2009: IRC discussions of child porn
May 2010: Schulte joins CIA as engineer
2011 and 2012: Google searches for child porn
April 2015: Allegedly rapes a woman (possibly partner) who is passed out and takes pictures of it
December 2015: Beginning of dispute with CIA colleague
February 2016: According to some colleagues interviewed in August 2016, his demeanor changes
March 1, 2016: Schulte alleges a colleague made a threat against him
March 3, 2016: Date of backup used to steal documents; date moved to new cubicle in OSB
March 29, 2016: Date of move to new units
March to June 2016: Schulte deleting logs of access to CIA computer
April 4, 2016: Schulte and co-worker reassigned; CIA shifts his access to Brutal Kangaroo; Schulte researches “Detecting USB insertion/removal in C++ non-GUI application”
April 8, 2016: Interview of Schulte by CIA
April 12 and 13, 2016: Schulte Google searches on windows command line copy all files subdirectories, windows copy all files and subdirectories, windows back files xcopy or robocopy, thumb drive copy speeds, and optimal way (including memory block size) to copy computer data
April 14, 2016: CIA informs Schulte he was no longer administrator for OSB libraries, but he reinstated them
April 15, 2016: Schulte searches, “admin view restricted pages” to learn bout to restrict the ability for other admins to see certain things about the LAN; Schulte logs into ESXi twice via vSphere 3:36PM
April 16, 2016: CIA tries to remove Schulte’s SA rights
April 18, 2016: Schulte given notice against restoring access; Schulte researches “copying multiple large files;” Schulte accesses server and edited logs
11:08AM: Schulte tries, but fails, to log into Confluence
11:12:08 and 11:12:18AM: Schulte logged in as root to the ESXi server.
11:43AM: Schulte logs out as root to one of those sessions.
12:59PM: Schulte e-mails Anthony stating that “It seems like overnight all my permissions on the servers themselves revoked.”
1:47PM: Schulte logs out as root to the other session on the ESXi server.
At 2:01 p.m., the defendant downloads the old ESXi server page from Confluence.
7:17PM: Schulte logs in as root to the ESXi server again.
Between 6 and 7:44 p.m., the defendant used his administrative session, that’s the SSH session from the shell log that we’ve been viewing for the last few slides, to view various log files on the server.
7:47PM: Schulte logs out as root from ESXi
April 20, 2016: Schulte creates snapshot of Confluence, reverts Confluence to April 16 snapshot, later reverts to April 20 image
3:58PM: IDB sends out email about server changes
5:30PM: Schulte makes a snapshot
5:35PM: Schulte reverts to April 16 backup
5:42PM: Schulte copies March 3 backup
5:43PM: Schulte copies March 3 database
5:52PM: He says he wants to go to a conference
6:51PM: Schulte reverts to snapshot
6:55PM: Schulte deletes April 20 snapshot
April 21, 2016: Schulte said he had equipment registered under his own name
April 24, 2016: Schulte searches for a SATA adapter (which lets you connect a computer hard drive via a USB connection); Schulte searches how to partition a drive
April 28, 2016: Schulte repeats search on how to restrict other admins from seeing aspects of the LAN
April 30, 2016: Schulte researches how to delete google history, Western Digital disk wipe, and Samsung ssd wipe (the search of Schulte’s apartment would find both Western Digital and Samsung drives)
Q. Just to recap, let’s walk through. What happened on April 23, 2016? A. The defendant opened Eraser Portable for the first time. Q. What happened next? A. On April 24, the defendant ordered a SATA adapter and downloaded Tails onto his computer. Q. Just remind us again what Tails is. A. Tails is an operating system that directly connects you into the TOR network. Q. What happened next? A. So, on April 28, 2016, by this time, the defendant had used Eraser Portable to securely delete two folders on the computer — Brutal Kangaroo and ArrayList — and had started the process of deleting five BKP files but did not complete it. Q. What’s the next thing that happened? A. So, on April 30, the defendant downloaded the Darik’s Boot and Nuke program, which is used to securely delete hard drives. Between 10:51 and 10:55 on April 30, there were searches performed, including “how to kill your data dead with these tips and tools” and “wipe” utilities for Samsung and Western Digital hard drives. Q. What happened next? A. From April 30 into May 1, so late on the 30th, the defendant periodically would unlock the screen saver to his virtual machine, indicating he was logged on. Around 3 a.m. on May 1, the defendant performed a search for “how I can verify that a one terabyte file transferred correctly.” In addition, he also searched for ways to hash data. Q. What’s the next thing that happened? A. On May 5, 2016, both drives, the C and the D drive, were reformatted
May 1, 2016, 3:20AM: Schulte searches on “how can I verify that a 1 tb file transferred correctly?”
May 4, 2016: Schulte searches on “can you use dban on ssd,” referring to a wiping software called Darik’s Boot and Nuke
May 6, 2016: Schulte researches trackers and Tor
May 8, 2016: Schulte Googles how to set up a Tor bridge
May 26, 2016: Schulte again asks for access to Brutal Kangaroo, then obtains it from another employee
June 8, 2016: Schulte revokes privileges to Brutal Kangaroo for OSB person
June 22, 2016: Date of warning letter to Schulte
June 28, 2016: Schulte writes Meroe Park and others
June 30, 2016: At meeting with Sean Roche, Schulte threatens to restore his access again
July 19, 2016: Date of interview of Schulte by CIA
August 1, 2016: Schulte searches on “create temporary email” then visits throwawaymail.com
August 3, 2016: Date of Snowden “it’s time” tweet that Schulte would later search for
August 4, 2016: Schulte conducts his first-ever WikiLeaks search
August 10, 2016: Schulte searches on Tails
August 14, 2016: Schulte searches on filing a lawsuit against his boss
September 1, 2016: Schulte searches on “what is a mole”
September 5, 2016: Schulte searches on “what is a mole”
October 12, 2016: Schulte sends colleague draft of resignation letter detailed claimed concerns about security of LAN; he does not submit letter to CIA
October 27, 2016: Schulte gives notice
October 31, 2016: Schulte sends email warning of streaming service downtime started November 9
November 10, 2016: Leaves CIA, sends email (marked unclassified, but containing classified information) to CIA OIG claiming to have contacted HPSCI about security concerns
November 14, 2016: Schulte starts at Bloomberg
December 16, 2016: Assange DM to Don Jr about becoming Ambassador
Hi Don. Hope you’re doing well! In relation to Mr. Assange: Obama/Clinton placed pressure on Sweden, UK and Australia (his home country) to illicitly go after Mr. Assange. It would be real easy and helpful for your dad to suggest that Australia appoint Assange ambassador to DC “That’s a really smart tough guy and the most famous australian you have! ” or something similar. They won’t do it, but it will send the right signals to Australia, UK + Sweden to start following the law and stop bending it to ingratiate themselves with the Clintons. 12/16/16 12:38PM
February 4, 2017: Wikileaks starts prepping Vault 7
March 7, 2017: Wikileaks starts releasing Vault 7; Schulte visits the site for the first time ever, after having conducted 20-some searches on WikiLeaks and read hundreds of articles about them
March 13, 2017: Initial search on apartment, Google, Github, Reddit search warrant
March 14, 2017, 1:36 AM: FBI presents second search application
March 14, 2017, 1:45 AM: Magistrate approves second search warrant
March 15, 2017 evening: FBI interview, Schulte denies having anything to do with the leak; Schulte admits he has a diplomatic passport he never returned to the CIA (but said it was in his apartment; it was in his backpack) in addition to his personal one; he leaves and goes to Bloomberg, where he tries to stash his passports
March 16, 2017: Schulte trip to Mexico scheduled
March 20, 2017: Search (including of cell phone, from which passwords to his desktop obtained)
March 20 – 21, 2017: Further FBI interviews, Schulte again denies involvement, denies making CIA network vulnerable to theft
March 23, 2017: Dark Matter released
March 31, 2017: Marble Framework — the one file obviously written by Schulte — released
April 5, 2017: FBI learns the number of SAs to the LAN might be higher or lower than 3 (PDF 138)
April 7, 2017: FBI finds child porn picture; Grasshopper Framework released
April 14, 2017: FBI obtains child porn/copyright crime warrant; HIVE development notes released
April 21, 2017: Weeping Angel released
April 28, 2017: Scribbles released
May 5, 2017: FBI obtains warrant for Bloomberg computer (PDF 129); Archimedes released
May 10, 2017: FBI obtains a new warrant for child porn, because FBI had continued to search for child porn before obtaining the April 14 warrant
May 12, 2017: After Midnight released
May 17, 2017: FBI obtains third child porn warrant
May 19, 2017: Athena released
June 1, 2017: Pandemic released
June 15, 2017: Cherry Blossom released
June 22, 2017: Brutal Kangaroo — another Schulte project, which he had taken with him and altered after doing so — released
June 26, 2017: Schulte interviewed about child porn
June 28, 2017: Elsa released
June 29, 2017: Interview, Schulte claims he didn’t work on Brutal Kangaroo outside of CIA, denies taking classified information home; Outlaw Country released
July 6, 2017: BothanSpy released
July 13, 2017: Highrise released
July 19, 2017: UCL/Raytheon released
July 27, 2017: Imperial released
August 3, 2017: Dumbo released
August 10, 2017: CouchPotato released
August 17, 2017: Dana Rohrabacher tries to broker deal for Assange with Trump
August 23, 2017: Arrest affidavit
August 24, 2017: Arraignment, ExpressLane released
THE COURT: Well, it sounds like, based on the interview, that he knew what the government was looking at.
MR. LAROCHE: That wasn’t the basis of the interview, your Honor.
MR. KOSS: I think it was either two or three [interviews]. I think it was three occasions. I was there on all three, including one of which where we handed over the telephone and unblocked the password to the phone, which they did not have, and gave that to them. And as I said, I have been in constant contact with the three assistant U.S. attorneys working on this matter literally on a weekly basis for the last 4, 5, 6 months. And any time Mr. Schulte even thought about traveling, I provided them an itinerary. I cleared it with them first and made sure it was okay. On any occasion that they said they might want him close so that he could speak to them, I cancelled the travel and rescheduled it so that we would be available if they needed him at any given time.
September 7, 2017: Protego released
September 13, 2017: Bail hearing
MR. LAROCHE: It does because of the manner in which he committed this crime, your Honor. It makes him more dangerous because he is a highly sophisticated individual when it comes to computers. He buried the child pornography within severals layers of encryption. It makes him more dangerous because he talked regularly in the IRC chats about the distribution and receipt of child pornography. So we do believe that it makes him more dangerous and separates him from —
THE COURT: The IRC chats according to the complaint stops in 2009.
MR. LAROCHE: We don’t believe that they stopped, your Honor.
THE COURT: No record of it.
MR. LAROCHE: It’s simply that we don’t have a record of it.
[snip]
MR. LAROCHE: Well, I believe there still is a danger because it’s not just computers, your Honor, but electronic devices are all over society and easy to procure and this type of defendant having the type of knowledge he has does in terms of accessing things — so he has expertise and not only just generally computers but using things such as wiping tools that would allow him to access certain website and leave no trace of it. Those can be done from not just a computer but from other electronic devices.
But the child pornography itself is located on the defendant’s desktop computer. They can be accessed irrespective of those servers. So if all the government had was this desktop computer, we could recover the child pornography. So I think this idea that numerous people had access to the serves and potentially could have put it there, is simply a red herring. This was on the defendant’s desktop computer. And the location where it was found, this sub-folder within several layers of encryption, there were other personal information of the defendant in that area. There was his bank accounts. I think there was even a resume for the defendant where he was storing this information. And the passwords that were used to get into that location, those passwords were the same passwords the defendant used to access his bank account, to access various other accounts that are related to him. So this idea that he shared them with other people, the government just strongly disagrees.
October 11, 2017: Schulte lawyer Spiro withdraws
October 17, 2017: CIA WikiLeaks Task Force completed
October 24, 2017: At Trump’s request Bill Binney meets with Mike Pompeo to offer alternate theory of the DNC hack
November 8, 2017: Status hearing; almost certainly the court hearing where Schulte traveled to the appearance from vicinity of Grand Central, possible conversation with man he claimed not to know
SMITH: I believe the government has told us that there’s more data in this case than in any other like case that they have prosecuted.
MR. STANSBURY: Let me just clarify that part first. We proposed this just in an abundance of caution given the defendant’s former employer and the fact that — and I meant to flag this before. I apologize now for not. There’s a small body of documents that were found in the defendant’s residence that were taken from his former employer that might implicate some classified issues. We have been in the process of having those reviewed and I think we’re going to be in a position to produce those in the next probably few days. But we wanted to just make sure that we were acting out of an abundance of caution in case any SEPA [sic] issues come about in the case. I don’t expect them too at this point but we wanted to do that out of an abundance of caution.
November 9, 2017: Wikileaks publishes Vault 8 exploit
November 14, 2017: Assange posts Vault 8 Ambassador follow-up
November 14, 2017: Arrest warrant in VA
November 15, 2017: Charged in Loudon County for sexual assault
November 16, 2017: Schulte falsely describes a trip (probably on November 8) to court from Grand Central vicinity, and falsely claims to have met an unknown male who told him the US had bankrupted and betrayed him
November 16, 2017: Use of Tor
November 17, 2017: Use of Tor
November 26, 2017: Use of Tor
November 29, 2017: Abundance of caution, attorney should obtain clearance
November 30, 2017: Use of Tor
December 5, 2017: Use of Tor, Smith withdraws
December 6, 2017: Most recent access of Gmail
December 7, 2017: NYPD arrests on VA warrant for sexual assault; letter motion for detention
December 12, 2017: Move for detention, including description of email and Tor access
Separately, since the defendant was released on bail, the Government has obtained evidence that he has been using the Internet. First, the Government has obtained data from the service provider for the defendant’s email account (the “Schulte Email Account”), which shows that the account has regularly been logged into and out of since the defendant was released on bail, most recently on the evening of December 6, 2017. Notably, the IP address used to access the Schulte Email Account is almost always the same IP address associated with the broadband internet account for the defendant’s apartment (the “Broadband Account”)—i.e., the account used by Schulte in the apartment to access the Internet via a Wi-Fi network. Moreover, data from the Broadband Account shows that on November 16, 2017, the Broadband Account was used to access the “TOR” network, that is, a network that allows for anonymous communications on the Internet via a worldwide network of linked computer servers, and multiple layers of data encryption. The Broadband Account shows that additional TOR connections were made again on November 17, 26, 30, and December 5.
[snip]
First, there is clear and convincing evidence that the defendant has violated a release condition—namely, the condition that he shall not use the Internet without express authorization from Pretrial Services to do so. As explained above, data obtained from the Schulte Email Account and the Broadband Account strongly suggests that the defendant has been using the Internet since shortly after his release on bail. Especially troubling is the defendant’s apparent use on five occasions of the TOR network. TOR networks enable anonymous communications over the Internet and could be used to download or view child pornography without detection. Indeed, the defendant has a history of using TOR networks. The defendant’s Google searches obtained in this investigation show that on May 8, 2016, the defendant conducted multiple searches related to the use of TOR to anonymously transfer encrypted data on the Internet. In particular, the defendant had searched for “setup for relay,” “test bridge relay,” and “tor relay vs bridge.” Each of these searches returned information regarding the use of interconnected computers on TOR to convey information, or the use of a computer to serve as the gateway (or bridge) into the TOR network.
December 14, 2017: Bail hearing; US custody in NY
MR. KAPLAN: Well, your Honor, we’ve obtained the discovery given to prior counsel, and I’ve started to go through that. In addition, there was one other issue which I believe was raised at our prior conference, which was a security clearance for counsel to go through some of the national security evidence that might be present in the case.
While most of the national security stuff does not involve the charges, the actual charges against Mr. Schulte, the basis for the search warrants in this case involve national security.
So I’m starting the process with their office to hopefully get clearance to go through some of the information on that with an eye towards possibly a Franks motion going forward. So I would ask for more time just to get that rolling.
December 21, 2017: Complaint filed against Julian Assange
January 8, 2018: Bail appeal hearing
MR. KAPLAN: Judge, on the last court date, when we left, the idea was that we had consented to detention with the understanding that Mr. Schulte would be sent down to Virginia to face charges based on a Virginia warrant. None of that happened. Virginia never came to get him. Virginia just didn’t do anything in this case. But before I address the bail issues, I think it’s important that this Court hear the full story of how we actually get here. At one of the previous court appearances, I believe it was the November 8th date, this Court asked why the defense attorney in this case would need security clearance. And the answer that was given by one of the prosecutors, I believe, was that there was some top secret government information that was found in Mr. Schulte’s apartment, and that out of an abundance of caution it would be prudent that the defense attorney get clearance. But I don’t think that’s entirely accurate.
While the current indictment charges Mr. Schulte with child pornography, this case comes out of a much broader perspective. In March of 2017, there was the WikiLeaks leak, where 8,000 CIA documents were leaked on the Internet. The FBI believed that Mr. Schulte was involved in that leak. As part of their investigation, they obtained numerous search warrants for Mr. Schulte’s phone, for his computers, and other items, in order to establish the connection between Mr. Schulte and the WikiLeaks leak.
As we will discuss later in motion practice, we believe that many of the facts relied on to get the search warrants were just flat inaccurate and not true, and part of our belief is because later on, in the third or fourth search warrant applications, they said some of the facts that we mentioned earlier were not accurate. So we will address this in a Franks motion going forward, but what I think is important for the Court is, in April or May of 2017, the government had full access to his computers and his phone, and they found the child pornography in this case, but what they didn’t find was any connection to the WikiLeaks investigation. Since that point, from May going forward, although they later argued he was a danger to the community, they let him out; they let him travel. There was no concern at all. That changed when they arrested him in August on the child pornography case.
[snip]
The second basis that the government had in its letter for detaining Mr. Schulte was the usage of computers. In the government’s letter, they note how, if you search the IP address for Mr. Schulte’s apartment, they found numerous log-ons to his Gmail account, in clear violation of this court’s order. But what the government’s letter doesn’t mention is that Mr. Schulte had a roommate, his cousin, Shane Presnall, and this roommate, who the government and pretrial services knew about, was allowed to have a computer.
And more than that, based on numerous conversations, at least two conversations between pretrial services, John Moscato, Josh Schulte and Shane Presnall, it was Shane’s understanding that pretrial services allowed him to check Mr. Schulte’s e-mail and to do searches for him on the Internet, with the idea that Josh Schulte himself would not have access to the computer.
And the government gave 14 pages of log-on information to establish this point. And, Judge, we have gone through all 14 pages, and every single access and log-in corresponds to a time that Shane Presnall is in the apartment. His computer has facial recognition, it has an alphanumeric code, and there is no point when Josh Schulte is left himself with the computer without Shane being there, and that was their understanding.
LAROCHE: As defense counsel noted, in March of 2016, there was a significant disclosure of classified material from the Central Intelligence Agency. The material that was taken was taken during a time when the defendant was working at the agency. The government immediately had enough evidence to establish that he was a target of that investigation. They conducted a number of search warrants on the defendant’s residence. And I would disagree with defense counsel’s characterization that those search warrants haven’t yielded anything that is consistent with his involvement in that disclosure. In fact, our investigation is ongoing. He remains a target of that investigation. And part of that investigation is analyzing whether and to what extent TOR was used in transmitting classified information. So the fact that the defendant is now, while on pretrial release, using TOR from his apartment, when he was explicitly told not to use the Internet, is extremely troubling and suggests that he did willfully violate his bail conditions.
KAPLAN: In this case, the reason why TOR was accessed was because Mr. Schulte is writing articles, conducting research and writing articles about the criminal justice system and what he has been through, and he does not want the government looking over his shoulder and seeing what exactly he is searching.
LAROCHE: Because there is a classified document that is located on the defendant’s computer, it is extremely difficult, and we have determined not possible, to remove that document forensically and still provide an accurate copy of the desktop computer to the defendant.
So in those circumstances, defense counsel is going to require a top secret clearance in order to view these materials. It’s my understanding that that process is ongoing, and we have asked them to expedite it. As soon as the defendant’s application is in, we believe he will get an interim classification to review this material within approximately two to three weeks. Unfortunately, that hasn’t occurred yet. So the defendant still does not have access to that particular aspect of discovery. So we are working through that as quickly as we can.
January 17, 2018: Bail appeal denied
March 6, 2018: 2nd Circuit upholds denial of bail
March 8, 2018: Julian Assange indicted
March 15, 2018: Status hearing; Sabrina Shroff appointed
March 28, 2018: Initial ban of Internet access and visitors for Assange
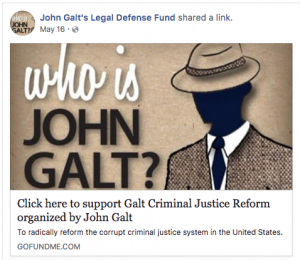
April 15, 2018: Schulte creates John Galt Gmail account
April 16, 2018: Due to conflict, Shroff asks for a delay in status hearing
April 17, 2018: Schulte creates Who is John Galt site
April 18, 2018: Jail call in which Schulte directs a reporter how to ID other CIA officers
April 20, 2018: Schulte’s diaries (ostensibly the purpose of using Tor) posted
May 3, 2018: Shroff asks for another delay
May 10, 2018: Ecuador bans visitors for Assange
May 11, 2018: Status hearing; additional charges (including conspiracy) discussed
The government also tells me that they are not yet ready, and I’m going to ask the Court for some relief on this point, in terms of superseding Mr. Schulte with the additional charges that they’ve been talking about bringing.
[snip]
MR. LAROCHE: The superseder, that’s correct, your Honor. As the Court is aware, this case — the investigation — started not as a child pornography investigation but a broader investigation that’s been referred to during court. The government is moving as quickly as possible to try to get to a superseder in this case, and we are anticipating that there will be a superseder. Because of the nature of the underlying investigation, that requires consultation with people outside of our office, which we are doing as quickly as we can. We’re trying to get that done. THE COURT: Can you put a time frame on this, Mr. Laroche? MR. LAROCHE: We are hopeful that we will get this done within the next 45 days. That’s our hope. We’re moving as quickly as we can to get that done, and as I said, we’re consulting with a lot of folks that are not within our office, so we’re moving as quickly as we can on that front.
[snip]
MS. SHROFF: Mr. Schulte has been under indictment, as I understand it, or at least under arrest, since August of 2017. I came in late, so I want to make sure my dates are not wrong. I’m not asking Mr. Laroche or the government to tell me what it is they’re doing in the grand jury. But surely telling me that they’re going to investigate him or charge him with, I don’t know, an 18 U.S.C. 371 violation — or are they charging him with sedition? Are they charging him with espionage? I’d like to know generally out loud what Mr. Schulte is being charged with. I don’t think it should be a secret what he’s being charged with. That’s No. 2. And August of 2017, we’re almost at — look, I’m not pushing this, because I’m behind in my review, so I want to be candid with the Court, but I doubt it’s fair to Mr. Schulte to first proceed on a child pornography trial and then proceed on a second trial when the evidence of the two is clearly interlinked, as is the motion practice. Basically we’re just spinning our wheels here. I ask the Court most respectfully to set a deadline. Either they supersede or they’re done.
May 15, 2018: WaPo and NYT report that Schulte is suspect for Vault 7
May 16, 18, 2018: Sealed documents placed in vault
May 16, 2018: Schulte Facebook site starts legal defense fund
May 21, 2018: Hearing on violation of protective order
June 7, 2018: Pro se bail application
June 18, 2018: Schulte superseding indictment
June 19, 2018: Wikileaks posts links to diary
June 20, 2018: Arraignment on new charges
June 28, 2018: Status hearing; Schulte provides judge with pro se filing that includes classified information
July 10, 2018: Sealed document placed in vault
August 8, 2018: Status hearing (including sidebar on pro se motions)
August 14, 2018: Schulte creates three WordPress sites: joshschulte, presumtionofslavery, presumptionofinnocence
August 21, 2018: To do list includes “delete all Google Docs from johnsmith,” “delete all emails from johnsmith,” “delete suspicious emails from my gmail,” “create new protonmail,” “presumed guilty,” “migrate wordpress to protonmail”
August 22, 2018: Schulte changes WordPress email to Protonmail
August 30, 2018: Presumed date for draft fake CIA tweet
September 1, 2018: Using contraband phone, Schulte creates @freejasonbourne Twitter account
September 3, 2018: Schulte creates Buffer account (used to schedule social media posts)
September 12, 2018: Schulte makes to do list for his information war
September 17 and 18, 2018: Dates Schulte planned to download discovery and upload it to WikiLeaks; posted to Facebook
September 25, 2018: Schulte posts to wordpress
September 28, 2018: Brady letter corrects details in initial warrant applications
October 1, 2018: Schulte posts Master of Whisperers article
October 2, 2018: Schulte placed in SHU, final login for his Twitter account; FBI obtains warrant for cell
October 3, 2018: Search of Schulte’s cell; FBI obtains warrant on Conj Khyas account (not provided)
October 5, 2018: Recovery of phones
October 6, 2018: FBI obtains warrant for 3 Proton Mail accounts found on Schulte’s phone, documents in cell
October 8, 2018: Content posted on WordPress
October 26, 2018: SAMS imposed; FBI obtains warrant for social media accounts
October 31, 2018: 2nd Superseding indictment and letter
November 2, 2018: Arraignment
February 5, 2019: Announcement that server with Schulte’s unclassified discovery “misplaced”
March 20, 2019: Signed date of lawsuit
March 26, 2019: Schulte requests that search warrants no longer be covered by protective order
March 29, 2019: Parties request adjournment to November 4, 2019
April 2, 2019: Government objects to release of search warrants
April 11, 2019: Julian Assange indicted
April 12, 2019: Schulte sues the Attorney General for SAMs
April 17, 2019: Schulte appeals Crotty order on protective order
April 15, 2109: Judge Crotty denies motion to exclude warrants from protective order
April 29, 2019: Bill of particular lays out accusations against Schulte
May 10, 2019: Schulte moves to vacate SAMs
May 23, 2019: Superseding Assange indictment
June 17, 2019: Government response to motion to vacate SAMs
June 18, 2019: First motion to suppress evidence (from jailhouse searches)
June 19, 2019: Schulte moves to sever child porn trial from CIA leak trial; government de-designates discovery as confidential