DOJ Reportedly Will Pay Ashli Babbitt’s Estate $5 Million; Claims to Have Charged LaMonica McIver
/89 Comments/in emptywheel /by emptywheelOne thing even good reporting on Stephen Miller’s attempt to deport hundreds of Venezuelans under Miller’s nested false claims that they are members of Tren de Aragua and that Tren de Aragua is a terrorist group directed by the Venezuelan government to invade the United States misses is that Miller is doing it to aid in false equivalences.
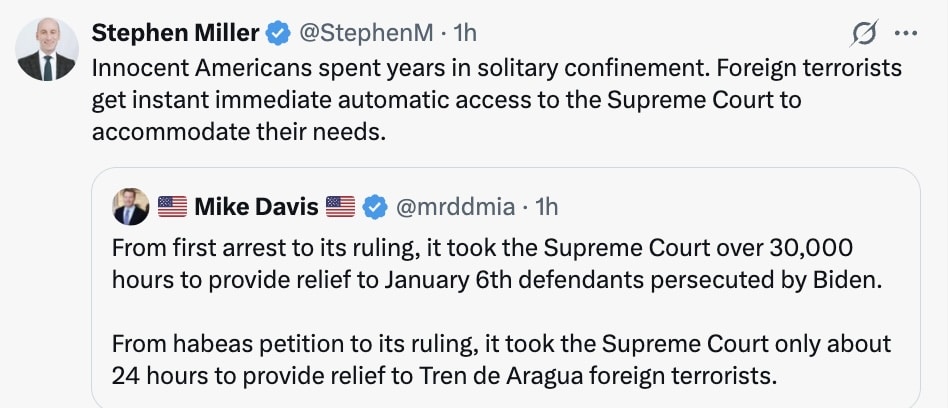
Both Miller and Trump propagandist Mike Davis illustrated this the other day.
Davis falsely claimed that the Supreme Court, in ruling against Trump’s attempt to render detainees over Easter weekend, provided habeas in just 24 hours. But, Davis claimed, it took the same court 30,000 hours to “provide relief” to Jan6ers “persecuted by Biden,” by which he meant those who were prosecuted under 18 USC 1512(c)(2).
Ultimately SCOTUS narrowed the application of the law to those who corruptly tampered with evidence involved in a proceeding. Almost everyone charged with obstruction premeditated their effort to disrupt the vote certification, to deny Joe Biden his victory and his supporters their right to have their vote counted.
Miller called these people who attacked democracy, “innocent Americans.” He, like Davis, called the Venezuelans “terrorists.”
CATO’s David Bier released a report yesterday showing that 50 of the men already sent to to Nayib Bukele’s concentration camp were not only not proven to be terrorists, but had been admitted into the United States legally. Most were detained because of their tattoos.
These legal immigrants include a temporary visa holder and four men who were authorized to travel through the US refugee program. The government vetted these refugees abroad and concluded that they would face persecution, letting them resettle in the United States. The other 45 legal immigrants scheduled appointments using the CBP One app, through which they were permitted to seek entry. Among those with appointments, 24 were paroled into the United States, where they could live and work legally for up to two years, while the other 21 were detained at the port of entry.
[snip]
These people came to the United States with advanced US government permission, were vetted and screened before arrival, violated no US immigration law, and the US government turned around and “disappeared” them without due process to a foreign prison. It is paying the Salvadoran government to continue to keep them incarcerated.
[snip]
Most, at least 42, were labeled as gang members primarily based on their tattoos, which Venezuelan gangs do not use to identify members and are not reliable indicators of gang membership. According to court documents, DHS created a checklist to determine that heavily weights “dressing” like a gang member, using “gang signs,” and, most critically, tattoos. No criminal conviction, arrest, or even witness testimony is required.
DHS’s images of “TdA tattoos” include the Jordan logo, an AK-47, a train, a crown, “hijos,” “HJ,” a star, a clock, and a gas mask. But as the American Immigration Council’s Aaron Reichlin Melnick has shown, all of these supposed TdA tattoos were not taken from Venezuelan gang members but rather stolen by DHS from social media accounts that have nothing to do with TdA or Venezuela. For instance, DHS obtained its TdA “Jordan” from a Michael Jordan fan account in the United States. It pulled its AK-47 tattoo from a Turkish tattoo artist.
Because these men were denied due process, the public had no opportunity to obtain a real accounting of any evidence against them.
By comparison, those charged with obstructing the vote count for January 6 were arrested on criminal complaints sworn out to a judge, given initial hearings, and convicted via a trial or confession. They got due process.
Stephen Miller called them innocent, even those who admitted to willfully attempting to obstruct the certification of Joe Biden’s win.
Monday, SCOTUS lifted the stay on a Temporary Postponement of Kristi Noem’s efforts to deport Venezuelans from whom Trump withdrew Temporary Protected Status. Those with individual challenges can continue their challenges but Trump can move forward with deportations.
As part of the same effort to decriminalize January 6, DOJ has agreed to pay Ashli Babbitt’s estate almost $5 million to settle a wrongful death claim related to Babbitt’s invasion of the Speaker’s Lobby where Congress was trying to escape an armed mob.
The Trump administration has agreed to pay just under $5 million to settle a wrongful death lawsuit that Ashli Babbitt’s family filed over her shooting by an officer during the U.S. Capitol riot, according to a person with knowledge of the settlement. The person insisted on anonymity to discuss with The Associated Press terms of a settlement that have not been made public.
The settlement would resolve the $30 million federal lawsuit that Babbitt’s estate filed last year in Washington, D.C. On Jan. 6, 2021, a Capitol police officer shot Babbitt as she tried to climb through the broken window of a barricaded door leading to the Speaker’s Lobby.
The officer who shot her was cleared of wrongdoing by the U.S. Attorney’s office for the District of Columbia, which concluded that he acted in self-defense and in the defense of members of Congress. The Capitol Police also cleared the officer.
This is Trump’s goal, Stephen Miller’s goal; it is how Miller got Trump elected. Trump has always claimed investigations into himself and his mob were unjust, but his own investigations into Joe Biden’s kid and before that Hillary Clinton was a hunt for corruption.
Trump’s power rests on claiming up is down, attacks on the US are noble and the defense of rule of law is a crime, accountability for anyone on his team is unjust.
Finally, today, Alina Habba announced on Xitter (nothing appears to be filed yet) that she is dismissing the petty trespassing case against Newark Mayor Ras Baraka “for the sake of moving forward” — or, more likely, because video evidence shows that when he was asked to leave Delaney Hall, he did so, and only after that was he arrested. But in the same statement, Habba announced she was has charged Congresswoman LaMonica McIver, who was shoved while she was objecting to the arrest of Newark’s mayor, which right wingers describe as an attempt to body slam the cops arresting Baraka. McIver is being charged with the same assault charge used against hundreds of Jan6ers who have since been pardoned for their crimes.
Habba claims she,
persistently made efforts to address these issues without bringing criminal charges and [has] given Representative McIver every opportunity to come to a resolution, but she has unfortunately declined.
Uh huh. McIver probably declined to do what CBS is about to, to falsely admit guilt when there is none. In a statement, McIver called the charges political.
McIver, D-10th Dist., called the charges filed by Habba, an appointee and former lawyer for President Donald Trump “purely political.”
“Earlier this month, I joined my colleagues to inspect the treatment of ICE detainees at Delaney Hall in my district,” McIver said in a statement. “We were fulfilling our lawful oversight responsibilities, as members of Congress have done many times before, and our visit should have been peaceful and short.
“Instead, ICE agents created an unnecessary and unsafe confrontation when they chose to arrest Mayor Baraka. The charges against me are purely political—they mischaracterize and distort my actions, and are meant to criminalize and deter legislative oversight.”
The charge comes amid a WaPo report that Pam Bondi is (was?) considering eliminating the requirement that investigations into Members of Congress and other public officlas involve DOJ’s Public Integrity Division. The Division would have, in this case, warned DOJ officials that in past cases (most notably with people like Scott Perry and Jim Jordan) DOJ determined charges for such actions might violate separation of powers.
Trump not only doesn’t care about things like that, infringing on Congress’ powers is the point.
As I said to Nicole Sandler Friday, Trump was always going to find a way to charge a Member of Congress, just like he found a way to charge a judge. Habba has done so here where McIver has a clear immunity claim, and has done so as someone who clearly has conflicts. Habba’s statement lacks DOJ’s boilerplate comment asserting that charges are just allegations. And the siren in her tweet will add to any claim McIver makes that this violates due process.
Sure, Habba claims she tried to avoid this. But the entire scene at Delaney Hall was designed to elicit such confrontation, to create nesting legal attacks out of which Stephen Miller can spin his lies.
These developments are all of a piece. They are all an effort — one Trump has been pursuing for a decade — to replace rule of law with rule of mob.
Journalists’ Persistent Willingness to Chase Trump’s Squirrels, Biden Recording Edition
/27 Comments/in emptywheel /by emptywheelTo get a sense of how much releasing recordings of Rob Hur’s interview with Joe Biden in advance of the legal release of them was about attention management, you need look no further than the Fox News homepage (this was from shortly after midnight ET).
The humiliating defeat for Donald Trump’s One Big Beautiful Bill in the House? Buried on the bottom of the front page.
The Supreme Court’s ruling protecting due process rights for those Trump tried to render to El Salvador using an Alien Enemies Act, which made it clear at least two Republican justices believe they can’t trust the Trump Administration? Second row.
Judge Paula Xinis’ rebuttal of DOJ’s claims that deporting Kilmar Abrego Garcia without a warrant, in spite of an order prohibiting it, was legal? Third row down.
A clip from the exclusive interview Bret Baier had with the President, in which Trump falsely claimed China needed to make a deal more than he did and bizarrely refused to say the work “nuclear”? Also buried there on the bottom.
For Fox News, a cherry-picked excerpt of Robert Hur’s interview of President Biden merited the entire top of the page, with six different stories based on that cherry-picked release to Marc Caputo and Alex Thompson.
Biden.
Biden.
Biden.
Biden.
Biden.
Biden.
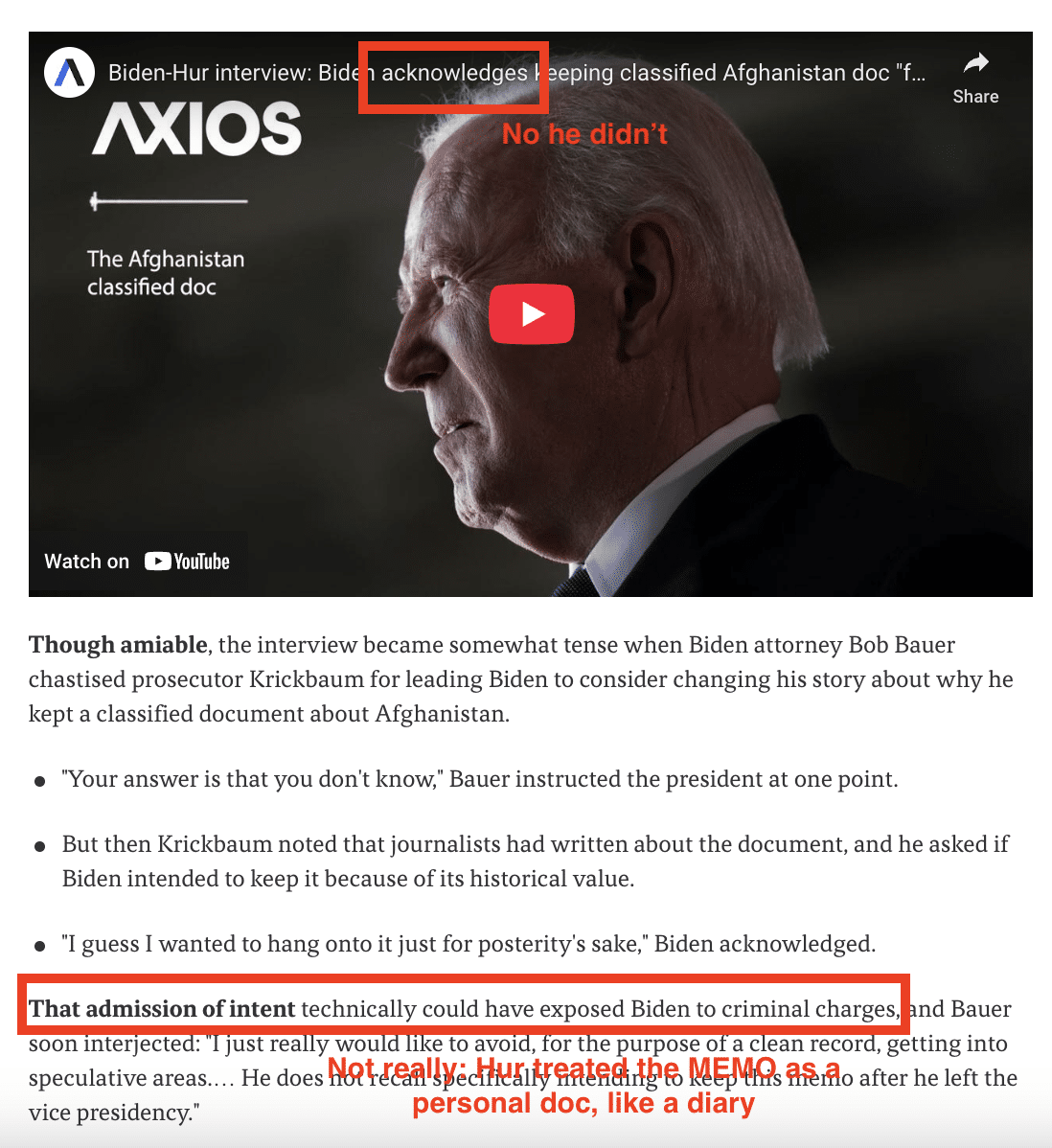
Other outlets weren’t much better. While Caputo and Thompson misrepresented the Hur investigation and the reason wby Bob Bauer would object to Hur and Marc Krickbaum’s persistent request that Biden speculate, presumed that Biden did intentionally keep classified documents not covered by a personal use exemption, and made false claims about Biden “acknowledging” that he kept a document he viewed to be classified, they were diligent about two other points.
They described that “overall [Biden] was engaged in the interview” and admitted that the interview took place immediately after the October 7, 2023 attack on Israel.
Reality check: While Biden had clear memory lapses and needed assistance at times (with words such as “fax machine” and “poster board”), overall he was engaged in the interview.
- He cracked jokes and made humorous asides, and was able to respond to the general gist of the questions. But he had little memory of how he came to have classified documents after he left office as vice president.
- On Oct. 8 — the first day of the interview and the day after Hamas’ attack on Israel — Biden often was slow and forgetful of basic facts.
- That day, it took Hur more than two hours to clearly determine how the documents could have ended up in various personal desks and file cabinets after Biden left office. That was because Biden kept veering into other subjects.
- On Oct. 9, however, Biden sounded much more engaged and vigorous.
When the full recording is released, it will show the ways that old geezer Biden caught prosecutors trying to sandbag him, parts of the interview wildly inconsistent with Thompson’s little project (not unlike the time Thompson screencapped himself ignoring evidence that Hunter Biden’s plight, not necessarily age, may have explained Biden’s very worst collapses).
Indeed, the fact that two rabid sensationalists only presented eight minutes of recording out of five hours to back their claims may explain why these recordings got released in advance — to undercut the possibility that the recordings would instead undermine the claims Hur and everyone else made about Biden (as DOJ’s release of the transcript on the eve of his testimony did).
But the people who leapt on these cherry-picked recordings were even less responsible than Caputo and Thompson.
[!!!]
CNN, Politico, NYT, and NBC didn’t mention the Israeli attack the day before. Politico and NBC did not explain that Axios released just 8 minutes of recording (CNN did, as did a second NYT story). And yet, presumably not having reviewed the full recording themselves, journalists are making claims about what the recording reveals that goes even beyond what Axios claimed.
There is a bit of news, or scandal, to this release, but it’s not covered there (or even by Axios).
Biden invoked Executive Privilege over the recordings, correctly predicting that (as Axios noted without mentioning the privilege invocation) scandal-mongers like Alex Thompson would “chop them up, distort them, and use them for partisan political purposes.”
But, as Politico acknowledged when it previewed the release weeks ago, DOJ was faced with the question of what to do with the recordings in the face of Biden’s privilege claim and DOJ’s own rationale that making recordings of voluntary interviews that then get released for partisan purposes will make people less likely to do such voluntary interviews in the future.
A deadline of sorts is approaching on May 20: In separate Freedom of Information Act lawsuits brought by conservative groups like Judicial Watch and the Heritage Foundation and various news organizations, the Justice Department has been ordered by a judge to say whether it will stand by Biden’s assertion of executive privilege to block the release of the tapes. Last May, Biden and his Justice Department claimed releasing the tapes would have a chilling effect on witnesses cooperating in high-profile investigations.
DOJ officials will also have to indicate whether they will continue to press other arguments for keeping the audio secret, including that disclosure would invade Biden’s privacy and that it could interfere with future investigations by making high-level officials less willing to cooperate.
When Trump was asked yesterday about the release, he claimed he wasn’t involved. Pam Bondi made the decision.
Trump said Friday that White House was not directly involved in handling the disclosure.
“I haven’t looked into that. That’s up to Pam and the group,” he told reporters aboard Air Force One as he returned from the Middle East, referring to Attorney General Pam Bondi.
If no one at the White House was involved, it would be fairly big news. It would mean someone other than the President or his surrogate (like White House Counsel David Harrington) had simply blown off the privilege invocation of a prior President.
By contrast, Biden’s DOJ overrode Trump’s own privilege invocations in conjunction with January 6 in one of two ways. For matters pertaining to the investigative materials held by the Archives, Biden himself waived privilege based on what Congress asked for; there’s no record DOJ obtained information outside this scope, meaning there’s no record that Merrick Garland shared any information about the criminal investigation with the President. For waivers of privilege pertaining to interviews with Trump’s aides, DOJ got Biden’s White House Counsel to make the waivers.
But as far as we know, the Biden White House always made the waivers, an Executive finding that a waiver overrode whatever concerns his predecessor might have about privilege.
Here, Trump is at least claiming that he wasn’t involved, effectively ceding the very concept of privilege to DOJ.
To be clear, critics of Biden were absolutely justified in claiming that the release of the transcript effectively waived privilege, and it may be that DOJ simply adopted that argument. But the legal basis matters, especially coming from a guy who won’t stop complaining about an investigation in which DOJ spent ten months carefully working through Trump’s privilege claims.
And the pre-release of these recordings to a White House mouthpiece and a lead Dick Pic sniffer was bound to maximally serve scandal.
It is an utterly masterful example of playing the press, of eliciting precisely the same kind of shitty reporting right wingers claim they’ve shown. Because most of the people commenting on these excerpts exhibit no awareness Biden matched the wits the much younger prosecutors in other parts of the interview.
Update: Heritage, which was suing to release the recording, is pissed about Thompson’s cherry picking.
The American people must take the snippets leaked to Axios and have apparently been spliced without notation; not the true accounting which Heritage Plaintiffs seek to provide. In the hours since the Axios release, the news has been plastered with the Axios clips. They are everywhere; apparently all concede the voices match the interview participants; they may have even been officially released. Axios released approximately 14 minutes and 28 seconds of the nearly five-and-a-half hours of President Biden’s interview with Special Counsel Hur. The media has created a running narrative about President Biden’s mental fitness based on less than 4.5 percent of the entire interview.
Since I posted this, Thompson has made the full 5+ hours available.
Trump Confesses Migrants Aren’t the Criminals He Claimed They Are
/36 Comments/in emptywheel /by emptywheelThere’s a story that largely faded into the non-stop stream of stories about corrupt things DOJ is doing under Pam Bondi (or, as this NYT profile of Bondi admits, Stephen Miller’s watch). Reuters first reported it, but NBC’s story is more comprehensive.
The FBI has ordered field offices to shift a significant number — almost half, in some offices — of agents from hunting crime to hunting migrants.
FBI field offices around the country have been ordered to assign significantly more agents to immigration enforcement, a dramatic shift in federal law enforcement priorities that will likely siphon resources away from counterterrorism, counterintelligence and fraud investigations, multiple current and former bureau officials told NBC News.
[snip]
The shift in resources spans the country, according to two FBI officials. In a major change, 45% of all agents in the 25 largest FBI field offices will be working on immigration full time.
The bureau’s Atlanta field office will assign 67 agents to work on immigration “enforcement and removal operations” full time, seven days a week, the officials said. That is around half of all the agents assigned to the Atlanta field office headquarters
In Los Angeles, the field office is creating nine squads to address enforcement and removal operations full time. They will pursue noncitizens who have overstayed their visas, even if they have no criminal history.
And the FBI’s Boston field office was ordered to assign an additional 33 special agents to immigration enforcement.
[snip]
Given that FBI resources are finite, current and former officials say, a significant increase in immigration enforcement will draw agents away from what have long been top FBI priorities, including counterterrorism, counterespionage, fraud and violent crime. [my emphasis]
The story appeared amid a parallel story that DHS has asked DOD for 20,000 National Guard members to deploy to American neighborhoods.
Regarding the FBI shift, NBC focuses on how this will require the FBI to pull agents from investigating crimes, including terrorism and violent crime: the opportunity cost of doing this, and implicitly, the likelihood that FBI will miss terrorists or spies.
But consider what this says. FBI says they aren’t finding enough migrants to deport by looking for criminals, even by looking for the kinds of crimes that Trump and Stephen Miller have been claiming, for years, migrants commit.
FBI is not finding migrants by looking for terrorists.
FBI is not finding migrants by looking for rapists.
FBI is not finding migrants by looking for murderers.
As a POGO column yesterday noted, CBP is also not finding drug dealers when finding migrants.
Of the over 5.8 million migrants stopped by Border Patrol between fiscal years 2022 and 2024, drugs were seized from only 249 people, CBP migrant encounter data showed.
Marijuana accounted for more than half of those 249 drug seizures; just 1 in 53,965 migrants were caught with drugs other than marijuana. To put that into perspective, the odds of dying from a bee sting are 1 in 41,076.
You can’t find migrants by looking for criminals.
And so you have to move FBI agents from looking for criminals and make them search for migrants another way, for migrants as migrants, rather than for criminals.
By demanding that the FBI take agents who are currently looking for criminals and instead assign them to look for migrants, Donald Trump and Stephen Miller are confessing that migrants aren’t the criminals that Trump’s entire political career has been built on claiming they are.
The Comings and Goings from Stephen Miller’s Gulag
/58 Comments/in emptywheel /by emptywheelLet’s start with the good news, not least because the good news may explain some of the bad news.
Habeas Corpus still exists in the US
In the last several weeks, judges in Vermont and Alexandria, VA, have ordered the government to free Mohsen Mahdawi, Rumeysa Ozturk, and Badar Khan Suri from custody. Their release does not end their legal fight over whether Trump can deport them for their First Amendment protected speech or not. But they will be able to continue their academic work, live at home, and make public comments while those legal proceedings go forward.
Now the horrible news.
As noted above, some of the releases were ordered by Federal judges in Vermont — William Sessions in the case of Ozturk and Geoffrey Crawford in the case of Mahdawi.
Yesterday, detained Harvard genetics researcher Kseniia Petrova had a hearing before a third Vermont judge, Chief Judge Christina Reiss. Anna Bower live-skeeted it here.
Petrova’s case differs from the others in several ways. She wasn’t detained for her First Amendment protected speech. Rather, she was detained because she didn’t declare frog samples from France she was carrying back to Harvard for her research at the border.
And while the government’s public actions to date — a quick transfer for Petrova to Louisiana in a transparent attempt to make any habeas corpus challenge more difficult — look quite similar, the legal posture was different for several reasons: a Customs and Border Patrol Officer had reportedly canceled her visa themselves upon discovering the samples (an offense that is normally let off with a warning). Petrova had agreed to leave the country, so long as she wasn’t deported to her native Russia, where she credibly expects she’d be harshly persecuted for her speech there. Because of that threat, Petrova also started applying for asylum.
But as laid out in the hearing yesterday, Petrova had always said she’d be willing to leave for France, and the government still publicly maintained they wanted to deport her to Russia.
Judge Reiss noted that she had reviewed the statute laying out the grounds for customs officers to find someone inadmissible to the United States, and “I don’t see anything about customs violations.”
Jeffrey M. Hartman, an attorney representing the Department of Justice, said “it’s the secretary of state’s authority” to cancel a visa, and that the secretary has delegated that authority to customs officials.
“The C.B.P. office was our first line of defense against unknown biological materials from a foreign national out of a port of entry,” he said.
Mr. Hartman argued that the federal court in Vermont had no jurisdiction over Ms. Petrova’s detention. He said Ms. Petrova may contest her detention, but only in an immigration court in Louisiana, where ICE is holding her.
“It’s not something that a district court can entertain,” he said. “We think the proper venue for that question is Louisiana, where she is detained and where her custodian is.”
“But she is only detained there because you moved her,” said the judge.
Judge Reiss asked the government to clarify whether or not it planned to deport Ms. Petrova to Russia.
“You are asking for her removal to Russia?” she asked.
“Yes, your honor,” Mr. Hartman replied.
Shortly after telling Judge Reiss that the government wanted to deport Petrova to Russia, DOJ instead unsealed a criminal complaint against Petrova, obtained on Monday (the first business day after Ozturk’s release), saying they actually want to prosecute Petrova for crimes that can impose up to a 20-year sentence.
Two months after detaining Petrova, as judges in Vermont free targets of Stephen Miller’s witch hunt and as problems with the unilateral revocation of her visa become clear, the government suddenly decided Petrova engaged in smuggling, without taking the time to present the case to a grand jury first.
The key paragraph of this complaint claims that Petrova prevaricated when asked about carrying biological materials and whether she knew she had to declare them, first denying she had biological material, then admitting she did.
PETROVA was asked to present herself at the secondary inspection area. She was wearing a backpack and carrying a plastic bag. When questioned about her luggage, PETROVA denied carrying any biological material. When the CBP officer asked her again, PETROVA identified the plastic bag she was carrying as having biological material. An inspection of the bag revealed a foam box containing frog embryos in microcentrifuges, as well as embryo slides. A CBP officer interviewed PETROVA under oath and conducted a manual review of her cell phone. PETROVA admitted that the items in her duffle bag and in the plastic bag were biological specimens. PETROVA was asked if she knew that she was supposed to declare biological material when entering the United States. After a long pause, she answered she was not sure. The CBP officer then confronted PETROVA with a text message on her phone from an individual who she identified as her colleague at a Boston-area medical school, where she is currently a research assistant. The individual wrote, “if you bring samples or antibody back make sure you get the permission etc. Like that link I sent to leon-/group chat about frog embryos because TSA went through my bags at customs in Boston.” When asked again whether she knew she was supposed to declare the items, she responded that she “was not sure about embryos specifically”
Even though the government maintains that they have to deport Petrova to Russia, not France, they make much of her past work in a Russian research lab, as if she’s some Russian threat, even while treating her fear of deportation as feigned.
11. PETROVA told CBP agents that she was educated in Russia and worked at the Moscow Center for Genetics as a bioinformatician of genetic disorders from 2016 to 2023. When asked if this was a Russian government institution, she replied that about half of the scientists worked for the Russian government and the other half for hospitals. She also stated that she was most recently employed by the Institute of Genetic Biology in Moscow from 2023 to 2024.
Again, on its face, this looks like the government’s bid to ratchet up its attack in the face of embarrassing setbacks in Petrova’s case. I wonder if they would have unsealed this if not for what looked like a pending loss before Judge Reiss and possibly even this powerful op-ed from Petrova, published by NYT on Tuesday, implicitly likening the plight of scientists in Russia to increasing threats in the US.
The political environment in Russia made it hard to do science because everything was unpredictable. The war in Ukraine affected scientists’ ability to get funding and materials; we worried that our male colleagues might be conscripted. That type of uncertainty is incompatible with science, which requires the ability to plan what type of experiments and research you will do a year into the future. I fear that if I return to Russia I will be arrested.
I am hesitant to comment broadly on what it’s like for scientists now in America because I have only limited information about what is going on outside of this detention center. What I do know is that my colleagues, many of whom are, like me, foreign scientists, are terrified of being detained or having their visa status revoked.
One more thing may have convinced the government to charge Petrova, though.
As pattern jury instructions on the charge lay out, to prove the case against Petrova, the government must prove that Petrova had the intent of defrauding the government.
To find the defendant guilty of this crime you must be convinced that the government has proved each of the following beyond a reasonable doubt:
[snip]
Third: the defendant acted knowingly and willfully with intent to defraud the United States. [It is not necessary, however, to prove that any tax or duty was owed on the merchandise.]
[Fourth: the defendant did something which was a substantial step toward committing [crime charged], with all of you agreeing as to what constituted the substantial step. Mere preparation is not a substantial step toward committing [crime charged], rather the government must prove that the defendant, with the intent of committing [crime charged], did some overt act adapted to, approximating, and which in the ordinary and likely course of things would result in, the commission of [crime charged].
To act with “intent to defraud” means to act with intent to deceive or cheat someone.
To prove this, the government will have to call the people with whom Petrova discussed how to address the samples at customs.
9. Another text message on PETROVA’s phone contained the following question from her medical school colleague: “What is your plan to pass the American [referred to as US in PETROVA’s interview] Customs with samples? This is the most delicate place of the trajectory.”
10. The CBP officer confronted PETROVA with another text message between her and another individual who she identified as her principal investigator in which she was asked by this individual: “what is your plan for getting through customs with samples?” To that question, PETROVA replied, “No plan yet. I won’t be able to swallow them.
That is, this will put Petrova’s lab on trial, with her colleagues either forced to testify against her or possibly implicated with it, as if there’s some great conspiracy against the United States to … do science.
DOJ unsealed this complaint on Tuesday, after Harvard expanded its lawsuit against the US, adding the retaliation Trump has taken in response to Harvard’s initial lawsuit.
7. In response to Harvard’s defense of its own constitutional freedoms, the federal Government announced that it was freezing “$2.2 billion in multiyear grants and $60M in multiyear contract value to Harvard University” (the “April 14 Freeze Order,” attached as Exhibit C). Ex. C at 2. Within hours of the April 14 Freeze Order, Harvard began receiving stop work orders. And the situation is getting worse. On April 20, it was reported that the Government is “planning to pull an additional $1 billion of [Harvard]’s funding for health research.”6 On May 5, the Secretary of Education, purporting to speak on behalf of every agency and department, announced an “end of new grants for the University,” and directed that “Harvard should no longer seek GRANTS from the federal government, since none will be provided,” and “Harvard will cease to be a publicly funded institution” (the “May 5 Letter” or “May 5 Freeze Order,” attached as Exhibit D). Ex. D at 3-4. That announcement reiterated the Government’s earlier demands and said it was based, among other things, on the Government’s assessment of Harvard’s “academic rigor,” admissions requirements and practices, grading systems, faculty hiring, teaching, and course construction. Id. at 2. The April 14 Freeze Order and May 5 Freeze Order are collectively referred to herein as the “Freeze Orders.”
8. Following in the footsteps of the April 14 and May 5 Freeze Orders, Harvard began, starting on May 6, to receive institution-wide termination notices for various agencies, invoking the earlier April 11 and 14 communications. On May 6, for example, the National Institutes of Health sent Harvard a letter stating that it was terminating all of Harvard’s grant funding from that agency based on “the University’s unwillingness to take corrective action or implement necessary reforms” and that Harvard’s grant “awards no longer effectuate agency priorities” because of “recent events at Harvard University involving antisemitic action” and “Harvard’s ongoing inaction in the face of repeated and severe harassment and targeting of Jewish students” (the “May 6 Letter” or “May 6 NIH Termination Letter,” attached as Exhibit E). Ex. E at 2-3. The letter states that “NIH generally will suspend (rather than immediately terminate) a grant and allow the recipient an opportunity to take appropriate corrective action,” but “no corrective action is possible here.” Id. at 3.
And the escalation continues. In the last week, Trump announced more cuts on funding to Harvard as well as an EEOC investigation into a faculty that underrepresents women and people of color, claiming it discriminates against people who look like Stephen Miller.
Charging Petrova for daring to commit science in the United States is undoubtedly a way to rescue a legally problematic case against her. It’s also another way to put Harvard’s defense of scholarship on trial.
Perhaps it is an auspicious sign, then, that British professors just determined that a copy of the Magna Carta that Harvard bought for $30 in 1946, thinking it was a copy made in 1327, is in fact a seventh original of the 1300 document.
British researchers have determined that a “copy” of the Magna Carta owned by the Harvard Law School Library is a rare original issued by England’s King Edward I in 1300. The copy was previously thought to date back to 1327.
The Magna Carta, issued by King John in 1215, established that the monarch is a subject under the law, just like any other citizen. It was reissued a number of times throughout the thirteenth century, and was released for the final time with the king’s seal in 1300.
Seven original charters issued by King Edward I are known to exist. Six copies are in the United Kingdom, while Harvard Law School’s Magna Carta is now the only known copy abroad.
The discovery was made by David Carpenter, a professor at King’s College London, and Nicholas Vincent, a professor at the University of East Anglia. Carpenter, a Magna Carta expert, was researching unofficial copies of the charter and suspected the Law School’s copy was actually an original. He then worked with Vincent, another Magna Carta expert, to investigate further.
The charter, an agreement between the King of England and rebel barons, gave way to the idea of a limited government and inspired the writers of the U.S. Constitution and Bill of Rights. In a joint press release between the three universities, Vincent called it “the most famous single document in the history of the world.”
All this time, an original document enshrining habeas corpus — the legal right Petrova was asserting, the legal right that got Mahdawi, Ozturk, and Suri released, the legal right Stephen Miller wants to suspend — was sitting right there in Boston, where the fight for American freedom started.
There will be multiple other developments in Stephen Miller’s deportation regime today.
SCOTUS will review whether judges can issue nationwide injunctions on matters — birthright citizenship — that necessary apply nationwide.
Hannah Dugan
Judge Hannah Dugan will be arraigned in Milwaukee on an indictment obtained Tuesday. The indictment claims, with no context, that Dugan “falsely [told the ICE team] they needed a judicial warrant to effective the arrest of [Eduardo Flores-Ruiz].” That claim goes beyond anything mentioned in the complaint and likely misrepresents the intent of Dugan’s comment. The indictment similarly provides no context for Dugan’s order directing the ICE team to go to the Chief Judge’s office, who was still working on a policy covering such issues; nor does it mention that there was no policy that Dugan violated.
The indictment also makes clear that the grand jury obtained testimony from Flores-Ruiz’ attorney, claiming that Dugan,
advis[ed] E.F.R.’s counsel that E.F.R. could appear by “Zoom” for his next court date.
But having spoken to Flores-Ruiz’ attorney, there’s still no allegation that Dugan told her that ICE was in the courthouse. This means the government lacks that kind of evidence that might substantiate corrupt intent, making it a much weaker case than the one against Judge Shelly Joseph back in 2019.
Nothing about this case has gotten stronger at the indictment stage. It still appears to lack any evidence about Dugan’s intent.
That said, the indictment is not a ham sandwich either. The government has clearly provided probable cause that a person who knew of an administrative arrest warrant made it difficult for ICE to arrest someone.
There’s no evidence that prosecutors explained why Dugan’s question about an administrative versus judicial warrant is actually exculpatory. Likewise, there’s no evidence that prosecutors told the grand jury that two DEA agents from the ICE team had the opportunity to detain Flores-Ruiz in the hallway there were staking out. And the matter of judicial immunity, which was left for an appellate phase that never happened in Joseph’s case (the Biden DOJ dismissed the case), would not have been briefed to the grand jury.
The latter detail, judicial immunity, may be litigated more aggressively than it was for Judge Joseph because of actions Trump took.
Yesterday, Dugan filed a motion to dismiss the case based on judicial immunity. The motion cited Trump’s own successful attempt to avoid any trial based on his claim of immunity three times.
The problems with this prosecution are legion, but most immediately, the government cannot prosecute Judge Dugan because she is entitled to judicial immunity for her official acts. Immunity is not a defense to the prosecution to be determined later by a jury or court; it is an absolute bar to the prosecution at the outset. See Trump v. United States, 603 U.S. 593, 630 (2024).
[snip]
Judge Dugan’s subjective motivations are irrelevant to immunity. “Judges are entitled to absolute immunity for their judicial acts, without regard to the motive with which those acts are allegedly performed.” Id.; accord Trump v. United States, 603 U.S. at 618 (“In dividing official from unofficial conduct, courts may not inquire into the President’s motives”).
[snip]
Judge Dugan therefore has both immunity from conviction and immunity from prosecution. “The essence of immunity ‘is its possessor’s entitlement not to have to answer for [her] conduct’ in court.” Trump, 603 U.S. at 630, quoting Mitchell v. Forsyth, 472 U.S. 511, 525 (1985); Mitchell, 472 U.S. at 526 (“The entitlement is an immunity from suit rather than a mere defense to liability; and like an absolute immunity, it is effectively lost if a case is erroneously permitted to go to trial.”) (emphasis in original)
This last citation adopts John Sauer’s own reliance on civil, not criminal, liability. A citation to Mitchell itself would be inapt (a criticism some people are making); but Dugan is citing the current Solicitor General’s inapt reliance on it, not the case directly. Effectively, Dugan is saying that if Trump can avoid trial for anything covered by his official duties, than so can Dugan.
Ras Baraka
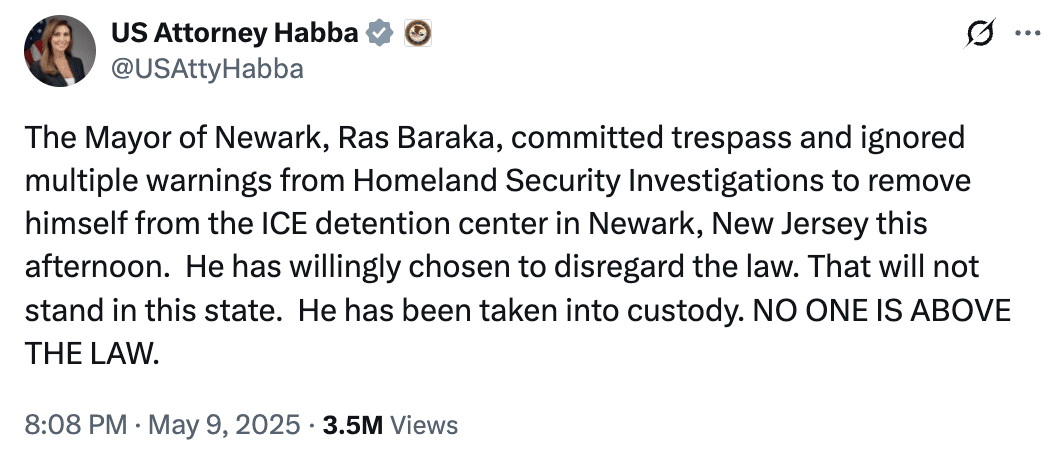
Ras Baraka will also have a hearing in his prosecution for misdemeanor trespassing today. As with Dugan’s case, there’s reason to believe Trump’s public comments about the case are overblown.
To substantiate the misdemeanor trespassing charge against him, the complaint against Newark’s Mayor does not make the claims that Alina Habba made publicly, that Baraka was repeatedly asked to leave. Rather, HSI Special Agent in Charge Ricky Patel relied only on the no trespassing signs and the presence of security guards.
3. The Delaney Hall Facility is surrounded by chain-link fences and is accessible only through granted access. In addition to maintaining security, it likewise displays No Trespassing signage.
But video shows that after security guards asked Baraka to leave (after first letting him in), he did. The arrest happened on public ground, not in the facility itself. The video undermines the complaint as attested.
In advance of today’s hearing, the AUSA who presented the case on Friday was swapped out for Alina Habba herself and another AUSA, often a sign under this Administration that an attorney wasn’t telling the lies the government wants to tell.
Having made that swap, Habba tried to get today’s hearing canceled (though she couldn’t even manage to get the date right!), so they could move right to trial.
The Government writes with respect to the upcoming preliminary hearing scheduled for Thursday, May 12, 2025. The Government does not believe that a preliminary hearing is warranted in this case. Under Fed. R. Crim. P. 5.1(a), “[i]f a defendant is charged with an offense other than a petty offense, a magistrate judge must conduct a preliminary hearing unless” certain conditions are satisfied. Fed. R. Crim. P. 5.1(a) (emphasis added). Here, the charge is a petty offense. Under state law, assimilated under 18 U.S.C. § 13, the statutory maximum sentence is 30 days. That means the offense is a class C misdemeanor under federal law. See 18 U.S.C. § 3559(a). That, in turn, means that it’s a “petty offense” under federal law. See 18 U.S.C. § 19. Defendant, therefore, is not entitled to a preliminary hearing under Rule 5.1. See United States v. Radin, No. 16 Cr. 528, 2017 U.S. Dist. LEXIS 77783, 2017 WL 2226595 (S.D.N.Y. May 22, 2017).
The Government requests that the Court cancel the preliminary hearing and schedule this matter for trial at an appropriate time. [my emphasis]
Magistrate Judge André Espinosa, to whom Patel didn’t disclose that Baraka left the facilities when asked, was having none of that. He granted Habba’s request to vacate a preliminary hearing as unnecessary, but in the same order, granted Baraka’s request for a status conference to be held at the previously scheduled time.
WHEREAS the United States of America (the “Government”), by way of a May 13, 2025 letter brief emailed to the Court and all counsel, now seeks cancellation of that hearing, arguing that it is not required under Federal Rule of Criminal Procedure Rule 5.1; and
WHEREAS the clear language of Rule 5.1(a) does not require a preliminary hearing when a defendant is charged with a petty offense; and
WHEREAS the offense charged in this action carries a maximum penalty of 30 days’ imprisonment, making it a Class C misdemeanor, see 18 U.S.C. § 3559(a), and constituting a “petty offense” under federal law. See 18 U.S.C. § 19; and
WHEREAS, nevertheless, by way of email correspondence to the Court, copying counsel for the Government, counsel for Defendant has sought a status conference on the same date and at the same time, if the preliminary hearing does not proceed; therefore
IT IS on this 13th day of May 2025,
ORDERED that the Court’s May 9, 2025 oral Order setting a preliminary hearing in this action for May 15, 2025, at 10:00 a.m., is VACATED; and it is further
ORDERED that the Court will hold a status conference in this action on May 15, 2025, at 10:00 a.m., in Courtroom 2D of the Martin Luther King Courthouse, in Newark, at which all counsel shall appear.
As Josh Gerstein observed, in last week’s hearing, in response to a request from Baraka, Espinosa issued a warning about public statements that violate local rules.
COME ON ALINA — In Baraka hearing, magistrate cautioned federal officials about public statements, by POLITICO’s Ry Rivard and Josh Gerstein: Before Newark Mayor Ras Baraka was released from custody on Friday, a federal magistrate quickly determined he was not a flight risk and cautioned federal officials against making out-of-court statements about the mayor, who is also running for New Jersey governor, according to a newly-released transcript of the extraordinary virtual hearing … During the 18-minute videoconference, Baraka’s attorney Raymond Brown asked [U.S. Magistrate André M.] Espinosa to warn Trump administration officials against making derogatory public statements about his client … Earlier in the day, interim U.S. Attorney for New Jersey Alina Habba had posted on social media that Baraka had “willingly chosen to disregard the law” before he was arrested at the immigration detention center he was protesting and seeking to inspect along with three members of New Jersey’s congressional delegation. Espinosa said to the extent anyone had made such comments, he would “caution them to heed carefully to the rules of professional conduct” and “boundaries of propriety for public comment related to an ongoing investigation and/or prosecution.”
So it may turn out that Trump’s Parking Garage Lawyer, who has a history of struggling with basic lawyering tasks, will get directly warned about her violation of due process even before Pam Bondi or Chad Mizelle or Kristi Noem or Kash Patel. Or maybe Habba will have to warn Noem to shut her yap after DHS continued to attack members of Congress for engaging in oversight of a facility they claim still lacks the proper local permits.
In short, basic due process remains a struggle. But there are some reasons to believe that authentic Magna Carta is an auspicious sign.
Trump’s Mob Understands “Skeezy” Better than the Corruption Beat Journalists
/46 Comments/in emptywheel /by emptywheelFour days before old man Joe Biden dropped out of the race last summer, I argued that the endless discussion of Joe Biden Old was swamping three far more important stories, starting with whether Donald Trump was a partner, agent, or employee of Saudi Arabia.
[W]e are two days into Trump’s nomination party, and no one has asked — much less answered — whether Donald Trump is a business partner, paid foreign agent, or merely an employee of Saudi Arabia.
This is not a frivolous question. Since Trump left office, his family has received millions in four known deals from the Saudis:
- A deal to host LIV golf tournaments. Forbes recently reported that Trump Organization made less than $800K for about half the tournaments it has hosted. But Trump’s role in the scheme has given credibility to an influence-peddling scheme that aims to supplant the PGA’s influence. When Vivek Ramaswamy learned that two consultants to his campaign were simultaneously working for LIV, he forced them to resign to avoid the worries of influence-peddling. Yet Trump has continued to host the Saudis at his properties.
- A $2 billion investment in Jared Kushner’s private equity firm, in spite of the fact that analysts raised many concerns about the investment, including that he was charging too much and had no experience.
- A deal to brand a property in Oman slated to open in 2028, which has already brought Trump Organization $5 million. The government of Oman is a key partner in the deal, signed with a huge Saudi construction firm.
- A newly-announced deal with the same construction firm involved in the Oman deal, this time to brand a Trump Tower in Jeddah.
These Saudi deals come on top of Trump’s testimony that Turnberry golf course and his Bedford property couldn’t be overvalued because some Saudi would be willing to overpay for them.
But I believe I could sell that LIV Golf for a fortune, Saudi Arabia. I believe I could sell that to a lot of people for numbers that would be astronomical because it is like — very much like owning a great painting.
[snip]
I just felt when I saw that, I thought it was high. But I could see it — as a whole, I could see it if this were s0ld to one buyer from Saudi Arabia — I believe it’s the best house in the State of New York.
And while Eric Trump, not his dad, is running the company, Eric also has a role in the campaign and his spouse Lara has taken over the entire GOP.
Trump never fulfilled the promises to distance himself from his companies in the first term. A very partial review of Trump Organization financial records show the company received over $600K from the Saudis during his first term. As far as I’m aware, no one has even asked this time around.
Which means as things stand, Trump would be the sole beneficiary of payments from key Saudi investors if he became President again. Trump would be, at the very least, the beneficiary of a business deal with the Saudis, as president.
Admittedly, under the Supreme Court’s latest ruling on gratuities, it might be legal for Trump to get a bunch of swank branding deals as appreciation for launder Saudi Arabia’s reputation (one of the things for which Menendez was just convicted).
But that doesn’t mean it should be ignored, politically. It doesn’t mean American voters shouldn’t know these details. It doesn’t mean journalists (besides NYT’s Eric Lipton, whose most recent story on this was buried on page A7) shouldn’t demand answers.
It was, frankly, dizzying when I reread that post (and this one from election day, which added several more questions, including who was bribing Trump via Truth Social and his other online businesses) this morning. As we watch Trump (and Elon Musk) cash in in Saudi Arabia before Trump heads to Qatar to collect a $400 million flying bribe, self-imagined journalists are still obsessing about Joe Biden Old.
It may help to explain why this clear evidence of corruption was buried during the election that Eric Lipton, whose reporting was buried beneath all the Joe Biden Old stories, claimed the other day that “corruption requires explicit quid quo pro,” inverting the relationship between corruption (which includes a broad range of activities, much of it legal, of which the common understanding of bribery is a subset, of which John Roberts’ far narrower definition of bribery is a smaller subset of that subset) and bribery.
Just as alarming, though, Lipton pitched what is at least the fourth major story about the corruption of Trump’s memecoin (Molly White was onto this three weeks ago, and remains on it) with a purported contrast. Trump’s memecoin is no “Russian Hoax,” Lipton claimed, repeating Trump’s propaganda term unquestioningly.
I guess if you believe pardoning four of the five people adjudged to have lied about Russia — about the terms of the impossibly lucrative Trump Tower deal negotiated during the election, about the foreknowledge of Russia’s help in the election, about whether Trump’s campaign manager shared campaign strategy in exchange for a commitment to carve up Ukraine, about the terms via which Trump’s rat-fucker got early access to stolen Podesta files, and about whether Trump was involved in his National Security Adviser’s attempt to undercut punitive sanctions on Russia — is a hoax, then you’re bound to have a very constrained understanding of corruption.
This is NYT’s primary journalist covering Trump’s corrupt foreign entanglements, and he confesses he not only can’t explain the import of anything short of bribery, but doesn’t consider it corruption.
No wonder it got buried. No wonder Trump’s corruption continues to get buried under Joe Biden Old mania.
Joe Biden Old is easy enough even beltway scribes can claim to understand it, the purported scandal being that Biden’s aides didn’t publicly announce that they considered that Joe Biden Old might have to use a wheelchair in the future, in a second term, especially if he had a fall, but had not used one yet. That’s the kind of purported scandal the guardians of democracy infesting DC will chase like toddlers.
Remarkably, some of Trump’s most ardent supporters appear to better understand what Lipton claims he does not, how Trump’s overt corruption can harm America.
After ABC advanced the story of the $400 million flying castle Trump is set to take from Qatar, I tried to make some trouble on Xitter, describing Trump’s corruption in ways that might bother even MAGAts.
Just hours later, Laura Loomer posted a racist tweet objecting to the deal.
Loomer did attempt to walk back her statement, disclaiming corruption on Trump’s part, but she did get the import of appearances right.
Ben Shapiro got even closer to my prompt (while matching Loomer’s racism), arguing that accepting this plane was inconsistent with Trump’s claimed ideology of America First.
Taking sacks of goodies from people who support Hamas, Muslim Brotherhood, al-Jazeera, all the rest, that’s not America first. Like, please define America first in a way that says you should take sacks of cash from the Qatari royals who are behind al-Jazeera. It just isn’t America first in any conceivable way. So back to the original question — is this good for President Trump? Is it good for his agenda? Is it good for draining the swamp and getting things done? The answer is, no. It isn’t. It isn’t. If you want President Trump to succeed, this kind of skeezy stuff needs to stop. And here’s the thing, it’s already having an impact. It’s already having an impact.
Even in Congress, people are expressing their opposition on various grounds. Rand Paul complained about the look of it. Ted Cruz invoked the same concerns about Qatar’s ties to Hamas as Loomer and Shapiro.
NYT’s story on the plane, “Trump’s Plan to Take Jet From Qatar Heightens Corruption Concerns,” by Charlie Savage, situated it within all the other corrupt things Trump has done (and it’s a good catalog). But it mostly presents the risk of corruption in terms of benefit to Trump, not the corruption of US policy choices. Lipton’s piece on a Chinese firm with no revenue but with ties to TikTok and the Chinese government, dumping $300 million into Trump’s memecoin, discusses an ethical conflict, but doesn’t ever get around to considering the possibility that Trump will put China’s interests above the interests of any Americans, interests that go well beyond TikTok.
The purchase would create clear ethical conflicts, enriching Mr. Trump’s family at the same time that the president tries to reach a deal that would allow TikTok to keep operating in the United States rather than face a congressionally approved ban.
You want deception of far graver import than the non-disclosure of future, hypothetical wheelchair use? Donald Trump sold himself promising that he would deliver on the interests of American white working class people (or at least American white working class Christian men). But the more important sales deal was happening behind the scenes (or at least, in business deals reported in stories buried beneath dozens of stories on Joe Biden Old), where Trump was selling autocrats overseas and fraudsters around the world on a promise that dismantles not just the spirit of democracy, but even the very commitment to it.
And all that’s before the stuff we don’t yet know, whether all the things that Trump has done that helped China, like dismantling America’s soft power and chipping away at the dollar, were done because Trump is stupid or because he’s corrupt.
I’ve obviously been struggling for a long time about our failure to convey Trump’s corruption in terms that really resonate to the people he’s defrauding (and yes, my suspicions that appealing to racism might do the trick were not disappointed; it’s an insight Peter Pomerantsev develops in his How to Win an Information War). Everything Trump does is corrupt. And that corruption — whether it involves Elon Musk or Qatar or Putin — has a very detrimental effect even on the most committed MAGAt. But they’re not going to care that Trump, their liege, gets an unfair benefit. They’re going to care if the targets of their bigotry benefit or something is unfairly taken away from them.
Until we learn how to describe that, we’ll be missing a key element of the fight to get people, from all parties, to fight for democracy.
Stephen Miller Invites John Roberts to be the Instrument of His Own Destruction
/44 Comments/in emptywheel /by emptywheelI meant to write this post last week; I meant to argue that a Stephen Miller-related effort to FOIA the US Courts could be more significant development than Trump’s refusal to tell Kristen Welker he would adhere to the Constitution because he will instead do what “the lawyers” — probably including non-lawyer Stephen Miller among them — tell him to do.
KRISTEN WELKER:
But even given those numbers that you’re talking about, don’t you need to uphold the Constitution of the United States as president?
PRES. DONALD TRUMP:
I don’t know. I have to respond by saying, again, I have brilliant lawyers that work for me, and they are going to obviously follow what the Supreme Court said. What you said is not what I heard the Supreme Court said. They have a different interpretation.
It didn’t happen. I didn’t write the post.
But the delay proved useful, because the firings of the Librarian of Congress and the Register of Copyrights reflect yet another step in the same process that — I suspect — the lawsuit could one day join.
For all the chaos of the Trump term, after some initial missteps, Trump has preceded relentlessly to use presidential firings to remap government agencies over which the Executive is supposed to have limited or no influence. There has been a certain logical progression. Trump started with agencies entirely within the Executive (like USAID), then proceeded to boards and agencies designed to be independent (starting with the Special Counsel and Merit Systems Protection Board, effectively stripping federal employees of key protections, then moving onto the Federal Elections Commission, the Consumer Financial Protection Board, and the Federal Trade Commission, and more recently the Consumer Product Safety Commission). DOGE then started swallowing up independent agencies, like the US African Development Foundation and the Institute for Peace, before moving onto Radio Free Europe and the Postal Service.
Those efforts are all stuck in various stages of legal challenges. Their takeover may not succeed.
But after moving through independent agencies, Trump has turned to an agency of Congress, the Library of Congress, all without even telling Republicans he was coming.
Trump’s firing of the librarian, in particular, was so sudden that the move caught several of his Republican allies on Capitol Hill off guard, according to the two sources, with some GOP lawmakers who help conduct oversight of the Library of Congress unaware that the White House was going to do it; they learned about the firings in the media and elsewhere.
We’re just days into the latest escalation and thus far at least, Congress has prevented replacement staffers from taking over the Copyright Office.
Two men claiming to be newly appointed Trump administration officials tried to enter the US Copyright Office in Washington, DC on Monday, but left before gaining access to the building, sources tell WIRED. Their appearance comes days after the White House fired the director of the copyright office, Shira Perlmutter, who had held the job since 2020. Perlmutter was removed from her post on Saturday, one day after the agency released a report that raised concerns about the legality in certain cases of using copyrighted materials to train artificial intelligence.
[snip]
The US Copyright Office is a government agency within the Library of Congress that administers the nation’s copyright laws. It processes applications to copyright creative works and maintains a searchable database of existing registrations. Last week, the Trump administration also fired the Librarian of Congress, Carla Hayden, who was the first woman and the first Black person to hold the position.
The document the two men cited also stated that deputy attorney general Todd Blanche, who previously served as a personal defense lawyer for Trump, was now the acting Librarian of Congress. The Department of Justice announced Monday that Blanche would be replacing Hayden, who had been in the job for nearly a decade. White House press secretary Karoline Leavitt told reporters that Hayden’s firing stemmed from “quite concerning things she had done at the Library of Congress in pursuit of DEI.”
Ranking House Committee on Administration Member Joe Morelle has asked the Inspector General to investigate whether this breached Congress’ independence. Politico claims Republicans might object to this — but that’s based off a feckless comment from John Thune (and none from Mike Johnson).
Senate Majority Leader John Thune said in a brief interview that congressional leaders “want to make sure we’re following precedent and procedure” in naming a replacement for Carla Hayden, the Librarian of Congress whom Trump dismissed Thursday.
Thus far, no one has sued, but it often takes a few days to do so.
We’re still just at Day One on Trump’s attempt to take over two entities of Congress, with still more entities — like the Congressional Budget Office or Government Accountability Office, the latter of which is two months into a review of DOGE — Trump might want to undercut next.
In the past such an approach has succeeded in persuading even sympathetic judges that the President can use such firings to remake government. And the assault on Congressional entities matches the model used before: the White House fires someone appointed by the President (in this case, Congressional Librarian Carla Hayden), and then proceeds to claim authority to totally remap the agency, in significant part because it acts like an agency and courts, including SCOTUS, have said the President has unitary authority over agencies.
If that logic were to continue, it would be unsurprising to see Trump attempt a similar method with the Administrative Office of the US Courts. Indeed, DOGE has already probed the limits of Article III authority by including the Courts in the weekly DOGE email, the firing of GSA staffers who maintain Phoenix’s courthouse, and the attempted exclusion of law firms from federal properties, which would include courts.
TPM’s Josh Kovensky, who first reported this aspect of the lawsuit [docket], included some of these examples to demonstrate what he describes (with justification) as an escalating campaign to erode the independence of the judiciary.
The executive branch has tried to encroach on the power of the judiciary in other ways too, prompting a degree of consternation and alarm unusual for the normally-staid Administrative Office of U.S. Courts. As TPM has documented, DOGE has already caused disorder at the courts and sent out mass emails to judges and other judiciary employees demanding a list of their recent accomplishments. Per one recent report in the New York Times, federal judges have expressed concern that Trump could direct the U.S. Marshals Service — an executive branch agency tasked with protecting judges and carrying out court orders — to withdraw protection.
These are all facets of an escalating campaign to erode the independence of the judiciary, experts told TPM. The lawsuit demonstrates another prong of it: close allies of the president are effectively asking the courts to rule that they should be managed by the White House.
It’s on the basis that experts Kovensky quotes dismiss the seriousness of this challenge, again, with good justification.
“It’s like using an invalid legal claim to taunt the judiciary,” Anne Joseph O’Connell, a professor at Stanford University Law School, told TPM.
“To the extent this lawsuit has any value other than clickbait, maybe the underlying message is, we will let our imaginations run wild,” Peter M. Shane, a constitutional law scholar at NYU Law School, told TPM. “The Trump administration and the MAGA community will let our imaginations run wild in our attempts to figure out ways to make the life of the judiciary miserable, to the extent you push back against Trump.”
But against the background of the relentless assault on agencies of government, independent or not, the argument looks very familiar. America First Legal Foundation — Stephen Miller’s NGO, his affiliation with which unserious people sometimes mistake Miller for a lawyer — situates its argument in Sheldon Whitehouse’s efforts to crack down on Clarence Thomas and Sammy Alito’s open corruption. Because the Judicial Conference and Administrative Office of the Courts responded to oversight requests from Whitehouse, along with Hank Johnson, AFLF argues, it makes them Executive Agencies.
5. The Judicial Conference and the Administrative Office are central levers for Senator Whitehouse and Representative Johnson’s lawfare enterprise. The Conference and the Administrative Office have actively accommodated oversight requests from these congressmen concerning their allegations against Justices Thomas and Alito. Under our constitutional tradition, accommodations with Congress are the province of the executive branch. The Judicial Conference and the Administrative Office are therefore executive agencies. Such agencies must be overseen by the President, not the courts. Judicial relief here not only preserves the separation of powers but also keeps the courts out of politics.
The Judicial Conference is doing agency stuff, and therefore must be supervised by the Executive Branch, the lawsuit contends.
7. The federal judiciary is the system of courts. These courts are made up of judges who preside over cases and controversies. The executive branch, on the other hand, is responsible for taking care that the laws are faithfully executed and ensuring the proper functioning of the government. Federal courts rely on the executive branch for facility management and security. Federal judges, as officers of the courts, need resources to fulfill their constitutional obligations.
8. Courts definitively do not create agencies to exercise functions beyond resolving cases or controversies or administratively supporting those functions. But the Administrative Office of the U.S. Courts does exactly that. The Administrative Office is controlled by the Judicial Conference, headed by the Chief Justice of the United States Supreme Court, John Roberts. The Administrative Office is run by an officer appointed by—and subject to removal by—Chief Justice Roberts. 28 U.S.C. § 601.
9. Congress cannot constitutionally delegate to an officer improperly appointed pursuant to Article II powers exceeding those that are informative and investigative in nature. Buckley v. Valeo, 424 U.S. 1, 137–39 (1976).
10. The Judicial Conference’s duties are executive functions and must be supervised by executive officers who are appointed and accountable to other executive officers. United States v. Arthrex, Inc., 594 U.S. 1, 6 (2021) (Officers who engage in executive functions and are not nominated by the President “must be directed and supervised by an officer who has been.”).
11. Thus, the Judicial Conference and Administrative Office exercise executive functions and are accordingly subject to FOIA. Accordingly, their refusal to comply with AFL’s FOIA request is unlawful.
This is packaged up as a FOIA lawsuit. The entire argument — which should be that the Judicial Conference is an agency and therefore must respond to a FOIA — is presented in reverse, so that the outrageous claims about Article III are the primary argument. But it also lays out precisely the kind of argument we’ve seen used to rationalize the takeover of agencies Congress set up to be independent.
As of right now, Trevor McFadden, the Trumpiest DC District Judge (in my experience McFadden also fiercely guards judicial prerogaties), has been assigned the case. On Friday he invited calls from the parties to ask for his recusal.
[T]he undersigned is a member of the Judicial Conference’s Committee on Court Administration and Case Management (CACM). Any party wishing to submit a recusal motion on that basis must do so on or before the due date for Defendants’ Answer.
Like virtually all other legal challenges, it will take some time to see where this will go.
I’m not saying this lawsuit — a naked attempt to get a judge to say that judges’ own infrastructure must be relegated to the Executive Branch, susceptible to takeover just like the Institute of Peace or Radio Free Europe — will succeed.
I’m saying that it adopts the very same pattern that has been used to subsume independent agencies, the same pattern used in recent days in an assault on Congress’ prerogatives.
It’s possible the lawsuit, which named John Roberts as a defendant, will clue SCOTUS in to the use to which Stephen Miller’s minions plan to put Supreme Court precedent, including Roberts’ own fondness for the unitary executive. Notably, Roberts’ comments on the import of judicial independence came after this lawsuit was filed, after former subordinates of Trump’s top advisor argued that the Executive must takeover Article III’s bastions of independence.
Roberts, speaking at a public event in Buffalo, New York, said an independent judiciary is a key feature of the U.S. constitutional system that had not existed in other countries when it was founded.
“In our Constitution … the judiciary is a co-equal branch of government, separate from the others, with the authority to interpret the Constitution as law and strike down, obviously, acts of Congress or acts of the president,” he said.
“And that innovation doesn’t work if … the judiciary is not independent,” he added. “Its job is to, obviously, decide cases but, in the course of that, check the excesses of Congress or the executive, and that does require a degree of independence.”
Roberts repeated his concern about the courts yesterday.
So maybe this purported FOIA challenge was a strategically stupid move by Miller’s crowd, showing their hands prematurely to the guy most able to swap cards. Or maybe they took it as a deniable first probe into whether they could use with the courts the same tactic used to dismantle the independence of much of the rest of federal government.
None of us know how this will work out. It might just happen that, by alerting Roberts that he’s next, after Trump finishes off the Institute of Peace and the Library of Congress, Roberts will look more critically at Trump’s arguments in those legal fights, knowing full well that rubber stamping Executive authority may rubber stamp the takeover of the courts, or at least the courthouses, the same way he might look differently at the commission firings knowing that Jerome Powell might be next.
But this is, in my opinion, more than just a troll, more than just an attempt to bully judges. This certainly looks like a test to see whether Miller’s minions can extend their thus far successful takeover plan to encompass the judiciary itself.
Update: In a piece on the Library of Congress firing, Daniel Schuman concludes,
Trump likely can fire the Librarian of Congress. Trump likely cannot appoint an interim replacement. Trump cannot hire or fire subordinates. Congress must provide Robert Newlen support as he protects the independence of the Library of Congress and its ability to serve all members of Congress.
In his own post on it, Chris Geidner reviews some of the precedents.
NYT’s Storytime on Trump’s Houthi Capitulation
/19 Comments/in emptywheel /by emptywheelNYT has a story that purports to explain, “Why Trump Suddenly Declared Victory Over the Houthi Militia.” It’s a fantastic story, down to the detail that DOD never achieved air superiority over the Houthis.
But it is provably unreliable in at least two ways: the timeline, and the claimed involvement of Trump. Given that the story describes a clusterfuck, it does raise questions about whether there’s an even bigger clusterfuck (or Trump scandal) behind it.
Start with the timing. The entire story is premised on Trump approving a 30-day operation, and after that didn’t work, he pulled the plug.
When he approved a campaign to reopen shipping in the Red Sea by bombing the Houthi militant group into submission, President Trump wanted to see results within 30 days of the initial strikes two months ago.
By Day 31, Mr. Trump, ever leery of drawn-out military entanglements in the Middle East, demanded a progress report, according to administration officials.
But the results were not there. The United States had not even established air superiority over the Houthis. Instead, what was emerging after 30 days of a stepped-up campaign against the Yemeni group was another expensive but inconclusive American military engagement in the region.
The Houthis shot down several American MQ-9 Reaper drones and continued to fire at naval ships in the Red Sea, including an American aircraft carrier. And the U.S. strikes burned through weapons and munitions at a rate of about $1 billion in the first month alone.
It did not help that two $67 million F/A-18 Super Hornets from America’s flagship aircraft carrier tasked with conducting strikes against the Houthis accidentally tumbled off the carrier into the sea.
By then, Mr. Trump had had enough.
[snip]
At some point, General Kurilla’s eight- to 10-month campaign was given just 30 days to show results.
In those first 30 days, the Houthis shot down seven American MQ-9 drones (around $30 million each), hampering Central Command’s ability to track and strike the militant group. Several American F-16s and an F-35 fighter jet were nearly struck by Houthi air defenses, making real the possibility of American casualties, multiple U.S. officials said.
As the timeline below lays out, this decision didn’t happen at the 31-day mark. It happened at the 51-day mark.
And the loss of the two F/A-18s both happened after the 30-day mark; indeed, at least as currently reported, the second was lost on May 6, hours after Trump announced the halt (a decision that had been made “last night“).
Even the timing of the loss of the Reaper drones is wrong. One was shot down before the first strikes, six more were shot down between then and April 23, of which three appear to have been shot down after the 30-day mark. (The Houthis have successfully targeted Reapers for longer than that.)
And look at how those problems in the timeline intersect with the agency ascribed to Trump in the story (Maggie Haberman and Jonathan Swan are bylined).
Word three of the story describes Trump approving the campaign.
When he approved a campaign to reopen shipping in the Red Sea by bombing the Houthi militant group into submission, President Trump wanted to see results within 30 days of the initial strikes two months ago.
By Day 31, Mr. Trump, ever leery of drawn-out military entanglements in the Middle East, demanded a progress report, according to administration officials.
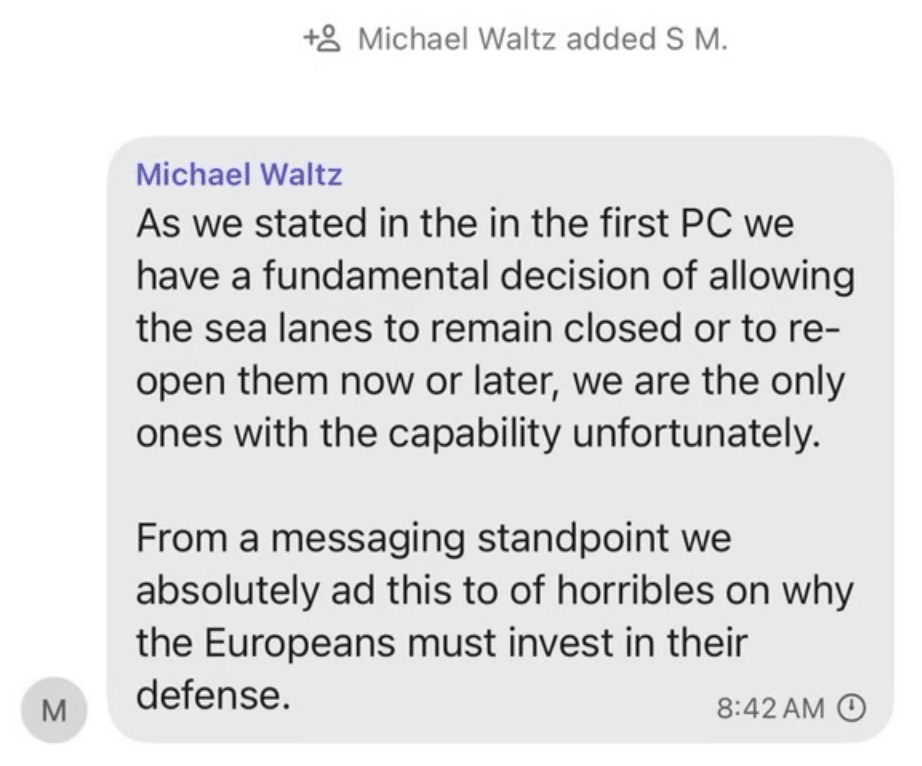
But that’s not what the Signal texts released by Jeffrey Goldberg show. They show that Trump ordered the reopening of shipping lanes, but his top advisors, including Stephen Miller, were still debating how and when to do that the day of the attack.
There’s good reason to believe that Miller’s interpretation of Trump’s views served as the approval for the timing of the attack.
While the NYT story describes the other top advisors involved in all this — Mike Waltz, Pete Hegseth, Chairman of the Joint Chiefs Dan Caine, Centcom Commander Michael Kurilla, Steve Witkoff, JD Vance, Tulsi Gabbard, Marco Rubio, and Susie Wiles, all skeptics, with the exception of Kurilla — Miller is not mentioned in the story.
Embedded between claims about Trump’s agency — Trump had had enough, Trump was ready to move on, Trump had signed off on an eight- to 10-month campaign to which he gave just 30 days to show results, Trump became the most important skeptic, Trump decided to declare the operation a success — there are actually two better substantiated explanations for the end of the campaign. First, that newly-confirmed CJCS Caine was “concerned that an extended campaign against the Houthis would drain military resources away from the Asia-Pacific region” (presumably including the USS Vinson, which Hegseth had moved from the seas off China, one of the stories for which he launched a witch hunt to ID its sources), and that Oman proposed “a perfect offramp.”
By then, Mr. Trump had had enough.
Steve Witkoff, his Middle East envoy, who was already in Omani-mediated nuclear talks with Iran, reported that Omani officials had suggested what could be a perfect offramp for Mr. Trump on the separate issue of the Houthis, according to American and Arab officials. The United States would halt the bombing campaign and the militia would no longer target American ships in the Red Sea, but without any agreement to stop disrupting shipping that the group deemed helpful to Israel.
U.S. Central Command officials received a sudden order from the White House on May 5 to “pause” offensive operations.
[snip]
Mr. Trump has never bought into long-running military entanglements in the Middle East, and spent his first term trying to bring troops home from Syria, Afghanistan and Iraq.
[snip]
By May 5, Mr. Trump was ready to move on, according to interviews with more than a dozen current and former officials with knowledge of the discussions in the president’s national security circle.
[snip]
By early March, Mr. Trump had signed off on part of General Kurilla’s plan — airstrikes against Houthi air defense systems and strikes against the group’s leaders. Defense Secretary Pete Hegseth named the campaign Operation Rough Rider.
At some point, General Kurilla’s eight- to 10-month campaign was given just 30 days to show results.
[snip]
But Mr. Trump had become the most important skeptic.
[snip]
On Tuesday, two pilots aboard another Super Hornet, again on the Truman, were forced to eject after their fighter jet failed to catch the steel cable on the carrier deck, sending the plane into the Red Sea.
By then, Mr. Trump had decided to declare the operation a success. [my emphasis]
This casting of Trump by two Trump-whisperers as an agent that the Signal texts show he was not comes in a story that understates Trump’s first term belligerence (particularly as it pertains to ISIS) and the timing of his efforts to bring troops home.
Trump is the hero of this story, except much of that story conflicts with the timeline and known details.
Caine’s concern about withdrawing resources from China — finally, someone prioritizing the Administration’s stated goal of taking on China!! — is notable. The story doesn’t acknowledge it, but the objective of the operation — opening the shipping lanes — changed over the course of the operation to stopping the targeting of US ships, but not targeting of Israelis, much less trade between the Europeans and China about which there was so much animus expressed on the Signal chat (though, as mentioned here, the Signal chatters never actually mentioned China). Strategically, leaving China and Europe to deal with the Houthis is consistent with the trade war Trump subsequently launched. But that public discussion doesn’t appear in this story, much less admission that Trump failed to fulfill his stated objective.
Meanwhile, there are two paragraphs that describe the journalists’ sources rebutting an entirely different story (or stories).
The chief Pentagon spokesman, Sean Parnell, said the operation was always meant to be limited. “Every aspect of the campaign was coordinated at the highest levels of civilian and military leadership,” he said in an emailed statement.
A former senior official familiar with the conversations about Yemen defended Michael Waltz, Mr. Trump’s former national security adviser, saying he took a coordinating role and was not pushing for any policy beyond wanting to see the president’s goal fulfilled.
One of those stories — the one Parnell, Hegseth’s propagandist, rebutted — is that the operation lacked coordination at the highest level of leadership. That story is consistent with Trump not approving the operation, which is consistent with many other details that appear in the story and also the discussion the day of the first attack about when to launch it.
The other story — from a former senior official (and so probably one of the people that either Laura Loomer, Pete Hegseth, or Trump himself has fired during this period) defending Mike Waltz — denies that Waltz was pushing a policy inconsistent with Trump’s goals. Given that Trump’s declared victory very pointedly doesn’t extend to Israel, and given the report that Trump distrusted Waltz because he coordinated with Bibi Netanyahu, and given the reports that Trump has not been coordinating with Bibi since Waltz’ departure, it’s possible that the story Waltz’ defender was trying to rebut is that he accounted for Israeli interests to an extent Trump didn’t care to.
It’s worth noting that American Oversight’s lawsuit keeps revealing additional parts to the Signal chat, so it’s possible we’ll learn more about these rebutted stories from pending FOIAs.
Anyway, it’s a nice story NYT has told and I have no doubt that the non-Trump whisperers have faithfully conveyed what their sources told them; likewise, I have no doubt that the expressed concerns of Parnell and the Waltz defender are real.
But given the clusterfuck described, it only raises questions about the real story underlying this one.
Timeline
March 15: First strikes
March 21: Redeployment of USS Vinson
April 14: 30 day mark; Dan Caine sworn in
Late April: Conference call with Hegseth, the Saudis, and Emiratis (no mention of Caine)
April 28 (day 44): Loss of first F/A-18
May 1: Trump fires Mike Waltz, in part because he coordinated closely with Bibi Netanyahu
May 5 (day 51): Order given to CentCom to “pause” offensive operations
May 6 (day 52), 12:09PM: Trump declares Houthi decision to halt attacks “last night”
May 6, 9PM local time; around 2PM DC time: Loss of second F/A-18
Jamieson Greer Says Trump’s Trade Deficit Emergency Wasn’t as Serious an Emergency “as Maybe Thought”
/37 Comments/in emptywheel /by emptywheelAgainst the background of empty ports, stalled shipping traffic, and impending business failures, Trump has capitulated on his trade embargo with China. Treasury Secretary Scott Bessent and Trade Representative Jamieson Greer will announce an even bigger rollback of tariffs than the 80 or 50% tariffs Trump floated last week, to 30% (which is the 10% tariffs imposed worldwide, plus the 20% that purports to be a punishment for China’s role in providing precursors for fentanyl).
The U.S. and China agreed to slash punishingly high tariffs on each other’s goods, a major thaw in trade relations that resets the tone between the world’s two largest economies from outright conflict to constructive engagement.
After weekend talks in Geneva:
- President Trump’s “reciprocal” tariff on China will fall to 10% from 125%.
- A separate 20% tariff the president imposed over what he described as China’s role in the fentanyl trade will remain.
- Beijing will cut its retaliatory levies on U.S. goods to 10% from 125%.
- The U.S. said the reductions would last for 90 days while the two sides begin further talks.
The agreement lowered tariffs levels more than Wall Street expected and came after just two days of talks.
In announcing this “deal,” Greer offered up thin excuses for capitulating within hours.
It’s important to understand how quickly we were able to come to an agreement, which reflects that perhaps the differences were not so large as maybe thought. That said, there was a lot of groundwork that went into these these two days.
Just remember why we’re here in the first place is the United States has a massive $1.2 trillion trade deficit. So the President declared a national emergency, and imposed tariffs. We’re confident that the deal we struck with our Chinese partners will help us to resolve — work toward resolving that national emergency.
“Perhaps the differences were not so large as maybe thought” — thought by whom, Greer doesn’t say. But Greer does note that the President was the guy who declared those differences that were not so large as maybe thought to be an emergency.
Trump thought it was an emergency. Now Greer says it wasn’t, as it turns out.
Once it became clear that Trump had caused a far bigger emergency by declaring one, it took just hours to rethink the claimed emergency.
The focus on the emergency may cause the Administration headaches going forward (which may be why Greer attempted to offer an excuse).
That claimed emergency is the basis via which Trump usurped Congress’ authority to set tariffs.
By the authority vested in me as President by the Constitution and the laws of the United States of America, including the International Emergency Economic Powers Act (50 U.S.C. 1701 et seq.)(IEEPA), the National Emergencies Act (50 U.S.C. 1601 et seq.)(NEA), section 604 of the Trade Act of 1974, as amended (19 U.S.C. 2483), and section 301 of title 3, United States Code,
I, DONALD J. TRUMP, President of the United States of America, find that underlying conditions, including a lack of reciprocity in our bilateral trade relationships, disparate tariff rates and non-tariff barriers, and U.S. trading partners’ economic policies that suppress domestic wages and consumption, as indicated by large and persistent annual U.S. goods trade deficits, constitute an unusual and extraordinary threat to the national security and economy of the United States. That threat has its source in whole or substantial part outside the United States in the domestic economic policies of key trading partners and structural imbalances in the global trading system. I hereby declare a national emergency with respect to this threat.
A series of lawsuits challenging Trump’s tariffs — in this case, one brought by a wine importer, VOS Selections, and other small businesses, supported by right wing funders, in which Greer is a named defendant — have argued the trade deficit is not an emergency. [docket]
The President has no authority under IEEPA to issue the tariffs. IEEPA does not even mention tariffs. No other President has asserted this authority. IEEPA was passed to limit the President’s emergency powers. If Congress wanted to grant the President the authority to issue tariffs in IEEPA, it could have, as it has done so elsewhere. But when Congress does give the President tariff authority, it does so subject to strict statutory limits.
Legitimate use of IEEPA is limited to cases of emergencies where there is an “unusual and extraordinary threat.” But the national emergency the President has declared—the existence of bilateral trade deficits with some countries—is not an emergency, nor is it unusual or extraordinary. The United States has had some amount of trade deficit in goods for most of the last century, while having the most economic success of any country in history.
Moreover, the power claimed by the President here is extreme: he claims the power to unilaterally impose infinite tariffs of his choosing on any country he chooses—even countries with which we run a trade surplus. Any grant of such authority by Congress to the President should qualify as a major question subject to the strictest judicial scrutiny—which this claim of authority under IEEPA cannot survive.
The government, in response, has argued that it — like other Executive authorities — is not subject to court review.
More to the point, courts have consistently held that the President’s emergency declarations under the National Emergencies Act, and the adequacy of his policy choices addressing those emergencies under IEEPA, are unreviewable. “Although presidential declarations of emergencies . . . have been at issue in many cases, no court has ever reviewed the merits of such a declaration.” Ctr. for Biological Diversity v. Trump, 453 F. Supp. 3d 11, 31 (D.D.C. 2020) (emphasis in original). And the Federal Circuit has recognized that an inquiry to “examine the President’s motives and justifications for declaring a national emergency” under IEEPA “would likely present a nonjusticiable political question.” Chang v. United States, 859 F.2d 893, 896 n.3 (Fed. Cir. 1988); see, e.g., Yoshida, 526 F.2d at 579 (“courts will not normally review the essentially political questions surrounding the declaration or continuance of a national emergency”); United States v. Shih, 73 F.4th 1077, 1092 (9th Cir. 2023) (refusing to review declaration of emergency under IEEPA); In re 650 Fifth Ave. & Related Props., 777 F. Supp. 2d 529, 575 n.16 (S.D.N.Y. 2011) (concluding that whether the government of Iran’s actions and policies constituted an “unusual and extraordinary threat to the national security, foreign policy, and economy of the United States” was an unreviewable judgment “reserved to the executive branch”); Beacon Products Corp. v. Reagan, 633 F. Supp. 1191, 1194-95 (D. Mass. 1986) (concluding that whether Nicaragua posed sufficient threat to trigger the President’s IEEPA power to impose an embargo on the country was a nonjusticiable political question).
Reviewing the legitimacy of the underlying emergency—a foreign-affairs and nationalsecurity matter constitutionally and statutorily committed to the President—would require “the court to assess the wisdom of the President’s judgment concerning the nature and extent of that threat, a matter not susceptible to judicially manageable standards.” Beacon Products, 63 F. Supp. at 1195. Thus, the President’s “motives, his reasoning, his finding of facts requiring the action, and his judgment, are immune from judicial scrutiny.” Florsheim, 744 F.2d at 796; see United States v. George S. Bush & Co., 310 U.S. 371, 380 (1940) (“For the judiciary to probe the reasoning which underlies this Proclamation would amount to a clear invasion of the legislative and executive domains.”).
Normally, such an argument would carry a lot of sway with courts.
But in a parallel invocation of Presidential authority, judges already are pointing to Trump’s fickleness as evidence that his justifications for exercising Executive authority are bullshit. In her opinion granting Perkins Coie summary judgement against Trump’s attack on the law firm, Beryl Howell noted that the only thing that happened between the time Trump claimed Paul, Weiss lawyers could not be trusted with security clearances and when he decided they could be was their agreement to provide $40 million in pro bono legal services. [docket]
Second, and tellingly, the Paul, Weiss EO contained a virtually identical security clearance review provision to the one at issue in this case. Compare EO 14230 § 2, 90 Fed. Reg. at 11781, with Paul, Weiss EO § 2, 90 Fed. Reg. at 13039. As discussed, see supra Part III.B.1(b), the Paul, Weiss EO was revoked only seven days after its issuance when President Trump reached a “deal” with that firm. See generally Paul, Weiss Revocation Order, 90 Fed. Reg. 13685. While the Paul, Weiss Revocation Order summarized that firm’s agreement to, inter alia, “adopt[] a policy of political neutrality with respect to client selection and attorney hiring; tak[e] on a wide range of pro bono matters representing the full political spectrum; commit[] to merit-based hiring, promotion, and retention . . .; dedicat[e] the equivalent of $40 million in pro bono legal services during [President Trump’s] term in office . . .; and other similar initiatives,” none of these agreedupon policy or practice changes appear to explain or address how any national security concerns sufficient to warrant the Paul, Weiss EO could have changed so rapidly. Id. § 1, 90 Fed. Reg. at 13685. The speed of the reversal and the rationale provided in the Paul, Weiss Revocation Order, which focused only on agreements to advance policy initiatives of the Trump Administration, see id., further support the conclusion that national security considerations are not a plausible explanation for Section 2.
As Roger Parloff noted, Paul Clement made a similar point in arguing that the EO against Wilmer Hale must be overturned (I’m fairly certain he has made this more general observation about how the Paul, Weiss flipflop made the retaliatory EOs more vulnerable).
I think it’s crystal clear, he proceeds, that it’s all tied together. Section 1 explains what motivated all the sections.
What happened with the law firm of Paul Weiss Rifkind Wharton & Garrison adds further support for viewing the order as a whole, he argues. Paul Weiss faced the same operative provisions in an executive order issued on March 14. But on March 21, a later executive order repealed the whole thing. It didn’t keep, say, the security clearances or restrictions on government buildings while rescinding other sections.
Clement thinks that’s particularly telling with respect to the security clearances, he says. When you look to the agreement Paul, Weiss made with the president, there wasn’t anything specific mentioned about national security or the national interest or anything else. It was mostly about providing $40 million in pro bono services that were more to the president’s liking.
This trade deficit emergency Trump declared remains the claimed basis for the 10% tariffs still levied against China and most other countries in the world (as a wine importer, tariffs on those other countries, not China — Austria, Italy, Greece, Lebanon, Morocco, Spain, France, Portugal, Mexico, Argentina, Germany, Croatia, Hungary, and South Africa — are the ones that pose a problem for VOS Selections).
And now his Trade Representative has gone on TV to proclaim that maybe what was claimed to be an emergency was “not so large as maybe thought.”
I look forward to plaintiffs invoking Greer’s admission going forward.