Clapper’s Claim that FBI Cannot Count Back Door Searches for Technical Reasons Probably Bullshit
I wanted to explain why I think it’s such a big deal that James Clapper specifically highlighted the carve out for transparency reporting on FBI’s back door searches in Leahy’s version of Freedom Act’s in his letter supporting the bill.
As I described, the bill requires reporting on back door searches, but then exempts the FBI from that reporting.
But that’s not the part of the bill that disturbs me the most. It’s this language:
‘(3) FEDERAL BUREAU OF INVESTIGATION.—
Subparagraphs (B)(iv), (B)(v), (D)(iii), (E)(iii), and (E)(iv) of paragraph (1) of subsection (b) shall not apply to information or records held by, or queries conducted by, the Federal Bureau of Investigation.
The language refers, in part, to requirements that the government report to Congress:
(B) the total number of orders issued pursuant to section 702 and a good faith estimate of—
(iv) the number of search terms that included information concerning a United States person that were used to query any database of the contents of electronic communications or wire communications obtained through the use of an order issued pursuant to section 702; and
(v) the number of search queries initiated by an officer, employee, or agent of the United States whose search terms included information concerning a United States person in any database of noncontents information relating to electronic communications or wire communications that were obtained through the use of an order issued pursuant to section 702;
These are back door searches on US person identifiers of Section 702 collected data — both content (iv) and metadata (v).
In other words, after having required the government to report how many back door searches of US person data it conducts, the bill then exempts the FBI.
In his letter, Clapper says,
[W]e are comfortable with the transparency provisions in this bill because, among other things, they recognize the technical limitations on our ability to report certain types of information.
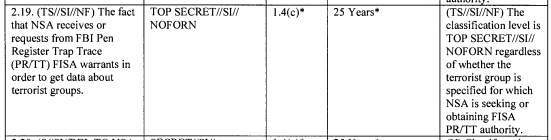
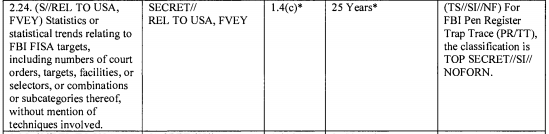
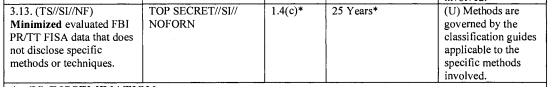
FBI back door searches are the most obvious limit on transparency guidelines, and FBI told PCLOB they couldn’t count them for technical reasons.
So effectively, Clapper is suggesting that Congress has recognized that FBI is incapable — for technical reasons — of counting how often it conducts back door searches.
That technical claim is almost certainly bullshit.
As a reminder, here’s what the government told PCLOB about FBI’s back door searches.
Because they are not identified as such in FBI systems, the FBI does not track the number of queries using U.S. person identifiers. The number of such queries, however, is substantial for two reasons.
First, the FBI stores electronic data obtained from traditional FISA electronic surveillance and physical searches, which often target U.S. persons, in the same repositories as the FBI stores Section 702–acquired data, which cannot be acquired through the intentional targeting of U.S. persons. As such, FBI agents and analysts who query data using the identifiers of their U.S. person traditional FISA targets will also simultaneously query Section 702–acquired data.
Second, whenever the FBI opens a new national security investigation or assessment, FBI personnel will query previously acquired information from a variety of sources, including Section 702, for information relevant to the investigation or assessment. With some frequency, FBI personnel will also query this data, including Section 702–acquired information, in the course of criminal investigations and assessments that are unrelated to national security efforts. In the case of an assessment, an assessment may be initiated “to detect, obtain information about, or prevent or protect against federal crimes or threats to the national security or to collect foreign intelligence information.”254 If the agent or analyst conducting these queries has had the training required for access to unminimized Section 702–acquired data, any results from the Section 702 data would be returned in these queries. If an agent or analyst does not have access to unminimized Section 702–acquired data — typically because this agent or analyst is assigned to non-national security criminal matters only — the agent or analyst would not be able to view the unminimized data, but would be notified that data responsive to the query exists and could request that an agent or analyst with the proper training and access to review the unminimized Section 702–acquired data.