In a show of transparency, I Con the Record just released annual statistics for certain programs. Here are my thoughts, in rolling updates.
These arent’t the Certificates you’re looking for
Here’s what I Con the Record tells us about Section 702:
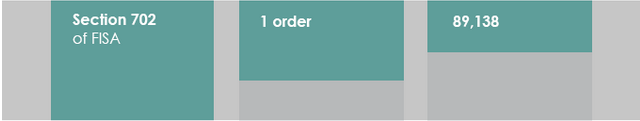
Just one order!!
Of course, we know from the 2011 John Bates opinion that one order likely includes several certificates. For a long time I wrongly bought off on ONDI propaganda that there were 3 certificates, covering counterterrorism, counterproliferation, and cybersecurity. But it appears the 3rd certificate is instead an unbelievably broad “foreign intelligence” one, which pretty much swallows the idea of specific certification.
I Con the Record even admits the proper unit is certificate.
Under Section 702, the Foreign Intelligence Surveillance Court (FISC) approves Certifications as opposed to individualized orders.
Yet I Con the Record won’t even tell us whether there are just 3 certificates still or more. Instead, it gives us how many orders there were.
Note, in internal reports, ODNI tracks average tasked selectors, which last year provided a number in the range of 65,000 selectors. So either their spying on a lot more 702 targets, or that number was artificially low.
I Con the Record finally admits “target” doesn’t mean what we think it means — or what they mean, sometimes
This might be regarded by some as “transparency.”
Targets: Within the Intelligence Community, the term “target” has multiple meanings. For example, “target” could be an individual person, a group, or an organization composed of multiple individuals or a foreign power that possesses or is likely to communicate foreign intelligence information that the U.S. government is authorized to acquire by the above-referenced laws.
Some laws require that the government obtain a Court order specifying the communications facilities used by a “target” to be subject to intelligence collection. Although the government may have legal authority to conduct intelligence collection against multiple communications facilities used by the target, the user of the facilities – the “target” – is only counted once in the above figures.
Except that it doesn’t admit that, at least in the past, sometimes target means “the switch we know lots of al Qaeda calls to use.” Meaning the term “target” is a misnomer even within the context they lay out.
Hiding the “Government Agency Protocols” that the Founders did not start a Revolution for
For Section 215 (which, remember, includes the phone dragnet, more targeted 2 or 3-degree queries for communication records, and collections of things like acetone purchase records and URL searches), the government gives us this weird byzantine map.

First, note that almost 150 more selectors were approved for querying the phone dragnet last year (423) than the year before (288). Plus, we can now put some of the queries in perspective. At the time of the Marathon attack, when the very wired Tsarnaev brothers (probably about 4 selectors between them) were queried, NSA permitted 3 hop chaining. That likely means just those 4 phone identifiers sucked in the better part of Cambridge, MA (if they went to that 3rd hop). All those people have had the NSA churning all their data (not just their phone number) for the last year.
Then there’s the general measure of how many “targets” of business records there are: 172. But note that some of these are “entities.” What if that includes anyone searching on a URL related to a particular entity, like AQAP or Wikileaks? That could suck in far more Americans. Note, the Tsarnaev brothers are probably one of those “entities” (or rather, two of the individuals) on whom there were multiple searches, potentially up to and including pressure cooker purchases or searches).
Finally, I Con the Record doesn’t talk about how many of 178 applications involved minimization procedures — what I shall now call “government agency protocols” after John Roberts’ observation that they don’t meet terms our Founders fought a Revolution for. The FISA report covering last year says they modified 141 applications. Most modified orders from the previous year involved government agency protocols, so last year’s probably were too (though there is still a February 2013 dragnet order they’re hiding). So that means about 137 of these orders were likely to be sufficiently large to require minimization, which means they likely implicate far more people, likely Americans, than the 137 reasons they were targeted.
I Con the Record’s National Security apples and oranges
I Con the Record did something rather … interesting with their NSL numbers.
To understand why, you need to understand that Congress only requires they report NSLs concerning US persons — except those asking for subscriber information. Presumably, that means there’s a whole bunch of bulky NSLs for subscriber information of Americans — basically FBI using NSLs to recreate phone books and email subscribers. Based on logic I lay out here, I think FBI issued about 5,500 of those phone book NSLs in 2012.
But today’s I Con the Record reports numbers somewhat differently. I Con the Record explains:
In addition to those figures, today we are reporting (1) the total number of NSLs issued for all persons, and (2) the total number of requests for information contained within those NSLs. For example, one NSL seeking subscriber information from one provider may identify three e-mail addresses, all of which are relevant to the same pending investigation and each is considered a “request.”
We are reporting the annual number of requests rather than “targets” for multiple reasons. First, the FBI’s systems are configured to comply with Congressional reporting requirements, which do not require the FBI to track the number of individuals or organizations that are the subject of an NSL.
Even if the FBI systems were configured differently, it would still be difficult to identify the number of specific individuals or organizations that are the subjects of NSLs. One reason for this is that the subscriber information returned to the FBI in response to an NSL may identify, for example, one subscriber for three accounts or it may identify different subscribers for each account.
Which gives us this:
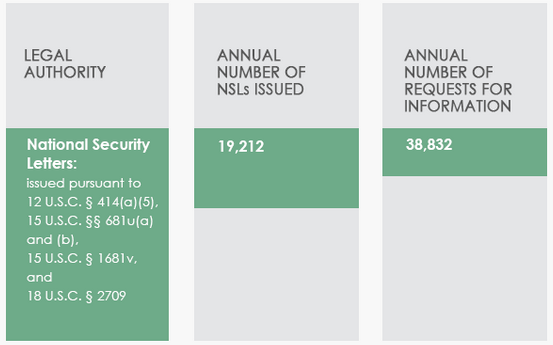
So the FISA report says 14,219 requests total, which includes just domestic, but those requests are for 5,334 individual Americans.
This report says 38,832 requests total, including domestic, domestic subscriber (phone book), and foreign (assuming the phone book numbers are around 5,000 again, that works about to be half domestic, half foreign). But we don’t know — effectively the government has managed to bracket off bulky requests under both “transparency” measures.
Ultimately, though, they never ever tell how many American are affected by NSLs. It could be not much more than that 5,334. Or it could be far, far higher, because requests are not targets.




