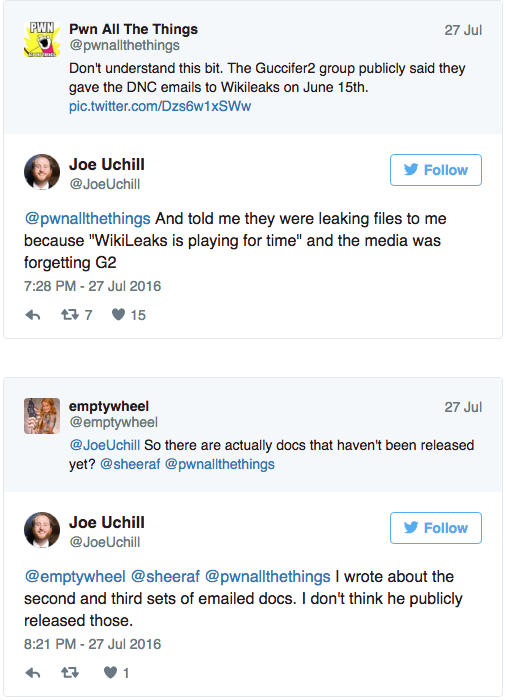
Monday: Skate Away
Monday means it’s movie day, and I think this charming little documentary fills the bill. Valley Of A Thousand Hills from Jess Colquhoun looks at Zulu youth participating in a skate camp and the impact on their lives. They’re quite optimistic in spite of limited resources and opportunities. The film left the feeling they’re on the verge of a breakthrough — like these kids could really change global culture if they wanted to. They appear more self-aware and energized than most adults I run into of late.
Wrath of Gods kind of weather
- Catastrophic flooding displaced more than 20,000 Baton Rouge area residents (NOLA.com) — Damn it, the news coverage on this flooding was so thin this morning save for local papers. Flood victims include the governor and his family who had to be rescued from their home; actor Wendell Pierce lost everything in his Baton Rouge area home. Four parishes had already been declared a disaster including Tangipahoa, St. Helena, East Baton Rouge and Livingston.
- Aerial photos show massive damage to more than 10,000 homes (TheAdvocate.com) — Follow Maya Lau on Twitter for more photos; LSU campus is inundated and many homes are beneath water to their rooflines.
- Severe monsoon flooding displaced 50,500 around Manila, Philippines (Floodlist) — There have been a handful of deaths reported with more persons unaccounted for. Worst rainfall amount in 24-hour period 14-15 August was 6 inches over the Dagupan area. More rain is expected.
- Half a month’s rain in short time period floods Moscow (euronews) — Flooding is worst Moscow has seen in 130 years. Reporting is extremely thin about this event which ocurred over the last 24-48 hours.
- Massive flash flood killed 20 last weekend in Skojpe, Macedonia (video, France24) — There’s quite a bit of video from other outlets in YouTube about the flooding; ironic that Russian aide workers went to help Macedonia just before flooding began in Moscow.
- Nearly 3000 homes swamped in Thailand (Bangkok Post) — Flooding near Phayao was the worst in seven years; at least one person is missing.
- Sudanese states Kassala, Sennar, South Kordofan, West Kordofan and North Darfur flooded, killing 100 (Deccan Chronicle) — Heavy rains since June worsening two weeks ago led to a late night flash flood that swept away villages. More than 100,000 have been displaced. Clean drinking water is now a serious problem.
Might be time to brush off that copy of J. G. Ballard’s The Drowned World and ponder a post-apocalyptic future under water. We’ve likely passed the 1.5C degree global warming threshold without any sense of urgency to act on climate change which fuels this wave of flooding.
Sigh-ber
- Hotels across ten states breached (Reuters) — Hey, now you philanderers have an excuse for that bizarre charge to your room at the Starwood, Marriott, Hyatt, or InterContinental hotel for strawberries, whip cream, and a leather flogger during your last business trip. “It’s just a hacker, honey, that’s all, really…” HEI Hotels & Resorts, the operator of the affected hotels, found the malware in its systems handling payment card data. The malware had been present in the system for roughly 18 months while 20,000 transactions were exposed.
- Google ‘secretly’ developing a new OS (TechnoBuffalo) — A well-known Linux blogger wrote Google references “Pink + Purple == Fuschia (a new Operating System)” in its Git repository. The two colors are believed to refer to Magenta and LK kernels which Google is using to build a wholly new operating system. Magenta does not have a Wikipedia entry at the time of this post but Googlesource has a brief explainer for Magenta and LK. The two kernels serve different purposes but combined they may be able to operate any device whether small Internet of Things single purpose devices or multi-purpose devices like personal computers. This may be the direction Google has chosen to go rather than fully merge its Chrome OS with Android. The new operating system could also resolve some annoying problems with antitrust regulators if Android is cut loose and managed by an open source consortium, perhaps one established by and aligned with the Open Handset Alliance.
- Banking malware attacks Android users browsing sites using Google AdSense (SecureList) — The thieves pay for a listing on AdSense, put their malicious ad in the system, and it downloads to an Android device whenever the user reads a website featuring the contaminated ad. Yuck. Use your antivirus app regularly on your Android devices as this nasty thing may pick up your financial information.
Longread: Manners matter?
At Aeon.com, Professor Eleanor Dickey of University of Reading-UK discusses the ‘magic word’ and its use in early democratic society, and its decline with the rise of a hierarchical system in the fourth century BCE. Are we a more or less democratic society based on our current level of societal manners?
Catch you tomorrow if the creek doesn’t rise!

![[Journalism 101 fail again -- who are these competitors and what country do they play for? Which sport is this?]](https://www.emptywheel.net/wp-content/uploads/2016/08/Olympics_Volleyball_BBC_08AUG2016.jpg)