John Brennan Denies a Special Harry Reid Briefing
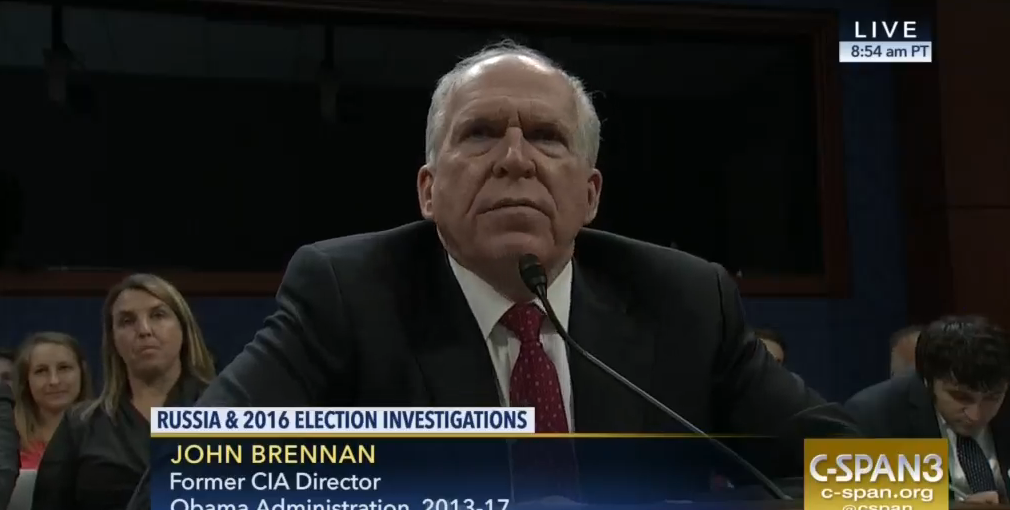
This passage from John Brennan’s testimony about Russia to the House Intelligence Committee yesterday has gotten a lot of attention:
Through the so-called Gang of Eight process, we kept Congress apprised of these issues as we identified them. Again, in consultation with the White House, I personally briefed the full details of our understanding of Russian attempts to interfere with the election to Congressional leadership, specifically Senators Harry Reid, Mitch McConnell, Dianne Feinstein, and Richard Burr, and to Representatives Paul Ryan, Nancy Pelosi, Devin Nunes, and Adam Schiff between 11 August and 6 September. I provided the same briefing to each of the Gang of Eight members. Given the highly sensitive nature of what was an active counterintelligence case involving an ongoing Russian effort to interfere in our presidential election, the full details of what we knew at the time were shared only with those members of Congress, each of whom was accompanied by one senior staff member. The substance of those briefings was entirely consistent with the main judgments contained in the January classified and unclassified assessments, namely that Russia’s goals were to undermine public faith in the US democratic process, denigrate Secretary Clinton and harm her electability and potential presidency and to help President Trump’s election chances.
The passage has been used to question why GOP leaders, most especially Mitch McConnell, didn’t react more strongly, particularly given public reports that he wouldn’t sign onto a more aggressive statement about Russian efforts.
As I noted in this post, the record thus far reflects a difference in emphasis (on protecting the election systems rather than on Russian attempts to hurt Clinton).
But I want to look more closely at what Brennan actually said.
His description of the briefings seems to be a denial of what I laid out in this post — the NYT report that he gave Harry Reid a special briefing (one which may have been based on the Christopher Steele dossier) that was more alarming than others.
CIA DIRECTORS SHOULD NOT MEET WITH JUST ONE GANG OF EIGHT MEMBER
The second detail I find most interesting in this story is that John Brennan privately briefed Harry Reid about his concerns about the Russians.
John O. Brennan, the C.I.A. director, was so concerned about the Russian threat that he gave an unusual private briefing in the late summer to Harry Reid, then the Senate Democratic leader.
Top congressional officials had already received briefings on Russia’s meddling, but the one for Mr. Reid appears to have gone further. In a public letter to Mr. Comey several weeks later, Mr. Reid said that “it has become clear that you possess explosive information about close ties and coordination between Donald Trump, his top advisors, and the Russian government — a foreign interest openly hostile to the United States.”
While I’m generally sympathetic to Democrats’ complaints that DOJ should have either remained silent about both investigations or revealed both of them, it was stupid for Brennan to give this private briefing (and I hope he gets grilled about it by HPSCI when he testifies in a few weeks). In addition to the things Reid said publicly about the investigation, it’s fairly clear he and his staffers were also behind some of the key leaks here (and, as CNN reported yesterday, leaks about the investigation actually led targets of it to alter their behavior). For reasons beyond what appears in this story, I think it likely Reid served as a cut-out for Brennan.
And that’s simply not appropriate. There may well have been reasons to avoid briefing Richard Burr (who was advising Trump). But spooks should not be sharing information with just one party. CIA did so during its torture cover-up in ways that are particularly troubling and I find this — while not as bad — equally problematic.
When Brennan said he “provided the same briefing to each of the Gang of Eight members,” he might be seen as denying that the briefing to Reid was anything unusual.
Except this NYT article describes Reid’s as taking place in “late summer” and describes top officials as already having received briefings. Another NYT article describes the special briefing for Reid as having taken place on August 25.
In an Aug. 25 briefing for Harry Reid, then the top Democrat in the Senate, Mr. Brennan indicated that Russia’s hackings appeared aimed at helping Mr. Trump win the November election, according to two former officials with knowledge of the briefing.
The officials said Mr. Brennan also indicated that unnamed advisers to Mr. Trump might be working with the Russians to interfere in the election. The F.B.I. and two congressional committees are now investigating that claim, focusing on possible communications and financial dealings between Russian affiliates and a handful of former advisers to Mr. Trump. So far, no proof of collusion has emerged publicly.
Mr. Trump has rejected any suggestion of a Russian connection as “ridiculous” and “fake news.” The White House has also sought to redirect the focus from the investigation and toward what Mr. Trump has said, with no evidence, was President Barack Obama’s wiretapping of phones in Trump Tower during the presidential campaign.
The C.I.A. and the F.B.I. declined to comment for this article, as did Mr. Brennan and senior lawmakers who were part of the summer briefings.
In the August briefing for Mr. Reid, the two former officials said, Mr. Brennan indicated that the C.I.A., focused on foreign intelligence, was limited in its legal ability to investigate possible connections to Mr. Trump. The officials said Mr. Brennan told Mr. Reid that the F.B.I., in charge of domestic intelligence, would have to lead the way.
As described by the NYT, the Reid briefing went beyond what Brennan says he briefed all the Gang of Eight members on, specially with regards to Trump advisors working with Russia. It’s possible Brennan briefed Reid twice.
Much later in the hearing, Trey Gowdy asked Brennan about the Steele dossier. Some of Brennan’s responses — especially his claim not to know who commissioned the Steele dossier; watch him play with his pen — were not all that believable. Brennan went on to say that the CIA didn’t rely on the dossier, but his denial pertained to the IC report on the hack.
It wasn’t part of the corpus of intelligence, uh, information that we had. It was not in any way used as a basis for the intelligence community assessment that was done, uh, it was not.
Note the funny mouth gesture which used to be Brennan’s main “tell.”
Gowdy being Gowdy was not smart enough to ask whether the dossier was ever used in a briefing to members of Congress.
As I have noted, the IC denials pertaining to the dossier are, um, unconvincing (one two three). That’s all the more true given that Steele has admitted to sharing copies of his dossier with his former employer, who would naturally share with Brennan (elsewhere in the hearing Brennan refused to address what our foreign partners had shared with us).
In any case, it seems to me the question is not so much whether McConnell blew off the seriousness of the Brennan warning, but, still, whether Reid received another briefing–perhaps outside that date scope–that included information McConnell didn’t get.





![[Photo: National Security Agency, Ft. Meade, MD via Wikimedia]](https://www.emptywheel.net/wp-content/uploads/2017/08/NationalSecurityAgency_HQ-FortMeadeMD_Wikimedia.jpg)