Did FBI Stall an IG Review of Innocent Americans Sucked Up in the Dragnet?
I mentioned earlier that the FBI withheld information on the Bureau’s use of phone dragnet tippers from DOJ’s Inspector General long enough to make any review unusable for Congress’ consideration before it passed USA F-ReDux.
That’s important because of this passage from the Stellar Wind IG Report.
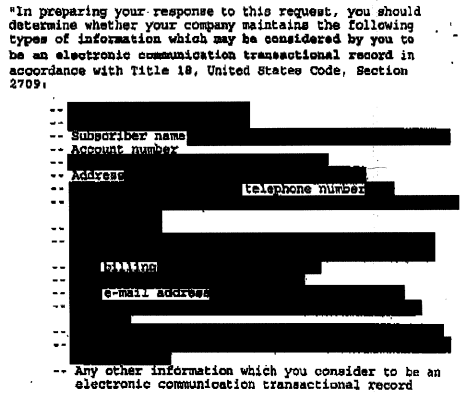
Another consequence of the Stellar Wind program and the FBI’s approach to assigning leads was that many threat assessments were conducted on individuals located in the United States, including U.S. persons, who were determined not to have any nexus to terrorism or represent a threat to national security.402 These assessments also caused the FBI to collect and retain a significant amount of personal identification about the users of tipped telephone numbers and e-mail addresses. In addition to an individual’s name and home address, such information could include where the person worked, records of foreign travel, and the identity of family members. The results of these threat assessments and the information that was collected generally were reported in communications to FBI Headquarters and uploaded into FBI databases.
The FBI’s collection of U.S. person information in this manner is ongoing under the NSA’s FISA-authorized bulk metadata collection. To the extent leads derived from this program generate results similar to those under Stellar Wind, the FBI will continue to collect and retain a significant amount of information about individuals in the United States, including U.S. persons, that do not have a nexus to terrorism or represent a threat to national security.
We recommend that as part of the [redacted] project, the Justice Department’s National Security Division (NSD), working with the FBI, should collect addresses disseminated to FBI field offices that are assigned as Action leads and that require offices to conduct threat assessments. The information compiled should include whether individuals identified in threat assessments are U.S. or non-U.S. persons and whether the threat assessments led to the opening of preliminary or full national security investigations. With respect to threat assessments that conclude that users of tipped telephone numbers or e-mail addresses are not involved in terrorism and are not threats to national security, the Justice Department should take steps to track the quantity and nature of U.S. person information collected and how the FBI retains and utilizes this information. This will enable the Justice Department and entities with oversight responsibilities, including the OIG and congressional committees, to assess the impact this intelligence program has on the privacy interests of U.S. persons and to consider whether, and for how long, such information should be retained. (PDF 666-7/329-330)
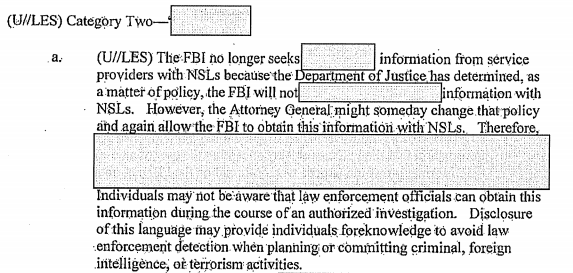
After a preceding section talking about how many of the tippers to FBI — which, after all, may be two hops away from someone of interest — weren’t all that useful, DOJ’s IG (the current IG, Michael Horowitz’s predecessor, Glenn Fine) noted how many Americans with no nexus to terrorism nevertheless have their names, home addresses, workplace, travel records, and family members’ identities collected and stored in an FBI database, potentially for decades. And, we now know, those assessments would include a search for any previously-collected content, which the FBI could read without a warrant.
Fine recommended that FBI begin to track what happens with the Americans sucked up in PATRIOT-authorized dragnets.
But we can be virtually certain FBI chose not to heed that recommendation, because it hasn’t heeded similar recommendations with NSLs, and because FBI refuses to track any of their other FISA-related activities.
And Horowitz has been very disciplined in following up on previous IG recommendations in reports that follow up on like topics, so that is likely one of the things he planned to investigate with his focus on the “receiving, processing, and disseminating [of] leads” from the phone dragnet.
The review will examine the FBI’s procedures for receiving, processing, and disseminating leads the NSA develops from the metadata, as well as any changes that have been made to these procedures over time. The review will also examine how FBI field offices respond to leads and the scope and type of information field offices collect as a result of any investigative activity that is initiated. In addition, the review will examine the role the leads have had in FBI counterterrorism efforts
Frankly, because NSA had to curtail so much of what they were doing with the phone dragnet in 2009, there should be fewer Americans sucked up in the dragnet now then there was when Fine did his Stellar Wind review in 2008-09. Though if FBI continued to require an assessment of every new identifier, it would still result in a lot of innocent Americans having their lives unpacked and stored for 30 years by the FBI.
But those numbers will likely be higher — potentially significantly higher — under USA F-ReDux, because any given query will draw off of more kinds of information. More importantly, FBI is exempted from counting the queries it does on any database of call detail records obtained under the new CDR function.
(C) the number of search terms that included information concerning a United States person that were used to query any database of call detail records obtained through the use of such orders;
[snip]
(A) FEDERAL BUREAU OF INVESTIGATION.—Paragraphs (2)(A), (2)(B), and (5)(C) of subsection (b) shall not apply to information or records held by, or queries conducted by, the Federal Bureau of Investigation.
This strongly suggests the data will come in through the FBI, be treated under FBI’s far more permissive (than NSA’s) minimization procedures, and searched regularly. Which likely means the privacy implications of innocent Americans sucked up into the dragnet will be far worse. And all that’s before any of the analysis NSA will do on these query results.
There was no public consideration of the privacy impact of the innocent Americans sucked in under the CDR function during the USA F-ReDux debate (though I wrote about it repeatedly).
But if DOJ’s IG intended to include past recommendations in its review of what FBI does with the phone dragnet data — which would be utterly consistent with past practice — that’s one of the things this review, the review FBI stalled beyond the point when it could be useful, would have focused on.