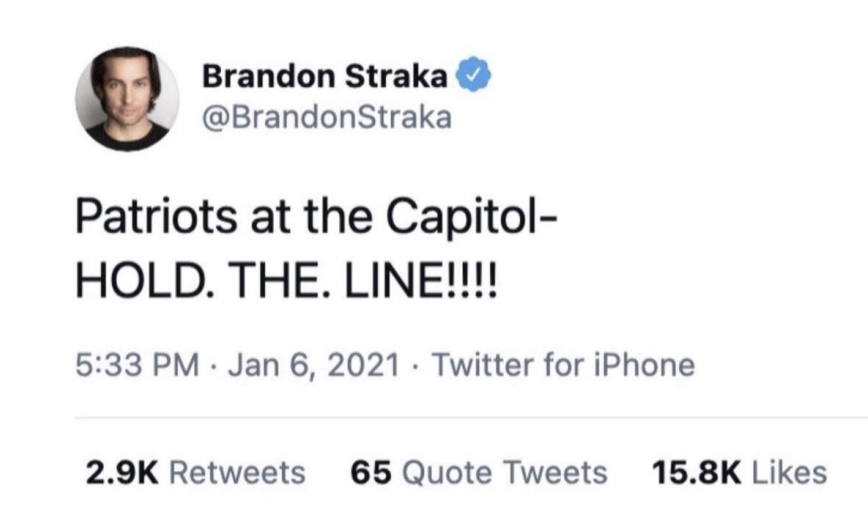
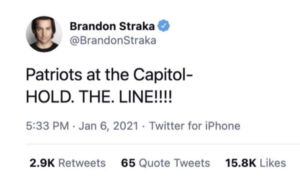
“HOLD. THE. LINE!!!” DOJ’s Late Research into Brandon Straka’s Grift
It’s difficult to tell what really went down with the Brandon Straka plea.
That’s because — as laid out here — the government seems to have realized that Straka had been less than forthright in interviews, in which he was deemed cooperative last year, that got him a sweet plea deal. In their sentencing memo, the government seems to be at pains to argue that Straka’s cooperation was worth minimizing his overt incitement of the obstruction attempts.
Straka, meanwhile, is desperate to dismiss claims he “snitched” out others. So it’s unclear what to make of the claim — in a memo signed by Bilal Essayli, a California politician who only just filed his notice of appearance in the case — that the government was pressuring Straka to implicate Trump directly.
During the interviews the government was focused on establishing an organized conspiracy between defendant, President Donald J. Trump, and allies of the former president, to disrupt the Joint Session of Congress on January 6. Defendant answered all questions truthfully and denied the existence of any such plot. In August 2021, the FBI arrived at the same conclusion and found no evidence that violence was centrally coordinated by any individual or group.2 Despite these findings, the government persists with a false narrative that defendant’s actions were premeditated and orchestrated in concert with the greater mob that stormed the Capitol. The Court should reject this improper attempt to expand the scope of the appropriate sentencing factors, and consider only defendant’s relevant conduct with respect to the charged offense: misdemeanor disorderly conduct.
2 See Mark Hosenball, Exclusive: FBI finds scant evidence U.S. Capitol attack was coordinated – sources, Reuters, August 20, 2021, https://www.reuters.com/world/us/exclusive-fbi-finds-scant-evidence-us-capitol-attack-wascoordinated-sources-2021-08-20/
In an attempt to disclaim any organized conspiracy, Essayli cites the problematic Reuters article based on former officials who would have been in charge during the period when Straka’s initial interviews were deemed cooperative, but whose knowledge by August 2021 would have been out of date and whose claims would be utterly irrelevant to what DOJ understood by December, when Straka’s sentencing took a weird turn.
Even crazier, the Straka sentencing memo reveals that, on December 10 (so two days after Straka revealed new information that roiled the sentencing), his team shared a sentencing position with DOJ asking not just for no jail time, but to have the entire case dismissed.
Defendant feels compelled to respond on the record to the government’s sentencing memorandum, which was filed one week prior to the sentencing hearing. The government had the benefit of reading and considering defendant’s sentencing position, which was timely filed on December 10, 2021, when drafting its position. The government missed this deadline and informed defendant the following day that it was seeking to continue the sentencing hearing. The government sought a stipulation to continue, which defendant agreed to join, based on the government’s representation that it would consider a request from defendant to dismiss this case. The government informed defendant on January 13, 2022, that his request was denied and proceeded to file its sentencing position containing highly inflammatory characterizations of defendant. [my emphasis]
Since December, it seems Straka has given up that plan, because his attorneys now argue for “a modest non-custodial sentence.”
That said, much of the rest of the memo focuses on making a First Amendment argument claiming that Straka’s earlier posts (it is silent about his January 5 speech) don’t amount to incitement.
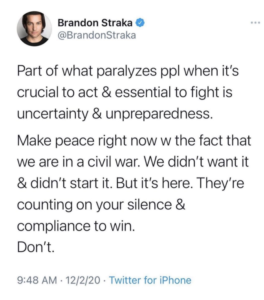
The first and second tweet sent in early December 2020 were a pair of strongly worded messages opposing the transition to President Biden without an audit of contested election results. Gov. Figure A and B. Defendant states, “If we don’t get a thorough audit we must not allow a transfer.” The references in the tweet to a “civil war” was not a call to violence, as the government suggests, it was a figure of speech referencing a political struggle. The government concedes that defendant’s “messages contain rhetorical flourishes that are common in political speech,” but then suggests, without evidence, that defendant’s statements could “have been interpreted by some readers as a call for more than just a figurative struggle.” ECF 36, p. 5. The government does not cite one example of defendant’s tweets influencing a single person to engage in criminal conduct.
Similarly, Gov. Figure C contains a tweet from December 19, 2020, with a call to “rise up” (figuratively) and be recognized by the government. The full statement reads, “Our government no longer listens & takes instructions from the People. They’ve decided to become dictators to the People. It’s time to rise up!” This is precisely the category of speech the First Amendment protects. It is not incitement, and barely registers above heated political rhetoric. See generally Cohen v. California, 403 U.S. 15, 24–26 (1971). It was also not imminent—being issued almost a month prior to January 6. See Brandenburg v. Ohio, 395 U.S. 444, 448 (1969) (First Amendment prohibits punishment of advocacy except when it incites imminent unlawful action).
The government’s sentencing memorandum is devoid of any mention of the First Amendment, let alone any analysis of whether defendant’s statements meet the Brandenburg standard required for punishing speech. The government may only punish protest-related speech that includes a direct “call to violence” or advocacy that is “directed to inciting or producing imminent lawless action and is likely to incite or produce such action.” See Brandenburg, 395 U.S. at 447; Noto v. U.S., 367 U.S. 290, 297–300 (1961). At the same time, the Supreme Court has consistently protected the statement of an idea that “may prompt its hearers to take unlawful action. . . .” Noto, 367 U.S. at 297 (quoting Dennis v. U.S., 341 U.S. 494, 545 (1951) (Frankfurter, J., concurring)). Indeed, even a protestor screaming, “We’ll take the f***ing street again” amidst an agitated crowd resisting police authority could not be punished for his speech. Hess v. Indiana, 414 U.S. 105, 107 (1973). The government fails to distinguish this important constitutional divide and, by so doing, seeks to penalize protected advocacy.
None of defendant’s statements meet the test for a “call to violence” as the government suggests. They lack any specific call to violence (hypothetically, “People, find a police officer and bash his head in!” or “Attack Senator John Doe now!”). They are not particular in that they do not ask protestors to take unambiguous actions or engage in detailed criminal acts. They are not imminent—the quoted material occurred a month before the January 6 event. And whatever the government believes defendant communicated to his supporters remains an inkblot in a constitutional Rorschach test. The speech that the government finds objectionable remains protected advocacy, and should not be considered for purposes of sentencing.
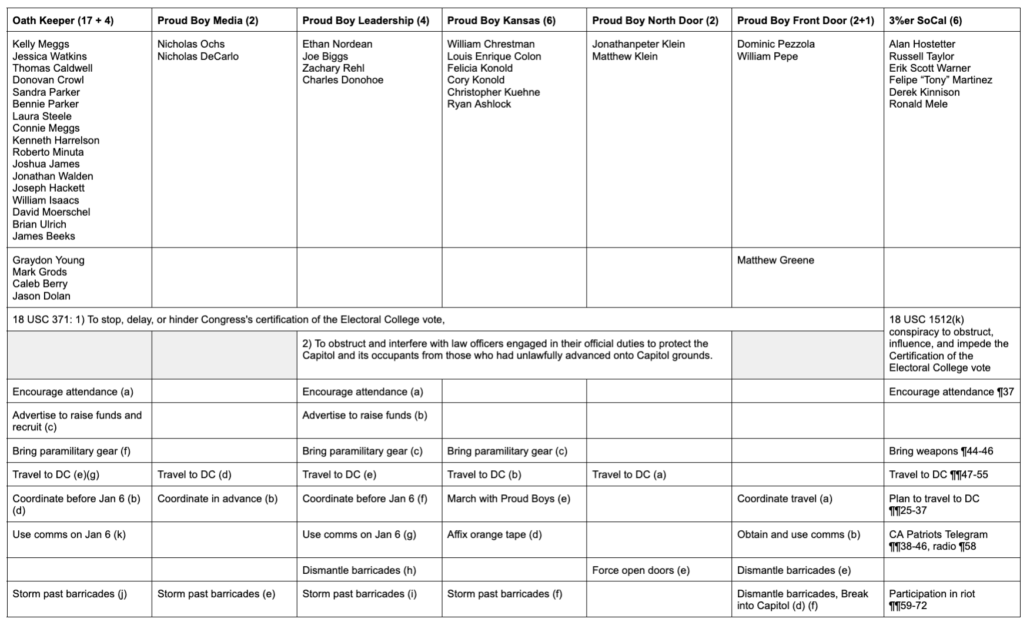
There are four attorneys who have filed notices of appearance for Straka. Not a single one has dealt with a prior January 6 defendant. So they may genuinely not know that DOJ has routinely turned to a defendant’s earlier speech to get not to incitement (militia defendants are an exception), but to motive.
And many of the other explanations Straka offers for his inflammatory language on January 6 don’t make sense (and has already been admitted at sentencing for dozens of other defendants). Straka’s team suggests that his incitement — as he was watching and cheering rioters strip a cop of a riot shield — couldn’t have encouraged the violence he was watching because his “social media posts were similarly written before defendant saw television footage of the west side of the Capitol,” as if there weren’t tons of things to alert him to the danger (even assuming he didn’t know of the collaboration between his associates and the organized militias) without seeing the West side.
Straka’s team seems to have gone from thinking they could get this entire case dismissed to being really worried about incitement that, through their good lawyering and possibly a lack of candor, hasn’t been charged against Straka.
Which brings me to a final detail of this exchange made visible by the timeline laid out in Straka’s filing.
As laid out below, after Straka’s presentence report came in, DOJ swapped prosecutors, April Russo for Brittany Reed (who wrote the sentencing memo). That presentence report, which is one of two things that changed DOJ’s response to sentencing, is referred to at least nine times in the government sentencing memo, though not at all in Straka’s.
The presentence report, for example, is what the government cites for Straka’s self-serving concern about how the prosecution affected his grifting.
During a presentence interview with U.S. Probation, the defendant expressed remorse for his actions. During his interview, the defendant stated that “if he could go back in time, he would never have gone to Washington D.C.” Straka described his conduct on January 6 as “one of the stupidest and tragic decisions of his life.” Straka lamented about how this incident has impacted his life and his business. He also informed U.S. Probation that he “feels the consequences for his actions have been quite extreme and disproportionate given his involvement in the offense is a misdemeanor.”
[snip]
Yet, it is worth pointing out that Straka believes that “the consequences for his actions this far have been quite extreme and disproportionate given his involvement.” Straka also believes that he is misunderstood. He has also expressed concern about how his business has been affected. ECF 28 ¶¶ 23-25. These statements indicate that Straka does not understand the gravamen of his conduct and that of the rioters on January 6.
The presentence report is also, alarmingly, the only place DOJ cites to explain Straka’s unique grift or that he flew to DC for the insurrection directly from doing similar incitement in Georgia.
It was in this context that Straka traveled to Washington D.C. on January 4, 2021, from where he had been working on the special election in Atlanta, Georgia to attend several “Stop the Steal” events where he would be a featured speaker. See ECF 28 at ¶ 17.
His role in the TCF mob in Michigan is not mentioned at all.
After that presentence report, the swapping of prosecutors, and the new information Straka provided on December 8, Straka’s team told DOJ they were going to ask to have the prosecution dismissed. That’s when the government told Straka they wanted a delay. Straka’s description of the timing of this is not entirely consistent with what shows in the docket (for example Judge Friedrich, with no public explanation, extended the deadline for the sentencing memo to December 15 on December 8, the day Straka provided new information), but there also seem to be several sealed entries. And while Straka claims DOJ told them they wanted a delay on December 11, the motion to continue describing the new information on December 8 and the presentence report is formally filed on December 17.
On December 8, 2021, the defendant provided counsel for the government with information that may impact the government’s sentencing recommendation. Additionally, the government is requesting additional time to investigate information provided in the Final PreSentence Report. Because the government’s sentencing recommendation may be impacted based on the newly discovered information, the government and defendant request a 30-day continuance of this case so that the information can be properly evaluated.
That makes what DOJ spent December 16 doing all the more interesting.
DOJ describes accessing the following materials on December 16, the day before they asked for a continuance:
- Straka’s June 29, 2018 YouTube video claiming to be a former Democrat
- The WalkAway Foundation website describing Straka’s 501(c)(3) status
- The WalkAway Campaign PAC website
- The WalkAway Twitter channel
- The June 25, 2021 ProPublica article about the panic among some Trump flunkies about Alex Jones and Ali Alexander’s role in January 6 events
The government cites the latter article — and not communications obtained directly by the FBI — to explain how Straka learned that his speech would be “delayed.”
At 2:33 pm on January 6, 2021, Michael Coudrey, the national coordinator for Stop the Steal, sent a message to a group chat telling those in the chat that the event that Straka was scheduled to speak at would be delayed because “They stormed the capital[sic].” Joshua Kaplan and Joaquin Sapien, New Details Suggest Sernior Trump Aides Knew Jan. 6 Rally Could Get Chaotic, ProPublica (June 25, 2021) available at https://www.propublica.org/article/new-details-suggest-senior-trump-aides-knew-jan-6-rally-could-get-chaotic (last visited December 16, 2021). Straka responded, “I just got gassed! Never felt so fucking alive in my life!!!” Id.
The government didn’t cite Straka’s November text messages (cited directly in the article) expressing disgust with close Ali Alexander ally Nick Fuentes.
Nor do they describe that Ali Alexander was on the group chat via which Straka learned his event would be delayed, or that shortly after Straka reveled in getting tear gassed, Alexander instructed everyone on the list to “get out of there” because “the FBI is coming hunting.”
“They stormed the capital,” wrote Stop the Steal national coordinator Michael Coudrey in a text message at 2:33 p.m. “Our event is on delay.”
“I’m at the Capitol and just joined the breach!!!” texted Straka, who months earlier had raised concerns about allying with white nationalists. “I just got gassed! Never felt so fucking alive in my life!!!”
Alexander and Coudrey advised the group to leave.
“Everyone get out of there,” Alexander wrote. “The FBI is coming hunting.”
Both the fact that Straka remained on organizing lists with Alexander months after he expressed distaste for Fuentes’ homophobia and that Alexander warned that the FBI were on their way change the import of everything else Straka did. Of particular note, it would dramatically change the connotation of Straka calling, from the safety of some distance from the crime scene, on others to “HOLD. THE. LINE!!!!”
And if DOJ really didn’t understand Straka’s grift until this point, that would suggest they made a plea deal without understanding that Straka was closely tied to those it is now investigating for coordinating with the militias who attacked the Capitol.
Brandon Straka claims he was asked, but denied, that there was, “an organized conspiracy between defendant, President Donald J. Trump, and allies of the former president, to disrupt the Joint Session of Congress on January 6.” But it appears that one thing leading to the month-long delay in his sentencing was newfound understanding both of Straka’s grift, but also of his close ties to those who coordinated with organized militias to end up precisely where Straka did: inciting violence from the top of the East steps of the Capitol.
Given that, his worries about whether his language counts as incitement seem misplaced. While he is legally in the clear for anything pertaining to January 6 (unless he lied to FBI), he should be more worried about inclusion in charges tied to the conspiracy he claims he denied.
Update: This language, from the Jan 6 Committee subpoena letter to Nick Fuentes, is of interest for the way it overlaps with Straka’s trajectory.
On November 14, 2020, you rallied with America First/Groyper followers at the Million MAGA March in Washington, D.C., urging your followers to “storm every state capitol until January 20, 2021, until President Trump is inaugurated for four more years.”5 You were also a prominent figure at “Stop the Steal” rallies in Atlanta, Georgia, on and around November 19, 2020,6 alongside featured speakers such as Alex Jones and Ali Alexander inside and outside the State Capitol, 7 where you discussed potential actions including showing up outside the homes of politicians. 8 On December 12, 2020, you spoke to a crowd of supporters at the “Stop the Steal” events in Washington, D.C., calling for the destruction of the Republican Party for failing to overturn the election.9
Timeline
January 11, 2021: Tip on Straka’s post to Twitter
January 13, 2021: Interview with Straka relative
By January 13, 2021: Straka removes January 5 video from Twitter; last view date for December 19, 2020 video cited in sentencing memo but not arrest affidavit
January 20, 2021: Straka charged by complaint
January 25, 2021: Straka arrest
February 17, 2021: First FBI interview
February 18, 2021: First continuance
March 25, 2021: Second FBI interview
June 3, 2021: Second continuance
July 2, 2021: Protective order
August 25, 2021: Third continuance
August 31, 2021: Date of plea offer
September 14, 2021: Deadline to accept plea
September 15, 2021: Straka charged by information
September 30, 2021: Stuart Dornan files notice of appearance for Straka
October 5, 2021: Updated information
October 6, 2021: Change of plea hearing (plea agreement; statement of offense); sentencing scheduled for December 17, with initial memo due December 10 and response due by December 15
Between October 7 and November 19, 2021: Pretrial services interview (sealed docket #28)
November 19, 2021: Brittany Reed substitutes for April Russo
December 8, 2021: Sentencing reset for December 22; sentencing memo due by December 15; Straka “provide[s] counsel for the government with information that may impact the government’s sentencing recommendation”
December 10, 2021: Straka shares sentencing position (possibly filed under seal)
December 11, 2021: Government tells defendants it seeks to continue, tells Straka it will consider request to dismiss case
December 16, 2021: Last view date for 2018 Straka video, Walkaway Foundation website, WalkAway Campaign PAC website, WalkAway Campaign YouTube Channel; ProPublica article on Michael Courdrey message (and attempts to distance Alex Jones and Ali Alexander)
December 17, 2021: Motion to continue (presented as joint) 30 days
By December 23, 2021: Sealed motion attempting to seal publicly filed motion to continue, denied by Judge Friedrich
January 5, 2022: Third FBI interview, this time including prosecutors (plural)
January 13, 2022: Government sentencing memo (sealed addendum at docket #37); government denies Straka request to dismiss case
January 14, 2022: Bilal Essayli files notice of appearance for Straka