As I noted in my last post, DOJ’s Inspector General recently created a page showing their ongoing investigations. It shows some things not described in Inspector General Michael Horowitz’ last report to Congress.
As I noted in my last post, DOJ’s Inspector General recently created a page showing their ongoing investigations. It shows some things not described in Inspector General Michael Horowitz’ last report to Congress.
Of particular interest is this investigation.
Administrative Subpoenas
The OIG is examining the DEA’s use of administrative subpoenas to obtain broad collections of data or information. The review will address the legal authority for the acquisition or use of these data collections; the existence and effectiveness of any policies and procedural safeguards established with respect to the collection, use, and retention of the data; the creation, dissemination, and usefulness of any products generated from the data; and the use of “parallel construction” or other techniques to protect the confidentiality of these programs.
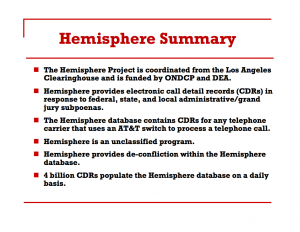
The description doesn’t say it, but this is Hemisphere, the program under which DEA submits administrative subpoenas to AT&T for phone records from any carrier that uses AT&T’s backbone. DEA gets information matching burner phones as well as the call records. In addition, it gets some geolocation — and continued to increase what it was getting even after US v Jones raised concerns about such tracking.
The presentation on Hemisphere makes it very clear the government uses “parallel construction” to hide Hemisphere.
Protecting the Program: When a complete set of CDRs are subpoenaed from the carrier, then all memorialized references to relevant and pertinent calls can be attributed to the carrier’s records, thus “walling off” the information obtained from Hemisphere. In other words, Hemisphere can easily be protected if it is used as a pointed system to uncover relevant numbers.
Exigent Circumstances — Protecting the Program: In special cases, we realize that it might not be possible to obtain subpoenaed phone records that will “wall off” Hemisphere. In these special circumstances, the Hemisphere analyst should be contacted immediately. The analyst will work with the investigator and request a separate subpoena to AT&T.
Official Reporting — Protecting the Program: All requestors are instructed to never refer to Hemisphere in any official document. If there is no alternative to referencing a Hemisphere request, then the results should be referenced as information obtained from an AT&T subpoena.
And this is not the only area where DEA Is using parallel construction to hide where it gets its investigative leads. Reuters reported in August that DEA also uses parallel construction to hide the leads it gets from purportedly national security-related wiretapping.
A secretive U.S. Drug Enforcement Administration unit is funneling information from intelligence intercepts, wiretaps, informants and a massive database of telephone records to authorities across the nation to help them launch criminal investigations of Americans.
Although these cases rarely involve national security issues, documents reviewed by Reuters show that law enforcement agents have been directed to conceal how such investigations truly begin – not only from defense lawyers but also sometimes from prosecutors and judges.
The undated documents show that federal agents are trained to “recreate” the investigative trail to effectively cover up where the information originated, a practice that some experts say violates a defendant’s Constitutional right to a fair trial. If defendants don’t know how an investigation began, they cannot know to ask to review potential sources of exculpatory evidence – information that could reveal entrapment, mistakes or biased witnesses.
[snip]
The two senior DEA officials, who spoke on behalf of the agency but only on condition of anonymity, said the process is kept secret to protect sources and investigative methods. “Parallel construction is a law enforcement technique we use every day,” one official said. “It’s decades old, a bedrock concept.”
A dozen current or former federal agents interviewed by Reuters confirmed they had used parallel construction during their careers. Most defended the practice; some said they understood why those outside law enforcement might be concerned.
Presuming that Horowitz is investigating whether DEA’s extensive use of parallel construction complies with the Constitution (and not, as is possible, whether the sources of this information are being adequately buried), this is welcome news indeed.
But it’s also one of several reasons why I’m particularly alarmed, in retrospect, that Horowitz is complaining about his ability to get grand jury information without having to get either Attorney General Holder or Deputy Attorney General James Cole to personally approve it.
After all, the only way you can learn what truly happens in prosecutions that have used parallel construction to hide their sources is to work backward from the actual prosecution. That would require seeing what the grand jury saw, and what DEA and other agencies had before they got to the grand jury stage. Furthermore, understanding how DEA uses parallel construction would require really broad access to investigations, as drug cases involve large networks of people. That’s a lot of requests for information Horowitz would, under the current system, be required to get.
And there’s one more thing that likely makes this problem even worse.
As NYT reported in its story on Hemisphere, the actual database is not funded by DEA, but rather by the White House Drug Czar (ONDCP) under the High Intensity Drug Trafficking Area program.
Mr. Fallon said that “the records are maintained at all times by the phone company, not the government,” and that Hemisphere “simply streamlines the process of serving the subpoena to the phone company so law enforcement can quickly keep up with drug dealers when they switch phone numbers to try to avoid detection.”
He said that the program was paid for by the D.E.A. and the White House drug policy office but that the cost was not immediately available.
Officials said four AT&T employees are now working in what is called the High Intensity Drug Trafficking Area program, which brings together D.E.A. and local investigators — two in the program’s Atlanta office and one each in Houston and Los Angeles.
This has always seemed like a ploy to put the program — which parallels earlier dragnet efforts done solely on Executive authority — in the White House, where it is immune from FOIA and even Congressional oversight.
I can well imagine DEA arguing that Horowitz cannot touch anything having to do with HIDTA (and therefore with Hemisphere) because it is a White House, not DEA, program. (Note, in Horowitz’ testimony he said, in addition to his difficulties getting grand jury information, “We have had similar issues raised regarding our access to some other categories of documents.”) Horowitz’s investigation of the “legal authority” for the program may well be stymied by claims of Executive Privilege too.
Michael Horowitz appears to be attempting to conduct a badly needed investigation that examines potentially grave Constitutional problems with our Drug War. Will Eric Holder permit him to do that work?
Update: I neglected to link to this post from bmaz right after the Reuters report came out. As he says, DEA has been doing this for decades. Also, read this post describing a case EFF and ACLU are intervening in, in which there is no legal process shown for a lot of the phone records provided in discovery. This is probably the kind of case we’re looking at with Hemisphere.