Yes, Margaret, the NSA Dragnet Does Involve Infiltration
Margaret Talbot has a piece at the New Yorker comparing COINTELPRO with Snowden’s leaks (and implicitly, the theft of data that lies behind both disclosures). Here’s the key paragraph of the comparison:
In most respects, the National Security Agency’s collection of domestic phone records which Edward Snowden revealed is nowhere near as disturbing as cointelpro’s activities. It is neither ideologically motivated (the N.S.A.’s actions were initially ramped up in response to a real attack; Hoover’s were intent on destroying perceived enemies) nor thuggish (it entails surveillance but not infiltration or harassment or blackmail or smear campaigns). Yet in one regard—its technological prowess—it is worse. As the U.S. District Court Judge Richard Leon wrote last month, in an opinion that strongly suggests that the metadata collection could be found unconstitutional, “Records that once would have revealed a few scattered tiles of information about a person now reveal an entire mosaic—a vibrant and constantly updating picture of a person’s life.” Leon noted that the government did not cite any instances in which the data collection proved necessary in preventing an imminent attack, and concluded that, when weighed against the “almost-Orwellian technology that enables the Government to store and analyze the phone metadata of every telephone user in the United States,” the N.S.A.’s rationale was simply too weak. [my emphasis]
There’s a lot I might quibble with in this paragraph. The government considered the anti-war effort part of Communism’s “attack” on the “free world,” whether or not that was true, in the same way it sometimes considers many critics of US policy in the Middle East — if they are themselves Muslim — to be inspired by al Qaeda, not opposition to crappy US policy. And the NSA has itself analogized its targeting of certain people in the US as terrorists with Project Minaret, the SIGINT targeting of largely anti-war activists; if the NSA makes this comparison, who are we to question it? Further, there’s evidence (albeit still very sketchy) that NSA targeted people associated with the Iraq War, not just terrorism.
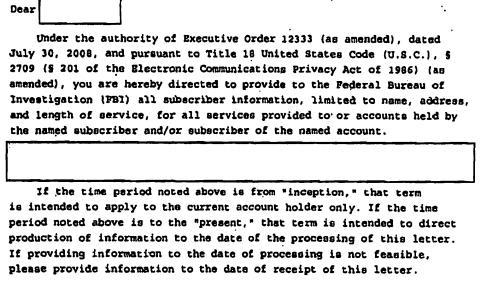
But I’m particularly concerned by Talbot’s claim that none of this dragnet entails infiltration. The government itself told the FISA Court that it uses the phone dragnet to find potential informants — it is, according to the representations the government has made to get the FISC to approve the program, one of the primary purposes of the dragnet.
From the very start of the FISC-approved program, the government maintained the dragnet “may help to discover individuals willing to become FBI assets,” and given that the government repeated that claim 3 years later, it does seem to have been used to find informants.
When you unpack the possibilities of using metadata including the phone records of all Americans to find people who might narc on their community, it becomes very scary indeed. Because the dragnet would allow the government to discover details about people — their 3 degrees of separation from people suspected of terrorist ties, sure, but also extramarital affairs or financial problems — they can use to harass or blackmail potential informants with to convince them to inform, something they’ve suggested they do with their SIGINT.
One of the only reasons why we don’t know more about this is because we’re seeing just the NSA side of these programs. The government is thoroughly redacting any details about what FBI or CIA do with the data that gets churned out of the dragnet (all while boasting of its transparency), so we can’t yet explain what happens between the time the data gets crunched and some kid gets caught in a sting or some American loses her right to fly.
But we do know what the end product of infiltrating the Muslim community looks like, both in the way FBI informants push young men until they press a button they can be arrested for, the descriptions of the extensive spying FBI’s (and NYPD’s) informants conduct, largely targeted at mosques, and in the effect it has had on the discourse that takes place within those mosques.
African-Americans in the heart of Michigan’s auto industry built the mosque I attended as a child.
[snip]
Our African-American imam took turns with others to deliver the Friday khutba (sermon). We witnessed oral traditions accented from around the globe and across the road: the khateebs(deliverers of sermons) were lyrical and inspired, awkward and soft-spoken; the congregants received the khutba differently too, from active talk back to a silent receptive posture. While varied in style, the khutba routinely offered global context and critical content. The khateebs would remind us of the poverty in Detroit’s neighborhoods and the death in Baghdad’s streets. They would preach about the importance of the Muslim ummah (global community) and the duty to speak out against injustices small and large. The khateeb would regularly call for civic engagement as he also reached for religious inspiration.
These days, when I stop in a mosque, I am struck by the new normal: no politics, no world, no nimble movement between religious ethics and social context. Today’s khutbas present the congregation religious teachings in a void. Khateebs speak of the importance of honesty, forgiveness, humility and remembrance. They ignore Iraq and Afghanistan, Guantánamo and drones, informants and surveillance. They tell stories about Muhammad, Abraham, Moses, Mary and Jesus but leave out the universal themes of poverty, inequality and injustice.
From mosques to Muslim Student Association offices, American Muslim community spaces have been emptied of their politics, leeched of their dynamism as centers for religious and political debate. This new normal is the result of ten years of post-9/11 scrutiny combined with our government’s more recent embrace of “counter-radicalization” and “countering violent extremism” programs, which subject Muslim communities’ religious and political practices to aggressive surveillance, regulation and criminalization.
It’s easy, I think, for elite non-Muslim commentators to consider the infiltration of a political tradition they or their associates had personal involvement in, the anti-war movement, to be worse than the infiltration of mosques. I’m not sure they’re in a position to judge. But at least from what I’ve seen and heard, the infiltration of America’s Muslim communities seems designed to “enhance the paranoia endemic in these circles and will further serve to get the point across there is an FBI agent behind every mailbox,” just as the FBI’s efforts targeting the anti-war and African-American communities aimed to do.
The NSA has told us the dragnet involves infiltration. That the NSA hands off the data it collects so the FBI can carry out the infiltration should not confuse us that it does, in fact, play a role in infiltrating communities and sowing paranoia.