I got distracted reading two pieces this morning. This great Andrew O’Hehir piece, on how those attacking Edward Snowden and Glenn Greenwald ought to consider the lesson of Justice Louis Brandeis’ dissent in Olmstead.
In the famous wiretapping case Olmstead v. United States, argued before the Supreme Court in 1928, Justice Louis Brandeis wrote one of the most influential dissenting opinionsin the history of American jurisprudence. Those who are currently engaged in what might be called the Establishment counterattack against Glenn Greenwald and Edward Snowden,including the eminent liberal journalists Michael Kinsley and George Packer, might benefit from giving it a close reading and a good, long think.
Brandeis’ understanding of the problems posed by a government that could spy on its own citizens without any practical limits was so far-sighted as to seem uncanny. (We’ll get to that.) But it was his conclusion that produced a flight of memorable rhetoric from one of the most eloquent stylists ever to sit on the federal bench. Government and its officers, Brandeis argued, must be held to the same rules and laws that command individual citizens. Once you start making special rules for the rulers and their police – for instance, the near-total impunity and thick scrim of secrecy behind which government espionage has operated for more than 60 years – you undermine the rule of law and the principles of democracy.
“Our Government is the potent, the omnipresent teacher,” Brandeis concluded. “For good or for ill, it teaches the whole people by its example. Crime is contagious. If the Government becomes a lawbreaker, it breeds contempt for law; it invites every man to become a law unto himself; it invites anarchy. To declare that in the administration of the criminal law the end justifies the means — to declare that the Government may commit crimes in order to secure the conviction of a private criminal — would bring terrible retribution.”
And this more problematic Eben Moglen piece talking about how Snowden revealed a threat to democracy we must now respond to.
So [Snowden] did what it takes great courage to do in the presence of what you believe to be radical injustice. He wasn’t first, he won’t be last, but he sacrificed his life as he knew it to tell us things we needed to know. Snowden committed espionage on behalf of the human race. He knew the price, he knew the reason. But as he said, only the American people could decide, by their response, whether sacrificing his life was worth it.
So our most important effort is to understand the message: to understand its context, purpose, and meaning, and to experience the consequences of having received the communication.
Even once we have understood, it will be difficult to judge Snowden, because there is always much to say on both sides when someone is greatly right too soon.
I raise them in tandem here because both address the threat of spying to something called democracy. And the second piece raises it amid the context of American Empire (he compares the US to the Roman decline into slavery).
I raise them here for two reasons.
First, because neither directly notes that Snowden claimed he leaked the documents to give us a choice, the “chance to determine if it should change itself.”
“For me, in terms of personal satisfaction, the mission’s already accomplished,” he said. “I already won. As soon as the journalists were able to work, everything that I had been trying to do was validated. Because, remember, I didn’t want to change society. I wanted to give society a chance to determine if it should change itself.”
“All I wanted was for the public to be able to have a say in how they are governed,” he said. “That is a milestone we left a long time ago. Right now, all we are looking at are stretch goals.”
Snowden, at least, claims to have contemplated the possibility that, given a choice, we won’t change how we’re governed.
And neither O’Hehir nor Moglen contemplates the state we’re currently in, in which what we call democracy is choosing to expand surveillance in response to Snowden’s disclosures.
Admittedly, the response to Snowden is not limited to HR 3361. I have long thought a more effective response might (or might not!) be found in courts — that if, if the legal process does not get pre-empted by legislation. I have long thought the pressure on Internet companies would be one of the most powerful engines of change, not our failed democratic process.
But as far as Congress is concerned, our stunted legislative process has started down the road of expanding surveillance in response to Edward Snowden.
And that’s where I find Moglen useful but also problematic.
He notes that the surveillance before us is not just part of domestic control (indeed, he actually pays less attention to the victims of domestic surveillance than I might have, but his is ultimately a technical argument), but also of Empire.
While I don’t think it’s the primary reason driving the democratic response to Snowden to increase surveillance (I think that also stems from the Deep State’s power and the influence of money on Congress, though many of the surveillance supporters in Congress are also supporting a certain model of US power), I think far too many people act on surveillance out of either explicit or implicit beliefs about the role of US hegemony.
There are some very rational self-interested reasons for Americans to embrace surveillance.
For the average American, there’s the pride that comes from living in the most powerful country in history, all the more so now that that power is under attack, and perhaps the belief that “Us” have a duty to take it to “Them” who currently threaten our power. And while most won’t acknowledge it, even the declining American standard of living still relies on our position atop the world power structure. We get cheap goods because America is the hegemonic power.
To the extent that spying on the rest of the world serves to shore up our hegemonic position then, the average American might well have reason to embrace the spying, because it keeps them in flat screen TVs.
But that privilege is just enjoyed by some in America. Moglen, tellingly, talks a lot about slavery but says nothing about Jim Crow or the other instruments of domestic oppression that have long used authoritarian measures against targeted populations to protect white male power. American history looked at not against the history of a slavery that is past, but rather against the continuity of history in which some people — usually poor and brown and/or female — don’t participate in the American “liberty” and “privacy” Moglen celebrates, our spying on the rest of the world is more of the same, a difference in reach but not in kind. Our war on drugs and war on terror spying domestically is of a piece with our dragnet internationally, if thus far more circumscribed by law (but that law is expanding and that will serve existing structures of power!).
But there’s another reason Americans — those of the Michael Kinsley and George Packer class — might embrace surveillance. That’s the notion that American hegemony is, for all its warts, the least bad power out there. I suspect Kinsley and (to a lesser extent) Packer would go further, saying that American power is affirmatively good for the rest of the world. And so we must use whatever it takes to sustain that power.
It sounds stupid when I say it that way. I’m definitely oversimplifying the thought process involved. Still, it is a good faith claim: that if the US curtails its omnipresent dragnet and China instead becomes the dominant world power (or, just as likely, global order will dissolve into chaos), we’ll all be worse off.
I do think there’s something to this belief, though it suppresses the other alternative — that the US could use this moment to improve the basis from which US exercises its hegemony rather than accept the increasingly coercive exercise of our power — or better yet use the twilight of our hegemony to embrace something more fair (and also something more likely to adequately respond to the global threat of climate change). But I do believe those who claim US hegemony serves the rest of the world believe it fairly uncritically.
One more thing. Those who believe that American power is affirmatively benign power may be inclined to think the old ways of ensuring that power — which includes a docile press — are justified. As much as journalism embraced an adversarial self-image after Watergate, the fundamentally complicit role of journalism really didn’t change for most. Thus, there remains a culture of journalism in which it was justified to tell stories to the American people — and the rest of the world — to sustain American power.
One of those stories, for example, is the narrative of freedom that Moglen embraces.
That is, for those who believe it is worth doing whatever it takes to sustain the purportedly benign American hegemon, it would be consistent to also believe that journalists must also do whatever it takes to sustain purportedly benign system of (white male) power domestically, which we call democracy but which doesn’t actually serve the needs of average Americans.
And for better or worse, those who embrace that power structure, either domestically and/or internationally, expanding surveillance is rational, so long as you ignore the collateral damage.
Update: Tempered critique of Packer because I agree he’s not embracing this journalist as narrative teller as much.
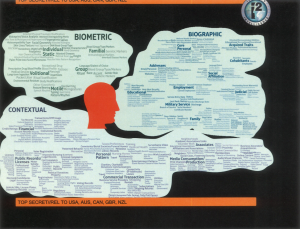 As part of my continuing obsession with the way NSA tracks identities, I wanted to take a close look at one slide released by the NYT with its facial recognition story the other day. It tracks all the kinds of data the NSA and its Five Eyes partners try to collect on targets (and I’m sure they aspire to this level of detail primarily with targets).
As part of my continuing obsession with the way NSA tracks identities, I wanted to take a close look at one slide released by the NYT with its facial recognition story the other day. It tracks all the kinds of data the NSA and its Five Eyes partners try to collect on targets (and I’m sure they aspire to this level of detail primarily with targets). Still. I was rather amused that a dragnet the US largely justifies in the name of counterterrorism includes sorority membership among the identity characteristics they collect.
Still. I was rather amused that a dragnet the US largely justifies in the name of counterterrorism includes sorority membership among the identity characteristics they collect.





