In this post, I laid out how Sidney Powell used what should have been a reply in her effort to obtain what she called Brady information to instead lay out, for the first time, her argument about how Flynn was abusively caught in his own acts by mean FBI Agents out to get him, and so should have the two guilty pleas he made under oath thrown out. Powell also complains about a slew of things that happen in most FBI investigations, and pretends they’re specifically abusive when they happen with her client.
In this post, I’d like to unpack what Powell does with her so-called evidence, 16 exhibits purportedly included to support her case, but also largely provided to rile up the frothy right.
Virtually everything she claims — with the possible exception that Flynn’s 302 says he acknowledged calling Sergey Kislyak 4-5 times on December 29, 2016, but actually said he didn’t remember that– is not backed by her evidence. In several cases, she presents evidence that undermines her own claims. She supports her most central claim — that the FBI Agents introduced a claim about Flynn getting a response on UN sanctions — by arbitrarily cutting up notes and hiding the continuity of notes that in fact back the Agents.
Exhibit 1: A timeline
Exhibit 1 is a timeline that purports to show how the Deep State was out to get Flynn and how all the people involved in Flynn’s prosecution allegedly involved in abuse. Powell uses the timeline to suggest all the events that happened at DOJ and FBI over a two year was a focused effort to get her client and his boss.
The real evidence the government had long suppressed caused a cavalcade of major events—many within mere days of Mr. Flynn’s plea—and all unknown to him before it. Lisa Page, Special Counsel to Deputy Director McCabe, resigned; she had edited Mr. Flynn’s 302 and was part of the small, high-level group that strategically planned his ambush. Lead Agent Peter Strzok was demoted from the Mueller investigation and ultimately fired. Strzok, who had met extensively with McCabe and the high-level, small group, was primarily responsible for creating the only basis for the charge alleged against Flynn. [emphasis original]
But the timeline is not “evidence” at all. For example, she includes a slew of events that we know don’t relate to her narrative, but which she claims do, including:
- Andrew McCabe’s firing for (allegedly) lying to the Inspector General about leaking information that confirmed a criminal investigation into the Clinton Foundation during the campaign
- Lisa Page’s departure from Mueller’s team, which texts to Strzok that Powell chooses not to include makes clear was planned from the time she joined Mueller’s team
- Rachel Brand’s resignation (as well as the career moves of a bunch of other people that likely don’t relate to Flynn, but are probably best explained by Christopher Wray bringing in his own team)
The timeline includes notable gaps including:
- President Obama’s warning to Trump not to hire Mike Flynn, based off issues that did not relate to Trump
- Elijah Cummings’ letter to Mike Pence about Flynn’s problematic meetings with Turkey, which explains the urgency behind DOJ’s FARA questions
- Mention of the December 23 and 31, 2016 calls from Kislyak to Flynn, which he also lied about; the December 23 call is utterly central to one of Powell’s key claims against the FBI Agents
- Details around White House requests in early 2017 to see the information on Flynn, which explains some of the texts (indicating what a challenge it was to investigate Flynn and concerns about documenting his interview before he left) Powell elsewhere says are damning
- The John Dowd call to Rob Kelner pressuring him not to cooperate
The timeline includes evidence that conflicts with Sidney Powell’s argument, including:
- A quote from Strzok making it clear that in an unfiltered text to Page, he believed Flynn had lied
- A description of how Rudolph Contreras recused from the Flynn case as soon as it would have become clear to him that Strzok was involved
- A 302 from Lisa Page undermining her claim that there were “many” meetings to strategize on Flynn’s interview
Exhibit 2: Cherry-picked Strzok-Page texts
Exhibit 2 is a cherry-picked selection of texts from Peter Strzok and Lisa Page.
For example, Powell claims,
The belatedly-disclosed Strzok-Page texts make clear that the agents left the interview with a firm conviction Mr. Flynn was being honest, and they maintained that conviction despite strong expressions of disbelief and cries of “bullshit” from their colleagues.
But one of the texts she includes quotes Strzok describing his, “excitement knowing we had just heard him denying it all, knowing we’d have to pivot into asking.” That comment actually confirms that even in an unguarded moment, there was no doubt in Strzok’s mind that Flynn had lied about the events.
She claims that a text that very obviously pertains to Strzok’s ongoing efforts to pursue leakers — including leakers who harm Trump associates — and suggests it has something to do with animus against Flynn.
April 20, 2017, Strzok texts Page: “I had literally just gone to find this phone to tell you I want to talk to you about media leak strategy with DOJ before you go.” Ex. 2.
This text is instead proof that, rather than being part of a plot to leak information to harm Trump associates, Strzok and Page continued to pursue all leakers, including those damaging Trump associates.
Significantly, Powell does not submit a single text that shows animus towards Flynn personally, as opposed to Trump. Indeed, she includes a text discussing this article on how Trump picked Pence as a running mate; it mentions Flynn, but neither Page nor Strzok mention that (or any concern that he might have picked someone who was already regarded a counterintelligence concern).
Exhibit 3: Cherry-picked Comey memos
Exhibit 3 are two of Comey’s memos. I don’t think Powell ever gets around to using Comey’s first memo as proof FBI was using the briefing about the dossier to see how Trump would react (though the rest of her brief is consistent with that). Instead, she cites to the memos for two purposes, neither of which it supports. First, she uses it to make much of the fact that Comey briefed Trump on the dossier the day after he met with Obama’s National Security advisors.
Then Director Comey had briefed the President-Elect about these “salacious and unverified” allegations on January 6, 2017, a day after meeting in the Oval Office with President Obama, Vice-President Biden, Acting Attorney General Sally Yates, Susan Rice, James Clapper, and John Brennan. Ex. 3.
But of course, the timing has nothing to do with the dossier and everything to do with the fact that Comey, Clapper, and Brennan were briefing Trump on the same thing they briefed Obama on the day before: the preliminary results of the Intelligence Community Assessment. It’s evidence they were treating Trump as they should the incoming president, something that’s backed by other evidence.
She then uses the Comey memos (plus two Strzok 302s below) to support a footnote where Powell deliberately conflates what it takes to open a counterintelligence investigation (which, even ignoring how Powell claims one can only open an investigation if one has proof beyond a reasonable doubt about someone, can also be opened if someone is being targeted by foreign intelligence services) and what it takes to charge someone.
Under federal law, to establish that an American is acting as an agent of a foreign power, the government must show that the American is purposefully engaging in clandestine activities on behalf of a foreign power, and that it is probable that these activities violate federal criminal law. See FISA, Title 50, U.S. Code, Section 1801(b)(2). Mr. Comey and Mr. McCabe publicly admitted that in the summer of 2016, they took it upon themselves to single out four individuals associated with the Trump campaign for investigation. Admittedly, the FBI had no evidence that any of the four had committed a crime—much less that they “knowingly engage[d] in clandestine intelligence gathering activities for or on behalf of a foreign power.” Id; see Ex. 3.
The memo in no way supports the passage.
Powell unsurprisingly doesn’t include the two Comey memos that hurt her client’s claim. The January 27 memo describes Trump telling the FBI Director that, “he has serious reservations about Mike Flynn’s judgement,” which would seem to support FBI’s decisions to treat the Flynn matter seriously. In the February 8 one, Comey describes Reince Priebus asking if FBI has a FISA order targeting Flynn, something that would totally justify the FBI’s concerns about how they were dealing with and documenting an investigation of the National Security Advisor that Powell makes much of.
Exhibit 4: CNN article
Exhibit 4 is a CNN article quoting Strzok-Page texts where Page says the release of the Steele dossier may provide pretext to interview people, which is a clear reference to George Papadopoulos (everything in Steele about Flynn is OSINT). It also describes Strzok to be obviously aggravated by all the leaking going on, as well as discussions about how FBI tried to walk back a problematic NYT article that doesn’t mention Flynn, but instead focused on Paul Manafort and Roger Stone.
Exhibit 5: Peter Strzok’s 302 about Sara Carter and John Solomon’s propaganda
Exhibit 5 is a Peter Strzok 302 that Powell purports to include for what she claims is a quote from it.
In the next two weeks, there were “many meetings” between Strzok and McCabe to discuss “whether to interview [] National Security Advisor Michael Flynn and if so, what interview strategies to use.” Ex. 5.
Except that’s an egregious misquote of what the 302 actually says, which is,
I have attended many meetings with DD McCabe regarding Russian influence investigations, including meetings which discussed whether to interview former National Security Advisor Michael Flynn and if so, what interview strategies to use.
The “many” here refers to meetings about Russian influence generally, just a subset of those many meetings relate to Flynn. Nor does the 302 reflect that all those meetings happened in the two weeks before Flynn’s interview.
Powell also uses this 302 to claim that “they all knew” they had no basis to open the CI exhibit, as noted above. The only way this could be used to support the case is to take allegations included in a Sara Carter/John Solomon report claiming bias which (per the government’s last filing) was repeatedly debunked after this time, as truthful, even though Strzok says repeatedly in the 302 they’re not.
Exhibit 6: Peter’s Strzok’s 302 on his own role in the investigation
Exhibit 6 is the 302 recording a July 19, 2017 interview of Strzok describing his role in starting the investigation. Powell uses it, rather than “a seven-line summary of Ms. Yates statement,” they received in discovery, to support a claim about why Sally Yates was angry that the FBI interviewed Flynn.
Comey and McCabe were executing their own agenda—not investigating a crime. This is why, in Brady evidence still suppressed, Deputy Attorney General Sally Yates candidly opined that the interview “was problematic” and “it was not always clear what the FBI was doing to investigate Flynn.”8 This is also why Strzok admitted that Yates “was not happy” to learn of the interview and PDAG Axelrod argued with FBI General Counsel James Baker about the FBI’s unilateral decision to interview Flynn. Ex. 6.
To prove she needed the full Yates interview, Powell would need to describe what’s inadequate in the Yates summary, but she chooses not to.
Powell also uses this 302 to support the claim that “they all knew” they had no basis for a counterintelligence investigation, which it doesn’t support.
The other things that Powell uses this exhibit to prove is that the FBI — as it does for all witnesses!!!! — tried to stage the interview to be as useful as possible.
They purposely did not tell him they were investigating him and strategized at length to avoid raising any concerns. Ex. 6 (“Flynn was unguarded and clearly saw the FBI agents as allies.”).
[snip]
The agents did three briefings the day of the interview. They reported he had a sure demeanor, and he was telling the truth or believed he was—even though he did not remember it all. Ex. 6.
[snip]
” They purposely did not tell him they were investigating him and strategized at length to avoid raising any concerns. Ex. 6 (“Flynn was unguarded and clearly saw the FBI agents as allies.”).
Powell slightly misrepresents this, describing the FBI agents as believing that Flynn was telling the truth instead of saying, “both had the impression at the time that Flynn was not lying or did not think he was lying,” and she leaves out key parts of the rest of the description, including that he “did not give any indicators of deception,” which changes the meaning somewhat. In general, however, the description of how FBI planned the interview doesn’t prove bias at all on the part of the FBI; it proves they treated Flynn like they treat everyone.
Exhibit 7: Two pages of the Steele dossier
Exhibit 7 is the two pages of the Steele dossier which include the sole reference in it to Flynn.
Kremlin engaging with several high profile US players, including STEIN, PAGE, and (former DIA Director Michael Flynn), and funding their recent visits to Moscow.
[snip]
Speaking separately, also in early August 2016, a Kremlin official involved in US relations commented on aspects of the Russian operation to date. Its goals had been threefold — asking sympathetic US actors how Moscow could help them; gathering relevant intelligence; and creating and disseminating compromising information (“kompromat”). This had involved the Kremlin supporting various US political figures, including funding indirectly their recent visits to Moscow. S/he named a delegation from Lyndon LAROUCHE; presidential candidate JILL STEIN of the Green Party; TRUMP foreign policy adviser Carter PAGE; and former DIA Director Michael Flynn, in this regard and as successful in terms of perceived outcomes.
According to Powell’s own theory, the RT event took place long after the US government came to be concerned about Flynn as a CI threat, and according to her own claims, Flynn was already on Trump’s campaign at this time, so the FBI would have been reviewing these publicly known facts in real time. And while the Kremlin only indirectly funded these trips, both the Page and the Stein/Flynn trips were paid for, albeit by cut-outs. This is actually an instance where the Steele dossier only repeats generally true, OSINT facts.
Nevertheless, Powell uses it to misrepresent both the timing of Nellie Ohr’s research on Flynn (most of her research was done in 2015 and early 2016, and so was funded by Paul Singer) and why her spouse shared it with the FBI (to help them vet the dossier).
It was only much later the defense learned what the FBI already knew: This document had been bought and paid for by the Clinton campaign and the DNC. Both the FBI and Fusion GPS hired former British spy Christopher Steele. Fusion GPS was on the Clinton payroll, and it also hired Nellie Ohr—a Russia specialist with CIA ties whose husband Bruce was the fourth highestranking official in DOJ. Ms. Ohr was researching Mr. Flynn also, and his name appears twice in the “Steele dossier.” Ms. Ohr and Steele funneled their “work” through Bruce Ohr in a backchannel to the FBI, long after the FBI fired Steele for lying. Ex. 7;
Powell also uses it to demand a letter from MI6 on Steele that the NYT recently reported said that Steele was honest, but displayed questionable judgement (of the sort that might lead him to trust Oleg Deripaska).
Mr. Horowitz has asked witnesses about an assessment of Mr. Steele that MI6, the British spy agency, provided to the F.B.I. after bureau officials received his dossier on Mr. Trump in September 2016. MI6 officials said Mr. Steele, a Russia expert, was honest and persistent but sometimes showed questionable judgment in pursuing targets that others viewed as a waste of time, two people familiar with the assessment said.
Whatever Carter Page’s possible beef with the dossier, all the dossier does on Flynn is report what the FBI was (even according to Powell’s claims) already reviewing with Flynn. And a letter saying that MI6 thought Steele was honest is not going to change that.
Exhibit 8: Not-Comey’s description of Comey’s action
Exhibit 8 is Josh Campbell’s description of how Comey decided to send FBI Agents to interview Flynn without going through the White House Counsel (which Andrew McCabe nevertheless gave Flynn the opportunity to ask to do).
The government did not disclose this to Mr. Flynn until after Mr. Comey bragged about his breach on national television—not because Mr. Van Grack was complying with this Court’s order. This short video (https://www.youtube.com/watch?v=NxNhjFrjXqI) reveals Mr. Comey’s deliberate disregard for DOJ and FBI rules. In fact, Mr. Van Grack only disclosed a bland summary four days after Comey gloated about it on national television to a laughing audience— four days before Mr. Flynn’s scheduled sentencing, and because this Court entered its minute order of December 12, 2017. Dkt. 10. Mr. Flynn seeks disclosure of the full report of Mr. Comey’s conduct, any memos, notes, and 302s documenting his decision, which was admittedly the subject of “many intensive discussions” within the FBI. There must be at least notes of several others, including Comey’s Special Assistant Mr. Campbell, that document the efforts directed against Mr. Flynn. Ex. 8;
Powell uses Campbell’s description, which includes the line “screw it,” rather than a transcript of Comey’s statements that she links, which are far less inflammatory, presumably to assume that Campbell must have taken official notes of the many conversations he claims happened.
But this exhibit, like all the others on how FBI tried to optimize this interview, only shows that the FBI treated Flynn like they’d treat anyone.
Exhibits 9 and 10: Joseph Pientka and Strzok’s notes
Exhibits 9 and 10 are the notes that Joe Pientka and Strzok made, respectively, about the Flynn interview. This is the core of any legitimate argument Powell has, though here, as elsewhere, part of what she’s complaining about is normal FBI process where two Agents do an interview and then write up a 302.
Only the junior agent was taking notes during the interview. Strzok’s 302 of July 2017 says that he was handling the interview and his partner was taking notes. A 302 is to be written into Sentinel within five days. Notes are to be signed and dated by the notetaker. Inexplicably, we have two sets of notes with significant redactions—neither of which is signed and dated as required. Exs. 9, 10. Agent Strzok’s notes are far more detailed, lengthy, and written in a way that would not appear to be physically possible to write in a contemporaneous, casual setting. Ex. 10.
Powell’s claims that these notes weren’t dated or signed might have merit, though given that virtually all of her claims misrepresent key details, it’s hard to tell, especially with the way she presents the notes in screen caps followed by transcriptions.
She makes two other substantive claims about the notes. First, she claims that the notes (plus a copy showing changes made on February 10, which is Exhibit 11) falsely claim that Flynn stated that he did not ask for any specific action regarding the UN vote on Egypt’s resolution on illegal Israeli settlements.
Overnight, the most important substantive changes were made to the Flynn 302. Those changes added an unequivocal statement that “FLYNN stated he did not”—in response to whether Mr. Flynn had asked Kislyak to vote in a certain manner or slow down the UN vote. This is a deceptive manipulation because, as the notes of the agents show, Mr. Flynn was not even sure he had spoken to Russia/Kislyak on this issue. He had talked to dozens of countries. Exs. 9, 10, 11.
[snip]
Whatever Mr. Flynn said to anyone regarding the UN issues had nothing to do with the FBI’s alleged “investigation” about the 2016 election and could not be the basis for false statements “material” to that issue. According to the notes, he was not even sure he had spoken to Kislyak on that issue. Exs. 9, 10.
Perhaps Sidney Powell is this dumb, or perhaps she just thinks Emmet Sullivan is, but this is thoroughly dishonest. What Pientka’s notes show is that when Flynn was asked to offer up what contacts he had had with Kislyak, he described the following ones post-election:
- A condolence call after Russia’s Ambassador to Turkey was killed on December 19, which Flynn described as happening “before Xmas, Mid-December day after assassination”
- A condolence call after Russia’s military band crashed in Syria on Christmas Day
- A single call on December 29
Then, when the Agents cue him again, he admits to:
- The in-person Trump Tower meeting about setting up a back channel around December 1
Then, when asked about the UN vote, Flynn starts by saying, “that’s a good reminder,” then admits to calls with others, makes representations generally about all his calls regarding the UN vote where he claims he only asked about people’s positions, not to abstain, then ends by saying “Appreciate you reminding me that was another convo.” In context, that probably records — and at the very least is consistent with — an admission he spoke with Russia among his UN calls. And given his description of it occurring “Maybe Thurs-Fri prior to Xmas,” he dates it to December 22 or 23, when he claims his call was offering condolences for the assassination. (Powell splits these two up in Pientka’s notes, as she also does with the same exchange in Strzok’s notes, but the flow is clear; this is clearer in the full version of Strzok’s notes submitted with Exhibit 16)

Furthermore, Powell claims that “he talked to dozens of countries,” which she pulls from his comment about his general interactions with other countries. The notes make clear that he instead said he “talked to a bunch” of countries. It’s clear that Powell’s claim he spoke to “dozens” is false in any case, because Flynn was talking about the UNSC, on which there are just 15 members, and Flynn described how those numbers worked out — and the need to get just 5 to abstain — for the Agents.
In other words, what the notes actually show is Flynn lying about his reason for the call, being given an opportunity to fix the lie about the subject of the call, then making claims that would apply to all his UN calls (including the Russian one) that were themselves false.
In short, the notes actually appear to back the Agents.
Exhibit 11: Redline of 302
Exhibit 11 is a redline of Flynn’s 302 which, in Powell’s theory, was changed on February 10, after the press reported that Flynn didn’t speak about sanctions (as if the FBI would respond to press reports on something they already knew to be a lie), to make it more damning.
She’s concerned about two changes made in this section pertaining to the UN vote.
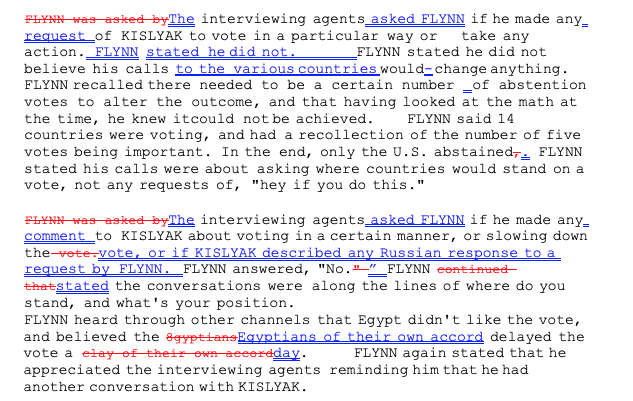
This section is the basis of the most inflammatory claim Powell made.
Those changes added an unequivocal statement that “FLYNN stated he did not”—in response to whether Mr. Flynn had asked Kislyak to vote in a certain manner or slow down the UN vote. This is a deceptive manipulation because, as the notes of the agents show, Mr. Flynn was not even sure he had spoken to Russia/Kislyak on this issue. He had talked to dozens of countries. Exs. 9, 10, 11.
Second, they added: “or if KISLYAK described any Russian response to a request by FLYNN.” That question and answer do not appear in the notes, yet it was made into a criminal offense. The typed version of the highly unusual “deliberative” 302 by that date already included an entire section from whole cloth that also serves as a criminal charge in the Information and purported factual basis regarding “Russia’s response” to any request by Flynn. The draft also shows that the agents moved a sentence to make it seem to be an answer to a question it was not. Exs. 9, 10, 11
As shown above, because Flynn’s comments about his asks regarding the UN vote apply to all the countries in question, it would apply to the Russian one as well.
But as shown, the only way Powell can sustain this claim is to separate Flynn saying three things that are clearly all about the same topic into three different sections of her transcription:
- That’s a great reminder
- No hey if you do this
- Appreciate you reminding me that was another convo

The “Appreciate you reminding me that was another convo” certainly is consistent with the December 23 call Kislyak made to say they weren’t going to abstain, because Flynn talks about it happening the Thurs-Fri before Xmas, which would be consistent with the ask on Thursday, December 22 and the response on Friday, December 23.
Note, too, that the charge that Flynn lied about getting a response from Russia would also apply to whether Flynn acknowledged getting a response back from Kislyak after the December 29 call. As she did with the UN notes, she splits these up too, so separates where Pientka notes “no recollection of that” from where he records Flynn saying, “Nothing long drawn out don’t do something.” Her transcription of “RePP?” and “I don’t, the conversation was on” doesn’t account for the possibility that this is a question — with question mark included — about Russia’s response.
Powell makes a more credible argument about the Agents recording that Flynn affirmatively stated he made 4-5 calls to Kislyak on December 29
Notes by both agents state that Mr. Flynn does not remember making four to five calls to Ambassador Kislyak from the Dominican Republic, where he was on vacation, but that if he did so, it was because phone service was poor and he kept getting dropped. “I don’t remember making 4-5 calls. If I did lousy place to call.” The final 302 states the opposite: “Flynn remembered making four to five calls that day about this issue, but that the Dominican Republic was a difficult place to make a call as he kept having connectivity issues.” Ex. 11. This dramatically demonstrates the wrongheadedness of allowing a 302 to create a federal felony.
But this issue is not an editing one, as the draft doesn’t change on this point.

More importantly, it’s not — as the UN question is — a charged lie.
Powell is right that the problem with charging false statements off a 302 is that the editing process is human, but that doesn’t change that the notes clearly back that Flynn told numerous material lies in his interview, and she doesn’t actually claim he didn’t.
Exhibit 12: Lisa Page rebuts Powell’s claim of “many” meetings to strategize Flynn’s interview
Exhibit 12 is a 302 with Lisa Page that, among other things, proves that contrary to claims the frothy right has made about Mueller’s team not checking about Strzok bias affecting the impact of the Flynn interview, Mueller’s team instead interviewed Page to check just that.
The 302 also disproves Powell’s claim that Strzok claimed he had attended “many” meetings about how to handle the Flynn interview. As reflected in Page’s telling, there was a meeting the night before, and one after the interview.
Powell doesn’t reveal that this 302 damages her story in key ways. Instead, she seems to include it to substantiate this claim:
Lisa Page, Special Counsel to Deputy Director McCabe, resigned; she had edited Mr. Flynn’s 302 and was part of the small, high-level group that strategically planned his ambush.
But she doesn’t actually cite the exhibit here. Nor does she in a later reference to Page editing the 302.
And for his third production, it gave the defense two pages on October 4, 2018. These go precisely to the issue of McCabe’s Special Counsel Lisa Page editing the Flynn 302. Ex. 2.
But in the second instance, the 302 actually shows that Brandon Van Grack provided Flynn texts reflecting Page editing Flynn’s 302 even before they had interviewed her (on October 25) to understand what they meant. That is, this detail shows how responsive Van Grack was, not that he was slow in turning things over.
In short, there’s no basis to believe Page altered the 302. Her edits, if they were actually incorporated, went through Bill Priestap, not Strzok. And she told the FBI that she would often edit things he wrote for grammar.
But unlike the frothy right, which has been harping on this point all weekend, Sullivan may never refer to that 302, because Powell didn’t appear to cite it.
Exhibit 13: WaPo reports on the Strzok-Page texts
Exhibit 13 is a WaPo report describing that Mueller reassigned Strzok in the wake of the discovery of his texts with Page. Powell provides this to substantiate a theory that Mueller’s prosecutors were pressuring Flynn to plead guilty knowing this would come out.
Not only did Mr. Van Grack not disclose a single text message before Mr. Flynn agreed to plead guilty, but Special Counsel apparently managed to control the press on the issue until the plea was entered on December 1, 2017, in Judge Contreras’s court. It defies credulity to suggest that it was only unlucky for Mr. Flynn that the story broke the very next day. Part of the evidence we request includes communications between the press and SCO, which will likely establish that Special Counsel intensified pressure on Mr. Flynn to plead immediately while it was pressuring the press not to explode the truth that destroyed the entire case. Karoun Demirjian, Top FBI official assigned to Mueller’s Russia probe said to have been removed after sending anti-Trump texts, THE WASH. POST (Dec. 2, 2017), https://www.washingtonpost.com/world/national-security/two-senior-fbiofficials-on-clinton-trump-probes-exchanged-politically-charged-texts-disparagingtrump/2017/12/02/9846421c-d707-11e7-a986-d0a9770d9a3e_story.html; MTC 11; Ex. 13.
Unfortunately for Powell, that doesn’t change the fact that according to her own timeline, Van Grack had already disclosed this three days earlier, and that the reason the texts came out is because Rod Rosenstein okayed their release in probable violation of the Privacy Act, something that Mueller’s team probably had no way of anticipating.
Exhibit 14: The InfoWars event Flynn co-headlined with Ray McGovern and Julian Assange
Exhibit 14 consists of materials from Flynn’s speaker’s bureau, which Powell submits to show that those events were solidly in the mainstream (which is absolutely true of the Kaspersky event).
Mr. McCabe pointed to Mr. Flynn’s “very public interactions with Vladimir Putin and other Russians.” These “interactions” seem to have arisen from the work of CIA/FBI operatives Stefan Halper and Joseph Mifsud, and bookings made by Mr. Flynn’s American speakers’ bureau, Leading Authorities (which books engagements for countless former government officials and prominent people). Leading Authorities booked him for three events with “Russian connections”: one in Moscow for RT and two in Washington. All were well attended by prominent persons from around the world because of the important issues discussed and the presence of other recognized experts on the programs. See Ex. 14; MTC 4, 16.
Yet among the other things these materials reveal are that the RT event featured Oliver Stone and Max Blumenthal on InfoWars (at a time when Russia had already kicked off its 2016 InfoWar against Putin).

It also featured Julian Assange and Ray McGovern on a panel about security and surveillance.

His talk to Volga-Dnepr Airlines was not recorded or open to the media.

The RT materials, while already broadly public, are especially damning, as they effectively show that Russia orchestrated his appearance, right alongside Putin, at the same event which a bunch of people who would later be part of the effort to deny Russia’s role in this infowar. A number of these people have been friends of mine (though they’re also among the people who’ve attacked me most baselessly once I started saying publicly that Russia did the hack), but they’re in no way the best experts to talk about infowars or how to balance privacy and counterterrorism.
Exhibit 15: Proof that Mueller’s team provided discovery before Flynn pled guilty a second time before Sullivan
Exhibit 15 is another timeline, this one providing the dates — but not the substance — of what Mueller provided in discovery in response to Emmet Sullivan’s order (note: it also gets at least some of the dates wrong, even as compared to her other timeline).
Powell claims in her brief that Flynn didn’t get all this material before he pled guilty the first time.
Neither Mr. Flynn nor his former counsel had any of these documents or knowledge of the plethora of information discussed above when Mr. Flynn entered his plea.
But Powell’s own timeline shows that every installment of the government’s production save one preceded the date last year when Flynn pled guilty again to Emmet Sullivan.
The exception is material handed over on August 16 of this year that relates to Flynn’s time at DIA which (given that it dates to at least two years before he committed the crimes in question) cannot be relevant to his crimes. Indeed, the government says that some of it is inculpatory.
Request #15: The government is not aware of any information in possession of the Defense Intelligence Agency that is favorable and material to sentencing, including the information that the government provided on August 16, 2019. Specifically, the information of which the government is aware, including that August 16 production, is either inculpatory or has no relevance to the defendant’s false statements to the FBI on January 24, 2017, or to the FARA Unit.
In short, Powell’s own timeline shows that the government complied with Sullivan’s standing order before Flynn pled guilty before Sullivan.
Exhibit 16: The handwriting analysis that doesn’t even try to disprove Strzok
Finally, there is Exhibit 16, a declaration from a handwriting analyst. Powell includes it to substantiate a demand for Strzok’s original notes of his interview with Flynn to investigate an “anomaly” that she doesn’t describe (making this request moot from a Brady standpoint).
Agent Strzok’s notes are far more detailed, lengthy, and written in a way that would not appear to be physically possible to write in a contemporaneous, casual setting. Ex. 10. The defense requests production of the actual, original notes, and handwriting samples of Strzok of contemporaneous and non-contemporaneous notes to evaluate another anomaly that further calls into question the entire effort by the FBI to manipulate and set up Mr. Flynn, and its report of that interview. Ex. 16.
But as her expert lays out, getting Strzok’s original notes would not be enough, because he would also need a baseline of how Strzok takes notes.
If additional comparable6 notations of Agent Strzok written under similar conditions could be obtained and submitted for analysis, it may be possible to determine whether the (Q-1) notations were prepared as purported. In consideration of both the observations made, as well as limitations present, further analysis of the original evidence would likely be necessary to support any definitive conclusions in this matter.
Ultimately, her expert says he can’t make any conclusions about whether the notes were “written during the course of the January 24th interview, or prepared at a subsequent time period.”
Based upon the inherent limitations arising from the examination of non-original evidence, compounded with the lack of any known comparison handwritten notations of Agent Peter Strzok (i.e., other non-contested handwritten notations prepared under like conditions), it has been determined that no conclusion can be rendered as to whether the submitted (Q-1) notations were written during the course of the January 24th interview, or prepared at a subsequent time period.
But as Powell makes clear in the very same paragraph where she makes this demand, no one claimed that Strzok wrote these notes during the interview. Only Pientka’s notes were taken during the interview (which is, again, one of those potentially bad things that is normal for FBI interviews that Powell thinks shouldn’t happen with her client).
Only the junior agent was taking notes during the interview. Strzok’s 302 of July 2017 says that he was handling the interview and his partner was taking notes.
So Powell uses this expert to claim she needs the original of Strzok’s notes to prove that he wrote them at a time he didn’t write them.
Which sounds like the definition of sanctionably frivolous behavior.