To Clarify the Debate, Tim Cook Should Start Shopping for Land in Cork, Ireland
There’s so much blathering from National Security and plain old pundits about FBI’s demand that Apple’s programmers write it a custom operating system that I think, to facilitate reasonable debate, Tim Cook should travel to Cork, Ireland (where Apple already has a presence) and start shopping for land for a new headquarters.
I say this not because my spouse and I are Irish (though the Irish spouse insists that Cork is the Irish equivalent of Texas), and not because I want Apple to take all its Silicon Valley jobs and move them to Ireland, and not because Apple has already been using Ireland as a tax haven, but because it would be the best way to get people who otherwise seem to misunderstand the current state of the world on encryption to better think it through.
FBI’s problem with Apple is that the company tries to offer its users around the globe the strongest possible security as a default option. Plenty of other companies (like Android) offer less perfect security. Plenty of other apps offer security. Some (like Signal) may even offer better security, but relying on devices (Android phones and desktops) that themselves may be insecure. But the problem with Apple is that all its more recent phones are going to be harder (though not impossible, unless law enforcement fucks up when they first seize the phone, as they did here) to access by default.
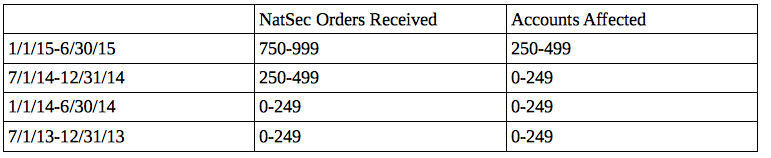
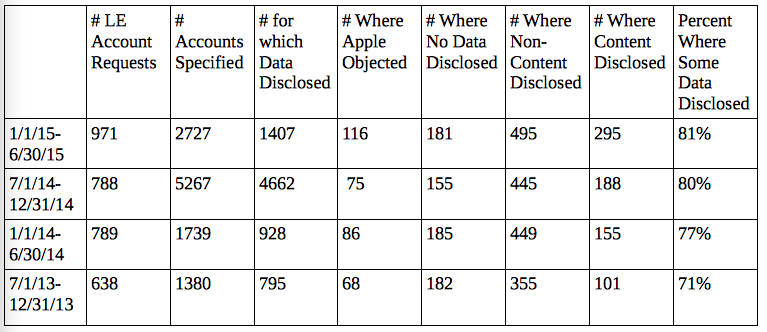
Thus far, however, Apple still serves as a valuable law enforcement partner — something lots of the pundits have ignored. Before the All Writs Act order on February 16, Apple had turned over metadata covering the entire period Farook used the phone (he apparently was using the phone into November), as well as the content that was backed up into iCloud until October 19. Presumably, Apple turned over all the same things on the victims Farook killed, up to 14 iPhones full of communications, including with Farook, set to auto-backup as Farook’s phone originally had been. Apple can and surely does turn over all the same things when an iPhone user in Paris or Beijing or Beirut sparks the interest of NSA.
If Apple were to move its headquarters and servers to Cork (perhaps with some redundant servers in Brazil, for example), that would be far less accessible to both US law enforcement and intelligence. And contrary to what you might think from those attacking Apple’s alleged non-compliance here, that would result in significantly less intelligence (or evidence) than both are getting now.
That’s because by offering the best encryption product in the world that relies on US-based servers, Apple ensures that at least the metadata — not to mention any content backed up to iCloud (which in Farook’s case, included content through October plus that from his colleagues) — is readily available. If Apple were to move to Cork, any backed up content would be far harder to get and NSA would have to steal Internet packets to get iMessage metadata (admittedly, that’s probably pretty easy to do from Ireland, given its proximity to GCHQ’s gaping maw, but it does require some work).
The counterexample is the way the terrorists behind the Paris attack used Telegram. Because that’s a non-US messaging system, data including metadata from it was not easily available (though as I understand it its encryption would be fairly trivial for NSA to overcome). Thus, terrorists were able to use an inferior product and obtain more obscurity (until Telegram, under pressure, shut down a bunch of ISIS channels) than they would have if they had used the superior iPhone because Apple’s servers are in the US. If US national security officials force multinational companies to choose between quality of product and US location, one or two may choose to offshore. Alternately, eventually the foreign products may come to rival what Apple is currently offering.
Right now, US officials are guaranteed that if intelligence and criminal targets use the best product in the world, they’ll have evidence readily available. Even ignoring all the economic reasons to want Apple to stay in the US (or better yet to actually pay its fair share of taxes in the US!) that could change if Apple were to decide it could not longer legally offer a secure product while remaining in the US.



![[image: Leo Reynolds via Flickr]](https://www.emptywheel.net/wp-content/uploads/2016/02/LiveJazzFriday_LeoReynolds-Flickr.jpg)
![[image: Leo Reynolds via Flickr]](https://www.emptywheel.net/wp-content/uploads/2016/02/LettersTh_LeoReynolds-Flickr.jpg)
![[image: Leo Reynolds via Flickr]](https://www.emptywheel.net/wp-content/uploads/2016/02/WednesCalendar_LeoReynolds-Flickr.jpg)
![[image (modified): Leo Suarez via Flickr]](https://www.emptywheel.net/wp-content/uploads/2016/01/BadPenny_LeoSuarez-Flickr_mod-253x300.jpg)