[NB: Note the byline, thanks! Updates will appear within the timeline or at the bottom of the text. /~Rayne]
I noted this past week that Trump’s attempt to extort performance from Ukraine had been in the works for three years.
18/21-JUL-2016 — The Republican National Committee debates the party’s platform at the RNC convention, including its position on aid to Ukraine.
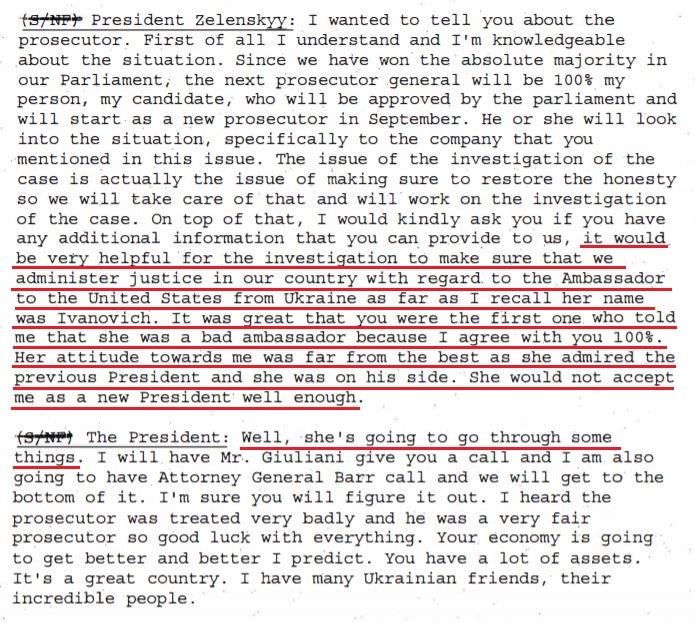
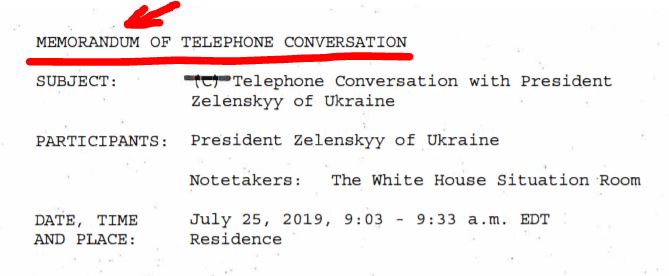
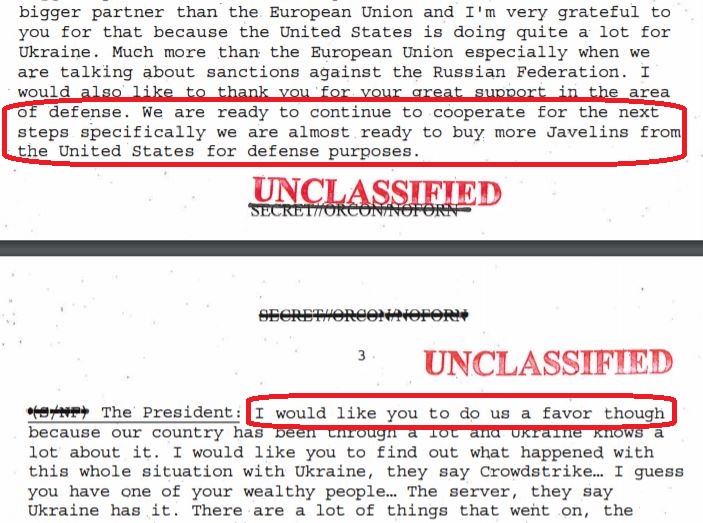
25-JUL-2019 — Trump talked with Ukraine’s Zelensky on the phone to congratulate him on his party’s parliamentary win on July 21 and to make a quid pro quo offer of aid for dirt on Trump’s re-election opponent, Joe Biden and Biden’s son Hunter.
This is all of the same, long story, in which:
• Long-time political consultant Paul Manafort rehabilitated pro-Russian Ukrainian politician Viktor Yanukovych’s image and helped him win the presidency in 2010;
• Manafort went on to become campaign manager for pro-Russian political candidate Donald Trump and helped him “win” the presidency in 2016 using some of the same techniques employed in Ukraine for Yanukovych;
• Trump’s pro-Russian policies manifested as resistance to bipartisan sanctions on Russia, pressure on NATO member states and threatened U.S. withdrawal from treaty obligations;
• Trump withheld military aid to Ukraine as part of a quid pro quo, asking for Ukraine’s assistance to help his personal re-election campaign.
But entwined in the years-long story arc is Rudy Giuliani, who shows up at key times and places having personal interests woven together with pro-Russian characters.
When the whistleblower timeline first began and events were crowdsourced from the emptywheel community, much of the timeline was focused on current events related to the middle east. Like the commercial media reporting on the whistleblower complaint, we didn’t make the connection to Ukraine initially. Nor did we make a direct connection to Russia.
The crowdsourced timeline didn’t make a connection to Giuliani, either. But as I continued to work on pulling together the events that led up to the July 25 phone call between Trump and Ukraine’s president Zelensky as well as the events afterward, Giuliani’s name popped up ever more frequently. He also deliberately inserted himself, too; he’s incapable of shutting the fuck up and has now pointedly implicated himself by admitting to seeking damaging information on Joe Biden and his son Hunter.
One of Giuliani’s companies has been doing business in Ukraine related to Russian-Ukrainian oligarch Pavel Fuchs. Fuchs has slowly acquired many of the assets which once belonged to Yanukovych, like some weird body-snatcher assuming Yanukovych’s identity. And Giuliani has a vested interest in whatever is shaking out of this in Fuchs’ native city, Kharkiv.
The more I pulled on the Giuliani thread, the more it became clear he is as tightly interleaved into Trump-Ukraine-Russia as is Paul Manafort. The association between Manafort ending up at Rudy’s favorite cigar bar — the Grand Havana Room at 666 Fifth Avenue, in a building owned by Jared Kushner, located a third of a mile from Trump Tower — to meet with Konstantin Kilimnik wasn’t a fluke.
It’s a very small world and the same players repeat over and over again.
So here’s the crowdsourcing assignment:
— In comments add any Ukraine, Russia, Giuliani-related event which shaped the quid pro quo made on July 25, or heightened the urgency of Ukraine’s national security, or affected the Special Counsel’s investigation related to Trump-Russia. Please provide citations easily validated by community members.
— If an additional person and related events should be added to this timeline, make the case in comments along with supporting citations.
This will NOT be an open thread; it will be dedicated to this project.
~ ~ ~ ~ ~
Timeline of Trump-Ukraine (I am leaving other non-Ukraine foreign policy matters in the timeline for now. Often what appears unrelated at present appears connected in the future.)
Legend: Indigo blue – Ukraine-related item; indented – older item in previous timeline.
__________
19-AUG-2016 — Ukrainian journalist and member of parliament Serhiy Leshchenko revealed secret payments outlined in the ‘black ledger of the Party of Regions’ showing payments made by the former pro-Russian president Viktor Yanukovych to Trump campaign chairman Paul Manafort.
24-AUG-2016 — Rudy Giuliani alleges the Clinton Foundation is a “pay-for-play operation” which was “going to be bigger than Watergate.” [UPDATE-4]
26-OCT-2016 — In an interview on Fox network, Rudy Giuliani said, “I mean, I’m talking about some pretty big surprises,” with regard to insider FBI information. In another Fox network program later that same day, Giuliani said, “I do think that all of these revelations about Hillary Clinton finally are beginning to have an impact. He’s got a surprise or two that you’re going to hear about in the next two days.” These remarks caused then-FBI director James Comey to launch an investigation into possible leaks. [UPDATE-4]
________
12-JAN-2017 — Rudy Giuliani named an informal security adviser for president-elect Donald Trump. (As an informal adviser Giuliani may not have been paid and may not have been required to comply with the same ethics standards as paid advisers, but may also have violated 31 U.S. Code § 1342 Limitation on voluntary services.)
24-JAN-2017 — Nikki Haley confirmed as U.S. ambassador to the United Nations. [UPDATE-4]
25-JAN-2017 — Trump tweeted, referencing then-Attorney General Jeff Sessions [UPDATE-4]:
03-MAR-2017 — Recruited by K.T. McFarland and Michael Flynn, “Russia hawk” Fiona Hill appointed Special Assistant to the President and Senior Director for European and Russian Affairs on his National Security Council staff. [UPDATE-4]
10-MAY-2017 — Trump met Russian Foreign Minister Sergey Lavrov and Russian ambassador to the US Sergey Kislyak in the Oval Office.
15-MAY-2017 — Washington Post reported Trump revealed code word level classified information to Lavrov and Kislyak during Oval Office meeting. The information covered ISIL’s bomb-making capabilities and may have exposed allies’ intelligence gathering means and methods.
XX-MAY-2017 — Date TBD. Giuliani met with officials for the city of Kharkiv, Ukraine and signed a deal for his firm Giuliani Security and Safety to review the city’s security services.
XX-MAY-2017 — Decision made to exfiltrate key Russian asset. Unclear exactly when decision made or when exfiltration occurred, only that it happened after the Oval Office meeting with Lavrov and Kislyak, and before the G20 meeting in Hamburg, Germany.
08-JUN-2017 — At a conference in Kyiv organized by Ukrainian metals magnate Victor Pinchuk, Giuliani met and spoke with then-President Petro Poroshenko, Prosecutor General Yuriy Lutsenko, and other government officials. Pinchuk had made a $150,000 donation to Trump’s charity in 2016, drawing Special Counsel’s attention. [UPDATE-2]
07-JUL-2017 — Kurt Volker was named U.S. Special Representative to Ukraine. At the time he was a senior international adviser to the BGR Group, a lobbying firm founded by GOP operative Haley Barbour; BGR had been hired by Ukraine to lobby the U.S. [UPDATE-1]
7/8-JUL-2017 — Trump meets Putin at G20 meeting in Hamburg, Germany.
11-JUL-2017 — European Union’s 28 member states formally endorsed the EU-Ukraine Association Agreement, effective September 1.
30-OCT-2017 — Paul Manafort, former Trump campaign manager, indicted.
14-NOV-2017 — National Security Council approved the sale of lethal aid to Ukraine, including Javelin missiles.
20-NOV-2017 — Giuliani met with officials for the city of Kharkiv, Ukraine this week as well as investor/developer Pavel Fuchs. Giuliani also met with then-president Petro Poroshenko in Kyiv. [UPDATE-1]
21-DEC-2017 — Trump authorized the sale of lethal aid to Ukraine, including Javelin missiles.
________
XX-JAN-2018 — Date, location TBD. Giuliani met with Ukraine’s prosecutor general Yuriy Lutsenko, according to Lutsenko. [UPDATE-4]
01-MAR-2018 — U.S. Defense Department approved the sale of Javelin anti-tank missiles and launch units to Ukraine.
04-MAR-2018 — former Russian military intelligence officer and UK double agent Sergei Skripal and his daughter were poisoned outside their UK home by a Russian-made nerve agent. [UPDATE-1]
26-MAR-2018 — U.S. expelled 60 Russian diplomatic personnel, the ‘heaviest’ response of three options posed by advisers to Trump in response to the nerve agent poisoning of Skripal and his daughter in UK. [UPDATE-1]
27-MAR-2018 — Giuliani met with officials from city of Kharkiv, Ukraine in New York City. The list of Ukrainian visitors is not known.
09-APR-2018 — John Bolton begins as National Security Adviser.
09-APR-2018 — Office of Trump’s personal lawyer Michael Cohen raided by FBI.
30-APR-2018 — U.S. State Department confirmed that Washington delivered thirty-five Javelin anti-tank launchers to Ukraine.
02-MAY-2018 — NYT reported Lutsenko’s office froze investigations into four open cases in April, limiting or eliminating cooperation with Special Counsel’s investigation; “‘In every possible way, we will avoid irritating the top American officials,’ one Ukrainian lawmaker says. ‘We shouldn’t spoil relations with the administration.'” Ukraine had also halted its money laundering investigation into former President Viktor Yanukovych, who may have used stolen Ukrainian taxpayer funds to pay convicted former Trump campaign manager Paul Manafort to aid him in winning in Ukraine. The four cases were deemed “too politically sensitive” putting U.S. financial and military aid at risk.
04-MAY-2018 — Senators Bob Menendez, Dick Durbin, and Pat Leahy wrote a letter to Lutsenko asking if his office had ceased cooperation with the Special Counsel’s investigation, if the Trump administration had asked them not to cooperate, and if the Special Counsel’s investigation had been discussed during a meeting between Trump and then-president Petro Poroshenko in New York 2017.
15-MAY-2018 — Russia’s President Putin opened a new bridge linking southern Russia to Crimea; Ukraine’s president Poroshenko said it was an attempt to legitimize the occupation of Crimea while Ukrainian critics said the bridge project violates international law. The bridge was built following the illegal 2014 annexation of Crimea by Russia.
08-JUN-2018 — Jonathan Cohen became deputy permanent representative to the United Nations. [UPDATE-4]
16-JUL-2018 — U.S.-Russia Summit meeting in Helsinki, Finland; Trump meets with Putin.
XX-JUL-2018 — Coats expressed opinion differing from Trump’s after Helsinki summit. Rumors began about Trump replacing Coats.
24-JUL-2018 — Trump suspends practice of notifying public his calls with foreign leaders; public readouts will no longer be furnished. [UPDATE-5]
13-AUG-2018 — Congress approved military aid to Ukraine as part of the annual National Defense Authorization Act which Trump signed this date. Trump, however, added a 15-page signing statement in which he reserved the right to refuse to recognize items related to Russia in this bill.
31-AUG-2018 — Manafort associate Sam Patten pleaded guilty to failing to register as a foreign agent under FARA; he agreed to cooperate with the Special Counsel’s investigation. Patten, while representing the Ukrainian political party the Opposition Bloc, laundered a $50,000 contribution from Russian/Ukrainian political consultant Konstantin Kilimnik to the Trump inauguration committee. [UPDATE-2]
02-OCT-2018 — Saudi journalist and US resident Jamal Khashoggi assassinated in the Saudi consulate in Istanbul, Turkey. [UPDATE-4]
09-OCT-2018 — Ambassador to the U.N. Nikki Haley announced her resignation; effective date 31-DEC-2018.
11-OCT-2018 — Ecumenical Patriarchate of Constantinople recognized the independence of the Ukrainian Orthodox Church, praised by Ukraine but protested by Russia. The move by the patriarchate heightened tensions between the two nation-states.
22/24-OCT-2018 — Giuliani was a guest speaker at the third International Forum of Eurasian Partnership (IFEP) in Yerevan, Armenia; one of two speakers with whom Giuliani appeared on a panel was Sergey Glazyev, who is sanctioned by the U.S. The forum was funded by the Russian Government. [UPDATE-2]
25-NOV-2018 — Russia seized three Ukrainian navy ships, injuring six crew after firing on them in the Kerch Straits of the Black Sea near Crimea. The attack violated a 2003 treaty which designated the Kerch Strait and Sea of Azov as shared territorial waters. US representative Nikki Haley called the incident an “outrageous violation of sovereign Ukrainian territory” during an emergency U.N. Security Council meeting.
26-NOV-2018 — Ukraine implemented martial law for 30 days in response to the Kerch Straits event, due to concerns over a Russian invasion.
26-DEC-2018 — Martial law in Ukraine ended, to allow adequate time before the country’s elections.
31-DEC-2018 — Volodymyr Zelensky, a TV producer who starred in a series playing the role of President of Ukraine, announced his candidacy for Ukraine’s presidency.
31-DEC-2018 — Ambassador to the U.N. Nikki Haley leaves as previously announced. [UPDATE-2019]
________
01-JAN-2019 — Jonathan Cohen became acting U.S. ambassador to the United Nations. [UPDATE-4]
XX-JAN-2019 — Date, TBD. Rudy Giuliani (member of Trump’s personal legal team) met with Lutsenko in New York City, venue unknown. [UPDATE-4]
29-JAN-2019 — Coats testified before Senate Intelligence Committee; he said North Korea “is unlikely to completely give up its nuclear weapons and production capabilities,” in contrast to Trump’s claims that Kim Jong-un has committed to denuclearization.
XX-FEB-2019 — Trump discussed replacements for DNI.
~13-FEB-2019 — Date, TBD. Rudy Giuliani met with Lutsenko in Warsaw, Poland, venue unknown. Giuliani had been speaking at a middle east conference delivering anti-Iran remarks. [UPDATE-4]
28-FEB-2019 — Congress was notified of military aid tranches to be released to Ukraine.
05-MAR-2019 — U.S. Ambassador to Ukraine Marie Yovanovitch criticized Ukraine’s record on corruption; she noted the country’s high court’s decision weakens Ukraine’s National Anti-Corruption Bureau.
06-MAR-2019 — Trump made remarks about aid to Ukraine [To be confirmed, details needed].
XX-MAR-2019 — Date TBD. Lutsenko relaunches an investigation into Burisma, the oil and gas company for which Joe Biden’s son had served as a board member. Per NYT (reported in May 2019):
… The decision to reopen the investigation into Burisma was made in March by the current Ukrainian prosecutor general, who had cleared Hunter Biden’s employer more than two years ago. The announcement came in the midst of Ukraine’s contentious presidential election, and was seen in some quarters as an effort by the prosecutor general, Yuriy Lutsenko, to curry favor from the Trump administration for his boss and ally, the incumbent president, Petro O. Poroshenko. …
20-MAR-2019 — The Hill’s John Solomon interviewed Ukraine’s prosecutor general Yuriy Lutsenko for Hill.TV; Lutsenko claimed Amb. Yovanovitch gave him a do-not-prosecute list during their first meeting. State Department denied this claim in an email to Radio Free Europe. [To be confirmed: Lutsenko also said there was an investigation launched into the Democratic National Committee.]
21-MAR-2019 — Attorney Victoria Toensing of law firm of diGenova & Toensing piles on with right-wing media in attacks on Yovanovitch, via Twitter [UPDATE-4]:
24-MAR-2019 — Donnie Trump Jr. made indirect, disparaging remarks about diplomat Yovanovitch via Twitter.
~28-MAR-2019 — In ‘early 2019’, Giuliani met with Ukraine’s prosecutor general Yuriy Lutsenko in New York (exact date TBD).
31-MAR-2019 — Ukraine’s first run-off presidential election narrowed down the field to the incumbent Petro Poroshenko and Volodymyr Zelensky.
31-MAR-2019 — Attorney Toensing continues with promotion of content against Ambassador Yovanovitch. [UPDATE-4]
12-APR-2019 — Patten sentenced to three years probation, after assisting the government in a number of other investigations. It’s not known what investigations he may have aided. [UPDATE-4]
21-APR-2019 — Volodymyr Zelensky won Ukraine’s presidential election over Petro Poroshenko, 73.22% to 24.45% of the vote. 12% of the population were unable to vote due to the conflict with Russia in Donbass region.
21-APR-2019 Trump called and congratulated Zelensky; the call was noted in a late evening/early morning tweet by Volker:
25-APR-2019 — After two years of indecision, former VP Joe Biden formally launched his campaign for POTUS.
25-APR-2019 — In an interview with Fox host Sean Hannity, Trump said, “I would imagine [Barr] would want to see this,” alleging Ukraine was conducting an investigation into collusion between Ukrainian officials and the Clinton campaign in 2016. “I would certainly defer to the attorney general, and we’ll see what he says about it,” Trump said. “He calls ’em straight…It sounds like big stuff, very interesting with Ukraine. I just spoke with the new president a while ago, and congratulated him. … But that sounds like big, big stuff, and I’m not surprised.” [UPDATE-4]
07-MAY-2019 — Amb. Yovanovitch was recalled — removed from her position.
09-MAY-2019 — Giuliani said he intended to meet with President-elect Zelensky in Ukraine to push for an investigation into the release of negative information about Paul Manafort as well as former VP Joe Biden’s efforts to remove Ukraine’s general prosecutor.
10-MAY-2019 — Senator Chris Murphy (D-CT) made an official request of the Senate Committee on Foreign Relations to investigate Giuliani’s influence operation in Ukraine.
11-MAY-2019 — Giuliani reversed his decision and said he won’t go to Ukraine to meet with Zelensky. Zelensky’s adviser Serhiy Leschenko said Zelensky
14-MAY-2019 — According to the whistleblower complaint, Trump “instructed Vice President Pence to cancel his planned travel to Ukraine to attend President Zelenskyy’s inauguration.” [UPDATE-4]
20-MAY-2019 — Date Zelensky assumes office of presidency.
21-MAY-2019 — Lawyer and film producer Andriy Yermak appointed aide to Ukraine’s Zelensky.
23-MAY-2019 — Congress was notified of military aid tranches to be released to Ukraine. John Rood, defense undersecretary for policy, advised Congress that DOD found Ukraine’s anti-corruption efforts adequate. [UPDATE-4]
24-MAY-2019 — Trump issued a directive allowing Attorney General William Barr to declassify any intelligence that sparked the opening of the Russia investigation.
11-JUN-2019 — Ukraine’s president Zelensky signed a motion for Ukraine’s parliament to dismiss prosecutor general Yuriy Lutsenko, an ally of former president Poroshenko. The MPs rejected the motion; Lutsenko also resisted, saying he would step down after the July 21 parlimentary elections.
11-JUN-2019 In an interview released on Thursday, June 13, Trump told ABC’s George Stephanopoulos,
“I think you might want to listen, there isn’t anything wrong with listening,” Trump continued. “If somebody called from a country, Norway, [and said] ‘we have information on your opponent’ — oh, I think I’d want to hear it.”
18-JUN-2019 — Fiona Hill announced her departure from administration effective August 2019. She will be succeeded by Tim Morrison, NSC adviser on weapons of mass destruction and biodefense. Morrison’s move was seen as a Bolton recommendation. [UPDATE-4]
20-JUN-2019 — In retaliation for downing a U.S. drone, Trump approved strikes on Iran which were abruptly aborted.
02-JUL-2019 — US Special Representative for Ukraine Kurt Volker met with Zelensky in Toronto; he discussed Ukraine’s “weak judicial system” and its affect on reform while weighing Zelensky’s political acumen given his lack of experience in governance. Zelensky joked about Giuliani during the meeting; the Bidens were not discussed.
~11-JUL-2019 — Date TBD. In mid-July, Giuliani had a phone meeting with Zelensky’s adviser, Andriy Yermak.
18-JUL-2019 — Trump ordered his acting chief of staff Mick Mulvaney to put the brakes on aid to Ukraine. Officials were instructed to tell lawmakers that the delay was due to “interagency process.” Mulvaney is also the Director of the Office of Management and Budget (OMB).
19-JUL-2019 — Text exchange between Kurt Volker and Rudy Giuliani: [UPDATE-5]
[7/19/19, 4:48 PM] Kurt Volker: Mr Mayor — really enjoyed breakfast this morning. As discussed, connecting you jere with Andrey Yermak, who is very close to President Zelensky. I suggest we schedule a call together on Monday — maybe 10am or 11am Washington time? Kurt
19-JUL-2019 — Text exchange between Kurt Volker and Gordon Sondland: [UPDATE-5]
[7/19/19, 4:49:42 PM] Kurt Volker: Can we three do a call tomorrow—say noon WASHINGTON?
[7/19/19, 6:50:29 PM] Gordon Sondland: Looks like Potus call tomorrow. I spike [sic] directly to Zelensky and gave him a full briefing. He’s got it.
[7/19/19, 6:52:57 PM] Gordon Sondland: Sure!
[7/19/19, 7:01:22 PM] Kurt Volker: Good. Had breakfast with Rudy this morning—teeing up call w Yermak Monday. Must have helped. Most impt is for Zelensky to say that he will help investigation—and address any specific personnel issues—if there are any
20-JUL-2019 — Attorney Lanny Davis and his firm, Davis, Goldberg & Galper, ended their arrangement with Ukrainian oligarch Dmytro Firtash, who had been charged with international racketeering by the U.S. in 2014. The law firm of diGenova & Toensing assumed representation for Firtash. [UPDATE-4]
22-JUL-2019 — Zelensky’s Servant of the People wins Ukraine’s parliamentary elections.
23-JUL-2019 —
24-JUL-2019 – Special Counsel Robert Mueller appears before House Judiciary Committee. The same day that GOP Rep. John Ratcliffe (TX-4) used his time to question Mueller to accuse Mueller of breaking DOJ regulations; CNN reported that “Ratcliffe has been under consideration for a job within the Trump administration, sources told CNN, including an intelligence or national security role.”
24-JUL-2019 — Toensing on Twitter the afternoon before key phone call [UPDATE-4]:
25-JUL-2019 — Trump talked with Ukraine’s Zelensky on the phone “to congratulate him on his recent election.” Ukraine’s English-language readout of this call said Trump discussed “investigations into corruption cases that have hampered interaction between Ukraine and the U.S.A.” (This call is the subject of whistleblower complaint.)
28-JUL-2019 — Coats’ departure and John Ratcliffe nominated as replacement announced by Trump via Twitter.
31-JUL-2019 — Trump spoke with Putin on the phone; they discussed fires in Siberia. [UPDATE-5]
31-JUL-2019 — Former U.S. ambassador to Canada Kelly Knight Craft confirmed U.S. ambassador to the United Nations. [UPDATE-4]
02-AUG-2019 — Ratcliffe withdraws from consideration.
~02-AUG-2019 — Trump administration asked ODNI for a list of all ODNI employees at the federal government’s top pay scale who have worked there for 90 days or more. This was believed to be a search for a new Director of ODNI; others speculated there was an impending personnel shakeup.
06-AUG-2019 — John Huntsman, U.S. Ambassador to Russia, submitted his resignation letter effective 03-OCT-2019, two years to the date he assume office. [UPDATE-5]
08-AUG-2019 — Primary Deputy Director DNI Sue Gordon resigned effective 15-AUG-2019, without additional prior notice, as ordered. Resignation letter without handwritten note.
Copy of former PDDNI’s resignation letter with handwritten cover: ODNI_LTR_08AUG2019
11-AUG-2019 — Giuliani debriefing with two State Department diplomats about his meeting with Ukraine’s Zelensky aide in Madrid, Spain.
12-AUG-2019 — IC IG received the whistleblower compaint, via Schiff’s 10-SEP letter.
15-AUG-2019 — Coats’ last day as DNI.
XX-AUG-2019 — Date TBD. In mid-August, lawmakers learned the Office of Management and Budget had taken over Defense and State Departments’ budgetary decisions, delaying aid distribution including aid to Ukraine. It’s not clear OMB had legal authority to restrain aid already authorized nearly a year earlier by Congress.
22-AUG-2019 — Giuliani said the U.S. State Department helped set up his meeting(s) with Zelensky’s aide Yermak, assisting “his efforts to press the Ukrainian government to probe two prominent Democratic opponents of the president: former Vice President Joe Biden and the Democratic National Committee.”
26-AUG-2019 — ICIG transmitted the whistleblower complaint to the Acting DNI, via Schiff’s 10-SEP letter.
26-AUG-2019 — GOP appointee Matthew Peterson resigned from Federal Election Commission; effective date of resignation 31-AUG-2019. FEC no longer has a quorum with his departure.
27-AUG-2019 — Russia barred a visa for entry to Senators Chris Murphy (D-CT) and Ron Johnson (R-WI) for a trip planned in early September. Senator Mike Lee (R-UT) received clearance and a visa, however. Johnson, Murphy and Lee are all members of the Senate Foreign Relations Committee; Johnson is the subcommittee chair for Europe & Regional Security Cooperation. The three senators voted in favor of the Russia sanctions bill.
28-AUG-2019 — John Bolton met with Ukraine’s Zelensky (video).
28-AUG-2019 — Bolton met his counterpart, Oleksandr Danyliuk, Ukraine’s head of the National Defense and Security Council; Bolton told Danyliuk that the U.S. support for Ukraine against Russian-backed separatists in contested eastern Ukraine would ‘intensify’.
29-AUG-2019 — Trump stalled the $250M military assistance provided under the Ukraine Security Assistance Initiative by asking Bolton and Defense Secretary Mark Esper to review the package. Defense Department had already reviewed the aid and supported it.
29-AUG-2019 — Lutsenko submitted his resignation on the first day of work for the new parliament.
30-AUG-2019 — Trump tweeted a high-resolution satellite image of Iran’s failed Safir SLV launch while claiming the U.S. was not involved. The image may have been classified and ‘insta-declassified’ by Trump.
30-AUG-2019 — Fiona Hill departs administration. Not clear if she left before/after Trump’s tweeted image of Safir SLV launch site.
01-SEP-2019 — VP Mike Pence flew to Poland and met with Poland’s president Andrzej Duda and Ukraine’s Zelensky, discussing security and energy issues (remarks issued by White House). Per pool reporter, the meeting included National Security Adviser John Bolton and Energy Secretary Rick Perry; Pence avoided answering media questions whether the Trump administration would still allocate $250M for security aid.
01/02-SEP-2019 — US Special Rep. for Afghanistan Zalmay Khalizad met with Afghan president Ashraf Ghani in Kabul where the Taliban, Afghan government and the U.S. had “reached an agreement in principle” toward an eventual “total and permanent cease-fire.”
02-SEP-2019 — During news conference after the meeting with Duda and Zelensky in response to a question by AP’s Jill Colvin, Pence denied speaking about Joe Biden with Zelensky:
“Well, on the first question [about Biden], the answer is no. But we — with President Zelensky yesterday, we discussed — we discussed America’s support for Ukraine and the upcoming decision the President will make on the latest tranche of financial support in great detail.”
02-SEP-2019 — Deadline for ADNI to forward the complaint to Intelligence committees of Congress passes without a referral, via Schiff’s 10-SEP letter.
03-SEP-2019 — Russian media outlet Tass reported that Russian Deputy Foreign Minister said the U.S. and Taliban “insist that Russia must be present in one capacity or another at the possible signing of the agreements that the parties are working on now.”
03-SEP-2019 — Sen. Murphy and Johnson began a 5-day trip to Serbia, Kosovo, Ukraine, and Germany. Several officials in Zelensky’s administration told Murphy during this visit that U.S. aid had been withheld; the delay was attributed to a resistance to investigating Joe and Hunter Biden though Zelensky himself did not communicate this.
04-SEP-2019 — Secretary of State Mike Pompeo refused to sign the agreement with the Taliban.
07-SEP-2019 — Russia and Ukraine completed a major prisoner swap; some of the prisoners included Ukrainian sailors seized during the Kerch straits incident.
09-SEP-2019 — CNN broke story of a CIA asset extracted from Russia in 2017; followed by NYT on the 9th (and then NBC’s Ken Dilanian appears at the asset’s house…)
09-SEP-2019 — Trump asked for Bolton’s resignation and tweeted about it the next morning.
09-SEP-2019 — Intelligence Community Inspector General (ICIG) sent a letter to the House Permanent Select Committee on Intelligence, notifying it of a whistleblower complaint which it had determined to be credible and a matter of “urgent concern.”
09-SEP-2019 — Three House committees launch investigation(s) to look into whether Trump and Giuliani asked Ukraine to investigate Joe and Hunter Biden.
10-SEP-2019 — Bolton tells Fox’s Brian Kilmeade by text that he’d quit.
10-SEP-2019 — HPSCI Rep. Adam Schiff requested the full, unredacted complaint, the IC IG’s determination about the complaint, and all documentation of ODNI’s action regarding this complaint, including correspondence with the White House.
11-SEP-2019 — Delayed aid to Ukraine finally released.
11-SEP-2019 — Bloomberg reported Bolton pushed back Monday-Tuesday at Trump over Iran sanctions; Bolton wanted maximum pressure while Trump wanted to encourage a meeting with Iran’s Rouhani later in September.
12-SEP-2019 — Schiff and ADNI “discussed at length” the need to protect the whistleblower from any retaliation, including if the whistleblower subsequently comes forward to the committee with his/her concerns, via Schiff’s 13-SEP letter.
12-SEP-2019 — Republican senators said aid to Ukraine had been delayed while Trump assessed whether Ukraine’s Zelensky was pro-West/pro-Russia, and that Sen. Dick Durbin threatened to hold up appropriations until the aid was released. There were concerns about finalizing defense appropriations before the end of the federal fiscal year on September 30.
13-SEP-2019 — Zelensky said in a press conference that not only was the U.S. going to send $250M in military aid but an additional $140M.
13-SEP-2019 — ODNI declined the request, claiming the request as “it involves confidentially and potentially privileged communications by persons outside the Intelligence Community.”
13-SEP-2019 — HPSCI subpoenaed acting DNI Joseph Maguire for materials declined by ODNI.
17-SEP-2019 — Deadline, materials responsive to subpoena must be turned over by this date; Maguire failed to do so.
18-SEP-2019 — Pence and Zelensky met by phone and discussed future aid for Ukraine’s security.
19-SEP-2019 — Date Maguire was compelled to appear before Congress in a public hearing. The Intelligence Community Inspector General Michael Atkinson appeared before the House Intel Committee in a closed door session.
19-SEP-2019 — Giuliani denied asking Ukraine to investigate Joe Biden moments before admitting that he had done just that.
20-SEP-2019 — Senator Murphy published a press release about the whistleblower complaint, renewing his call for a Senate Foreign Services Committee investigation into Giuliani’s efforts to influence Ukraine.
20-SEP-2019 — Russian armed forces bombarded front along western edge of contested Donbas territory.
22-SEP-2019 — During an interview on Meet the Press, Treasury Secretary Steve Mnuchin can’t explain where the additional $140M in aid for Ukraine came from.
22-SEP-2019 — In front of press on the White House lawn, Trump said he had spoken with Zelensky about Biden on July 25 in a congratulatory call. Later in the day he indicated he might allow a transcript of the call to be published.
26-SEP-2019 — Maguire testified before the House Intelligence Committee in a public hearing.
26-SEP-2019 — Toensing via Twitter, this time targeting HPSCI chair Rep. Schiff [UPDATE-4]:
27-SEP-2019 — Volker resigns as US Special Representative for Ukraine [UPDATE-1]
~ ~ ~ ~ ~
Future dates:
30-SEP-2019 — Federal fiscal year ends on September 30.
Scheduled House Permanent Subcommittee on Intelligence hearings:
02-OCT-2019 — former ambassador Marie “Masha” Yovanovitch
03-OCT-2019 — former U.S. Special Representative for Ukraine Kurt Volker
07-OCT-2019 — Deputy Assistant Secretary in the European and Eurasian Bureau George Kent
08-OCT-2019 — Counselor of the U.S. Department of State T. Ulrich Brechbuhl
10-OCT-2019 — Ambassador to the European Union Gordon Sondland
~ ~ ~ ~ ~
Again, this will NOT be an open thread; it will be dedicated to this project.
_____
UPDATE-3 — 4:25 P.M. EDT —
The HPSCI, House Oversight, and House Foreign Affairs Committees subpoenaed Rudy Giuliani today. Keep digging, people! I’ll add the content accumulated since 1:00 a.m. EDT later this evening. Thanks!
The chairs of these committees also subpoenaed Giuliani associates, noticing deposition for:
October 10, 2019: Lev Parnas
October 11, 2019: Igor Fruman
October 14, 2019: Semyon “Sam” Kislin
More details at the HPSCI website. These next two weeks are going to be busy!
ADDER: I can’t find any other outlet has covered this yet, very sorry — the article will be behind a paywall so most of us can’t read it.
“Among the administration officials” suggests we don’t yet have the full list of folks who were supposed to be in attendance on the call, on site physically or remotely.
Wondering how long before Pompeo is subpoenaed?
ADDER-2: Whoops, looks like Pompeo was prevaricating with the media before today.
UPDATE-4 — 11:39 P.M. EDT 01-OCT-2019 —
This update is still rolling, will continue to add items as I get through them from here forward. Thank you for all you contributions in thread; it’s taking me longer than I expected to read them and cross-match against other resources.
I expect to have a refreshed timeline completed by the end of the week though at the rate new reporting on the Trump-Russia-Giuliani relationship is crazy making. Like playing “Where’s Waldo?” with a loudmouthed, be-suited weasel in a crowd of weasels.
“Where’s Rudy?” More like where hasn’t he been?
UPDATE-5 — 11:45 P.M. EDT 03-OCT-2019 —
Documents from Kurt Volker’s deposition before the HPSCI, Foreign Affairs, and Oversight Committees have been released. Volker appears to be taking his lumps but it’s not a good look to appear to be supporting Trump’s abuse of power, holding promised aid hostage in exchange for a commitment to investigate Trump’s political rival.
The addition of the text messages from the deposition into the timeline will be the last update to this post.
Crap’s going to hit the oscillator in the morning.