There are a number of issues with Marc Ambinder’s interpretation of the WaPo’s analysis of the content of NSA’s 702 collections as a “bust.” Ambinder:
- Overstates the specificity of the certifications, particularly in light of the general “foreign government” one recently revealed by WaPo
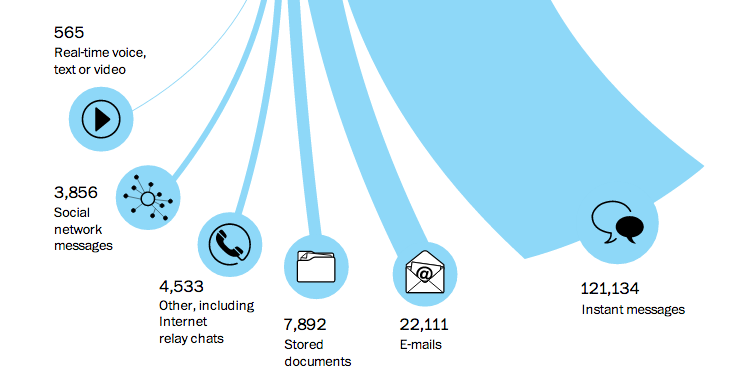
- Makes the same email rather than overwhelmingly IM mistake Stewart Baker made
- Doesn’t deal with the fact that the bulk of US identifiers that got minimized — the largest category, constituting over 57,000 instances — is IP address, which presents different privacy concerns than what he addresses
- Suggests this collection includes traditional FISA warrants; WaPo suggests it is all 702 collection, which ought to mean it includes less US person content (but apparently doesn’t)
- Ignores how readily the NSA provides unaudited access to raw data for tech personnel and SIGDEV, and therefore how (in)secure we should expect this data to be in practice
But the most troublesome problem with it is Ambinder’s treatment of the NSA’s minimization obligations and practices. Here are some statements Ambinder makes about NSA’s minimization requirements.
Ok, so: having run the data through an automatic minimization system of some sort, the NSA analysts are required to minimize every U.S.-person communication that they see. Minimize does not “to get rid of.” It means to anonymize the U.S.-based non-target source.
[snip]
Maybe I could be a customer service representative from the pizza place that got his order wrong, and I’m e-mailing him to apologize for it. The NSA and the FBI are required by statute to minimize the communication if they determine it has no intelligence value. (And why would the NSA waste time reading a conversation about pizza anyway?)
[snip]
The analyst’s judgment can be subjective. On the first instance, the analyst has to figure out whether the communication is relevant to a foreign intelligence purpose.
First he states that minimization does not mean “get rid of,” then states NSA is required by statute to get rid of communications that have no intelligence value, then notes an analyst has to determine whether a communication has foreign intelligence value. Overall, though, Ambinder suggests that NSA does get rid of communications involving US persons without foreign intelligence value.
Ambinder is absolutely right the law requires the government to get rid of US person data that has no foreign intelligence value.
Here’s what one version of the minimization requirements say:
(1) specific procedures, which shall be adopted by the Attorney General, that are reasonably designed in light of the purpose and technique of the particular surveillance, to minimize the acquisition and retention, and prohibit the dissemination, of nonpublicly available information concerning unconsenting United States persons consistent with the need of the United States to obtain, produce, and disseminate foreign intelligence information;
(2) procedures that require that nonpublicly available information, which is not foreign intelligence information, as defined in subsection (e)(1) of this section, shall not be disseminated in a manner that identifies any United States person, without such person’s consent, unless such person’s identity is necessary to understand foreign intelligence information or assess its importance;
(3) notwithstanding paragraphs (1) and (2), procedures that allow for the retention and dissemination of information that is evidence of a crime which has been, is being, or is about to be committed and that is to be retained or disseminated for law enforcement purposes; and
(4) notwithstanding paragraphs (1), (2), and (3), with respect to any electronic surveillance approved pursuant to section 1802 (a) of this title, procedures that require that no contents of any communication to which a United States person is a party shall be disclosed, disseminated, or used for any purpose or retained for longer than 72 hours unless a court order under section 1805 of this title is obtained or unless the Attorney General determines that the information indicates a threat of death or serious bodily harm to any person.
And here’s how that translates into the minimization procedures approved in 2011.
Personnel will exercise reasonable judgment in determining whether information acquired must be minimized and will destroy inadvertently acquired communications of or concerning a United States person at the earliest practicable point in the processing cycle at which such communication can be identified either: as clearly not relevant to the authorized purpose of the acquisition (e.g., the communication does not contain foreign intelligence information); or, as not containing evidence of a crime which may be disseminated under these procedures. Except as provided for in subsection 3(c)(2) below, such inadvertently acquired communications of or concerning a United States person may be retained no longer than five years from the expiration date of the certification authorizing the collection in any event.
Both the law and the minimization procedures approved by the FISC require NSA to get rid of US person communications that have no foreign intelligence purpose.
But here’s what the WaPo reveals about what NSA analysts do when they determine collection has no foreign intelligence value (note, however, these passages do not specify how many of these conversations include US person communications, though almost half of these communications involve US person identifiers).
Many other files, described as useless by the analysts but nonetheless retained, have a startlingly intimate, even voyeuristic quality. They tell stories of love and heartbreak, illicit sexual liaisons, mental-health crises, political and religious conversions, financial anxieties and disappointed hopes. The daily lives of more than 10,000 account holders who were not targeted are catalogued and recorded nevertheless.
[snip]
“None of the hits that were received were relevant,” two Navy cryptologic technicians write in one of many summaries of nonproductive surveillance. “No additional information,” writes a civilian analyst. [my emphasis]
While these passages are not quantifiable — both because WaPo didn’t say how many files NSA had determined to be “useless” and because WaPo didn’t identify how many of those include US persons — they do suggest that NSA is not complying with the legal requirement that they destroy communications involving US persons that don’t have foreign intelligence value. Not even for communications they describe as “useless” or “not relevant.”
That’s not surprising. As I noted the other day, PCLOB found that NSA “rarely” complies with this requirement and CIA and FBI never do.
[A]lthough a communication must be “destroyed upon recognition” when an NSA analyst recognizes that it involves a U.S. person and determines that it clearly is not relevant to foreign intelligence or evidence of a crime,531 in reality this rarely happens. Nor does such purging occur at the FBI or CIA: although their minimization procedures contain age-off requirements, those procedures do not require the purging of communications upon recognition that they involve U.S. persons but contain no foreign intelligence information.
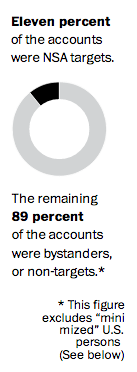
Ambinder is absolutely right that WaPo’s sample shows that NSA is pretty good, but not perfect, at masking US person identities in their data.
But both WaPo’s detailed analysis and PCLOB’s general review show that NSA does not comply with another key part of its legally required minimization obligations, to destroy communications involving US persons that have no foreign intelligence value. US person identifiers may be masked, but many of them shouldn’t be in the NSA’s databases at all. That needs to be acknowledged in any discussion of the NSA’s minimization procedures. The law requires them to get rid of US person communications with no intelligence value. But they don’t.
That’s why the sheer volume of very personal information in this sample is of concern (aside from the concern we should have for foreigners’ privacy; though again, WaPo doesn’t say how much of the US person data includes that personal information). Because the NSA and FBI and CIA can access this data without needing any suspicion of wrongdoing.