According to Mike Flynn’s Fox News lawyer, Sidney Powell, to “defend” himself in a guilty plea he has already sworn to twice under oath, he needs to obtain unredacted versions of a Comey memo showing he was not targeted with a FISA warrant and a FISA order showing that people who were targeted with FISA warrants might have been improperly scrutinized while they were overseas.
That’s just part of the batshittery included in a request for Brady material submitted to Emmet Sullivan last Friday.
The motion is 19 pages, most of which speaks in gross generalities about Brady obligations or repeats Ted Stevens Ted Stevens Ted Stevens over and over again, apparently a bid to convince Judge Emmet Sullivan that this case has been subject to the same kind of abuse that the late Senator’s was.
After several readings, I’ve discovered that Powell does make an argument in the motion: that if the government had provided Flynn with every damning detail it has on Peter Strzok, Flynn might not have pled guilty to lying to Strzok about his conversations with Russian Ambassador Sergey Kislyak or admitted that he used a kickback system to hide that he was a paid agent of Turkey while getting Top Secret briefings with candidate Trump.
They affirmatively suppressed evidence (hiding Brady material) that destroyed the credibility of their primary witness, impugned their entire case against Mr. Flynn, while at the same time putting excruciating pressure on him to enter his guilty plea and manipulating or controlling the press to their advantage to extort that plea. They continued to hide that exculpatory information for months—in direct contravention of this Court’s Order—and they continue to suppress exculpatory information to this day.
One of the things Powell argues Flynn should have received is unredacted copies of every text Strzok sent Lisa Page.
The government’s most stunning suppression of evidence is perhaps the text messages of Peter Srzok and Lisa Page. In July of 2017, (now over two years ago), the Inspector General of the Department of Justice advised Special Counsel of the extreme bias in the now infamous text messages of these two FBI employees. Mr. Van Grack did not produce a single text messages to the defense until March 13, 2018, when he gave them a link to then-publicly available messages. 14
Mr. Van Grack and Ms. Ahmad, among other things, did not disclose that FBI Agent Strzok had been fired from the Special Counsel team as its lead agent almost six months earlier because of his relationship with Deputy Director McCabe’s Counsel—who had also been on the Special Counsel team—and because of their text messages and conduct. One would think that more than a significant subset of those messages had to have been shared by the Inspector General of the Department of Justice with Special Counsel to warrant such a high-level and immediate personnel change. Indeed, Ms. Page left the Department of Justice because of her conduct, and Agent Strzok was terminated from the FBI because of it.
14 There have been additional belated productions. Each time more text messages are found, produced, or unredacted, there is more evidence of the corruption of those two agents. John Bowden, FBI Agent in Texts: ‘We’ll Stop’ Trump From Becoming President, THE HILL (June 14, 2018), https://thehill.com/policy/national-security/392284-fbi-agent-in-texts-well-stop-trumpfrom-becoming-president; see also U.S. Dept. of Justice, Office of the Inspector General, A Review of Various Actions by the Federal Bureau of Investigation and Department of Justice in Advance of the 2016 Election. Redacted Ed. Washington, D.C. (2018) (https://www.justice.gov/file/1071991/download). But the situation is even worse. After being notified by the Inspector General of the Department of Justice of the extraordinary text communications between Strzok and Page (more than 50,000 texts) and of their personal relationship, which further compromised them, Special Counsel and DOJ destroyed their cell phones. U.S. Dept. of Justice, Office of the Inspector General, Report of Investigation: Recovery of Text Messages From Certain FBI Mobile Devices, Redacted Ed. Washington, D.C. (2018), https://www.justice.gov/file/1071991/download. This is why our Motion also requests a preservation order like the one this Court entered in the Stevens case.
As is true of most of this filing, Powell gets some facts wrong here. The public record says that as soon as Mueller got the warning from Michael Horowitz about the texts, he started moving Strzok off the team. He didn’t need to see the texts, that they were there was issue enough. And Lisa Page remained at FBI until May 2018, even after the texts were released to the public.
And while, if Sullivan had taken Flynn’s initial guilty plea rather than Rudy Contreras, one might argue that Van Grack should have alerted Flynn’s lawyer Rob Kelner of the existence of the Strzok-Page texts, DOJ was not required to turn them over before Flynn’s guilty plea. Moreover, the problem with claiming that withholding the Strzok-Page texts prevented Flynn from taking them into account, is that they were made public the say day Emmet Sullivan issued his Brady order and Flynn effectively pled guilty again a year after they were released, in sworn statements where he also reiterated his satisfaction with his attorney, Kelner. Any texts suggesting bias had long been released; what remains redacted surely pertains either to their genuine privacy or to other counterintelligence investigations.
Finally, at least as far as public evidence goes, Strzok was, if anything, favorable to Flynn for the period he was part of the investigation. He found Flynn credible in the interview, and four months later didn’t think anything would come of the Mueller investigation. So the available evidence, at least, shows that Flynn was treated well by Strzok.
The filing also complains about information just turned over on August 16.
For example, just two weeks ago, Mr. Van Grack, Ms. Curtis, and Ms. Ballantine produced 330 pages of documents with an abject denial the production included any Brady material.6 Yet that production reveals significant Brady evidence that we include and discuss in our accompanying Motion (filed under seal because the prosecutors produced it under the Protective Order).
6 “[T]he government makes this production to you as a courtesy and not because production of this information is required by either Brady v. Maryland, 373 U.S. 83 (1963), or the Court’s Standing Order dated February 16, 2018.” Letter from Mr. Brandon Van Grack to Sidney K. Powell, Aug. 16, 2019.
Given the timing, it may well consist of the unclassified materials showing that Turkey (and possibly Russia) believed Flynn to be an easy mark and expected to be able to manipulate Trump through him. I await either the unsealing of Powell’s sealed filing or the government response to see if her complaints are any more worthy than this filing.
That’s unlikely. Because the rest of her memo makes a slew of claims that suggest she’s either so badly stuck inside the Fox bubble she doesn’t understand what the documents in question actually say, or doesn’t care. In her demand for other documents that won’t help Flynn she,
- Misstates the seniority of Bruce Ohr
- Falsely claims Bruce Ohr continued to serve as a back channel for Steele intelligence when in fact he was providing evidence to Bill Priestap about its shortcomings (whom the filing also impugns)
- Suggests the Ohr memos pertain to Flynn; none of the ones released so far have the slightest bit to do with Flynn
- Falsely suggests that Andrew Weissmann was in charge of the Flynn prosecution
- Claims that Weissman and Zainab Ahmad had multiple meetings with Ohr when the only known meeting with him took place in fall 2016, before Flynn committed the crimes he pled guilty to; the meeting likely pertained to Paul Manafort, not Flynn
- Includes a complaint from a Flynn associate that pertains to alleged DOD misconduct (under Trump) to suggest DOJ prosecutors are corrupt
In short, Powell takes all the random conspiracy theories about the investigation and throws them in a legal filing without even fact-checking them against the official documents, or even, at times, the frothy right propaganda outlets that first made the allegations.
Things get far weirder when it comes to her demands relating to FISA information. In a bid to claim this is all very pressing, Powell demands she get an unredacted version of the Comey IG Report.
Since our initial request to the Department by confidential letter dated June 6, 2019, we have identified additional documents that we specify in our Motion. Now, with the impending and just-released reports of the Inspector General, there may be more. The Report of the Inspector General regarding James Comey’s memos and leaks is replete with references to Mr. Flynn, and some information is redacted. There may also be a separate classified section relevant to Mr. Flynn. U.S. Dept. of Justice, Office of the Inspector General, Report of Investigation of Former Federal Bureau of Investigation Director James Comey’s Disclosure of Sensitive Investigative Information and Handling of Certain Memoranda, Oversight and Review Division Report 19-02 (Aug. 29, 2019), https://oig.justice.gov/reports/2019/o1902.pdf
The only redacted bits in the report are in Comey’s memos themselves — the stuff that the frothy right is currently claiming was so classified that Comey should have been prosecuted for leaving them in a SCIF at work. Along with unclassified sections quoting Trump saying he has “serious reservations about Mike Flynn’s judgment” (the redacted bit explains that the President was pissed that Flynn didn’t tell him about Putin’s congratulatory call right away) and “he had other concerns about Flynn,” there’s this section that redacts the answer to Reince Priebus’ question about whether the FBI has a FISA order on Flynn (PDF 74).
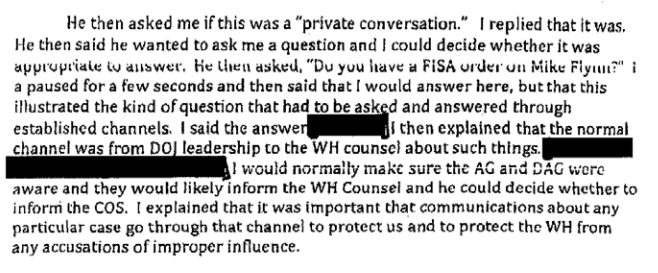
The answer, though, is almost certainly no. Even if the FBI obtained one later, there was no way that Comey would have told Priebus that Flynn was targeted; the FBI became more concerned about Flynn after this February 8 conversation, in part because of his continued lies about his work with Turkey.
Flynn’s team also demands an unredacted copy of this 2017 FISA 702 Rosemary Collyer opinion, though Powell’s understanding of it seems to based off Sara Carter’s egregiously erroneous reporting on it (here’s my analysis of the opinion).
Judge Rosemary Collyer, Chief Judge of the FISA court, has already found serious Fourth Amendment violations by the FBI in areas that likely also involve their actions against Mr. Flynn. Much of the NSA’s activity is in direct violation of the Fourth Amendment. Not only did the last administration—especially from late 2015 to 2016—dramatically increase its use and abuse of “about queries” in the NSA database, which Judge Collyer has noted was “a very serious Fourth Amendment issue,” it also expanded the distribution of the illegally obtained information among federal agencies.10 Judge Collyer determined that former FBI Director Comey gave illegal unsupervised access to raw NSA data to multiple private contractors. The court also noted that “the improper access granted the [redacted] contractors was apparently in place [redacted] and seems to have been the result of deliberate decision making” including by lawyers.11, 12
10 See also Charlie Savage, NSA Gets More Latitude to Share Intercepted Communications, THE N.Y. TIMES (Jan. 12, 2017) (reporting that Attorney General Loretta Lynch signed new rules for the NSA that permitted the agency to share raw intelligence with sixteen other agencies, thereby increasing the likelihood that personal information would be improperly disclosed), https://www.nytimes.com/2017/01/12/us/politics/nsa-gets-more-latitude-to-share-interceptedcommunications.html; See also Exec. Order No. 12,333, 3 C.F.R. 200 (1982), as amended by Exec. Order No. 13,284, 68 Fed. Reg. 4075 (Jan. 23, 2003).
11 FISC Mem. and Order, p. 19, 87 (Apr. 26, 2017) www.dni.gov/files/documents/icotr/51117/2016_Cert_FISC_Memo_Opin_Order_Apr_2017.pdf (noting that 85% of the queries targeting American citizens were unauthorized and illegal).
12 This classified and heavily redacted opinion is one of the documents for which defense counsel requests a security clearance and access.
As a threshold matter, Powell gets virtually everything about the Collyer memo wrong. Collyer didn’t track any increase in “about” searches (it was one of the problems with her memo, that she didn’t demand new numbers on what NSA was doing). It tracked a greater number of certain kinds of violations than previously known. The violation resulting in the 85% number she cited was on US persons targeted between November 2015 and May 2016, but the violation problem existed going back to 2012, when Flynn was still part of the Deep State. What Collyer called a Fourth Amendment violation involved problems with 704/705b targeting under FISA, which are individualized warrants usually tied to individualized warrants under Title I (that is, the kind of order we know targeted Carter Page), and probably a limited set of terrorism targets. Given that the Comey memo almost certainly hides evidence that Flynn was not targeted under FISA as of February 8, 2017, it means Flynn would have had to be a suspected terrorist to otherwise be affected. Moreover, the NSA claimed to have already fixed the behavioral problem by October 4, 2016, even before Carter Page was targeted. I had raised concerns that the problems might have led to problems with Page’s targeting, but since I’ve raised those concerns with Republicans and we haven’t heard about them, I’m now fairly convinced that didn’t happen.
At least some of the FBI violation — letting contractors access raw FISA information — was discontinued in April 2016, before the opening of the investigation into Trump’s flunkies, and probably all was discontinued by October 4, 2016, when it was reported. One specific violation that Powell references, however, pertains to 702 data, which could not have targeted Flynn.
Crazier still, some of the problems described in the opinion (such as that NSA at first only mitigated the problem on the tool most frequently used to conduct back door searches) cover things that happened on days in late January 2017 when a guy named Mike Flynn was National Security Advisor (see PDF 21).

Powell should take up her complaints with the guy running National Security at the time.
Craziest still, Powell describes data collected under EO 12333 as “illegally obtained information” (Powell correctly notes that the Obama Administration permitted sharing from NSA to other agencies, but that EO would not affect the sharing of FISA information at all). If EO 12333 data, which lifetime intelligence officer Mike Flynn used through his entire career, is illegally obtained, then it means lifetime intelligence officer Mike Flynn broke the law through his entire government career.
Sidney Powell is effectively accusing her client (incorrectly) of violating the law in a motion that attempts to argue he shouldn’t be punished for the laws he has already admitted breaking.
In short, most of the stuff we can check in this motion doesn’t help Flynn, at all.
And at least before Powell submitted this, Emmet Sullivan seemed unimpressed with her claims of abuse.
The government and Flynn also submitted a status report earlier on Friday. In the status report, the government was pretty circumspect. Flynn’s cooperation is done (which is what they said almost a year ago), they’d like to schedule sentencing for October or November, and they’ve complied with everything covered by Brady. Anything classified, like Powell is demanding, would be governed by CIPA and only then discoverable if it is helpful to the defense.
Powell made more demands in the status report, renewing her demand for a security clearance and insisting there are other versions of the Flynn 302.
To sort this out, the government suggested a hearing in early September, but Powell said such a hearing shouldn’t take place for another month (during which time some of the IG reports she’s sure will be helpful will come out).
The parties are unable to reach a joint response on the above topics. Accordingly, our respective responses are set forth separately below. Considering these disagreements, the government respectfully requests that the Court schedule a status conference. Defense counsel suggests that a status conference before 30 days would be too soon, but leaves the scheduling of such, if any, to the discretion of the Court. The government is available on September 4th, 5th, 9th or 10th of 2019, or thereafter as the Court may order. Defense counsel are not available on those specific dates.
Judge Sullivan apparently sided with the government (and scheduled the hearing for a date when Flynn’s attorneys claim to be unable to attend).
Every time Flynn has tried to get cute thus far, it has blown up in his face. And while Sullivan likely doesn’t know this, the timing of this status hearing could be particularly beneficial for the government, as they’ll know whether Judge Anthony Trenga will have thrown out Bijan Kian’s conviction because of the way it was charged before the hearing, something that would make it far more likely for the government to say Flynn’s flip-flop on flipping doesn’t amount to full cooperation.
And this filing isn’t even all that cute, as far as transparent bullshit goes.










![[Photo: National Security Agency, Ft. Meade, MD via Wikimedia]](https://www.emptywheel.net/wp-content/uploads/2017/08/NationalSecurityAgency_HQ-FortMeadeMD_Wikimedia.jpg)