Before Rand Paul Went to Moscow, He Was in a White House Meeting Discussing Lisa Page, Peter Strzok, and Andrew McCabe
/30 Comments/in 2016 Presidential Election, Mueller Probe /by emptywheelPeter Strzok filed what is billed as a motion for clarification of Judge Amy Berman Jackson’s order last week requiring that Strzok’s deposition of FBI Director Chris Wray take place before Strzok’s deposition of Trump.
In part, it is a fact check, laying out all the ways that DOJ seems to have panicked after (and because) Strzok scheduled a deposition with the former President on May 24.
In part, it seems to be an effort to pre-empt DOJ’s threat to file for a writ of mandamus against ABJ because she permitted these depositions. For example, Strzok’s lawyers describe how much easier it was to schedule time with the unemployed former President than with the FBI Director. Under the Apex doctrine that DOJ claims to be adhering to, that should mean that Wray’s deposition should come after Trump’s (and indeed, that’s effectively what DOJ seemed to argue last year).
More interesting, though, are notes Strzok included to establish a need to depose Trump regardless of what Wray says, both taken by John Kelly when he was Chief of Staff.
According to Kelly’s own transcription, this February 21, 2018 note reads:
Potus, AG, Don McGahn
- Deep state issues
- Investigations
- Firing love birds
McCabe?
- Trust?
This note establishes that pressure to fire Strzok and Page may have bypassed Wray. McCabe was fired weeks later.
More curious still, however, is this note:
Kelly transcribed the July 23, 2018 note this way:
Potus, Rand Paul +2
Security clearances
*add Page, McCabe, Stroch (sic)
For some reason, a week after Trump submitted to Vladimir Putin in Helsinki on July 16 and 15 days before Paul would carry a letter from Trump to Putin expressing an interest in remaining besties, Paul was in a meeting discussing the FBI officials Trump had a vendetta against (who also happen to be Russian experts).
Days after Paul returned from Moscow, the FBI fired Strzok.
Update: Per Rand’s Twitter account, he met with Trump to discuss revoking John Brennan’s security clearance that day.
Ben Smith Still Doesn’t Understand He Peddled Likely Russian Disinformation
/49 Comments/in 2016 Presidential Election, Mueller Probe /by emptywheelI’m not sure whether it was just chance or whether Ben Smith knew in advance that BuzzFeed would announce the closure of its news division on the same day that he posted an account of publishing the Steele dossier. His account doesn’t explain whether the cost of defending against serial Russian lawfare for publishing the dossier made it harder, in the aftermath, to pay journalists’ salaries, but it’s a question that deserves an answer.
But Ben’s account — which focuses, as most of Ben’s writing does, on insider news media stuff — makes two grave errors.
The first is that — even though he quotes Pete Strzok describing how the dossier framed the Russian investigation, thereby inoculating Trump against accountability for the very real scandalous behavior he had with Russia — Ben falsely suggests that the dossier was the genesis of the public concern about Trump’s ties to Russia.
We had embedded it as a PDF, which meant that it could travel context-free, without our article’s careful disclaimers, and that’s exactly what happened. I watched uneasily as educated Democrats who abhorred Trump supporters’ crude rants about child sex rings in Washington pizza joints were led by the dossier into similar patterns of thought. They read screenshots of Steele’s report; they connected the dots. They retweeted threads about how the plane of a Russian oligarch—previously unknown to them, now sinister—had made a mysterious stop in North Carolina.
[snip]
It had blown wide open a Russia investigation and forced voters to ask just why Trump seemed so friendly with Vladimir Putin.
[snip]
An FBI agent who investigated Trump, Peter Strzok, later said the dossier “framed the debate” in a way that ultimately helped Trump: “Here’s what’s alleged to have happened, and if it happened, boy, it’s horrible—we’ve got a traitor in the White House. But if it isn’t true, well, then everything is fine.”
The notion that Democrats and national security hawks weren’t concerned about Trump’s Russian ties until January 10, 2017 is ludicrous. The effort to understand Trump’s Russian ties went into high gear on July 27, 2016, when he encouraged Russia to attack his opponent and floated recognizing the annexation of Crimea. It never stopped thereafter.
And, as I had to explain patiently to Columbia Journalism Review, even the intense press reporting on Trump’s real ties to Russia started before January 10, because the WaPo was already onto Mike Flynn’s lies about his outreach to Sergey Kislyak by then. Strzok’s point, I think, is that publishing the dossier made it easier for Trump to get away with attempting to undermine sanctions on Russia and all the rest because at least undermining sanctions wasn’t a pee tape.
No one needed the dossier to heighten concerns about Trump’s fondness for Russia. That’s a myth created by Russiagate [sic] peddlers trying to distract from the very real scandal of Trump’s ties to Russia.
Ben’s other silence, though, is irresponsible.
As I have noted, as the Carter Page IG Report makes clear, and as Republicans in Congress have come to agree, there’s abundant reason to believe that Russians started feeding Igor Danchenko with disinformation from the start. Lawyers for Oleg Deripaska were likely the client for a Steele collection effort targeting Paul Manafort in March 2016. According to declassified footnotes in the IG Report, Deripaska likely learned of the dossier project before the second report. And he demonstrably played a double game throughout 2016, getting Steele to feed Bruce Ohr damaging claims about Manafort at the same time as his aide, Konstantin Kilimnik, was exploiting Manafort’s legal and financial vulnerability to get information on the Trump campaign and a commitment to help carve up Ukraine.
This dynamic is utterly central to understanding the dossier. Someone who played a central role in the 2016 Russian operation knew about the dossier project, and had means to know of Danchenko’s collection network, almost from the start. And that makes it likely that at least some of the content of the dossier was tailored to be wrong in ways that benefitted the Russian operation.
Ben’s silence about the likelihood that he unwittingly peddled Russian disinformation is all the more embarrassing given how his post transitions directly from suggesting that John Durham had “poked holes in Steele’s sourcing” to noting that there was something that Trump actually was lying to cover up: the impossibly lucrative Trump Tower deal in Moscow.
Simpson then told Ken something he didn’t know: Steele had been working the case of the president-elect, Donald Trump, and he’d assembled evidence that Trump had close ties to the Kremlin—including claims that Michael Cohen, one of his lawyers, had held secret meetings with Russian officials in Prague, and that the Kremlin had a lurid video of Trump cavorting with prostitutes in the Ritz-Carlton Moscow that would come to be known as the “pee tape.”
[snip]
But although the biggest-picture claim—that the Russian government had worked to help Trump—was clearly true, the release of Special Counsel Robert Mueller’s investigation in April 2019 did not support Steele’s report. Indeed, it knocked down crucial elements of the dossier, including Cohen’s supposed visit to Prague. Internet sleuths—followed by a federal prosecutor—had poked holes in Steele’s sourcing, suggesting that he’d overstated the quality of his information.
And there had always been a more mundane version of the Trump-Russia story. Trump was the sort of destabilizing right-wing figure that Putin had covertly supported across Europe. Trump’s value to Putin was related not to a secret deal, but to the overt damage he could do to America. And Trump, BuzzFeed News’s Anthony Cormier and Jason Leopold discovered, had a more mundane interest in Russia as well: He had drawn up plans to build the biggest apartment building in Europe on the banks of the Moskva River. The Trump Organization planned to offer the $50 million penthouse to Putin as a sweetener.
That real-estate project wasn’t mentioned anywhere in the dossier. Yet it seemed to explain the same pattern of behavior, without the lurid sexual allegations or hints of devious espionage.
The man responsible for publishing both the Steele dossier and the best reporting on the Trump Tower Moscow deal seems not to understand that false claims about Michael Cohen in the dossier were likely there because of the Trump Tower deal.
Ben invokes what Durham’s failed prosecution revealed about (what Ben mistakenly claims to be) Danchenko’s sourcing, without laying out the import of Danchenko’s ties to Charles Dolan: Dolan gave the source of the Cohen claims in the dossier, Olga Galkina, direct access to Dmitri Peskov, the one man in Russia with proof that when Trump falsely claimed in July 2016 that he wasn’t pursuing real estate deals in Russia, he was lying. Even Durham implied this was the import of Dolan’s relationship with Galkina! Dolan was important because he put Galkina, who was sending dirt on Trump to her childhood buddy, Igor Danchenko, in close touch with Peskov.
The source of the claims that Cohen had secret communications with the Kremlin in the dossier had direct ties to the one guy in Russia, Peskov, who provably knew that Cohen really did have secret communications directly with the Kremlin that he and Trump were lying to hide.
Once Trump publicly lied about chasing real estate deals in Russia in July 2016, it made the notes Peskov’s aide took, showing that Cohen had agreed to work with sanctioned banks and a retired GRU officer as fixer in order to chase one such deal, far more valuable to Russia, particularly after it became clear in the US that the GRU was behind the hack of Hillary. So it is likely not random at all that someone with direct access to Peskov told Danchenko that Cohen — who was lying to hide his real direct contact with the Kremlin during the election — had other, more damning direct contact with the Kremlin. It raised the stakes of Trump’s and Cohen’s lies. It raised the value of Russia’s silence about the earlier conversation with Peskov. To the extent that everyone kept their shared secret — and they did for the entire first year of the Trump Administration — it provided cover for the lies that Cohen would tell to Congress.
From the start, the FBI had warnings that the Cohen in Prague story was disinformation. And it just so happens that the story, which came from someone with ties to Peskov, repeated a true fact that Peskov knew: that Cohen really did have secret communications with the Kremlin, communications that had already compromised Trump and Cohen with Russia before the hacking even started. If the Cohen in Prague story was disinformation (and, again, FBI got warnings it was the day after Ben published the dossier), it was disinformation that made that earlier compromise more powerful.
And Ben Smith, who played a key role in disseminating that likely disinformation, appears to not even understand that, much less want to reflect on his role in being an unwitting mule for Russian disinformation.
How the Government Proved Their Case against John Podesta’s Hacker
/4 Comments/in 2016 Election, Cybersecurity, emptywheel, Financial Fraud, Mueller Probe /by emptywheelWe’re almost seven years past the hack of the DNC, and self-imagined contrarians are still clinging to conspiracy theories about the attribution of that and related hacks. In recent weeks, both Matt Taibbi and Jeff Gerth dodged questions about the attribution showing Russia’s role in the hack-and-leak by saying that the Mueller indictment of twelve GRU officers would never be tested in court (even while, especially in Gerth’s case, relying on unsubstantiated claims in John Durham indictments from his two failed prosecutions).
And while’s it’s likely true that DOJ will never extradite any of those twelve men to stand trial, DOJ did successfully convict one of their co-conspirators on a different hack: the hack-and-trade conspiracy involving Vladimir Klyushin and accused John Podesta hacker, Ivan [Y]Ermakov.
(The Mueller indictment and Ermakov’s second US indictment, for hacking anti-doping agencies, transliterated his name with a Y, the Boston one does not.)
That trial provides a way to show how DOJ would prove the 2018 indictment if one of the twelve men charged ever wandered into a jurisdiction with an extradition treaty with the US.
As laid out at trial, between 2018 and 2020, the co-conspirators hacked two securities filing agencies, Toppan Merrill and Donnelly Financial, to obtain earnings statements in advance of their filing, then traded based off advance knowledge of earnings. Klyushin was one of seven people (two charged in a separate indictment, three who were clients of Klyushin’s company M-13) who did the trading. Ermakov didn’t trade under his own name. He may have been compensated for Klyushin’s side of the trades with a Moscow home and a Porsche. But at least as early as May 9, 2018, forensic evidence introduced at trial shows, an IP address at which Ermakov’s iTunes account had just gotten updates was used to steal some of the filings.
Ermakov did not show up in a courtroom in Boston to stand trial and Klyushin has launched a challenge to his conviction that rests entirely on a challenge to venue there. But the jury did convict Klyushin on the hacking charge along with the trading charges, meaning a jury has now found DOJ proved Ermakov’s hacking beyond a reasonable doubt.
And they did it using the same kind of evidence cited in the Mueller indictment.
The crime scene
Start with the crime scene: the servers of the two filing agencies victimized in the hack-and-trade, Toppan Merrill and Donnelly Financial.
According to the trial record, neither figured out they had been hacked on their own. As the FBI had tried to do for months beforehand in the case of the DNC, a government agency, the SEC, had to tell them about it. The SEC had seen a number of Russians making big, improbable stock trades from clients of the two filing agencies, all in the same direction, and wanted to know why. So it sent subpoenas to both companies.
As the DNC did with CrowdStrike in 2016, both filing agencies hired an outside incident response contractor — Kroll Cyber in the case of Toppan Merrill, Ankura in the case of Donnelly Financial — to conduct an investigation.
The lead investigators from those two contractors were the first witnesses at trial. Each explained how they had been brought in in 2019 and described what they found as they began investigating the available logs, which went back six months, a year, and two years, depending on the type and company. The witness from Kroll described finding signs of hacking in Toppan Merrill’s logs:
- A November 28, 2018 use of DirBuster used to brute force file structure on a server
- Evidence of someone renaming PowerShell, RDTEVC, on December 23, 2019 to hide its use
- A December 25, 2019 use of a renamed copy of PuTTY remote access software
- A January 10, 2019 instance of a user invoking MimiKatz
- 8 domains from which intrusions had come with names like “developingcloud” and “finshopland”
- An IP associated with unauthorized activity from an AirVPN address.
The Ankura witness described how they first found the account of employee Julie Soma had been compromised, then used the IP addresses associated with that compromise to find other employees whose accounts were used to download reports or other unauthorized activity.
In sum, the two incident response witnesses described providing the FBI with the forensic details of their investigation — precisely the same thing that CrowdStrike provided to FBI from the DNC hack. There’s not even evidence that they shared a full image of the filing agencies’ servers (though an FBI agent described going back to Donnelly to search for the domain names behind the intrusions that Kroll had found at Toppan Merrill), which was one of the first conspiracy theories about the DNC hack Republicans championed: that the FBI failed to adequately investigate the DNC hack because it didn’t insist on seizing the actual victim servers during the middle of an election.
The forensic evidence wasn’t the only evidence submitted at trial from the crime scene. One after another of the employees whose credentials had been misused testified. Each described why they normally accessed customer records, if at all, how and when they would normally access such records, and from what locations they might access corporate servers remotely, including their use of the corporate VPN. Julie Soma — the Donnelly employee whose credentials were used most often to download customer filings — described that she would never have done what was done in this case, download one after another filing from Donnelly customers in alphabetical order.
Q. Would you ever go from client to client and alphabetically access those types of documents?
A. No.
Both interview records from the Mueller investigation (one, two, three) and documents from the Michael Sussmann case show that the FBI did similar interviews in the DNC hack. The Douglass Mackey trial, too, featured witnesses describing how the Hillary campaign identified that attack on the campaign as well.
In proving their case against John Podesta’s hacker, DOJ presented witness testimony that eliminated insiders as the culprit.
Fingerprinting
Having established the forensic data tied to intruders through the incident response contractors, prosecutors then called FBI agents as witnesses to describe how — largely through the use of IP addresses obtained using subpoenas or pen registers and the materials found in the suspects’ iCloud accounts — they tied Klyushin’s company, M-13, to both the hacking and the trading.
The trading was fairly easy: the co-conspirators accessed the two online brokers used to execute the trades under their own names and from IP addresses tied to M-13. An SEC witness described in detail how trades always shortly followed hacks but preceded the public filing of earnings statements.
Tying M-13 to the hacking took a few more steps.
For the hacking conducted via the domains Kroll identified, the FBI first found the account that registered the domains. Each was registered under a different name, but each of the names were based on a Latvian-based email service and used similar naming conventions. Each had been accessed from the same set of 3 IP addresses.
For IPs that Kroll identified, the FBI found BitLaunch servers created by an account in the name of Andrea Neumann, which was controlled from one of the same IP addresses that had registered the domain names. The FBI got search warrants to obtain images of those BitLaunch servers.
Another IP address used to steal filings, several FBI agents explained, was from an Italian-run VPN, AirVPN. The FBI used a pen register to show that someone accessed AirVPN from the M-13 IP address during the same period when the AirVPN IP was stealing records from the filing companies. The FBI also showed that Klyushin had accessed his bank at the same time from that same IP address. The FBI also showed that eight common IP addresses had accessed Ermakov’s iTunes account and the AirVPN IP address (in this case, the access was not at the same time because the FBI only had a pen register on the VPN for two months in 2020). While FBI witnesses couldn’t show that the specific activity tied to an AirVPN IP at the victim companies tied back to M-13, they did show that both Klyushin and Ermakov routinely used AirVPN.
Plus there were the filing thefts — noted above — that were done on May 9, 2018 using the same IP address that, four minutes earlier, had downloaded an Apple update from Ermakov’s iTunes account. As I’ve noted repeatedly, before Ermakov was first indicted by Mueller, he had already left a smoking gun in the servers at Donnelly in the form of IP activity that the FBI obtained over a year later inside the US.
In fact, much of the evidence used to prove this case (particularly establishing the close relationship between the conspirators) came from Apple, including WhatsApp chats saved in Klyushin and other co-conspirators’ iCloud accounts. We know Mueller used the same source of evidence. In March of this year, emails stolen by hacktivists revealed, Apple informed another of the GRU officers charged in the DNC hack that the FBI had obtained material from his Apple account in April 2018, in advance of the Mueller indictment.
The indictment likely also relied on warrants served on Google, especially on Ermakov’s account. The Mueller indictment (as well as the later anti-doping one) attributes much of the reconnaissance conducted in advance of the hacks to Ermakov: the names of some victims; information on the DNC, the Democratic Party, and Hillary; how to use PowerShell (which would be used against Toppan Merrill); and CrowdStrike’s reporting on GRU tools. If he did this research via Google, it would all be accessible with a warrant served on the US tech company.
The getaway car
One pervasive conspiracy theory about the Mueller indictment stems from testimony that Shawn Henry gave to the House Intelligence Committee in December 2017, describing that Crowdstrike did not see the data exfiltrated from the DNC servers. Denialists claim that is proof that the information was never exfiltrated by the GRU hackers. The conspiracy theory is ridiculous in any case, since there were so many other Russian hacks involving so many other servers, including servers run by Google and Amazon that had a different kind of visibility on the hack (something that Henry alluded to in his testimony), and since the indictment describes that the DNC hackers destroyed logs to cover their tracks.
But the Klyushin trial featured testimony about a tool used in the hack-and-trade conspiracy that has a parallel in the DNC hack: the AMS panel, hidden behind an overseas middle server, which the Mueller indictment described this way:
X-Agent malware implanted on the DCCC network transmitted information from the victims’ computers to a GRU-leased server located in Arizona. The Conspirators referred to this server as their “AMS” panel. KOZACHEK, MALYSHEV, and their co-conspirators logged into the AMS panel to use X-Agent’s keylog and screenshot functions in the course of monitoring and surveilling activity on the DCCC computers. The keylog function allowed the Conspirators to capture keystrokes entered by DCCC employees. The screenshot function allowed the Conspirators to take pictures of the DCCC employees’ computer screens.
[snip]
On or about April 19, 2016, KOZACHEK, YERSHOV, and their co-conspirators remotely configured an overseas computer to relay communications between X-Agent malware and the AMS panel and then tested X-Agent’s ability to connect to this computer. The Conspirators referred to this computer as a “middle server.” The middle server acted as a proxy to obscure the connection between malware at the DCCC and the Conspirators’ AMS panel. On or about April 20, 2016, the Conspirators directed X-Agent malware on the DCCC computers to connect to this middle server and receive directions from the Conspirators.
[snip]
For example, on or about April 22, 2016, the Conspirators compressed gigabytes of data from DNC computers, including opposition research. The Conspirators later moved the compressed DNC data using X-Tunnel to a GRU-leased computer located in Illinois.
In the hack-and-trade conspiracy, the hackers set up a similar structure, using the servers given names like “developingcloud” and “finshopland” as reverse proxies, with a final server behind them all executing orders on the hacked servers at Toppan Merrill (and the implication is, Donnelly, though the forensics came from Toppan Merrill via Kroll). The “computers numbered 1 through 7” in what follows are the servers identified by Kroll stealing earnings filings from Toppan Merrill.
A. So this is a digital depiction of the servers that I examined on the right there, so they each have a number on them, 1 through 9.
Q. Let me focus you first on the computers numbered 1 through 7. Do you see them there?
A. Yes.
Q. Are they kind of in a sideways V configuration?
A. Yes.
Q. Okay. And what do computers 1 through 7 show on this Exhibit DDD?
A. They functioned as gatekeepers for the furthest machine to the right, server number 8.
Q. And when you say “gatekeeper,” is there a technical term for that?
A. Yes. So the technical term is a “reverse proxy.”
Q. Can you explain to the jury, in a easy for me to understand way, what a reverse proxy or gatekeeper is in this chart, 1 through 7.
A. Yes. So in this chart, it would function — so the seven that are in that V formation, they would pass traffic to server number 8, if it was coming from an infected machine; and if it was something else, it would send the traffic to some other website.
This structure would have made it impossible for Toppan Merrill to understand the source or function of the anomalous traffic on its servers because any attempt to do so would be redirected away from the control server.
But not the FBI, because they obtained images of the servers with a warrant.
The forensic witness describing this structure showed, command by command, that the forensic clues identified by Kroll on the Toppan Merrill servers were controlled via that final server running PowerShell (the same tool that Mueller alleged Ermakov researched during the DNC hacks in 2016).
Q. And is there something on this log that you found that tells you the name of the program that was running on the victim’s computer at Toppan Merrill?
A. Yes, the process name line, and that reads rdtevc.
Q. And is process another name for computer program?
A. Yes.
Q. So this is a log that shows that a program named RDTEVC was running on a Toppan Merrill computer, right?
A. Yes.
Q. But it’s stored in the hacker computer?
[snip]
Q. And what does PowerShell do? You can call it anything, right? You can call it RDTEVC?
A. That’s probably a randomly chosen name.
Q. But no matter what it’s called, what does it do?
A. So it allows it to be remotely controlled and accessed.
Q. Allows what to be remotely controlled and accessed?
A. The infected machine.
The same forensic expert explained that he didn’t find any downloads of stolen files.
But he also explained why.
He had also found secure tunnels, readily available but similar in function to a proprietary GRU tool Crowdstrike found in the DNC server. As he described, these would be used to transfer data in encrypted form, making it impossible to identify the content of the data while it was in transit.
Q. Mr. Uitto, are you familiar with the concept of exfiltration?
A. Yes.
Q. Big word, but what does it mean?
A. It means to steal data, take data.
Q. And in your review, did you find evidence — you told Mr. Nemtsev you didn’t find evidence of the taking of data from the victim computers to these particular hacker servers; is that right?
A. That’s right, but I did see secure tunnels that were created.
Q. So when you say there were secure tunnels, were you able to tell what was going through those secure tunnels?
A. No.
Q. Those were encrypted, right?
A. Yes.
Q. So you actually don’t know whether or not there was financial information in those tunnels?
A. That’s correct.
Q. Or sports scores or anything?
A. That’s correct.
Q. It’s encrypted.
A. Yes.
[snip]
Q. What role does encryption serve in this hacker architecture?
[snip]
A. Yes, so it can be used to hide data or information.
Q. So if it’s encrypted, we can’t know what’s being passed?
To prove the hack, you would have to — and FBI did, in both cases — prove that the stolen data made it to the end point.
This testimony is important for more than explaining where you’d need to look to find proof of a hack (at the end points). It shows the import of understanding not just the crime scene and those end points, but the infrastructure used to control the hack and exfiltrate the data. With both the hack-and-trade conspiracy and the hack of the DNC, the FBI got forensics about the victim from the incident response contractors, but they obtained the data from these external servers directly, with warrants.
The denialists looking for proof in the DNC server were focused on just the crime scene, but not what I’ve likened to a getaway car, one to which the FBI had direct access but Crowdstrike did not.
Follow the money
Another specialized kind of fingerprint prosecutors used to prove the case against Klyushin parallels the one in the Mueller indictment (and, really, virtually all hacking cases these days): the cryptocurrency trail. As the Mueller indictment explained, the hackers who targeted the DNC used the same cryptocurrency account to pay for different parts of their infrastructure, thereby showing they were all related.
The funds used to pay for the dcleaks.com domain originated from an account at an online cryptocurrency service that the Conspirators also used to fund the lease of a virtual private server registered with the operational email account dirbinsaabol@mail.com. The dirbinsaabol email account was also used to register the john356gh URL-shortening account used by LUKASHEV to spearphish the Clinton Campaign chairman and other campaign-related individuals.
[snip]
For example, between on or about March 14, 2016 and April 28, 2016, the Conspirators used the same pool of bitcoin funds to purchase a virtual private network (“VPN”) account and to lease a server in Malaysia. In or around June 2016, the Conspirators used the Malaysian server to host the dcleaks.com website. On or about July 6, 2016, the Conspirators used the VPN to log into the @Guccifer_2 Twitter account. The Conspirators opened that VPN account from the same server that was also used to register malicious domains for the hacking of the DCCC and DNC networks.
By following the money, prosecutors were able to show the jury how these pieces of infrastructure fit together.
In the case of the hack-and-trade, the conspirators did nothing fancy to launder the cryptocurrency used in the operation. The servers obtained in the name of Andrea Neumann were paid using three successive cryptocurrency accounts, each with different names but accessed from the same IP address. The third name was Wan Connie. An interlocked Wan Connie email account had been accessed from M-13’s IP address. So while the cryptocurrency itself couldn’t tie the conspirators to the hack, the interlocked infrastructure did.
The conspiracy
To prove the hack, prosecutors at trial showed how the FBI had used evidence from the crime scene, the “getaway” car, the money trail, and evidence obtained at the end point from iCloud accounts to tie the hack back to Ermakov personally and M-13 more generally. The biggest smoking gun came from matching the IP addresses to which Ermakov got his iTunes updates to the infrastructure used in the hack (or, in the case of the May 9, 2018 thefts, directly to someone exploiting Julie Soma’s stolen credentials.
 All that was left in the Klyushin case was proving the conspiracy, showing that Klyushin and others had used this stolen information to make millions by trading in advance of earnings announcements. This would be the functional equivalent of tying the records stolen from Democrats (and some Republicans) to their release via Guccifer 2.0, dcleaks, and WikiLeaks.
All that was left in the Klyushin case was proving the conspiracy, showing that Klyushin and others had used this stolen information to make millions by trading in advance of earnings announcements. This would be the functional equivalent of tying the records stolen from Democrats (and some Republicans) to their release via Guccifer 2.0, dcleaks, and WikiLeaks.
At Klyushin’s trial, the government proved the conspiracy via two means: an SEC analyst presented a bunch of coma-inducing analysis showing how the trades attributed to online brokerage accounts that Klyushin and others had in their own names lined up with the thefts. The analyst explained that odds of seeing those trading patterns would be virtually impossible.
More spectacularly, prosecutors introduced Klyushin’s role with a bunch of pictures establishing that he was “besties” with Ermakov (and, eventually, that there were unencrypted and encrypted communications, along with a picture of Klyushin’s yacht, sent via Ermkaov to two guys in St. Petersburg who didn’t work for M-13 but who were making the same pattern of trades); I looked at some of that evidence here. One picture found in Klyushin’s account showed Ermakov, crashed on a chair, wearing an M-13 sticker, taken in the same period as some of the logs provided by Kroll showed hacking activity. About the only thing the FBI found in Ermakov’s iCloud account was the online brokerage account used to execute the insider trading, in Klyushin’s name, but that tied him to the trading side of the conspiracy.
As their trades began to attract attention, Ermakov and another M-13 employee attempted to craft cover stories, evidence of which prosecutors found via Apple. Prosecutors even introduced Threema chats in which Ermakov told Klyushin, his boss, not to share details about their trading clients or he might end up a defendant in a trial.
He did.
And at that trial, prosecutors were able to prove a hacking conspiracy against Klyushin using evidence and victim testimony from the crime scene, but also from other data readily available with a subpoena or warrant inside the US.
Update: Tweaked language describing secure tunnels.
The Long List of Reasons Why Potential Intimidation of Proud Boy Jurors Must Be Taken Seriously
/39 Comments/in 2016 Presidential Election, 2020 Presidential Election, January 6 Insurrection, Mueller Probe /by emptywheelEnrique Tarrio has already been investigated by a grand jury in Prettyman Courthouse for any role he had in threats to undermine a criminal prosecution.
That’s important background to Brandi’s report, at the end of her update on the Proud Boys trial, of how much of last week the trial was halted for a series of sealed hearings.
Apart from routine objections launched by the defense to even the most mundane of issues and separate from the unending series of motions for mistrial, last week featured a new and unwelcome variable: the sealed hearing.
A sealed hearing, or a hearing closed to the public and press, is typically held when sensitive or classified matters are being discussed by the parties. Trial days were stopped and started three times last week for sealed hearings that stretched for more than an hour. A press coalition moved to unseal proceedings on at least one of those days but was promptly denied by Judge Kelly for reasons he failed to describe on the record.
Though the exact reason was not disclosed by the court (nor would one expect it to be at this point), CNN reported that multiple sources said the sealed hearing was prompted after a juror raised concerns that she was being followed. Another juror has said they were “accosted” but no further details were available.
As CNN reported, a juror had become worried that someone was following her.
A juror told the court an individual came up to her outside of a Washington, DC, metro station and asked if she was a juror, multiple sources told CNN. The juror told court staff she had seen the same individual on several occasions and thought they might be following her.
Some jurors appear to be split on their views of the incidents, people familiar said. One juror told the judge he thought it was possible the interactions were random and it might have been someone experiencing homelessness in the area.
[snip]
When other jurors found out about the incident, they also began to look out for the individual and had taken at least one picture of the person, according to someone familiar with the matter.
Other jurors also told the court in sealed hearings this week that they had been “accosted,” one source told CNN, though it’s unclear to what extent.
But that report and some of the discussions I’ve seen elsewhere didn’t describe the list of reasons why such threats should be taken seriously.
First, there’s the fact that defendant Enrique Tarrio has already been investigated in this courthouse for his potential role in a threat against a judge. In 2019, Amy Berman Jackson put Roger Stone under oath and asked how he came to post an Instagram post of her with crosshairs on it. He blamed the “volunteers” who had made the meme — one of whom, he named, was Tarrio.
Amy Berman Jackson. How was the image conveyed to you by the person who selected it?
Stone. It was emailed to me or text-messaged to me. I’m not certain.
Q. Who sent the email?
A. I would have to go back and look. I don’t recognize. I don’t know. Somebody else uses my —
THE COURT: How big is your staff, Mr. Stone?
THE DEFENDANT: I don’t have a staff, Your Honor. I have a few volunteers. I also — others use my phone, so I’m not the only one texting, because it is my account and, therefore, it’s registered to me. So I’m uncertain how I got the image. I think it is conceivable that it was selected on my phone. I believe that is the case, but I’m uncertain.
THE COURT: So individuals, whom you cannot identify, provide you with material to be posted on your personal Instagram account and you post it, even if you don’t know who it came from?
THE DEFENDANT: Everybody who works for me is a volunteer. My phone is used by numerous people because it can only be posted to the person to whom it is registered.
[snip]
[AUSA] Jonathan Kravis. What are the names of the five or six volunteers that you’re referring to?
Stone. I would — Jacob Engles, Enrique Tarrio. I would have to go back and look
As CNN itself later reported, those whom Stone named were subpoenaed to testify about whether Stone had paid them to make threatening memes targeting his judge.
Tarrio, the leader of the Proud Boys, had been helping him with his social media, Stone said under oath, as had the Proud Boys’ Florida chapter founder Tyler Ziolkowski, who went by Tyler Whyte at the time; Jacob Engels, a Proud Boys associate who is close to Stone and identifies himself as a journalist in Florida; and another Florida man named Rey Perez, whose name is spelled Raymond Peres in the court transcript.
A few days later, federal authorities tracked down the men and gave them subpoenas to testify to a grand jury, according to Ziolkowski, who was one of the witnesses.
Ziolkowski and the others flew to DC in the weeks afterwards to testify.
“They asked me about if I had anything to do about posting that. They were asking me if Stone has ever paid me, what he’s ever paid me for,” Ziolkowski told CNN this week. When he first received the subpoena, the authorities wouldn’t tell Ziolkowski what was being investigated, but a prosecutor later told him “they were investigating the picture and if he had paid anybody,” Ziolkowski said. He says he told the grand jury Stone never paid him, and that he hadn’t posted the photo.
So four years ago, in this very courthouse, Tarrio or his associates were questioned about the circumstances of any participation they had in threatening a judge.
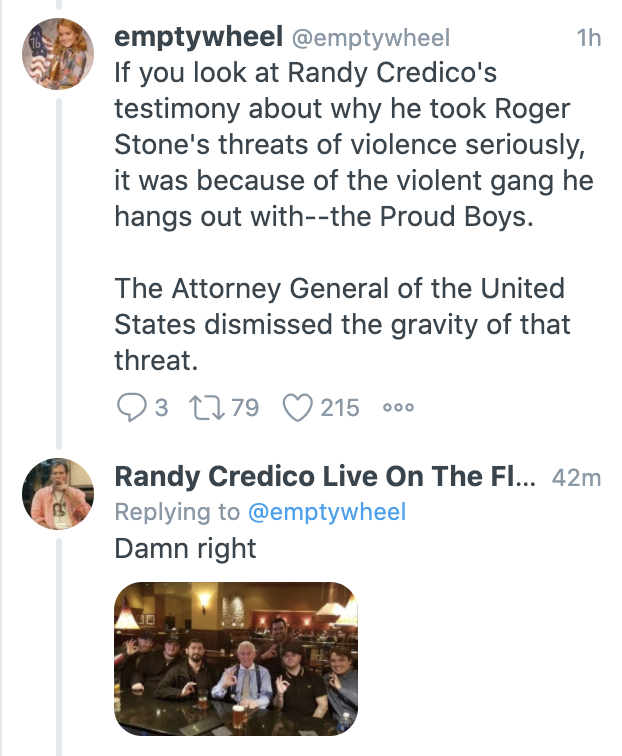
That wasn’t the only role the Proud Boys had in Stone’s witness tampering in that case. The first contact that Randy Credico had with FBI agents investigating 2016 was not the highly publicized grand jury testimony to which he brought his comfort dog Bianca. It was a Duty to Warn contact earlier that summer after the FBI had identified credible threats against him. Those credible threats came from the gangs, including the Proud Boys, that Stone hung out with.
In entirely unrelated news, Credico posted pictures showing him in Moscow last week.
It didn’t end with Stone’s guilty verdict, either. After the verdict, Stone associates got leaked copies of the jury questionnaires. Mike Cernovich started hunting down details on the jurors to retroactively cast doubt on the judgment, and Trump joined in the effort to create a mob. In the wake of those efforts, the jurors expressed fear and some regret at having served.
ALL 12 OF the jurors in the Roger Stone case have expressed fear in court filings on Wednesday. They worry they will continue to be harassed and they fear for the safety of themselves and their families if their identities are revealed.
According to The National Law Journal, jurors cited tweets from President Trump and remarks from conspiracy theorist Alex Jones as the reason “the threats to the jurors’ safety and privacy persist” after the trial ended in November.
One juror wrote, “I try to stay away from danger, but now it seems like the danger is coming to me.”
The jurors are looking to thwart the legal efforts of right-wing conspiracy theorist Mike Cernovich, who is attempting to make public the pretrial questionnaires the jurors filled out. Those questionnaires include jurors’ private information and employment history. The supposed aim of the petition to release the questionnaires is to vet them for bias in hopes of getting a new trial for Stone.
Another juror wrote, “Given the current climate of polarization and harassment, I do not want to draw any attention to myself, my family, or my employer in any way, shape, or form. It is intimidating when the president of the United States attacks the foreperson of a jury by name.”
“I am frightened that someone could harm my family simply because I was summoned and then chosen to serve on the jury,” another juror wrote.
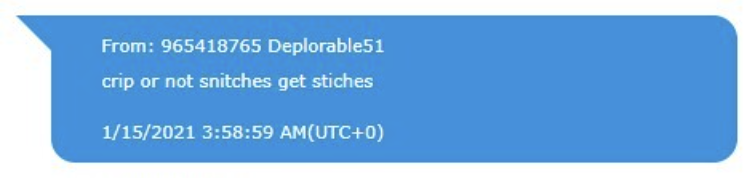
The efforts to intimidate have continued to this case. During a period when Zach Rehl was reportedly considering a plea, Tarrio sent messages to other Proud Boys about remaining loyal.
“The bigger problem with that is the guys that are in prison right now are holding on to hope that everybody is f—ing staying put because they didn’t do anything wrong,” Tarrio said. “The moment that they think one of the guys flipped, it throws everything off and it makes everybody turn on each other, and that’s what we are trying to f—ing avoid.”
Asked about the audio message, Tarrio told Reuters he was simply trying to stop members from speculating that anyone had decided to help prosecutors who are examining the deadly insurrection. “What I was trying to avoid is them turning against each other because of media stories,” he said.
Trial testimony showed that witnesses for the defense — in this case Fernando Alonzo — made threatening comments about Eddie Block for posting the video of the Proud Boys he shot on January 6. [Warning: he used an ableist slur against Block, who relies on a mobility scooter.]
Witnesses for other January 6 defendant have been harassed, as when one January 6 participant confronted Sergeant Aquilino Gonell during the trial of Kyle Fitzsimons on assault charges.
[January 6 participant Tommy] Tatum also tried to confront another officer, this one with the Capitol Police, in a courthouse elevator on Wednesday. He recorded and posted clips of both exchanges with the officers and identified himself outside the courthouse.
U.S. Capitol Police Sgt. Aquilino Gonell, who is also testifying in the trial, said that Tatum told him that he should be ashamed of himself in an exchange near the bathroom inside the courthouse on Wednesday. Shortly after, Tatum got into an expletive-laden confrontation with David Laufman, an attorney for Gonell, after he tried to get into an elevator with Gonell, Laufman and an NBC News reporter.
NBC News separately heard Tatum make negative comments inside the courthouse about how he believed Gonell was acting. Outside the courthouse, Tatum recorded himself accusing Gonell of committing perjury.
The confrontations with Gonell came before the conclusion of his testimony in the case against Fitzsimons, who is accused of assaulting Gonell inside the tunnel. Gonell’s cross-examination by Fitzsimons’ federal public defender will continue on Thursday morning.
“For Sgt. Gonell to be accosted like that, within the courthouse and while he remains a live witness at trial, was outrageous and amounts to witness intimidation that promptly should be addressed by the court as well as the FBI and the Department of Justice,” Laufman, who is representing Gonell pro bono, told NBC News on Wednesday night.
Finally, there are other key players in January 6 — most notably former Green Beret, Ivan Raiklin, who played a key role in Operation Pence Card, the effort to pressure Pence to overturn the election — who lurk around all events associated with January 6. Fellow Proud Boy Gabriel Garcia, in a recent bid to avoid pre-trial release sanctions for going to CPAC after he told Judge Amy Berman Jackson he was coming to DC to observe — among other things — the Proud Boys trial, claimed that he hung out with Raiklin at CPAC to formulate his defense.
While at CPAC, Mr. Garcia was working on his defense to these charges. Indeed, he asked Congressman M. Gaetz, who is from Mr. Garcia’s home state, how and when could his defense team access the 40,000 hours of unreleased video Capitol Police have. Also, he and his counsel met, and conferred extensively with, attorney Ivan Raiklin, whom they may retain for assistance and trial preparation. Mr. Raiklin had spoken to Mr. Garcia on March 2 at CPAC, and he told Mr. Garcia to return the next day with his counsel to discuss at length defense strategies, which they did.
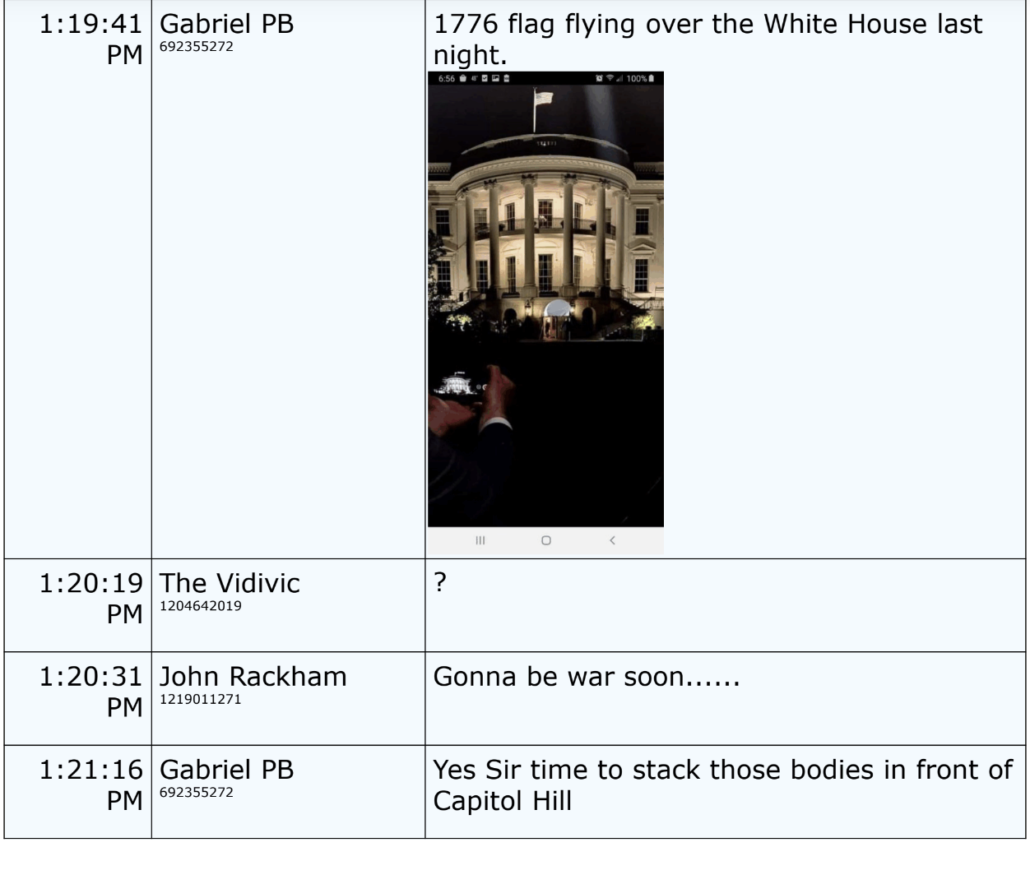
Former Army Captain Garcia is one of the Proud Boys who, in exhibits submitted at trial (here, Gabriel PB), was issuing the most chilling threats in advance of January 6.
None of this makes things easier for Tim Kelly, as he tries to sustain this jury long enough to get through deliberations. It’s not yet clear whether the jurors, watching testimony about the extent to which Proud Boys using intimidation to protect their organization, are seeing shadows, or whether there’s a real attempt to intimidate jurors before they start deliberating.
But given the history of individuals directly associated with the defendants, the threat is not an idle one.
Donald Trump’s Dumbass Russia Binder
/54 Comments/in 2016 Presidential Election, 2020 Presidential Election, emptywheel, Leak Investigations, Mueller Probe /by emptywheelThere is some tie between Donald Trump’s effort — as one of his last acts as President — to declassify a binder of materials from the Crossfire Hurricane investigation and his hoarding of still-classified documents that could get him charged under the Espionage Act.
It’s not yet clear what that tie is, though.
On May 5 of last year, Kash Patel offered the declassification effort as an alibi, claiming Trump had declassified a bunch of materials, including not just the Crossfire Hurricane materials, but everything else discovered in boxes returned to NARA in January 2022. Kash’s claim would be included in the search affidavit for Mar-a-Lago and ultimately lead to his compelled testimony in the investigation.
Last fall, at a time when Alex Cannon and Eric Herschmann would have been under some scrutiny for their role in Stefan Passantino’s dubious legal advice to Cassidy Hutchinson, Maggie Haberman told a story in which the Trump lawyers heroically warned Trump about the risks of holding classified documents. That story claimed Trump had offered to swap the documents he did have for the Russian-related documents the former President believed NARA had.
It was around that same time that Mr. Trump floated the idea of offering the deal to return the boxes in exchange for documents he believed would expose the Russia investigation as a “hoax” cooked up by the F.B.I. Mr. Trump did not appear to know specifically what he thought the archives had — only that there were items he wanted.
Mr. Trump’s aides — recognizing that such a swap would be a non-starter since the government had a clear right to the material Mr. Trump had taken from the White House and the Russia-related documents held by the archives remained marked as classified — never acted on the idea.
The story doesn’t mention Cannon’s role in a fall 2021 inquiry to NARA about the Russian documents. Nor does it say that National Archives General Counsel Gary Stern told Cannon and Justin Clark that NARA had 2,700 undifferentiated documents, but that the binder Trump wanted declassified had been rendered a Federal Record when it got sent back to DOJ.
That’s what NARA told John Solomon on June 23, 2022 — that Trump’s lawyers had requested the binder in fall 2021 — in Stern’s first explanation for why NARA didn’t have the binder.
John, fyi, last fall Justin Clark, another PRA representative of President Trump, also asked us for a copy of this declassified binder. Upon conducting a search, we learned that the binder had been returned to the Department of Justice on January 20, 2021, per the attached memo from Chief of Staff Mark Meadows to the Attorney General, titled “Privacy Act Review of Certain Declassified Materials Related to the FBI’s Crossfire Hurricane Investigation.”
Accordingly, we do not have the binder containing the declassified records. As we explained to Justin, what we were able to locate is a box that contains roughly 2700 undifferentiated pages of documents with varying types of classification and declassification markings, but we could not be certain of the classification status of any of the information in the box. We are therefore obligated under Executive Order 13526 to treat the contents of the box as classified at the TS/SCI level.
Then on August 9 and again on August 10 last year, immediately following the search on Mar-a-Lago, Solomon asked for all correspondence between Cannon and NARA up until days before the search.
Gary, John: My research indicates there may be a new wrinkle to the Russian declassified documents. As part of my authorized access, I would like to see all correspondence between NARA and attorney Alex Cannon between December 2020 and July 31, 2022. I think the information will have significant value to the public regarding current events. Can that be arranged?
[snip]
Checking back on this. It’s time sensitive from a news perspective. Can you accommodate?
Stern, no dummy, likely recognized that this information would not just have news value, but would also have value to those under criminal investigation; he responded with lawyerly caution. As NARA representative for Trump, he explained, Solomon was only entitled to access Presidential records — those that predate January 20, 2021 — and communications between Cannon and NARA post-dated all that. But, Stern helpfully noted, Cannon was cc’ed on the request for the Russian binder.
It’s important to clarify that, as a designated PRA representative of President Trump, you may receive access to the Presidential records of the Trump Administration that have been transferred to NARA, which date from January 20, 2017 to January 20, 2021.
Alex Cannon has represented President Trump on PRA matters (along with Justin Clark) only since the summer of 2021, principally with respect to the notification and review process in response to special access requests. Accordingly, there would not be any Trump Presidential records between NARA and Alex Cannon.
FYI, in my June 23 email to you (which is below within this email thread), I noted that “last fall Justin Clark, another PRA representative of President Trump, also asked us for a copy of this declassified binder.” Alex Cannon was cc’d on Justin’s request and our response. I am not aware of any other communications that would exist between NARA and Alex about this matter. [my emphasis]
That would be the only communications “about this matter,” seemingly distinguishing the Russian binder from the missing Presidential records.
At the time Maggie was distracting the chattering classes with the swap story, ABC had a very thorough story that revealed some of what Stern had explained to Solomon last year. That story suggests the month-long focus on the Russian binder had led overall compliance with the Presidential Records Act to be lacking. As Hutchinson tells it, it was worse, with 10 to 15 NSC staffers madly copying classified documents in the last days Trump was in office, with two sets of four copies — one still classified, one less sensitive — circulating to who knows where.
The tie between the Russian documents and the documents Trump stole may be no more than the alibi Kash tried to use them as, an attempt to claim that the limited declassification was instead a blanket effort. Perhaps it was also a failed effort to use Kash and Solomon as moles to figure out what NARA got back. Or perhaps some of these materials madly copied at the last moment were among the classified documents Trump took with him. Perhaps some of those materials were among the still-classified documents Trump took and hoarded in a storage closet with a shitty lock.
But that tie is one of the reasons I read the version of the binder released earlier this year in response to a Judicial Watch FOIA closely (release 1, release 2).
That is one dumbass binder. If you’re going to expose yourself and your assistants to Espionage Act prosecution, this is one dumbass document to do so over.
Having reviewed it — even with great familiarity with the unending ability of certain frothers to get ginned up over these things — I cannot believe how many people remain obsessed about this document.
The document, as released to Judicial Watch, is little more than a re-release of a bunch of files that have already been released. Perhaps the only released documents I hadn’t read closely before were memorializations that Andy McCabe wrote of conversations he had in the wake of Jim Comey’s firing with and about Trump, including the one that described Rod Rosenstein offering to wear a wire to meetings at the White House.
And because DOJ subjected the documents to a real Privacy Act review, unlike declassifications effectuated by Director of National Intelligence John Ratcliffe when Kash babysat him as his Chief of Staff, a number of the documents actually are more redacted than previous versions, something that will no doubt be a topic of exciting litigation going forward.
Mark Meadows ordered DOJ to do a Privacy Act review and as a result great swaths of documents were withheld, page after page of b6/b7C exemptions as well as b7D ones to shield confidential information.
Here’s what got released to Judicial Watch, along with links to the previous releases of the documents:
- Request 1: Pending with DOJ
- Tab 2: Christopher Steele 302 [25 withheld]
- Communications about the Steele dossier
- CHS reporting (probably Steele)
- [75 pages withheld]
- CHS reporting (probably Stefan Halper)
- CHS
- Andrew McCabe, Jim Comey, Peter Strzok, Lisa Page, and Bill Priestap text and Lync messages, all previously released to Congress
- Request 5: Pending with DOJ
- Request 6: Pending with DOJ
- Flynn 302s (but not equally damning ones from later in 2017)
- [10 pages withheld]
- Andrew McCabe memorialization of conversations with Trump
- [8 pages withheld]
- Bruce Ohr 302s [all but one previously released — also to Judicial Watch! — here]
- Memorialization of Flynn briefing [less redacted version here]
- Request 14 (for Sussmann or other Perkins Coie lawyers): No collection pertaining to Crossfire Hurricane
- Mifsud 302 [previously released here]
- Request 17 (meeting with Ohr and Weissmann): Pending with DOJ
- [95 pages withheld]
- Mike Rogers 302 [previously released here]
- June 29, 2017 Carter Page application [previously released here]
The Bruce Ohr 302s are the only documents that include much newly released materials, mostly reflecting Igor Danchenko’s subsequent public identification. Both the candidate briefing and the Carter Page FISA application include significantly more redaction (and those are not the only interesting new redactions); given the redactions, it doesn’t look like Trump contemplated disseminating any Page material that was sequestered by the FISA Court, which would have been legally problematic no matter what Trump ordered, but references to the sequestration were all redacted.
As noted above as Requests 1, 5, 6, 14, and 17, there were five things Trump asked for that were still pending at DOJ when Trump left office. Two of those are identified: A request for materials on Perkins Coie lawyers, which (DOJ informed Trump) had no tie to Crossfire Hurricane, and a request for details on an August 2016 meeting involving Bruce Ohr, Andrew Weissmann, and one other person “concerning Russia or Trump.”
There were a number of communications between Ohr, Weissmann, and others later in 2016, including communications potentially relating to an effort to flip Dmitry Firtash, as well as October 2016 communications between Ohr and McCabe. But the jumbled timeline of Ohr’s communications has often been used to insinuate that the Crossfire Hurricane team learned of the Steele allegations earlier in the investigation than the September 19 that DOJ IG reflects. In any case, some of these meetings likely touched on Oleg Deripaska and some might touch on the suspected Egyptian donation Trump used to stay in the race past September 2016, not the dossier.
Between other then-pending requests and big chunks of withheld information (I’ve noted the biggest chunks above, but it would be around 300 pages total), there are things I would have expected to see in this binder that are not there. For example, almost none of the material released as part of DOJ’s attempt to undermine the Flynn investigation (links to which are in this post) is included here. Most of that stuff constitutes information that would never normally be released. It was egregiously misrepresented by Barr’s DOJ. Some of the files were altered. If these were requested, I can think of a number of reasons it would take DOJ a while to provide the materials. Even still, though, the materials didn’t persuade Emmet Sullivan to overturn Flynn’s prosecution, and documents left out of this bunch — such as Flynn’s later 302s, including some where he obviously told the same lies he had told in January 2017, would easily rebut any claims Trump might offer with the Flynn documents.
The documentation showing Strzok learning of a Russian intelligence product claiming not very damning things about Hillary is not in here. That, too, is something that would never have been released with a normal DNI not being led around by Kash Patel and it’s one that would take DOJ a good deal of time to clear. But as I laid out here, the report came after Trump had already demonstrably started pursuing files stolen by Russia. By the time Hillary purportedly decided to call out Trump for encouraging the Russian hack, Trump was encouraging the Russian hack.
Given that Mike Rogers’ 302 from the Mueller investigation is included here, you’d expect those of Trump’s other top intelligence officials to be included as well. Dan Coats and Mike Pompeo were interviewed in the weeks after Rogers. Coats’ aide Mike Dempsey and NSA Deputy Director Rick Ledgett were also interviewed about Trump’s March 2017 effort to get the IC to deny he had a role in Russian interference, as was Trump’s one-time briefer Edward Gistaro (Gistaro was interviewed a second time in 2018, in an interview treated as TS/SCI, which likely pertained to his involvement in briefing at Mar-a-Lago during the transition). Details of these interviews show up in the Mueller Report, and his request only helps to make Trump look more guilty.
It doesn’t include materials released as part of the failed Sussmann and Danchenko prosecutions. But like Barr’s effort to overturn the Flynn prosecution, none of that evidence sustained Trump’s conspiracy theories either. Indeed, during a bench conference in the Danchenko trial, Durham fought hard to keep the substance of the discussions — ostensibly about energy investments — between Sergei Millian and George Papadopoulos starting in July 2016 out of the trial because, “it certainly sounds creepy.” The Sussmann trial showed how justified people were in wondering about Trump’s Russia ties in the wake of his “Russia are you listening” comment. It provided a glimpse of how time-consuming being a victim of a nation-state hack had been for Hillary in 2016. Durham even demonstrated that FBI badly screwed up the Alfa Bank investigation. When subjected to the rules of evidence, none of Trump’s hoax claims hold up.
The point is, nothing in this binder — particularly as released — supports Trump’s claims that the investigation into him wasn’t independently predicated and didn’t lead to really damning information implicating at least five of his top aides and his own son.
Trump keeps trying to collect some set of evidence that will make go away the far more damning ties to Russia that his National Security Advisor, his Coffee Boy, his personal lawyer, his campaign manager, and his rat-fucker all lied to hide. And in this case, it may have led Trump to do something far dumber, to defy a subpoena and hoard highly classified documents.
Which possibility only makes the dumbass Russia binder even more of a dumbass Russian binder.
“That’s How … You End Up as a Defendant in a Court Room:” Some Days in the Life of a Named-and-Shamed Former GRU Hacker, Ivan Ermakov
/5 Comments/in 2016 Presidential Election, emptywheel, Mueller Probe, Russian hacks /by emptywheelIn early 2018, Ivan [Y]Ermakov,* one of the hackers alleged to have stolen John Podesta’s emails two years earlier, was living it up.
For his April 10 birthday that year, he went on a stunning heli-ski trip with his future co-conspirator, Vladislav Klyushin (Ermakov is on the left in this picture, Klyushin, on the right and in the Featured Image picture).
In summer 2018, they were enjoying the Sochi World Cup together, too.
Just days after this trip to Sochi, however, on July 13, 2018, Robert Mueller would indict Ermakov, along with eleven of his former GRU colleagues, for hacking the DNC, DCCC, Hillary Clinton, election vendors, and registration websites, as well as orchestrating the release of the stolen files.
By the time of that first indictment against him — the first of three known indictments against the Russian hacker so far — Ermakov had already made one of the fatal slip-ups that would form part of the proof against Klyushin at trial, this time for a hack-and-trade scam. On May 9, 2018, Yermakov received three updates from his Apple iTunes account to the IP address 119.204.194.11. Just four minutes later, someone using that IP address downloaded an SEC filing using credentials stolen from a Donnelly Financial employee named Julie Soma. That download occurred hours before the report would be publicly filed with the SEC, one of dozens of such thefts of SEC filings that formed the basis of the hacking and securities fraud charges against the men.
So months before Mueller’s indictment alerted Ermakov that the FBI had discovered who he was and that they believed he was one of the hackers behind the 2016 hack, he had already left proof in US-based servers that would tie to him to a follow-up crime, the hack-and-insider trading conspiracy for which Klyushin was convicted in February.
Klyushin has challenged the verdict, largely based on a technical challenge to the venue of the charges in Massachusetts.
Per trial testimony, Ermakov left those tell-tale forensic tracks four months before Klyushin would first get involved in the hack-and-trade scheme, in August 2018. The scheme was doomed from the start — at least, it would be doomed if any of the identified co-conspirators traveled to a jurisdiction that would extradite to the US, as Klyushin did in March 2021.
In fact, there’s something curious about that.
One thing submitted as evidence at trial was a picture of a May 22, 2017 Reuters article reporting the US sentence for Ukrainian hacker Vadym Iermolovych, one of ten people prosecuted for a hack-and-trade conspiracy similar to the one for which Klyushin was convicted.
According to the FBI agent who introduced the exhibit, the picture itself was taken in August 2018. Someone printed out the article and packaged it up in a plastic folder over a year after the fact. That suggests Klyushin was in discussion with a very well-connected friend about the possibility of such charges in the same month that Klyushin first got involved in the scheme.
The possibility of prosecution hung over the conspiracy from the start.
Thanks to Klyushin’s promiscuous storage of damning evidence in his iCloud account, from which many of the pictures and chats in this post were obtained by the FBI, the Klyushin case offers an unprecedented public glimpse into the effect that US indictments against nation-state hackers like Ermakov might have on one of the target’s lives. In Ermakov’s case, it didn’t stop him from hacking US targets. Indeed, it’s possible that others used the indictments to pressure Ermakov to use his hacking skills for them.
Since 2014, DOJ has been indicting nation-state hackers in what have always been assumed to be name-and-shame documents, indictments that would never lead to trial. Indeed, that’s what the two earlier indictments of Ermakov have always been assumed to be: a public accusation that would never lead to Ermakov’s imprisonment. The wisdom of indicting nation-state hackers has never been obvious. Yevgeniy Prigozhin’s exploitation of his own name-and-shame indictment has revealed the potential perils of the policy. And Russian denialists brush off the July 2018 indictment charging Ermakov and others with the election year hack (as Matt Taibbi did in his recent congressional testimony), arguing that since the indictment will never be tested at trial, it could be mere government propaganda.
At least in the case of the 2016 Russian operation, the indictment has done little to persuade denialists, who simply refuse to read about the many places where the hackers left evidence.
In a follow-up, I’ll show how DOJ proved their case against Klyushin using the same kind of evidence they used in the earlier indictments against Ermakov and his colleagues, largely metadata and content obtained from US-based and a few foreign servers. DOJ may never get a chance to prove the first two indictments against Ermakov, but using the same investigative techniques, they did prove the case against Ermakov’s co-conspirator, Klyushin.
This case, where a sealed complaint ultimately led to the trial of one co-conspirator of a hacker previously charged, also provides a glimpse of what happened after one nation-state hacker got name-and-shamed in the US.
It’s not clear from the trial record when Ermakov left the GRU or who his formal employer was before he joined Klyushin’s M-13, an information services company with ties to Putin’s office that offered, among its services, pen testing.
The FBI found a contact card for Igor Sladkov, with whom Ermakov may have started the hack-and-trade scheme at least as early as October 2017, in Ermakov’s own iCloud account, one of the only interesting pieces of evidence they found there. It was dated November 16, 2016, just over a week after Donald Trump got elected with Ermakov’s help. Sladkov — whose iCloud OpSec was just as shoddy as Klyushin’s — had a bunch of photos of Ermakov in his iCloud account, including the hacker’s passport, a 2016 picture of Ermakov sitting before an enormous plate of some animal flesh, and a picture from Ermakov’s 2018 ski trip, as well as a picture of Klyushin’s yacht that Ermakov had shared.
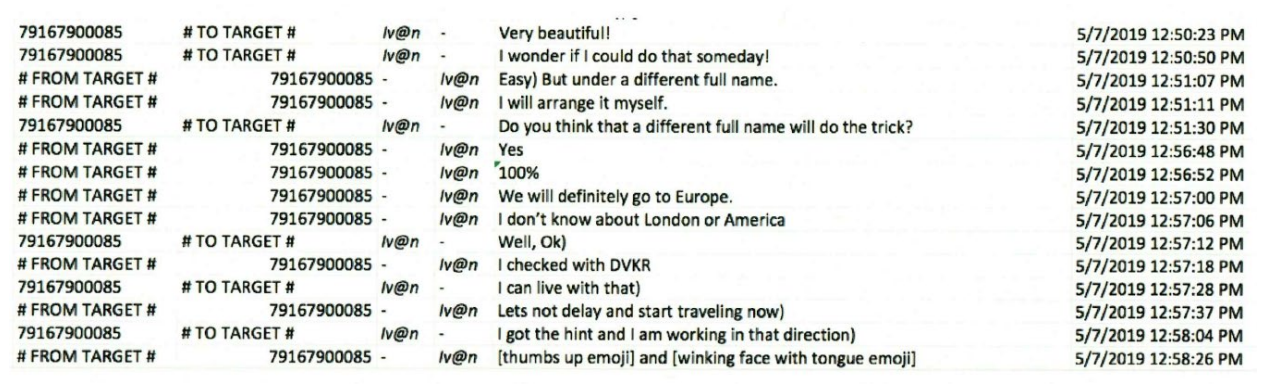
Before trial, Klyushin’s team argued that Ermakov never worked for Klyushin’s company, bolstering the claim with a chat from May 2019 in which Ermakov bitched about his job to Klyushin and a certificate from the Russian tax service claiming that [Y]Ermakov never worked at M-13.
But days after that chat, per another pre-trial filing, Ermakov spoke longingly of being able to travel like Klyushin could. Klyushin responded that he would get Ermakov new identity papers so the two could travel to Europe together, but not — Klyushin conceded — London or America. Klyushin seemingly used that discussion as background to press Ermakov to get back to work, with the implication being he should get back to the hack-and-trade scheme.
That is, Ermakov appears to have included Klyushin in the hack-and-trade scheme while still working for someone else. And Klyushin seems to have used his promise to help Ermakov mitigate the risks created by those earlier indictments to pressure Ermakov to keep hacking. If that’s right, the vulnerability created by the earlier indictments gave Klyushin leverage to get Ermakov to keep hacking.
But Ermakov did eventually join M-13, at least informally. The government introduced an M-13 employee list reflecting Ermakov’s participation in specific project at trial. And they submitted a picture, from December 2019, showing Ermakov with an M-13 sticker, within days of the time when a staging server similar to the one used in the 2016 hack of the Democrats was set up.
Klyushin may have even incorporated Sladkov into M-13. The FBI found a proposal for a data analysis service, dated September 4, 2019, which M-13 would introduce on October 28, 2020, as well as encrypted communications from an M-13 chat application, in Sladkov’s iCloud account.
Klyushin fought hard to exclude one of the most telling pieces of evidence that the hacking scheme came to be tied to M-13 — the four Porsches that, Klyushin bragged to an investor, he had bought for himself, Ermakov, and one other co-conspirator with the proceeds of the insider trading.
But this currency — expensive gifts — seems to have been at least part of the way Erkamov was compensated for his role in the scheme.
Ermakov did not engage in any trading himself. Instead, two men in St. Petersburg, two associated with M-13 (including Klyushin himself), and three clients of M-13, profited off documents [Y]Ermakov seems to have stolen.
But in addition to the Porsche, on August 17, 2020, ten days before the delivery of the Porsches, Ermakov took possession of a Moscow house worth millions, the loan agreement for which Klyushin reportedly ripped up. Months earlier, Klyushin had tied paying for the house with continued hacking — which, Klyushin joked, amounted to just turning on the computer and thinking about making money.
Ermakov was effectively printing money for Klyushin, and his reward was that house.
In September 2020, the hack-and-trade scheme would be shut down for good.
Throughout the time it was going, however, those co-conspirators knew of the indictment against Ermakov. Sladkov downloaded Ermakov’s wanted poster from the FBI website on October 5, 2018, just a day after Ermakov was charged in the 2016 hack-and-leak of anti-doping agencies while Ermakov was still a GRU officer.
And on October 4, 2020, Klyushin took a screencap of Ermakov’s wanted poster from the FBI website.
By the time Klyushin took this screencap, the victim filing agencies had finally shut down Ermakov’s access to the site, after eight months of trying. Perhaps Klyushin was contemplating what that would mean or how it had happened? According to trial evidence, DOJ didn’t identify the hack-and-trade scheme by tracking what Ermakov was doing. Rather, the investigation started when the SEC started tracking some large-scale trading by a bunch of Russians together, then asked the filing agencies if they had been hacked. At least according to the public record, the involvement of Ermakov was disclosed only after working backwards from the forensic evidence. But in October 2020, Klyushin may have considered the risks of entering into a hack-and-trade scheme with a hacker whose habits were already known within the FBI.
By then it was too late. Indeed, Ermakov had already warned his boss about his shoddy OpSec. On July 18, 2019, Kluyshin asked Ermakov and the other M-13 co-conspirator Nikolai Rumiantcev how the hack-and-trade was going. He included pictures of two of the M-13 investors. In response, Ermakov warned his boss that that kind of OpSec is the kind of thing that would land him as a defendant in a courtroom.
Q. Okay, thank you. And now can we move to 3980, please. And this date is?
A. This is July 18 of 2019.
Q. Would you begin with 3980.
A. “Vladislav Klyushin: So what did we earn today?”
Q. And then there’s an attachment?
A. Correct.
Q. And then he says what?
A. Ermakov responds: “About 350 and another 350 in the mind. Sasha the most among the rest. “Klyushin: Our comrades are wondering.”
MR. FRANK: Could we stop right there, and I realize it’s hard, Ms. Lewis, because we’re in the Excel, but could you please display Exhibits 52 and Exhibit 50.
Q. Those are the attachments, Special Agent. Have you had an opportunity to review those?
A. Yes.
Q. Who’s depicted in Exhibits 52 and 50?
A. On the left, 52 is Sergey Uryadov. On the right is Boris Varshavksiy in Exhibit 50.
MR. FRANK: I offer 52 and 50. (Exhibits 50 and 52 received in evidence.)
Q. Okay. So those are the two attachments Mr. Klyushin has just transmitted in the chat?
A. Yes.
Q. Can we go back to the chat and pick up where we left off. So Mr. Klyushin says, “What did we earn today? Our comrades are wondering.” Could you continue, please, at 3987.
A. After sending those pictures we just looked at, Ermakov replies: “Vlad, you are exposing our organization. This is bad.” Nikolai Rumiantcev: Vlad, stop sending to Threema.” Klyushin replies, “So sorry.” “Ermakov: And that’s how they get you and you end up as a defendant in a courtroom.”
Q. How does Mr. Klyushin respond?
A. Klyushin responds, “Removed. Open a chat with us already. “Ermakov: Go ahead and create. It was a bad move now. “Klyushin: Sorry. Did a dumb thing. “Rumiantcev: I suggest to recreate the chat with the deletion of attachments in Threema, or switch to ours if ready. “Klyushin: I will delete this one on my end.”
Klyushin did delete this chat. Rumiantcev left it in his iCloud account, where the FBI found it.
At the time, the men appear to have been shifting their trading discussions to the encrypted M-13 chat application found in all their iCloud accounts, finally taking measures to cover their tracks going forward, over eighteen months into the hack-and-trade conspiracy. Going forward, those working with Ermakov might not exhibit the kind of abysmal OpSec that produced abundant trial evidence against his co-conspirator. Maybe they learned their lesson, and they’ll be able to exploit Ermakov’s skill more safely going forward.
It remains to be seen whether the prosecution of Klyushin, with his ties to high even higher ranking Russians, does more than hold him accountable for millions in fraudulent trades. But that may have little effect on the life of John Podesta’s suspected hacker.
* The government has used two different transliterations for [Y]Ermakov’s last name. In 2018, they used the one that aids in pronunciation. In 2021, they used the direct transliteration from the Cyrillic. Because evidence submitted at Klyushin’s trial uses the initials “IE” to refer to Ermakov, I’ll adopt that spelling here.
KT McFarland Likened Trump’s Transition Interventions to the Iran October Surprise
/30 Comments/in 2016 Presidential Election, emptywheel, Mueller Probe /by emptywheelIn an FBI interview on September 14, 2017, KT McFarland likened Mike Flynn’s transition period interference with Obama policy to Richard Nixon’s Chennault Affair and what she called Reagan’s “purported dealings with Iran to free American hostages.”
Based on her study of prior presidential transitions, McFarland believed the sorts of things Flynn did were not unusual. She cited Richard Nixon’s involvement in Vietnam War peace talks and Ronald Reagan’s purported dealings with Iran to free American hostages during their transitions as precedent for proactive foreign policy engagements by an incoming administration. Most incoming administrations did similar things. No “red light” or “alarm bells” went off in her head when she head what Flynn was doing. The President-elect made his support for Israel very clear during the campaign and contrasted his position with President Obama, who he believed had not treated Israel fairly.
To be clear: She was only talking about Flynn’s request of Russia, on December 22, to help stave off a UN vote condemning Israeli illegal settlements. At that point in September 2017, she was still claiming not to remember the calls Flynn made on December 29 to undermine Obama’s sanctions on Russia itself. She wouldn’t unforget those calls until after Flynn pled guilty a month and a half later.
But to the extent that she was happy to acknowledge that Trump’s National Security Advisor — her boss — was undermining US policy, she rationalized it by comparing it to Nixon and Reagan’s efforts to undermine US policy for political gain.
Only, it wasn’t just Flynn involved in undermining Obama’s foreign policy. Records from Mueller’s investigation show the following sequence on December 22:
- 6:02AM: A “senior advisor to a Republican Senator” writes McFarland, cc’ing Flynn and others, warning that the UNSC was “voting to condemn Israeli settlements at 10a.m.” yet Obama was silent
- 8:46AM: Flynn and Kushner speak for four minutes
- 8:53AM: Flynn calls Sergei Kislyak, then calls a representative of the Egyptian government and speaks to him for four minutes
- 8:59AM Flynn speaks to Kislyak for three minutes
- Flynn had “several additional” calls with the representative of the Egyptian government
- Egypt delayed the vote
When the President’s son-in-law read a draft statement from Egypt noting that Abdel Fattah El-Sisi had spoken with Trump that day and had “agreed to lay the groundwork … to drive the establishment of a true peace between the Arabs and the Israelis,” Kushner asked whether they could alter the statement. “Can we make it clear that Al Sisi reached out to DJT so it doesn’t look like we reached out to intercede?” He then falsely claimed, on an email with others like Reince Priebus that, “This happens to be the true fact pattern and better for this to be out there.”
Only it wasn’t the true fact pattern. Flynn had reached out. Not Sisi.
Indeed, this incident was probably the start of Kushner’s Abraham Accords, which in turn probably relates to why the Saudis paid Kushner $2 billion after he left the White House.
And it wasn’t just Flynn involved. Flynn made all these calls from Mar-a-Lago. After Egypt delayed the vote, McFarland bragged that Flynn, “had worked it all day with trump from Mara lago.” [my emphasis]
Trump was involved too.
That December 22 transcript was withheld from those released in 2020. But on a later call with Kislyak — the one where he asked Kislyak to hold off on sanctions — analysts suggested “he may be using a speaker phone.” Had Flynn used a speaker phone on December 22, when he was in Mar-a-Lago with Trump, Trump would have been on that call as well.
The next day, McFarland bragged still some more. She suggested Flynn should leak to the press about,
the crucial role [he] played in working your contacts built up over the decades to get administration ambush Israel headed off. You worked the phones with Japanese Russians Egyptians Spanish etc and reversed a sure defeat for Israel by kerry/Obama/susan rice/samantha power cabal.
In 2016, McFarland wanted Flynn to get credit in the press that he had undermined US policy to help Israel. In 2017, she rationalized doing so because Nixon and Reagan had done similar things in their day.
I raise all this not just because I wonder whether Bill Barr killed the investigation into whether Egypt kept Trump’s campaign alive in September 2016 with a $10 million donation.
I raise all this because NYT, on the verge of Jimmy Carter’s death, has finally revealed who reached out to Iran to get them to hold Americans hostage longer to help Reagan win the White House.
It was former Texas Governor John Connolly.
It was 1980 and Jimmy Carter was in the White House, bedeviled by a hostage crisis in Iran that had paralyzed his presidency and hampered his effort to win a second term. Mr. Carter’s best chance for victory was to free the 52 Americans held captive before Election Day. That was something that Mr. Barnes said his mentor was determined to prevent.
His mentor was John B. Connally Jr., a titan of American politics and former Texas governor who had served three presidents and just lost his own bid for the White House. A former Democrat, Mr. Connally had sought the Republican nomination in 1980 only to be swamped by former Gov. Ronald Reagan of California. Now Mr. Connally resolved to help Mr. Reagan beat Mr. Carter and in the process, Mr. Barnes said, make his own case for becoming secretary of state or defense in a new administration.
What happened next Mr. Barnes has largely kept secret for nearly 43 years. Mr. Connally, he said, took him to one Middle Eastern capital after another that summer, meeting with a host of regional leaders to deliver a blunt message to be passed to Iran: Don’t release the hostages before the election. Mr. Reagan will win and give you a better deal.
Then shortly after returning home, Mr. Barnes said, Mr. Connally reported to William J. Casey, the chairman of Mr. Reagan’s campaign and later director of the Central Intelligence Agency, briefing him about the trip in an airport lounge.
At that moment of history, when Reagan won a victory in part thanks to Connally’s sacrifice of Americans’ freedom, KT McFarland was at the height of her credibility on foreign policy, fresh off going ABD in a PhD program. With the new Republican regime, she worked first for Texas Senator John Tower on the Senate Armed Services Committee, then for Cap Weinberger at DOD.
KT McFarland, who derives any foreign policy credibility to that moment created by an effort to harm US policy for political gain, likened what Trump did to what Reagan had done before.
Judge Unseals Details on Cooperating Witness in Douglass Mackey Case
/22 Comments/in 2016 Presidential Election, 2020 Presidential Election, January 6 Insurrection, Mueller Probe /by emptywheelThe government was just forced to reveal that it has a cooperating witness against Douglass Mackey, the far right troll who tried to help Trump win in 2016 by tricking Hillary voters into texting their vote instead of casting it legally. The cooperating witness will testify against Mackey, whose trial starts on March 16.
The documents were all made available today:
- Government motion for a protective order
- Mackey opposition
- Government reply
- Judge Garaufis order approving pseudonymous testimony but unsealing request
The charge against Mackey accuses him of conspiring with four other people. As Luke O’Brien laid out when Mackey was arrested in 2021, three of Mackey’s co-conspirators were readily identifiable.
HuffPost can report that one co-conspirator is a prominent alt-right botmaster who goes by “Microchip” and was instrumental in making pro-Trump and anti-Hillary Clinton hashtags and content go viral on Twitter during the 2016 election. A fascist accelerationist who has expressed admiration for Adolf Hitler and Nazism, Microchip claims to have been involved in the early spread of the QAnon conspiracy cult and repeatedly told this reporter that his goal was to destroy the United States.
Another of Mackey’s co-conspirators is Anthime “Baked Alaska” Gionet, a pro-Trump white nationalist who was arrested on Jan. 16 for his involvement in storming the Capitol on Jan. 6. Gionet also participated in the deadly white nationalist “Unite the Right” rally in Charlottesville, Virginia, in 2017. (A New York Times story reported Wednesday afternoon that Gionet was a co-conspirator, citing a source close to the investigation, and HuffPost can confirm that reporting based on the Twitter ID cited in the complaint.)
HuffPost was able to link the Twitter IDs in the complaint to Gionet and Microchip through previously collected Twitter data, interviews and evidence left by both extremists on other websites. In direct messages with this reporter last year, Microchip also confirmed that he was using the Twitter account associated with the user ID listed in the complaint.
The user ID for a third co-conspirator belongs to a pro-Trump far-right activist who goes by “Nia” and has a long history of spreading disinformation on Twitter. HuffPost has not yet been able to identify the fourth co-conspirator.
The fourth was not.
As the government laid out in its motion, at some point, the cooperating witness pled guilty to the same crime charged against Mackey, a violation of the Ku Klux Klan Act. Since then, he has been cooperating with the government on other investigations, presumably targeting the far right.
The CW has pleaded guilty to a violation of 18 U.S.C. § 241 and entered into a cooperation agreement with the government. The government expects that the evidence at trial will show that the CW had communications with the defendant and other relevant persons over the internet through the use of Twitter, including communications discussing the creation and dissemination of deceptive images concerning the time, place, and manner by which voters could cast a vote in the 2016 presidential election. In particular, the CW participated in direct-message groups that included the defendant and others. In all instances, the CW used an online moniker for these communications and did not reveal his or her true identity, face, or likeness to the defendant or the other participants in the groups.
The government intends at trial to introduce the CW’s communications as exhibits and to question the CW concerning them and the CW’s understanding of the purpose of the deceptive images discussing the time, place, and manner of voting, among other related online activities. The CW has advised that apart from the CW’s family, a former girlfriend. and possibly one or two former business associates, no one is aware that the CW is in fact the user of the relevant internet monikers. As far as the government is aware, the CW’s true identity has never been publicly associated with any of the online monikers used by the CW on Twitter or other social media, notwithstanding the efforts of investigative journalists who have attempted to learn the CW’s identity.
In addition, since entering into the cooperation agreement, the CW has provided assistance to the FBI in other criminal investigations beyond the scope of this case. The CW is presently involved in multiple, ongoing investigations and other activities in which he or she is using assumed internet names and “handles” that do not reveal his or her true identity. The CW has not interacted with any witness, subject, or target in these investigations and activities on a face-to-face basis, and the government has no reason to think that the CW’s true identity has been compromised as a result of this work.
The government provides no other details about the CW (though Mackey’s reply refers to him as male), but it does go out of the way to note that the person had not flipped by 2016, I guess to avoid any possibility Republicans will claim this was part of Crossfire Hurricane.
For the avoidance of doubt, the CW was not cooperating with the government at any point before or during 2016.
The government noted in its reply, the technical proficiency of those who might suspect they were being investigated is such that revealing his identity might make him the target of harassment and cyber attacks.
The fact of the CW’s cooperation is sure to be seen by many in that community as a profound betrayal, with the result that, at a minimum, online harassment is bound to follow the CW should his or her identity become a matter of public record. That harassment can have negative consequences in and of itself. In addition, to claim that intense online attacks do not endanger a person’s physical safety is to ignore the reality of our current world, as evinced in common newspaper headlines. See, e.g., Sheera Frenkel, The Storming of Capitol Hill Was Organized on Social Media, N.Y. TIMES, Jan. 6, 2021, available at https://www.nytimes.com/2021/01/06/us/politics/protesters-storm-capitol-hillbuilding.html; Eric Lipton, Man Motivated by “Pizzagate” Conspiracy Theory Arrested in Washington Gunfire, N.Y. TIMES, Dec. 5, 2016, available at https://www.nytimes.com/2016/12/05/us/pizzagate-comet-ping-pong-edgar-maddisonwelch.html. It is simply (and regrettably) a fact of the times that many acts of politically motivated violence in current society arise from campaigns of online harassment.
Beyond the risk to the CW, the potential consequences include the disruption of the CW’s ongoing work with the FBI. It is certainly true that the nature of this work is online and anonymous, but, if the CW’s name and location were to become known, the CW would become a target for all who believe that they might be under investigation (whether they are or not). Given the technical proficiency of those with whom the CW associates, it is not difficult to envision multiple scenarios in which the CW’s online work could be jeopardized by way of a cyberattack (at a minimum).
While it doesn’t say so, those two past incidences in which online trolling led to violence — January 6 and PizzaGate — are both other instances in which Mackey’s other co-conspirators and those in the same network were involved. Indeed, co-conspirator Baked Alaska is currently serving time for his role in the January 6 attack.
Unsurprisingly, the government provides no details about how long this cooperation has been going on — but it presumably started before Mackey was arrested in 2021. Which is likely to make a lot of right wingers awfully nervous.
Trophy Documents: The Entire Point Was to Make FBI Obedient
/68 Comments/in 2016 Presidential Election, 2020 Presidential Election, emptywheel, Leak Investigations, Mueller Probe /by emptywheelThose who didn’t follow John Durham’s trials closely undoubtedly missed the parade of scarred FBI personnel whose post-Crossfire Hurricane vulnerability Durham attempted to exploit to support his invented claims of a Clinton conspiracy.
Sure, lots of people wrote about Jim Baker’s inability to provide credible answers about the meeting he had with Michael Sussmann in September 2016. Fewer wrote about the credible case that Sussmann’s attorneys made that a prior Durham-led investigation into Baker — for sharing arguably classified information with a reporter in an attempt to forestall publication of a story — made Baker especially quick to cooperate with Durham in 2020. Fewer wrote about Baker’s description of the stress of Jim Jordan’s congressional witch hunts.
It sucked because the experience itself, sitting in the room being questioned the way that I was questioned, was, as a citizen of the United States, upsetting and appalling, to see members of Congress behaving the way that they were behaving. It was very upsetting to me.
[snip]
It sucked because my friends had been pilloried in public, my friends and colleagues had been pilloried in public, improperly in my view; that we were accused of being traitors and coup plotters. All of this was totally false and wrong.
Such a circus was the kind of thing that might lead someone like Baker to prefer the “order” of a prosecutor chasing conspiracy theories, someone whose memory was seared by the firing of Jim Comey.
[Sean Berkowitz]. And this is a pretty terrible experience as well. Right?
A. It’s more orderly.
Q. (Gestured with hand to ear.)
A. This is more orderly. It’s terrible but orderly.
Q. And you’re doing the best you can. Right, sir?
A. Yes, sir.
Q. But it’s hard to remember events from a long time ago, 1snre sez
A. It depends on what the event is. I remember Jim Comey being fired, for example. That’s a long time ago and I have a clear recollection of that. So it depends on what you’re talking about.
But Baker wasn’t the only one who discussed the years of scrutiny. Counterintelligence Special Agent Ryan Gaynor, who worked in DC on the Russian investigations during 2016, described how in October 2020, after he revealed to Durham’s team that he knew a DNC lawyer had brought in the Alfa Bank tip, Durham’s team told him they were no longer treating him as a witness, but as a subject of the investigation.
A. Yeah. There were two thoughts. The first one was that I felt like I had woefully ill prepared for the meeting, because I didn’t know what the meeting was honestly going to be about with this investigation.
The second thought was that I was in significant peril, and it was very concerning as a DOJ employee to be told that now the Department of Justice is interested in looking at you as a subject instead of a witness.
Sussmann lawyer Michael Bosworth got Gaynor to explain that after he told a story more to Durham’s liking, he was moved back to the status of witness.
During his testimony, Curtis Heide (who played a key role in the George Papadopoulos investigation) explained how the FBI Inspection Division investigation into Crossfire Hurricane Agents, including him, remained pending, 6 years after the events in question. He noted that, three years after the DOJ IG Report, he was still being investigated even though he, “didn’t author any of the affidavits or any of the materials related to the applications in question.”
The same was true in the Danchenko case. Brian Auten, a key intelligence analyst on Crossfire Hurricane, described how, after having met with agents from DOJ IG four times, having done a long report for FBI’s Internal Affairs Division, and having met with the Senate Judiciary Committee — all with no concerns raised about his own conduct — the first time he met with Durham’s team, he was told he was a subject of the investigation. After Auten gave testimony that confirmed Danchenko’s reliability — seriously damaging his case — Durham himself raised investigations that undermined his own witness’ testimony.
Q. Do you recall that there was a reporter that the OIG had written concerning the Carter Page FISAs?
A. Yes.
Q. And how would you characterize that report?
A. The report was quite extensive and it discussed characterizing a number of errors and omissions.
Q. And with respect to the errors and omissions, were they tick-tacky kinds of omissions or were they significant omissions and errors that had been committed?
A. I believe the OIG described them as significant.
Q. And then with respect to the investigation done by the OIG, separate and apart from that, would it be a fair statement that you and your colleagues were under investigation by the inspection division by the FBI?
A. Yes.
Q. And would it be a fair statement that your conduct in connection with that is, you, yourself, based on the investigation done by the inspection division of the FBI, have some issues, correct?
A. I — be a little bit more specific. I’m sorry. I don’t — I have issues?
Q. Isn’t it, in fact, true that you’ve been recommended for suspension as the result of the conduct?
A. It is currently under appeal.
That line of testimony immediately preceded a hilarious failed attempt from Durham to get Auten to agree that George Papadopoulos was simply a young man with no contact to Trump who was only investigated for his suspect Israeli ties, not for his Russian ties. But it was a palpable example of the way that Trump’s minions used criminalizing FBI investigations into Trump as a way to create a makebelieve world that negates real evidence of Trump’s corruption.
About the only two FBI agents who weren’t portrayed as somehow tainted by the events of 2016 in Durham’s two failed prosecutions were two agents who fucked up investigations: Scott Hellman, who correctly told a junior agent that she would face zero repercussions of she botched the Alfa Bank investigation, and Ryan James, an FBI agent who started his career in Connecticut, who nevertheless failed to pull the evidence necessary to test Sergei Millian’s claims.
Durham rewarded the incompetence that served his purpose and attempted to criminalize what he considered the wrong answers or at least to use the threat of adverse consequences to invent a false record exonerating Trump.
And Durham came in after Jim Comey, Peter Strzok, Andrew McCabe, and Bruce Ohr had already been fired, and Lisa Page, with Strzok, deliberately humiliated on a global stage serially. He came in and exploited the uncertain status — the Inspection Division review left pending while Durham worked — of everyone involved. Such efforts didn’t end with the conclusive acquittals debunking Durham’s theories of conspiracy. Since then, Jim Baker has been dragged back through the mud — publicly and in Congress — as part of Twitter Files, Chuck Grassley passed on “whistleblower” complaints about Auten identifying Russian disinformation as such, and Timothy Thibault was publicly berated because some of the same so-called whistleblowers feeding Jim Jordan shit had complained to Chuck Grassley he was discouraging GOP conspiracy theories about Hunter Biden.
It was never just Strzok and McCabe. The entire Republican Party has relentlessly focused on punishing anyone involved in the Trump investigation, using both unofficial and official channels. When Trump promised “retribution” the other day at CPAC, this kind of relentless effort to criminalize any check on Trump’s behavior is what he was talking about.
That kind of background really helps to understand the WaPo story that described Washington Field Office FBI agents quaking at the prospect of searching Donald Trump’s beach resort.
[P]rosecutors learned FBI agents were still loath to conduct a surprise search. They also heard from top FBIofficials that some agents were simply afraid: They worried takingaggressive steps investigatingTrump could blemish or even end their careers, according to somepeople with knowledge of the discussions. One official dubbed it “the hangover of Crossfire Hurricane,” a reference to the FBI investigation of Russia’s interference in the 2016 presidential election and possible connections to the Trump campaign, the people said. As president, Trump repeatedly targeted some FBI officials involved in the Russiacase.
[snip]
FBI agents on the case worried the prosecutors were being overly aggressive. They found it worrisome, too, that Bratt did not seem to think it mattered whether Trump was the official subject of the probe. They feared any of these features might not stand up to scrutiny if an inspector general or congressional committee chose to retrace the investigators’ steps, according to the people.
Since I wrote my piece wondering whether the FBI hesitation gave Trump the chance to steal 47 documents, Strzok himself, Joyce Vance, and Jennifer Rubin have weighed in.
Rubin, I think, adopts the position of someone who hasn’t followed the plight of all the people not named Strzok who were targeted for investigating Donald Trump. She attributes the reluctance to investigate Trump (and the intelligence failures leading up to January 6, which I’ll return to) to Wray.
After a debacle of this magnitude, that sort of passivity should alarm all Americans. Imagine if, after the terrorist attacks of Sept. 11, 2001, the national security community did not evaluate how it missed the telltale signs of an imminent attack. The failure of leadership in the Jan. 6 case is inexcusable. Yet Wray has never been held to account for this delinquency.
[snip]
[O]ne is left wondering why the FBI seems disinclined to stand up to right-wing authoritarian movements and figures. Whatever the reason, the pattern reveals an unmistakable lack of effective leadership. And that in turn raises the question:Why is Wray still there?
It is absolutely the case that Wray did far too little to protect FBI agents in the face of Trump’s attacks. Wray created the opportunity for pro-Trump FBI agents and Durham to criminalize investigating Trump. I think Wray attempted to avoid rocking the boat at all times, which led the FBI to fail in other areas (including the investigation of Brett Kavanaugh). Though I’m also cognizant that if Wray had been fired during the Trump administration, he might have been replaced by someone like Kash Patel, and having a Trump appointee in charge right now may provide cover for the ongoing investigations into Trump.
But you could fire Wray tomorrow and not eliminate the effects of this bureaucratic discipline, the five year process to teach everyone in the FBI that investigating Trump can only lead to career disaster, if not criminal charges.
Also under Wray, though, the Bureau had already increased its focus on domestic terrorism, with key successes both before and after January 6. Steven D’Antuono, the chief voice of reluctance to search Mar-a-Lago, presided over the really troubled but ultimately successful effort to prevent a kidnapping attempt targeting Gretchen Whitmer, a plot that arose out of anti-lockdown protests stoked by Trump (though unusually, D’Antuono let a subordinate take credit for the arrests).
I think the specific failures in advance of January 6 lay elsewhere. Wray has not done enough in the aftermath to understand the FBI’s failures, but FBI has also been overwhelmed with the case load created by the attack. But, as I hope to return to, I think the specific failure in advance of January 6 lies elsewhere.
Whatever the merit in blaming Wray for FBI’s failure to prepare for January 6, there’s a bigger problem with Rubin’s attempt to blame him on the MAL search. Strzok sketched out in great detail something I had seen, too. The dispute about searching Trump’s house wasn’t between the FBI and DOJ. It wasn’t just what Vance and Strzok both describe as a fairly normal dispute between the FBI and DOJ with the former pushing the latter to be more aggressive.
It was between the WFO on one side and DOJ and FBI HQ on the other.
[A] careful reading of the Post’s reporting (insofar as the reporting is complete) reveals this was not so much a conflict between DOJ and the FBI as much as a conflict between DOJ and FBI headquarters, on the one hand, and the management of the FBI’s Washington Field Office, on the other.
Indeed, a key part of the drama surrounding the pre-August search meeting described by the WaPo involved the conflict between FBI General Counsel Jason Jones — whom WaPo makes a point of IDing as a Wray confidant, thereby marking him as Wray’s surrogate in this fight — and WFO Assistant Director Steven D’Antuono.
Jason Jones, the FBI’s general counsel who isconsidered a confidant of FBI Director Christopher A.Wray, agreed the team had sufficient probable cause to justify a searchwarrant.
[snip]
Jones, the FBI’s general counsel, said he planned to recommend to Deputy FBI Director Paul Abbate that the FBI seek a warrant for the search, the people said. D’Antuono replied that he would recommend that they not.
This, then, was partly a fight within FBI, one in which Wray’s surrogate sided with prosecutors.
Strzok makes a compelling argument that this story may have come from pushback necessitated by people at WFO floating bullshit claims, not dissimilar from — Strzok doesn’t say this, but I will — the leak by right wing agents to Devlin Barrett about the Clinton Foundation investigation in advance of the 2016 election, which led Andrew McCabe to respond in a way that ultimately gave Trump the excuse he wanted to fire him.
Indeed, Strzok’s post includes a well-deserved dig on the WaPo’s claim about, “the fact that mistakes in prior probes of Hillary Clinton … had proved damaging to the FBI,” an unsubstantiated claim I also called out.
[E]ven journalists can be imprecise or inaccurate. The Post’s article isn’t, for example, the type of comprehensive accounting you’d get in a report produced by an Inspector General, who can compile the statements of everyone involved and review and compare those statements to the written record in all its various forms.
Strzok right suggests that DOJ IG’s Report disproved WaPo’s claim about the Hillary investigation, but he seems to have forgotten that the DOJ IG Report into McCabe’s response on the Clinton Foundation didn’t fully air the FBI spox’s exculpatory testimony.
All of which is to say that, in the same way that WFO agents have an understandable visceral concern about getting involved in an investigation targeting Trump, people at HQ might have an equally visceral concern about stories seeded to Devlin Barrett alleging internal conflict that might create some flimsy excuse for firing.
But there’s something still unexplained about the WaPo story. Vance notes, as I did, that D’Antuono may have given Trump the opportunity to steal 47 documents.
[T]he delay couldn’t be undone. We still don’t know whether that resulted in the permanent loss of classified material. It did result in a delay in the timeline for making prosecutive decisions, ultimately extending the investigation into the period where Trump announced his 2024 candidacy, leading to the appointment of a special counsel to continue the investigation and determine whether to prosecute.
But Vance still accepts WaPo’s specious claim about timing, the claim that the delay (from June to August) in searching Trump’s resort led the investigation to bump up against a Trump campaign announcement that would surely have happened earlier had Trump not gotten an injunction. There’s nothing to support that temporal argument, and the public record on the injunction (which, again, lasted until almost a month after Jack Smith’s appointment) disproves it.
The timing issue is one of many reasons why I keep thinking about this earlier Devlin Barrett story, one that did bump up against the appointment of a Special Counsel. On November 14, the day before Trump formalized his 2024 run and so four days before the appointment of Jack Smith, Barrett and WaPo’s Mar-a-Lago Trump whisperer, Josh Dawsey, published a story suggesting that maybe Trump shouldn’t be charged because he just stole a bunch of highly classified documents to keep as trophies.
Federal agents and prosecutors have come to believe former president Donald Trump’s motive for allegedly taking and keeping classified documents was largely his ego and a desire to hold on to the materials as trophies or mementos, according to people familiar with the matter.
As part of the investigation, federal authorities reviewed the classified documents that were recovered from Trump’s Mar-a-Lago home and private club, looking to see if the types of information contained in them pointed to any kind of pattern or similarities, according to these people, who spoke on the condition of anonymity to discuss an ongoing investigation.
That review has not found any apparent business advantage to the types of classified information in Trump’s possession, these people said. FBI interviews with witnesses so far, they said, also do not point to any nefarious effort by Trump to leverage, sell or use the government secrets. Instead, the former president seemed motivated by a more basic desire not to give up what he believed was his property, these people said.
[snip]
The analysis of Trump’s likely motive in allegedly keeping the documents is not, strictly speaking, an element of determining whether he or anyone around him committed a crime or should be charged with one. Justice Department policy dictates that prosecutors file criminal charges in cases in which they believe a crime was committed and the evidence is strong enough to lead to a conviction that will hold up on appeal. But as a practical matter, motive is an important part of how prosecutors assess cases and decide whether to file criminal charges.
As I showed, that story, like this one, simply ignored stuff in the public record, including:
- Trump’s efforts, orchestrated in part by investigation witness Kash Patel, to release documents about the Russian investigation specifically to serve a political objective
- The report, from multiple outlets, that Jay Bratt told Trump’s lawyers that DOJ believes Trump still has classified documents
- Details about classified documents interspersed with a Roger Stone grant of clemency and messages — dated after Trump left the White House — from a pollster, a book author, and a religious leader; both sets of interspersed classified documents were found in Trump’s office
- The way Trump’s legal exposure would expand if people like Boris Epshteyn conspired to help him hoard the documents or others like Molly Michael accessed the classified records
Since then, other details have become clear. Not only was that story written after DOJ told Trump they believed he still had some classified documents, but it was written in the period between the time Trump considered letting the FBI do a consensual search and the time he hired people to do the search for him, a debate inside the Trump camp that parallels the earlier investigative fight between WFO and DOJ. Indeed, when DOJ alerted Trump’s lawyers in October that they believed Trump still had classified documents, that may have reflected WFO winning the debate they had lost before the August search: to let Trump voluntarily comply.
That’s important background to where we are now. Trump’s team has misrepresented to the press how cooperative they have been since. First, Trump’s people misleadingly claimed that Beryl Howell had decided not to hold Trump in contempt (rather than just deferred the decision) and Trump lied to the press for several months, hiding the box with documents marked classified and the additional empty classified folder. Those public lies should only make investigators wonder what Trump continues to hide.
We know Trump blew off the subpoena that WFO agents were sure would work in June, and there’s good reason to believe DOJ finds Trump’s more recent claims of cooperation to be suspect as well.
So let’s go back to that earlier Devlin story. As I noted at the time, I don’t dispute that the most classified documents have the appearance of trophies, but that’s because of the Time Magazine covers they were stored with, not because of any halfway serious scrutiny of Trump’s potential financial goals. Particularly given the presence of 43 empty classified folders in the leatherbound box along with the most sensitive documents, no thorough investigator could rule out Trump already monetizing certain documents, particularly given Trump and Jared Kushner’s financial windfalls from the Saudi government, particularly given the way that Trump’s Bedminster departure coincided with Evan Corcoran’s turnover of classified documents, particularly given that the woman who carted a box including some marked classified around various offices had been in Bedminster with Trump during the summer. I don’t dispute that’s still a likely explanation for some — but in no way all — of the documents, but no competent investigator could have made that conclusion by November 14, when Devlin published the story.
Unless Devlin’s sources — perhaps the same or similar to the sources who know that WFO agents were cowed by the treatment of Crossfire Hurricane agents — were working hard to avoid investigating those potential financial ties.
Unless the timing of the story reflected an attempt to win that dispute, only to be preempted by the appointment of Jack Smith. The earlier dispute could not have been impacted by the appointment of Jack Smith. If there was a later dispute about how to make sure Trump wasn’t still hoarding classified documents, though, it almost certainly was.
Someone decided to leak a story to Devlin Barrett suggesting that investigators had already reached a conclusion about Trump’s motive, even though as the story acknowledged, “even the nonclassified documents” — better described as documents without classification marks that not only hadn’t been reviewed yet, which could have included unmarked classified information — “taken in the search may include relevant evidence.” (Note, these are the same unclassified documents that, the recent story describes D’Antuono, insanely from an investigative standpoint, scoffing at collecting because, “We are not the presidential records police.”) Devlin’s sources decided to leak that story at a time when DOJ was trying to figure out how to get the remaining documents from Trump, and yet his sources presented a working conclusion that it didn’t matter if DOJ got the remaining documents: it had already been decided, Devlin’s sources told him, that Trump was just a narcissist fighting to keep his trophies from time as President and probably that shouldn’t be prosecuted anyway.
The story of the earlier dispute is alarming because it confirms that WFO agents remain cowed in the face of the prospect of investigating Trump, as some did even six years ago. The later story, though, is alarming because leaks to Devlin have a habit of creating political firestorms that are convenient for Trump. But it is alarming because it suggests even after the August search proved the WFO agents’ efforts to draw premature conclusions wrong, someone still decided to make — and force, by leaking to Devlin Barrett — some premature conclusions in November, an effort that genuinely was thwarted by the appointment of Jack Smith.