I’m a leading purveyor of the theory that Robert Mueller is producing his mythical “report” via one after another speaking indictments. That said, it has always been true that some of the most interesting parts of his indictments involved what didn’t get said. That’s especially true in today’s Roger Stone indictment. Before I explain what didn’t get said, let me review what got said. The indictment shows that Stone was asked to figure out what emails on Hillary Julian Assange had, and using at least Jerome Corsi and Randy Credico as go-betweens, Stone did so, providing information (most explicitly) to Trump campaign manager Steve Bannon. When Congress asked Stone about all this, he lied, first hiding any of his go-betweens, and then seemingly using Randy Credico to hide Jerome Corsi. Mueller provides a lot of the communications between Stone and his go-betweens and the communications from October 2016, as well as some of the ones from the cover-up period.
But he doesn’t provide us everything.
I have argued that the early morning raid, not to mention the larding on of charges, suggest this is an effort to get Stone to flip, both against Jerome Corsi (which is why Meuller locked in testimony from Corsi’s stepson yesterday) and Trump himself.
With that in mind, here are the things that Mueller doesn’t say.
With whom — besides Campaign Manager Steve Bannon — at the Trump Campaign did Roger Stone speak
The word “campaign” shows up 52 times in Stone’s indictment, of which (by my count) 7 are generic references, 16 are to Hillary’s campaign or a descriptor for John Podesta, and 29 are to Trump’s campaign or associates of it. The indictment describes Stone’s discussions with people on the campaign over and over. While a number of those are to identified individuals — most notably Steve Bannon — a number of those are generic, including the following references.
During the summer of 2016, STONE spoke to senior Trump Campaign officials about Organization 1 and information it might have had that would be damaging to the Clinton Campaign. STONE was contacted by senior Trump Campaign officials to inquire about future releases by Organization 1.
[snip]
STONE also continued to communicate with members of the Trump Campaign about Organization 1 and its intended future releases.
[snip]
By in or around June and July 2016, STONE informed senior Trump Campaign officials that he had information indicating Organization 1 had documents whose release would be damaging to the Clinton Campaign.
[snip]
STONE thereafter told the Trump Campaign about potential future releases of damaging material by Organization 1.
It does so in an indictment that alleges (correctly, obviously) that one of Stone’s lies to the House Intelligence Committee that was material was whom he was speaking with on the campaign. The description of that lie cites the October 4 Bannon communication and the “supporter.” But it still leaves who else he spoke with unstated.
STONE’s False and Misleading Testimony About Communications with the Trump Campaign
35. During his HPSCI testimony, STONE was asked, “did you discuss your conversations with the intermediary with anyone involved in the Trump campaign?” STONE falsely and misleadingly answered, “I did not.” In truth and in fact, and as described above, STONE spoke to multiple individuals involved in the Trump Campaign about what he claimed to have learned from his intermediary to Organization 1, including the following:
a. On multiple occasions, STONE told senior Trump Campaign officials about materials possessed by Organization 1 and the timing of future releases.
And, of course, there’s this reference, which uses the word “directed” exactly a week after BuzzFeed got pilloried for using it about Trump.
After the July 22, 2016 release of stolen DNC emails by Organization 1, a senior Trump Campaign official was directed to contact STONE about any additional releases and what other damaging information Organization 1 had regarding the Clinton Campaign.
Mind you, this indictment had to have been approved in advance by Big Dick Toilet Salesman Matt Whitaker, and the last time he permitted prosecutors to name Individual-1 in an indictment, he got chewed out for it.
So maybe Mueller is not saying who else on the Trump campaign Stone was talking to (though we know he had frequent calls with Trump all through the campaign) to hide what else he knows. Maybe the Big Dick Toilet Salesman wouldn’t let Mueller lay this out (though I doubt that’s the case). Or maybe Mueller is just trying to avoid a second week in a row featuring headlines about what Trump “directed” his associates to do as part of the Russian conspiracy.
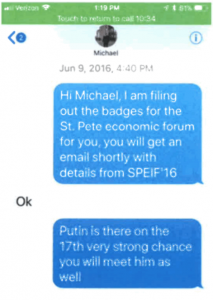
Corsi’s (and possibly Credico’s) role in the conspiracy
As I noted above, Mueller got aggressive with Stone to get him to flip on others. Obviously, the big prize is Trump. But there’s space for Stone to take his revenge on Jerome Corsi (and possibly even Randy Credico).
I suspect that Credico is not in any danger here. That said, he is described as a potential co-conspirator, Person 2, and did clearly discuss a conspiracy to obstruct HPSCI’s investigation. “‘Stonewall it. Plead the fifth. Anything to save the plan’ . . . Richard Nixon,” Stone wrote as he tried to persuade Credico not to testify to HPSCI.
There’s just one detail that makes me wonder if Credico was not fully truthful with Mueller. When Credico discussed Stone’s September request that he ask Assange about emails pertaining to Hillary’s efforts to undermine a Libyan peace effort with WSJ last year, he denied he had sent the request to either Assange or his lawyer Margaret Kunstler.
“Please ask Assange for any State or HRC e-mail from August 10 to August 30–particularly on August 20, 2011,” Mr. Stone wrote to Randy Credico, a New York radio personality who had interviewed Mr. Assange several weeks earlier. Mr. Stone, a longtime confidant of Donald Trump, had no formal role in his campaign at the time.
Mr. Credico initially responded to Mr. Stone that what he was requesting would be on WikiLeaks’ website if it existed, according to an email reviewed by the Journal. Mr. Stone, the emails show, replied: “Why do we assume WikiLeaks has released everything they have ???”
In another email, Mr. Credico then asked Mr. Stone to give him a “little bit of time,” saying he thought Mr. Assange might appear on his radio show the next day. A few hours later, Mr. Credico wrote: “That batch probably coming out in the next drop…I can’t ask them favors every other day .I asked one of his lawyers…they have major legal headaches riggt now..relax.”
Mr. Credico said in an interview with the Journal that he never passed the message on to Mr. Assange or his lawyers, but “got tired” of Mr. Stone “bothering” him, and so told Mr. Stone he had passed along the message.
The indictment says he in fact did forward the request to Kunstler.
On or about September 20, 2016, Person 2 forwarded the request to a friend who was an attorney with the ability to contact the head of Organization 1. Person 2 blind-copied STONE on the forwarded email.
That said, the indictment clearly remains silent about a lot of the details Mueller has incriminating Corsi in a cover-up (who, remember, prosecutors threatened to charge in a conspiracy to suborn perjury with respect to Stone’s testimony, and whose stepson Mueller locked into testimony before this indictment). The indictment includes this reference to a November discussion between Stone and Corsi.
On or about November 30, 2017, STONE asked Person 1 to write publicly about Person 2. Person 1 responded, “Are you sure you want to make something out of this now? Why not wait to see what [Person 2] does. You may be defending yourself too much—raising new questions that will fuel new inquiries. This may be a time to say less, not more.” STONE responded by telling Person 1 that Person 2 “will take the 5th—but let’s hold a day.”
But it remains silent on the report that Stone asked Corsi to write in August 2016 to establish a cover story, and it remains silent on whether Stone paid Corsi hush payments to stay silent after that.
Farage and Malloch and any other go-betweens
The indictment names Ted Malloch, though not as a co-conspirator.
On or about the same day, Person 1 forwarded STONE’s email to an associate who lived in the United Kingdom and was a supporter of the Trump Campaign.
[snip]
The body of the email read in part that Person 1’s associate in the United Kingdom “should see [the head of Organization 1].”
It doesn’t, however, put the Malloch references into context.
For example, it doesn’t reveal that — around the time someone “was directed” to get Stone to find out what WikiLeaks had — Stone and Alex Jones met with Nigel Farage at the RNC, which ultimately led to Farage joining Trump at a campaign event.
One night during the convention, Farage was introduced to Trump’s longtime adviser, the infamous political trickster, Roger Stone, at an Italian restaurant in The Flats district of Cleveland, according to both men.
Stone, who was accompanied that night by the Internet radio host and conspiracy theorist Alex Jones, said Farage’s main goal appeared to be to get a meeting with Trump.
The next day, Stone said, he tried to help by calling his former business partner, Paul Manafort – then Trump’s campaign chairman – and suggested that the Republican nominee get together with Farage. Manafort’s response was something along the lines of, “I’ll put a good word in,” Stone recalled.
Then, Stone met Ted Malloch — with Corsi — for dinner in NYC.
Asked about the nature of his relationship with Malloch, Stone said he did not know the other man well. He initially said he met Malloch three times but later said he recalled only two meetings with him.
Stone’s and Malloch’s first meeting was at a New York restaurant, Strip House, during the 2016 campaign. The two men dined with Jerome Corsi, a far-right political commentator and conspiracy theorist, Stone said.
Stone said his conversation with Malloch and Corsi at dinner was friendly but not memorable, and that they discussed “Brexit and globalism.” He added that they never discussed WikiLeaks, Assange, or Russia.
Stone, at least, is very sketchy about the timing of this, though it may actually precede when Stone asks Corsi to reach out to Malloch (indeed, might be the very reason he thought Corsi could get to Assange via Malloch).
That led to Farage’s campaign appearance with Trump on August 23.
Note, too, that the Stone indictment actually doesn’t say that Corsi is the go-between that Stone was hiding when he instead claimed Credico was his link to Assange. Indeed, of that go-between, he says he had only phone contact (though as I’ll write in a follow-up, that may have been for other reasons).
Particularly given Stone’s move to begin setting up a cover-story in August 2016, I’m not yet convinced we know who Stone’s real go-between is (and I’m still fairly certain that he and possibly Corsi had actual Podesta emails by then). He could have been working with Malloch directly. Or it could be someone else entirely.
Whoever it is, nothing in the Stone indictment tells us that for sure.
The Assange pardon
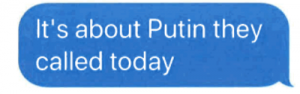
The Stone indictment is also silent about something that they have evidence — in the form of texts between Credico and Stone, surely among other things — that Stone tried to get Assange a pardon early last year.
In early January, Roger Stone, the longtime Republican operative and adviser to Donald Trump, sent a text message to an associate stating that he was actively seeking a presidential pardon for WikiLeaks founder Julian Assange—and felt optimistic about his chances. “I am working with others to get JA a blanket pardon,” Stone wrote, in a January 6 exchange of text messages obtained by Mother Jones. “It’s very real and very possible. Don’t fuck it up.” Thirty-five minutes later, Stone added, “Something very big about to go down.”
The recipient of the messages was Randy Credico, a New York-based comedian and left-leaning political activist whom Stone has identified as his back channel to WikiLeaks during the 2016 campaign—a claim Credico strongly denies. During the election, Stone, a political provocateur who got his start working for Richard Nixon’s presidential campaign, made statements that suggested he had knowledge of WikiLeaks’ plans to publish emails stolen from Hillary Clinton’s campaign chairman, John Podesta, and other Democrats, and his interactions with WikiLeaks have become an intense focus of special counsel Robert Mueller’s ongoing investigation into Russian election interference. As Mueller’s team zeroes in on Stone, they have examined his push for an Assange pardon—which could be seen as an attempt to interfere with the Russia probe—and have questioned at least one of Stone’s associates about the effort.
Particularly given that any pardon would have had to involve the one guy in the United States who can pardon Assange, it seems relevant to Mueller’s investigation. And yet it doesn’t show up in this indictment.
That’s something, then, that Stone could walk Mueller through as an effort to get rid of the 20-year witness tampering charge he faces.
Russia
Finally, the indictment remains mostly silent about Russia, particularly Roger Stone’s 180-turn on August 1 to claim that Russia may not have been behind the hack of the DNC. That’s all the more interesting given the way the indictment lays out the attribution to Russia made in mid-June.
On or about June 14, 2016, the DNC—through Company 1—publicly announced that it had been hacked by Russian government actors.
And then included Stone’s denial that Russia had hacked the DNC in his statement before HPSCI.
“These hearings are largely based on a yet unproven allegation that the Russian state is responsible for the hacking of the DNC and [the Clinton Campaign chairman] and the transfer of that information to [Organization 1].”
The indictment makes these two nods to attribution even as (as a number of people have observed) in their motion to seal Stone’s indictment, prosecutors deemed Stone’s indictment to be related to the GRU indictment, and his docket includes one of the DC AUSAs also on the Internet Research Agency case, Jonathan Kravis. (I’ve updated my running docket of Mueller and potentially related cases here.)
Remember, the GRU indictment describes (but doesn’t charge) Stone’s communications with Guccifer 2.0.
On or about August 15, 2016, the Conspirators, posing as Guccifer 2.0, wrote to a person who wasin regular contact with senior members of the presidential campaign of Donald J. Trump, “thank u for writing back . . . do u find anyt[h]ing interesting in the docs i posted?” On or about August 17, 2016, the Conspirators added, “please tell me if i can help u anyhow . . . it would be a great pleasure to me.” On or about September 9, 2016, the Conspirators, again posing as Guccifer 2.0, referred to a stolen DCCC document posted online and asked the person, “what do u think of the info on the turnout model for the democrats entire presidential campaign.” The person responded, “[p]retty standard.”
So prosecutors are saying that Stone’s crimes are more closely related to the actual Russian hack (which, remember, continued into September, after Stone deemed the DCCC analytics Guccifer 2.0 released to be “standard”) than they are to Flynn or Manafort or Papadopoulos or anyone else’s indictments.
Mind you, WikiLeaks appears as an unindicted co-conspirator in both the Stone and the GRU indictments, which may explain the connection.
But for some reason, Mueller thinks it important to note in Stone’s indictment that he pretended to believe Russia didn’t hack the DNC long after the hack had been attributed, without ever once mentioning that he had also spoken with the GRU persona dumping files.
Update: I’ve taken out the reference to Sam Nunberg, who says he’s not the person listed in this indictment.
Update: I’ve corrected this to reflect it was Jerome Corsi’s stepson who appeared before the grand jury Thursday. h/t AK
As I disclosed last July, I provided information to the FBI on issues related to the Mueller investigation, so I’m going to include disclosure statements on Mueller investigation posts from here on out. I will include the disclosure whether or not the stuff I shared with the FBI pertains to the subject of the post.