As I have repeatedly noted, I think President Obama will protect John Brennan — and the CIA more generally — because of the mutual complicity built in between CIA and the White House over covert ops.
It’s not just that CIA knows the full details of the drone killings Obama authorized on his sole authority. It’s also that the CIA is still protecting the Office of the Presidency’s role in torture by withholding from the Senate documents over which the White House might — but did not formally — claim Executive Privilege. Obama did the same thing when he went to some lengths to prevent a very short phrase making it clear torture was Presidentially-authorized from being released in 2009; it wasn’t just the Finding that still authorized his drone strikes the President was protecting, but the Office that George Bush sullied by approving torture.
I also think Obama will stand by Brennan because they have worked closely so long Brennan is one of Obama’s guys.
Bloomberg View’s Jonathan Bernstein doesn’t agree, however. After dismissing Conor Friedersdorf’s version of the mutual incrimination argument, he suggests Obama is simply demonstrating to the national security bureaucracy he’s on their side.
Obama is concerned -– in my view, overly so -– with demonstrating to the intelligence bureaucracy, the broader national security bureaucracy, and the bureaucracy in general, that he is on their side. The basic impulse to stand up for the people he appointed isn’t a bad one; nor is the impulse to demonstrate to the intelligence community that he is no wild-eyed peacenik softie who opposes the work they do. For one thing, he’s more likely to effect change in national security areas if experts in the government believe he’s at least sympathetic to them as individuals and to their basic goals, even if he questions some of the George W.Bush-era (or earlier) methods. For another, the ability of bureaucrats to hurt the president with leaks doesn’t depend on the existence of deep dark secrets. Every president is vulnerable to selective leaks and a drumbeat of steady negative interpretations from the bureaucracy.
And yet, overdoing support for the bureaucracy can have severe costs. On torture, for example, emphasizing the good intentions of those faced with difficult choices during the last decade makes sense. But failing to take action, and leaving bureaucrats with serious liabilities because the status of their past actions is unresolved, only may have made reassuring them of presidential support increasingly necessary. That’s not a healthy situation.
Again: some of the incentive to (at least at first) stand up for presidential appointees is inherent in the presidency, and a healthy thing to do even when the president believes people have misbehaved and should go. But throughout his presidency, Obama has been overly skittish when it comes to potentially crossing his national security bureaucracy, and I strongly suspect that torture and other Bush-era abuses are both part of the original cause and will cause more of that timidity down the road.
Obama has been overly skittish when it comes to crossing his NatSec bureaucracy?
First, as I have already noted, Obama was perfectly happy demanding David Petraeus’ resignation for fucking his biographer. While I have my doubts whether that was really the reason — and while by firing him, Obama undercut a potential 2012 rival — he didn’t shy away from firing a man with some of the best PR in DC.
You might also ask the 19 top Generals and Admirals Obama has fired (most with the help of Bob Gates; also note the 20th on this list is Petraeus) — so many that conservatives accuse him of “purging” — whether he’s squeamish about crossing the NatSec bureaucracy. And while Micah Zenko’s comment on Twitter is correct that intelligence officials have largely escaped this treatment, Obama seemed happy to use Michael Leiter’s National Counterterrorism Center’s failure to stop the UndieBomb attack to fire then Director of National Intelligence Dennis Blair.
President Obama is not a man afraid to fire members of the national security bureaucracy.
The starkest contrast with Brennan’s treatment comes from the case of Stanley McChrystal.
Obama demanded McChrystal’s resignation not because his night raids were exacerbating extremism in Afghanistan. Not because many service members felt he had left them exposed. Not because, even then, it was clear the surge in Afghanistan was going to fail.
Obama demanded McChrystal’s resignation because Michael Hastings exposed McChrystal and his top aides (including Michael Flynn, who quit in April because of differences on policy) being insubordinate. Obama demanded McChrystal’s resignation because doing so was necessary to maintain the primacy of civilian control — like separation of powers, one of the bedrocks ensuring national security doesn’t trump democracy.
That, to me, is the important takeaway from comparing McChrystal’s fate with Brennan’s.
When a top member of the national security bureaucracy challenged the control of the civilian executive, he got canned, appropriately, in my opinion.
But when the Director of the CIA permitted his Agency to strike at the core of the separation of powers by investigating its overseers, Obama offered his support. Obama may have fired a top general for threatening Executive authority, but he has supported a top aide after he threatened Legislative authority.
You can come up with any number of explanations why Obama did that. But being afraid of taking on his National Security bureaucracy — as distinct from taking on the intelligence agencies, as Obama chose not to do when Clapper lied or when Keith Alexander oversaw the leaking of the family jewels even while getting pwned in his core cyberdefense capacity — is not the explanation.
Obama has proven to have no qualms about upsetting his national security bureaucracy. Just that part of it run covertly.
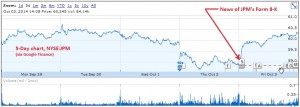 JPMorgan’s Form 8-K filed on Thursday with the Securities and Exchange Commission advises:
JPMorgan’s Form 8-K filed on Thursday with the Securities and Exchange Commission advises:
![[photo: liebeslakritze via Flickr]](http://www.emptywheel.net/wp-content/uploads/2013/06/SpyGrafitti_liebeslakritze-Flickr_300pxw.jpg)