Judicial Watch Sues DOJ and Obtains Proof that Mark Meadows and His Propagandists Are Conspiracist Idiots
Just over a year ago, on August 11, 2018, the President accused the “Fake News Media” of refusing to cover “Christopher Steele’s many meetings with Deputy A.G. [sic] Bruce Ohr and his beautiful wife, Nelly [sic].” It was the first of around 26 attacks Trump launched against the Ohrs on Twitter over the year.
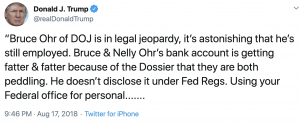
Trump reported that the FBI received documents from Ohr, which was true; the FBI asked for them as part of vetting the Steele dossier and understanding how it related to Fusion GPS’ other work. Trump complained that Nellie Ohr investigated members of his family for pay (true) and then fed it to her husband who gave it to the FBI; Trump didn’t reveal that FBI asked for the documents and that Steele’s efforts and Nellie’s were separate. The President claimed that Ohr “told the FBI it (the Fake Dossier) wasn’t true, it was a lie and the FBI was determined to use it anyway,” which was an exaggeration (Ohr said he believed that Steele believed his sources were telling him the truth, but Ohr described that all sorts of conspiracy theories could be spread from the Kremlin). Trump misquoted Ohr sharing with the FBI Steele’s concern that his sources would be exposed in the wake of the Jim Comey firing as a suggestion that Ohr was worried he, personally, would be exposed, which then got further misquoted by Fox propagandists. Trump accused the Ohrs of profiting off the dossier several times, “Bruce & Nelly Ohr’s bank account is getting fatter & fatter because of the Dossier that they are both peddling.”
Over the course of that year, Trump called for Bruce Ohr to be fired at least six times. “How the hell is Bruce Ohr still employed at the Justice Department? Disgraceful! Witch Hunt!”
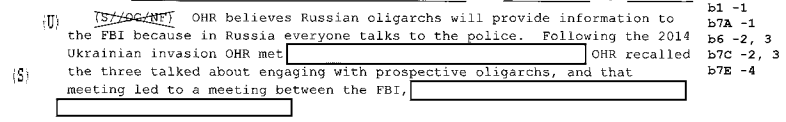
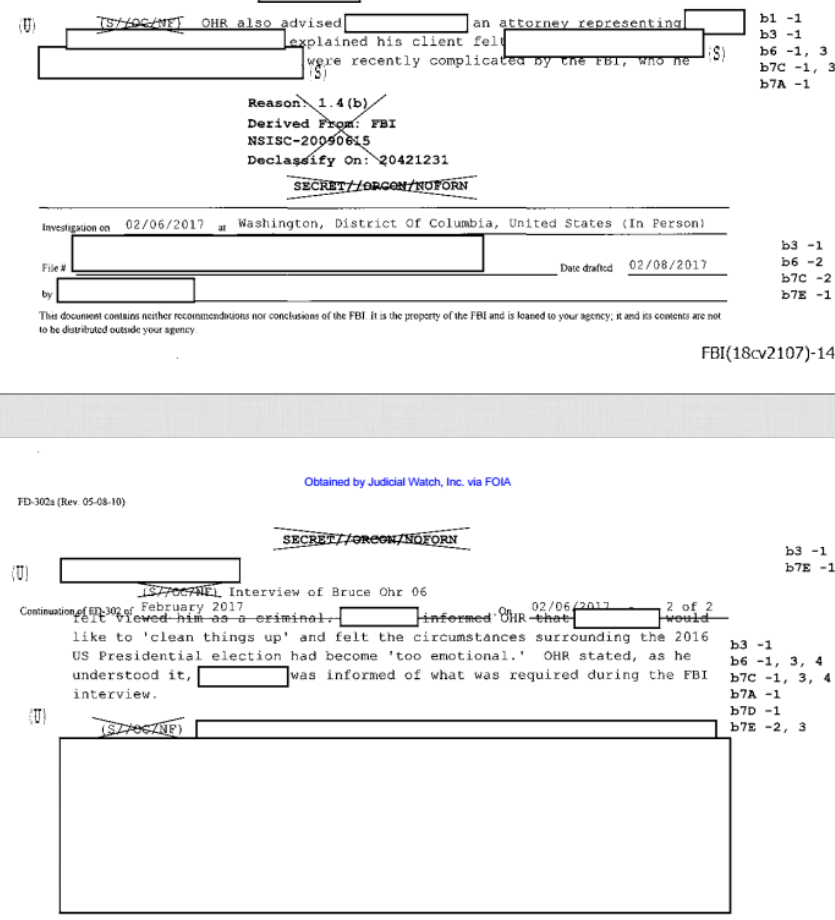
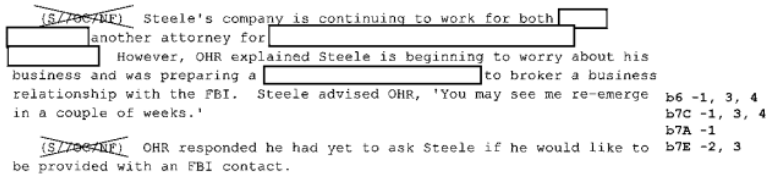
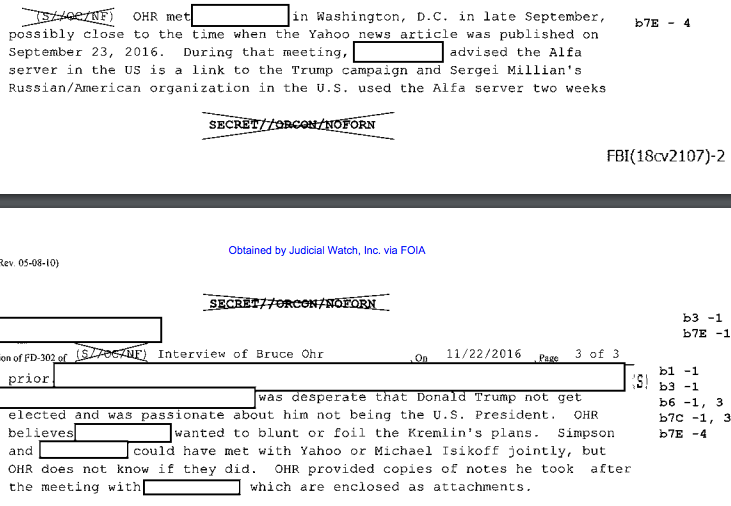
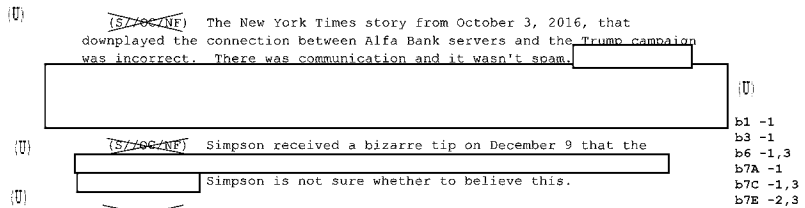
And yet, documents obtained under FOIA released by Judicial Watch in recent days (Ohr’s 302s, Ohr’s comms) show that virtually all the allegations made to fuel this year long campaign targeting Bruce Ohr are false. It is true that Bruce Ohr had ties to Christopher Steele going back almost a decade and was part of a network of experts combatting organized crime who compared notes (as was his wife Nellie, if the organized crime in question pertained to Ukraine or Russia). It is true that Ohr met with Steele in July 2016 and learned four things, two from the dossier (some version of Russian kompromat on Trump and allegations about Carter Page) and two not (Oleg Deripaska’s misleading claim to be prepping a legal attack on Paul Manafort and something related to Russian doping), which he passed on to the FBI. He also met and passed on information from Glenn Simpson later that fall, though given the team he met with at DOJ, the information may not have been sourced from the dossier and may have focused on the crimes Manafort has since pled guilty to. Neither of those meetings, however, are covered by the FOIAed documents. Moreover, Judicial Watch has not yet obtained documents from after May 2017, which (based on texts between the two that have been released) could show Steele trying to grill Ohr for details about ongoing investigations into his work. Maybe some day Judicial Watch will find a document that substantiates their attacks.
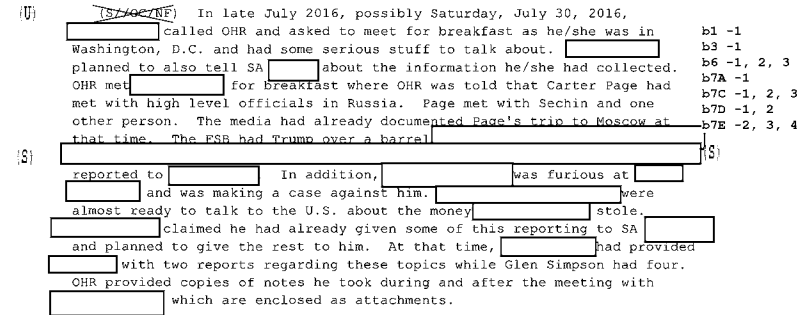
What the documents released so far don’t show is that Ohr served as some kind of “back channel” to the FBI via which Steele submitted new allegations. As I noted, Ohr’s 302s suggest there were three phases of communications covered by the 302s involving Steele (and Simpson) and Ohr. During the first — November 22 to December 20 — Ohr appeared to be helping the FBI understand Simpson’s project and Steele’s data collection process. He offered critical comments about Steele’s sourcing (noting that lots of fantastic stories come out of the Kremlin), appeared to prod Simpson for what he knew about Steele’s sourcing and then shared that information with the FBI, when he didn’t know answers to FBI questions (most notably, about whether Steele was involved in a key Michael Isikoff story), Ohr asked Simpson and reported the answer back to the FBI. Ohr offered up details about who else might have been briefed by Steele and why Steele was speaking to so many people.
Ohr would have done none of this if he were aiming to serve as a back channel to ensure Steele could continue to feed information to the FBI. The fact that members of the frothy right have, in recent days, focused on previously unknown details that Ohr shared with FBI’s Bill Priestap (such as when Victoria Nuland got briefed by Steele) is a testament to the fact that Ohr was not trying to hide a network of Steele contacts, but instead was helping FBI to understand them. Ohr cannot, simultaneously, be a source for unique knowledge for the FBI and at the same time be part of a Deep State plot aiming to feed the FBI new intelligence from Steele via as many different channels as possible.
Importantly, the main incidences where Ohr gave the FBI materials originating from Fusion — the materials include a timeline on Paul Manafort’s ties to oligarchs, a table showing Trump’s ties with suspect Russians, 137 pages of narrative backup for some of the table (part of which appears at PDF 216 to 299; Judicial Watch did not release this research as an independent link, presumably because it damages their narrative), and the latest version of the dossier from Simpson — came during that vetting period. Indeed, at the meeting where Ohr obtained a copy of the dossier from Fusion — according to his congressional testimony, at least, the only time he ever handled it — was the same meeting where he tried to get Simpson to tell him who Steele’s sources were (see PDF 33), information he passed onto the FBI. What the frothy right should do, if it had a single honest journalist left, would be to admit that Mark Meadows had them chasing a hoax for a year, but now that they can see the underlying evidence, it’s clear Meadows was wrong, lying, or perhaps opposed to the FBI doing the same kind of vetting that he imagines he himself to be doing.
Similarly, the frothy right is spinning what Nellie Ohr’s research shows in utterly deceitful ways. For much of the last year, the story was that Nellie’s work was an integral part of Steele’s dossier, a story that formed a critical part of any claim that Bruce Ohr would have some incentive to prop up the credibility of the dossier (which, as noted, the record shows he didn’t do). Her research shows that, in reality, there is little overlap between her research and Steele’s. There are over 75 names listed in her table of sketchy ties with Russia. The only identifiable overlap with the dossier are the Agalarovs, Mike Flynn, Paul Manafort, Sergei Millian (to the extent he really is one of the subsources for the dossier), and Carter Page. The Flynn and Manafort (and to some degree the Page) stuff goes beyond what is in the dossier.
In addition Nellie’s research includes others who should have been included in any solid HUMINT on what Trump was up to, starting with Felix Sater and Konstantin Kilimnik (but also including Michael Caputo and Giorgi Rtskhiladze). Chuck Ross notes these names in a piece on Nellie’s research, but doesn’t acknowledge the ways their inclusion undermines the conspiracy theories he has been peddling. I said in January 2018 that this open source research would probably have been more valuable for the election than the dossier, and I stand by that.
And look at the dates on Nellie Ohr’s research and the number of reports for each date (something else that Ross ignores the significance of):
- November 23, 2015 (12)
- December 14, 2015 (19)
- February 12, 2016 (8)
- February 13, 2016 (1)
- February 27, 2016 (1)
- March 4, 2016 (5)
- April 14, 2016 (2)
- April 22, 2016 (5)
- May 7, 2016 (1)
- May 13, 2016 (2)
- May 20, 2016 (1)
- May 27, 2016 (2)
- June 3, 2016 (1)
- June 10, 2016 (1)
- June 17, 2016 (4)
- June 24, 2016 (2)
- June 25, 2016 (3)
- July 1, 2016 (4)
- July 6, 2016 (3)
- July 9, 2016 (1)
- September 19, 2016 (2)
- September 22, 2016 (1)
Perhaps half of Nellie’s Ohr’s dated reports in this table date to before the Democrats started paying Fusion (that was sometime in April or May 2016, with Steele coming on around June 2016), and well more than half of the actual dated reports are from the primary period. That means that GOP billionaire Paul Singer, and not the Democrats, paid for much of the Nellie Ohr research in the table that the GOP is squawking about.
The GOP is squawking less about Nellie Ohr’s Manafort timeline (which is odd considering some of what Steele shared through Ohr consisted of Manafort details not reported in the dossier). But it’s worth mentioning that some of the same frothy right propagandists complaining here were instrumental in magnifying oppo research targeting John Podesta in 2016. The folks who made much of John Podesta’s stolen emails can’t complain about public source research focusing on Manafort’s corruption.
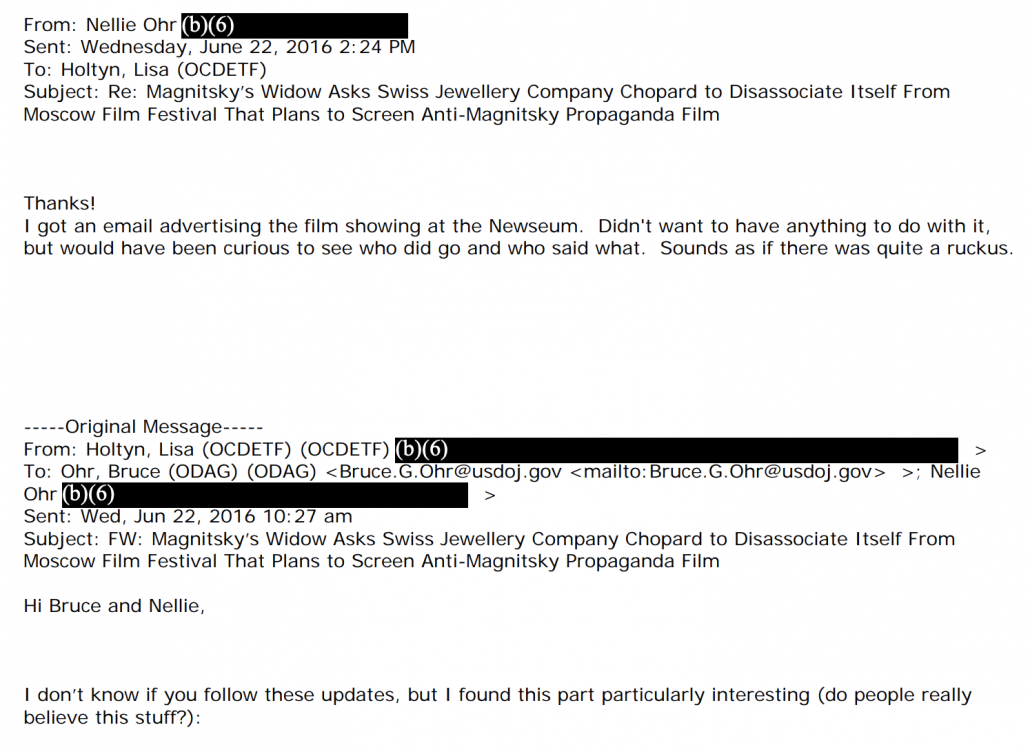
And for all the frothy right’s focus on Nellie Ohr’s interactions with Bruce’s colleague Lisa Holtyn (with whom Nellie clearly had a direct professional and personal relationship), they don’t mention this email to Holtyn, which suggests that Nellie has absolutely no clue about the connection that Fusion had with this anti-Magnitsky event that Natalia Veselnitskaya and Rinat Akhmetshin were involved in.
That provides some support to Simpson’s claim to Congress that the people working on the Trump oppo research were compartmented from those working on the Baker-Hostetler project tied to the June 9 meeting (though Nellie was never the most likely overlap).
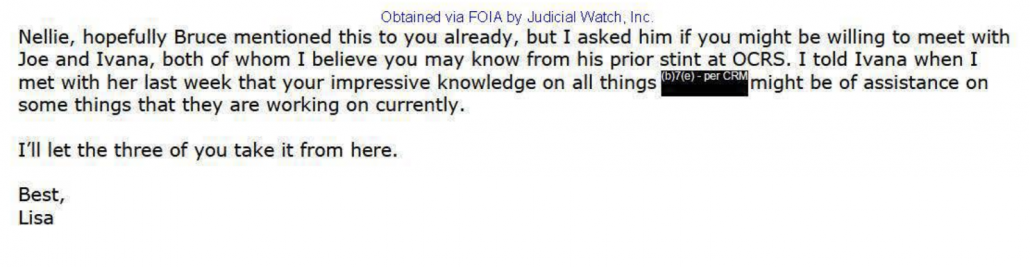
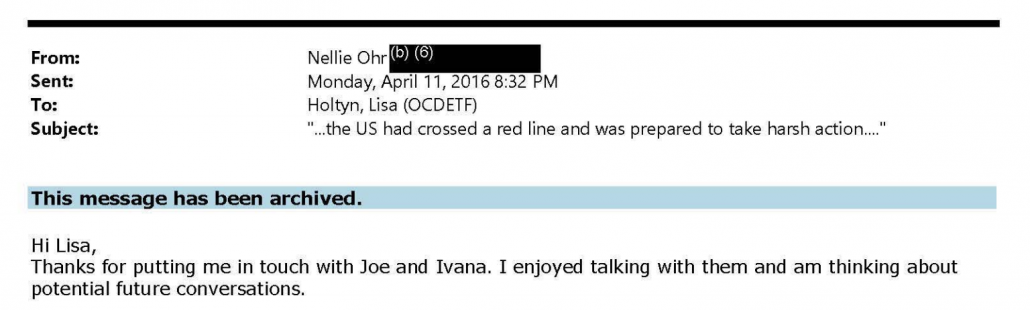
As to two smoking guns that Mark Meadows claimed to have found when he referred Nellie Ohr for criminal prosecution earlier this year, the first is that at Holtyn’s suggestion, Nellie met, informally, with two organized crime prosecutors, Joe Wheatley and Ivana Nizich, presumably to give them background on certain aspects of Russian and Ukrainian organized crime. Judicial Watch has focused on the set-up of the meeting, in which Bruce noted it should not be a conflict since Nellie would not be paid. They haven’t noted that Holtyn describes (PDF 31) her colleagues’ interest in the topic to be “some things that they are working on currently” which, if it’s a specific case, she’s careful not to mention directly, but sounds more like enterprise investigation. That kind of meeting is utterly consistent with Nellie’s claim to have no knowledge of ongoing investigations, Russian or otherwise.
Moreover, the aftermath of the meeting (PDF 24) certainly reflects that informal nature.
Meadows claims that this exchange (Nizich and Wheatley continued to exchange information from Nellie afterwards, but this is the only written discussion of a meeting) proves Nellie Ohr lied in this exchange with Democratic staffers Arya Hariharan and Susanne Sachsman Grooms last October.
Q You’ve never worked for the Department of Justice, correct?
A Correct.
Q You don’t currently work for them?
A Correct.
Q So you would not have any knowledge of what is going on in an ongoing investigation?
A Correct.
Ms. Sachsman Grooms. Just to make that one crystal clear, did you, at the time, that you were working for Fusion GPS have any knowledge of the Department of Justice’s investigations on Russia?
Ms. Ohr. No.
As to Meadows’ second allegation, he says that by sharing research on Zakhariy Kalashov, a Russian mobster, with Wheatley and Nizich, Nellie proved knowledge of an ongoing investigation and (he insinuates though doesn’t say directly) shared her Fusion research with people outside of Fusion and her spouse. (Best as I can tell, Judicial Watch hasn’t released this yet, but they have a habit of sitting on documents so it’s unclear if DOJ has released it to them.) If that’s true, Meadows must know Kalashov has some tie to Trump, which is not alleged in any of Nellie’s work for Fusion.
If it were true, I’m pretty sure it would have become a campaign issue.
Meadows has, at several times in his efforts to delegitimize the information sharing by a small network of people who compare notes on Russian organized crime, gotten shockingly close to suggesting that daring to investigate Russian criminals — whether they have any tie to Donald Trump or not — should itself be criminalized. This is one such instance.
But that’s not the most remarkable piece of evidence included these latest releases Judicial Watch that demolishes the attacks on the Ohrs.
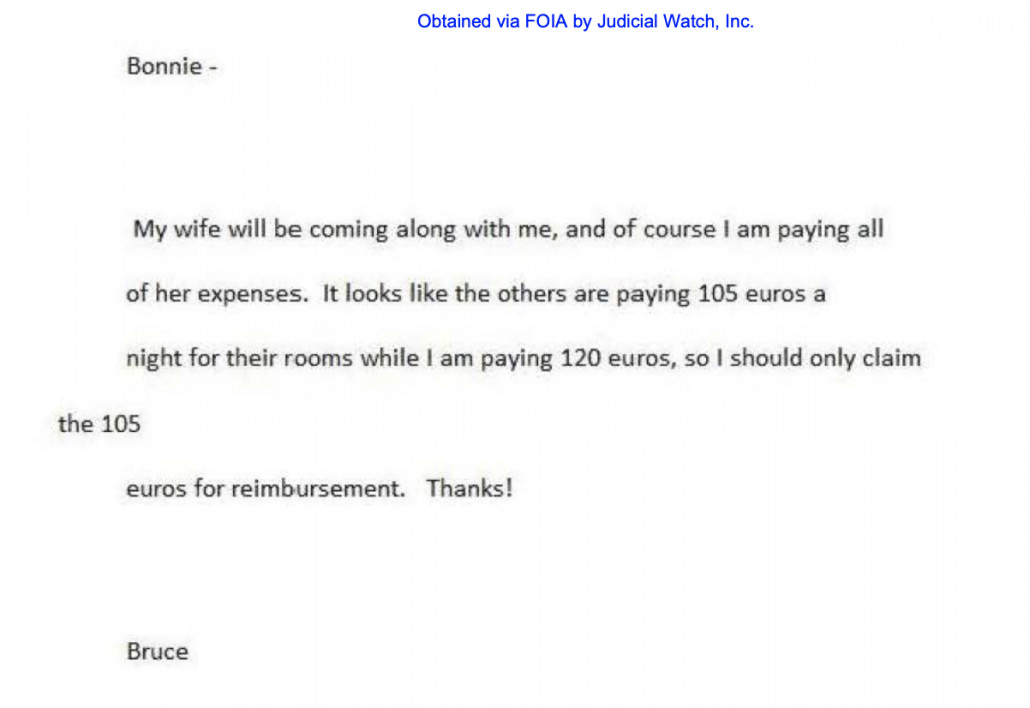
That majority of the documents involving Nellie Ohr turned over to Judicial Watch involve not — as you might expect if you read the frothy right — evidence of a Deep State plot. Rather, they are tedious discussions of Ohr’s travel plans, which he either forwarded to Nellie (perhaps because she scandalously likes to know what country her spouse is in or even likes to pick him up from the airport) or discussed the inclusion of Nellie on trips where spouses were invited. Bruce Ohr spends a lot of time figuring out what kind of per diem he’s permitted and seems to travel on a range of airlines (meaning he’s not maximizing frequent flier miles from his work travel, as most business travelers, myself included, like to do). But the most remarkable bit of tedium regarding travel — for a trip to Riga — shows that Bruce Ohr went to some effort to ensure he only claimed €105 a night reimbursement for hotel, rather than €120, because the additional €15 was a charge associated with Nellie’s inclusion (on the same trip, he also didn’t submit for reimbursement for parking at the airport).
This is a couple that has been accused, by the President of the United States — a guy who never met a grift he didn’t love — of sharing information on Russian criminals not because they want to keep the country safe, but to make their bank account “fatter & fatter.”
It turns out, instead, that they’re the kind of people who make sure taxpayers don’t pay an extra €30 for an overseas business trip.
Of course the frothy right hasn’t admitted how obscene it was for Donald Trump to accuse the Ohrs of self-dealing.
Who knows? Maybe Judicial Watch will one day discover the smoking gun that Meadows has been claiming to have found against the Ohrs. Maybe the details surrounding the 2016 communications or Steele’s efforts to undermine the investigation into his work will actually make the Ohrs into the villains they’ve been cast as for the last year.
And certainly, all that’s a different question than Simpson’s candor or the overall wisdom of Steele’s project.
But as far as the Ohrs go, what the evidence that Judicial Watch worked hard to liberate proves is that the President and Congressman Meadows owe this couple an apology — and the frothy right should stop prostrating themselves by parroting what Meadows tells them is there and begin describing all the ways these documents prove their past reporting to be a hoax.