-to-face complaint (we asked the NSA for any and that’s when they decided to just release the emails in the middle of the night instead of responding, though I assume there is an FBI 302 from an interview with the training woman)
- Given the record thus far, NSA only wrote up that face-to-face complaint the day after and because NSA first saw teasers from the April 2014 Vanity Fair article revealing Snowden’s claim to have talked to “oversight and compliance”
- In spite of what I agree was a very extensive (albeit frantic and limited in terms of the definition of “concern”) search, NSA did not — and had not, until our story — revealed that second contact, even though it was written up specifically in response to claims made in the press and well before the May 29 release of Snowden’s email
- In the wake of NSA not having acknowledged that second contact, a senior NSA official wrote Admiral Rogers a fairly remarkable apology and (as I’ll show in a follow-up post) the NSA is now moving the goal posts on whom they claim Snowden may have talked to
Now, I actually don’t know what happened in that face-to-face contact. We asked both sides of the exchange very specific questions about it, and both sides then declined to do anything but release a canned statement (the NSA had said they would cooperate before they saw the questions). Some would say, so what? Snowden was complaining about training programs! Training programs, admittedly, that related to other documents Snowden leaked. And at least one training program, as it turns out, that the NSA IG had been pushing Compliance to fix for months, which might explain why they don’t want to answer any questions. But nevertheless “just” training programs.
I happen to care about the fact that NSA seems to have a pattern of providing, at best, very vague information about how seriously NSA has to take FISA (or, in the one program we have in its entirety, perfectly legal tips about how to bypass FISA rules), but I get that people see this as just a training issue.
I also happen to care about the fact that when Snowden asked what NSA would like to portray as a very simple question — does what would be FISA take precedence over what would be EO 12333 — it took 7 people who had been developing that training program to decide who and how to answer him. That question should be easier to answer than that (and the emailed discussion(s) about who and how to answer were among the things conspicuously withheld from this FOIA).
But yes, this is just two questions about training raised at a time (we noted in the story) when he was already on his way out the door with NSA’s secrets.
Which is, I guess, why the balance of Cordero’s post takes what I find a really curious turn.
If this is all there is – a conversation and a question – then to believe that somehow NSA attorneys and compliance officials were supposed to divine that he was so distraught by his NSA training modules that he was going to steal the largest collection of classified documents in NSA history and facilitate their worldwide public release, is to live in a fantasy land.
No, what this new report reveals is that NSA lawyers and compliance personnel take questions, and answer them. Did they provide a simple bureaucratic response when they could or should have dug deeper? Maybe. Maybe not.
Because what they apparently do not do is go on a witch hunt of every employee who asks a couple legal questions. How effective do we think compliance and training would be, if every person who asks a question or two is then subject to intense follow-up and scrutiny? Would an atmosphere like that support a training environment, or chill it?
[snip]
NSA is an organization, and a workforce, doggedly devoted to mission, and to process. In the case of Snowden, there is an argument (one I’ve made before) that its technical security and counterintelligence function failed. But to allude – as today’s report does – that a couple questions from a low level staffer should have rung all sorts of warning bells in the compliance and legal offices, is to suggest that an organization like NSA can no longer place trust in its workforce. I’d wager that the reason the NSA lawyers and compliance officials didn’t respond more vigorously to his whispered inquiries, is because they never, in their wildest dreams, believed that a coworker would violate that trust.
Cordero turns a question about whether Snowden ever complained into a question about why the NSA didn’t notice he was about to walk off with the family jewels because he complained about two training programs.
There are two reasons I find this utterly bizarre. First, NSA’s training programs suck. It’s not just me, based on review of the few released training documents, saying it (though I did work for a number of years in training), it’s also NSA’s IG saying the 702 courses, and related materials, are factually wrong or don’t address critical concepts. Even the person who was most negative towards Snowden in all the emails, the Chief of SID Strategic Communications Team, revealed that lots of people complain about the 702 test (as is also evident from the training woman’s assertion they have canned answers for such complaints).
Complaints about fairness/trick questions are something that I saw junior analysts in NTOC … would pose — these were all his age and positional peers: young enlisted Troops, interns, and new hires. Nobody that has taken this test several times, or worked on things [redacted] for more than a couple of years would make such complaints. It is not a gentleman’s course. *I* failed it once, the first time I had to renew.
I’m all for rigorous testing, but all the anecdotes about complaints about this test may suggest the problem is in the test, not the test-takers. It’s not just that — as Cordero suggested — going on a witch hunt every time someone complains about training courses would chill the training environment (of a whole bunch of people, from the sounds of things). It’s that at precisely the moment Snowden took this training it was clear someone needed to fix NSA’s training, and Cordero’s response to learning that is to wonder why someone didn’t launch a CI investigation.
Which leads me to the other point. As Cordero notes, this is not the first time she has treated the Snowden story as one primarily about bad security. I happen to agree with her about NSA’s embarrassing security: the fact that Snowden could walk away with so much utterly damns NSA’s security practices (and with this article we learn that, contrary to repeated assertions by the government, he was in an analytical role, though we’ve already learned that techs are actually the ones with unaudited access to raw data).
But here’s the thing: you cannot, as Cordero does, say that the “foreign intelligence collection activities [are] done with detailed oversight and lots of accountability” if it is, at the same time, possible for a SysAdmin to walk away with the family jewels, including raw data on targets. If Snowden could take all this data, then so can someone maliciously spying on Americans — it’s just that that person wouldn’t go to the press to report on it and so it can continue unabated. In fact, in addition to rolling out more whistleblower protections in the wake of Snowden, NSA has made some necessary changes (such as not permitting individual techs to have unaudited access to raw data anymore, which appears to have been used, at times, as a workaround for data access limits under FISA), even while ratcheting up the insider threat program that will, as Cordero suggested, chill certain useful activities. One might ask why the IC moved so quickly to insider threat programs rather than just implementing sound technical controls.
Carrie Cordero’s lesson, aside from grading the participants in this email scrum with across-the-board As, is that Snowden complaining about the same training programs the IG was also complaining about should have been a counterintelligence issue but wasn’t because of the great trust at NSA. That argument, taken in tandem with Cordero’s vouching for NSA’s employees, should not, itself, inspire trust.