“They Were Trying to Boot the Machine:” John Paul Mac Isaac Claims the FBI Really WERE That Incompetent
If you can believe John Paul Mac Isaac, the FBI did some incredibly bone-headed things after they obtained Hunter Biden’s laptop in December 2019. As he describes it in his book (which I read recently while stuck in a hospital awaiting foot surgery), on the very same day the FBI collected the laptop purported to belong to Hunter Biden, on December 9, 2019, someone named “Matt” told Mac Isaac they had tried to boot it up.
“Hi, my name is Matt,” said a voice I didn’t recognize. “I work with Agent DeMeo and Agent Wilson. Do you have a second? I have some questions about accessing the laptop.”
Confused, I responded, “Sure, what’s going on?”
“Did the laptop come with any cables or a charger? How can I connect the drive to a PC? When I plug it in, it wants to format the drive,” Matt said.
“PCs can’t natively read Mac-formatted disks. You will only be able to access the drive from another Mac.”
This is fairly common knowledge among most computer users, and I was surprised that any kind of tech person wouldn’t know it.
“Sadly, Hunter never left the charger or any other cables,” I went on. “I have a charger and everything you need back at the shop. You guys are welcome to it.”
I was feeling really uncomfortable. This Matt guy definitely didn’t seem to have the training or resources to be performing a forensic evaluation of the laptop. Hadn’t the whole reason for taking the laptop been to get it to a lab for proper evaluation and dissemination?
“Tell him we’re OK and we won’t need to go back to his shop,” Agent DeMeo said in the background. “We’ll call you back if we need to,” Matt said before hanging up.
[snip]
“Hi, it’s Matt again. So, we have a power supply and a USB-C cable, but when we boot up, I can’t get the mouse or keyboard to work.”
I couldn’t believe it—they were trying to boot the machine!
“The keyboard and trackpad were disconnected due to liquid damage. If you have a USB-C–to–USB-A adaptor, you should be able to use any USB keyboard or mouse,” I said. He related this to Agent DeMeo and quickly hung up.
Matt called yet again about an hour later.
“So this thing won’t stay on when it’s unplugged. Does the battery work?”
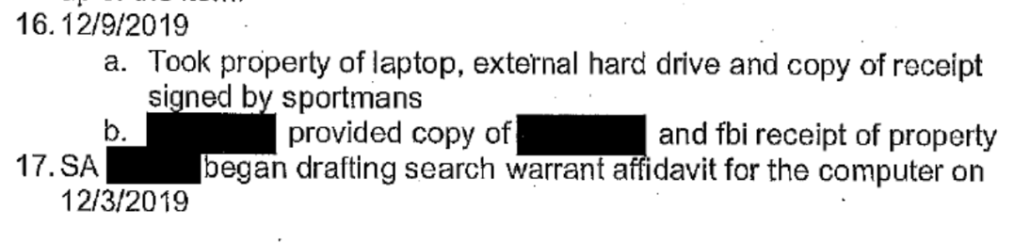
I explained that he needed to plug in the laptop and that once it turned on, the battery would start charging. I could sense his stress and his embarrassment at having to call repeatedly for help. [my emphasis]
To be sure, you can’t believe Mac Isaac.
His own story is riddled with questionable details and important discrepancies.
The most important discrepancy is his description of the laptop he turned over to the FBI, which he describes as a 2016 Mac, not the 2018 Mac identified by serial number.
I moved on to the last Mac, a thirteen-inch 2016 MacBook Pro. The drive was soldered onto the logic board. This one powered on but then would shut down. I suspected that there was a short in the keyboard or trackpad, and if I took it apart, I could at least get it to boot and possibly recover the data.
As I understand it, Mac Isaac’s claims that the hard drive was soldered onto the logic board is also inconsistent with the known details of the laptop shared with the FBI.
But there are important other discrepancies between the story Mac Isaac tells and the one the government tells. In his timeline of his interactions with the FBI, Mac Isaac gets the date for the actual handoff, December 9, correct, but other dates he uses differ from those that show up in Gary Shapley’s timeline. For example:
- Mac Isaac says that Agent Josh Wilson (who is mentioned in Shapley’s notes) reached out to his father on November 1; Shapley’s notes say that happened on November 3
- Mac Isaac says that Wilson called him on November 4; Shapley’s notes say that happened on November 6
- Mac Isaac says that Wilson came to his home on November 19; Shapley’s notes say that happened on November 7
These discrepancies aren’t all that important, legally. But Mac Isaac’s dates seem tailored to the impeachment proceedings going on in the same period, and so to laying a foundation for sharing the laptop with Rudy Giuliani.
A far more important set of discrepancies pertain to Mac Isaac’s description of what happened on December 9, 2019.
The blind computer repairman first describes that the second agent, Agent Mike DeMeo, called him to ask for the device identifiers that morning, before coming to the shop to pick up the device.
Agent DeMeo called around 9:30 a.m. It caught me a little off guard. The only other time we had communicated was shortly after our meeting almost three weeks earlier. He had asked me then to text him the timeline of my interaction with Hunter. I figured that he wanted something in writing showing the chain of custody—or it was an effort to trap me into writing something that could be twisted into a charge of lying to the FBI.
This time, he asked me to text him the model and serial number of the external drive and laptop. I explained that I hadn’t made it to the shop yet. “I need this information before we head over,” he insisted. “It’s important.”
“Give me thirty-five minutes,” I responded, then hung up. I finished getting ready and headed to the shop. After texting the numbers to Agent DeMeo, I waited in the shop with the blinds closed and the lights out, so as not to announce that the store was open. [my emphasis]
Shapley described that the FBI obtained and confirmed the device identifier before they ever met Mac Isaac, on November 6 (though perhaps Mac Isaac only referred to other identifiers needed for the subpoena).
Nevertheless, this discrepancy is important for a number of reasons, not least that if the FBI looked at all closely at the returns on a subscriber subpoena to Apple, it should have raised significant alarm that someone was trying to hack Hunter Biden. But if they didn’t obtain this information until the day they obtained the laptop, then they couldn’t have reviewed the subscriber data very closely in advance. That negligence might, in turn, amount to negligence in missing clear signs that the then former VP’s son was being hacked.
As Mac Isaac describes it, it was not until Agents arrived at his shop that they told him they were going to seize the laptop with a subpoena rather than imaging the laptop there at the shop.
Both agents arrived at my door about a half hour late. “Where’s the tech?” I asked, holding the door open.
“We have a change of plans,” Agent Wilson responded. “Can we go in the back?”
I led the agents to the back, and Agent Wilson placed his bag on the workbench. “
I have a subpoena here to collect the laptop, the drive, and all paperwork associated with the equipment,” he said, pulling out a collection of very formal and important-looking paperwork. “I’ll need you to sign it.”
When Mac Issac asked why they had changed their plan, he claims, lead Agent Josh Wilson deferred to Agent Mike DeMeo, who told him that they were taking the laptop back to a lab to image.
“You guys scared the shit out of me!” I exclaimed. “So why the change of plans? Don’t get me wrong; I’m grateful that you’re taking this stuff out of my shop.”
Agent Wilson looked over at Agent DeMeo, who was buried in his clipboard. “Ah, Mike?” he said. Agent DeMeo paused his writing and said, “We have a lab that takes these things and is better equipped than our field tech.”
Mac Isaac also claims that at that same meeting, DeMeo told him only to contact him, not Wilson.
“Tell them you keep abandoned equipment offsite, like a warehouse location,” Agent DeMeo answered, taking over. “Tell them it will take a day for you to check and they should call back the next day. Then immediately text me at my cell number. From now on, only communicate through my cell number. Not Agent Wilson, just me. We need to avoid communicating through, ah, normal channels. I’m sure you can understand. Text me and we will get the equipment back to you and deal with the situation.”
This communication works the opposite of the way you’d expect. Often, second agents are asked to take the stand, so you’d want them to have a clean digital trail. Here, the lead agent, Agent Wilson, was protecting his communications, whereas the second agent was not.
And then, as Mac Isaac tells it, that very same day, someone else, “Matt,” called using DeMeo’s phone, asking really embarrassing questions about how to access the laptop.
The claim that someone at the FBI was trying to boot up the laptop is alarming enough — though as I noted in July, there is some corroboration for the claim in Gary Shapley’s notes.
FBI determined in order to do a full forensic review a replacement laptop had to be purchased so the hard drive could be installed, booted and imaged.
[snip]
Josh Wilson stated that (while laughing) so whoever [people wanting to review the laptop] are they are going to have to buy a laptop to put the hard drive so they can read it.
Where Mac Isaac’s claims are totally inconsistent with the FBI claims, in a way that would cause grave legal problems for the FBI, is the date: Mac Isaac claims that the FBI was trying to boot up the laptop that same day, on December 9.
According to Gary Shapley’s notes, the FBI didn’t have approval to even get a warrant on December 9, much less have a signed warrant itself.
The FBI didn’t have a warrant to access the “Hunter Biden” “laptop” until December 13.
And yet, if you can believe Mac Isaac, the FBI was already trying to boot it up, perhaps irreparably altering its contents, three days before they got a warrant.
Featured image showing known dissemination of the “Hunter Biden” “laptop” by Thomas Fine.