NSA’s Privacy Officer Exempts Majority of NSA Spying from Her Report on EO 12333 Collection
NSA’s Director of Civil Liberties and Privacy, Rebecca Richards, has another report out, this time on “Civil Liberties and Privacy Protections” provided in the Agency’s EO 12333 programs. As with her previous report on Section 702, this one is almost useless from a reporting standpoint.
The reason why it is so useless is worth noting, however.
Richards describes the scope of her report this way:
This report examines (1) NSA’s Management Activities that are generally applied throughout the Agency and (2) Mission Safeguards within the SIGINT mission when specifically conducting targeted3 SIGINT activities under E.O. 12333.
3 In the context of this paper, the phrase “targeted SIGINT activities” does not include “bulk” collection as defined in Presidential Policy Directive (PPD)-28. Footnote 5 states, in part, “References to signals intelligence collected in ‘bulk’ mean the authorized collection of large quantities of signals intelligence data which, due to technical or operational considerations, is acquired without the use of discriminants (e.g., specific identifiers, selection terms, etc.).”
Richards neglects to mention the most important details from PPD-28 on bulk collection: when collection in “bulk” is permitted.
Locating new or emerging threats and other vital national security information is difficult, as such information is often hidden within the large and complex system of modern global communications. The United States must consequently collect signals intelligence in bulk5 in certain circumstances in order to identify these threats. Routine communications and communications of national security interest increasingly transit the same networks, however, and the collection of signals intelligence in bulk may consequently result in the collection of information about persons whose activities are not of foreign intelligence or counterintelligence value. The United States will therefore impose new limits on its use of signals intelligence collected in bulk. These limits are intended to protect the privacy and civil liberties of all persons, whatever their nationality and regardless of where they might reside.
In particular, when the United States collects nonpublicly available signals intelligence in bulk, it shall use that data only for the purposes of detecting and countering: (1) espionage and other threats and activities directed by foreign powers or their intelligence services against the United States and its interests; (2) threats to the United States and its interests from terrorism; (3) threats to the United States and its interests from the development, possession, proliferation, or use of weapons of mass destruction; (4) cybersecurity threats; (5) threats to U.S. or allied Armed Forces or other U.S or allied personnel; and (6) transnational criminal threats, including illicit finance and sanctions evasion related to the other purposes named in this section. In no event may signals intelligence collected in bulk be used for the purpose of suppressing or burdening criticism or dissent; disadvantaging persons based on their ethnicity, race, gender, sexual orientation, or religion; affording a competitive advantage to U.S. companies and U.S. business sectors commercially; or achieving any purpose other than those identified in this section.
5 The limitations contained in this section do not apply to signals intelligence data that is temporarily acquired to facilitate targeted collection. References to signals intelligence collected in “bulk” mean the authorized collection of large quantities of signals intelligence data which, due to technical or operational considerations, is acquired without the use of discriminants (e.g., specific identifiers, selection terms, etc.).
The NSA collects in “bulk” (that is, “everything”), temporarily, to facilitate targeted collection. This refers to the 3-5 day retention of all content and 30 day retention of all metadata from some switches so XKeyscore can sort through it to figure out what to keep.
And the NSA also collects in “bulk” (that is, “everything”) to hunt for the following kinds of targets:
- Spies
- Terrorists
- Weapons proliferators
- Hackers and other cybersecurity threats
- Threats to armed forces
- Transnational criminals (which includes drug cartels as well as other organized crime)
Of course, when NSA collects in “bulk” (that is, “everything”) to hunt these targets, it also collects on completely innocent people because, well, it has collected everything.
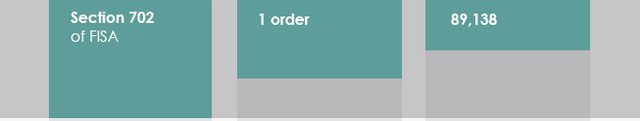
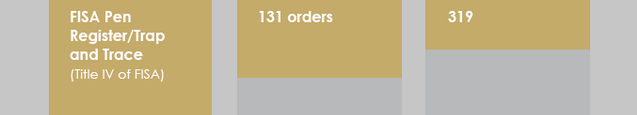
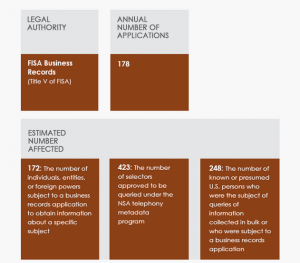
So at the start of a 17-page report on how many “civil liberties and privacy protections” the NSA uses with its EO 12333 collection, NSA’s Privacy Officer starts by saying what she’s about to report doesn’t apply to NSA’s temporary collection of everything to sort through it, nor does it apply to its more permanent collection of everything to hunt for spies, terrorists, weapons proliferators, hackers, and drug bosses.
That is, the “civil liberties and privacy protections” Richards describe don’t apply to the the great majority of what NSA does. And these “civil liberties and privacy protections” don’t apply until after NSA has collected everything and decided, over the course of 5 days, whether it wants to keep it and in some places, kept everything to be able to hunt a range of targets.
This actually shows up in Richards’ report, subtly, at times, as when she emphasizes that her entire “ACQUIRE” explanation focuses on “targeted SIGINT collection.” What that means, of course, is that process, where collecting only takes place after an NSA analyst has targeted the collection? It doesn’t happen in the majority of cases.
Once you collect and sort through everything, does it really make sense to claim you’re providing civil liberties and privacy protections?