Google’s Payoff from DOD: 20 Cheap Fuel Flights to Tortola
 Given that I’m very interested in the carrots and sticks the government uses to get tech companies to help spy on us, I find it rather interesting that from 2007 until August 31, DOD was allowing Google to pay for jet fuel at Moffett Field near Google’s HQ in Mountain View at DOD’s substantially discounted rate.
Given that I’m very interested in the carrots and sticks the government uses to get tech companies to help spy on us, I find it rather interesting that from 2007 until August 31, DOD was allowing Google to pay for jet fuel at Moffett Field near Google’s HQ in Mountain View at DOD’s substantially discounted rate.
Granted, this arose because Google provided a light airplane to perform scientific flights for Ames Research Center.
NASA officials have pointed to a related agreement by the Google executives to perform scientific flights and other NASA-related transport. That mostly has involved flights by an Alpha jet, a small trainer bought by the Google executives and used by NASA to measure atmospheric greenhouse gases and ozone.
[snip]
[T]he contract between H211 and the Pentagon stated that the fuel was supposed to be used only “for performance of a U.S. government contract, charter or other approved use,” and said violations could trigger civil or criminal penalties. There is no indication of any such investigation.
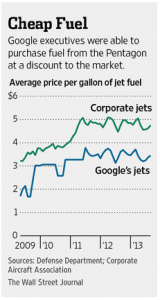
Flight records from the Federal Aviation Administration suggest that the vast bulk of the flights by the Google executives’ fleet have been for non-NASA purposes.
The main jets in the fleet—a Boeing 767, Boeing 757 and four Gulfstream V’s—have departed from Moffett a total of 710 times since 2007, FAA records show. The most frequent destinations were Los Angeles and New York, but the planes also flew 20 times to the Caribbean island of Tortola; 17 to Hawaii; 16 to Nantucket, Mass.; and 15 to Tahiti.
This agreement went into place before Google joined PRISM, for example (though I’m sure Google was already helping NSA on its storage challenges before that). Though I really look forward to Google defending these fuel purchases because so much of what they do is “for performance of a U.S. government contract.”
This is peanuts to a company as rich as Google; access to the airport is probably worth more to Google execs than the cheap gas.
Still, it’s a perk. The kind of perk that might explain why Eric Schmidt believes all this spying is just the nature of society. (h/t Kevin Gosztola)
There’s been spying for years, there’s been surveillance for years, and so forth, I’m not going to pass judgment on that, it’s the nature of our society.
Spying is the nature of society in the same way as special perks for those who help in it, after all.
