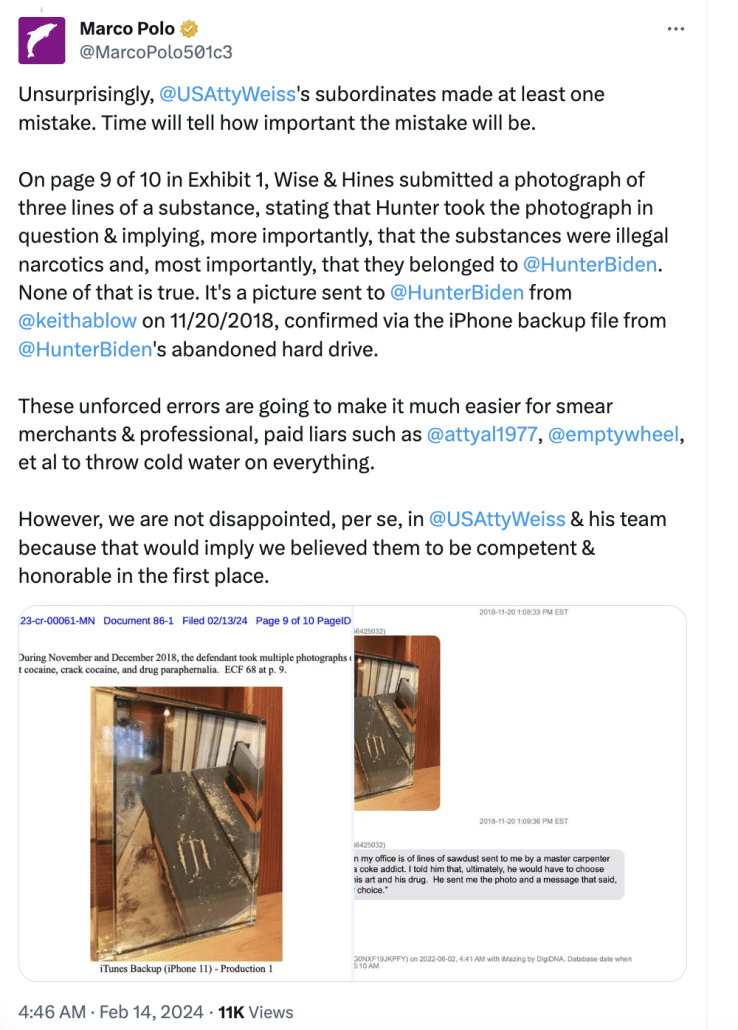
Joseph Ziegler, the disgruntled IRS agent who built a tax case on the digital payments Hunter Biden made during the depth of his addiction, is quite proud that he found one of the sex workers who slept with Joe Biden’s son. He brought it up twice in his testimony.
First, he boasted that he sought out women he called prostitutes and impressed the prosecutors.
Yeah. So standard practice is — for any transaction, you want to go out — and a lot of our job is hitting the pavement, going out and talking to people. There was a lot of different investigative steps that we took, that even going and talking to the prostitutes, we found multiple people that he called his employees that were also prostitutes, and that he would have them clean his hotel room or — there were a lot of these interviews that we ended up going and doing and talking to people that were so worth it, even though someone might — we were always being told by the prosecutors, you guys are wasting your time going and doing that. It’s not worth it. And literally, I would surprise them every time and find everyone.
Though maybe Ziegler was speaking loosely when he called these women prostitutes. Later in his testimony, he admitted that he had been calling Lunden Roberts, a former stripper and the mother of Hunter’s fourth child, a prostitute.
Then, he complained that prosecutors had withheld the sex videos involving a “potential prostitute” they had interviewed — effectively confessing that he had looked online for things that would have tainted his testimony.
But there was other things — we went out and talked to one of the potential prostitutes. And there were videos that I’ve seen out there on Twitter, on the internet, and information related to that person that I had never seen before.
He — or rather, Homeland Security Investigations — did find at least one sex worker, though.
In the documents Ziegler released last September, he included two interview excerpts, one with Hunter’s accountant, Jeffrey Gelfound, and another with a sex worker whom he calls “Gulnora.” Ziegler explained the two show that Hunter wrote off a payment to Gulnora, who admitted she met with Hunter as an escort.
EXHIBIT 1F & 1G: This was a memorandum of interview of Jeffrey Gelfound, Edward White & Company tax accountant who assisted with the preparation of RHB’s delinquent tax returns, to include the RHB’s personal and corporate tax returns for 2017 and 2018. When discussing deductions on RHB’s tax returns, Gelfound was asked about whole dollar transfers to Gulnora. Gelfound was asked if RHB verified this as a business expense in which Gelfound stated “Yes, we put it on the returns so …”. EXHIBIT 1G was an interview report turned over to the investigative team as a part of the RHB investigation. I have included a redacted excerpt of that interview of an escort by the name of Gulnora that was conducted on or about April of 2021 in which she admits to meeting RHB relating to escort work.
Note the interview with Gelfound, not the one with “Gulnora,” appears to have been in April 2021; the “Gulnora” one appears to have taken place in June 2021. Close enough for IRS-CI work, I guess.
In the Gelfound interview, DOJ Tax Prosecutor Mark Daly actually asks the accountant about two Venmo payments, one for $1,500 and another for $2,700.
DOJ-Tax Daly: [redacted] there is a series of large whole dollar transfers to something called Gulnora?
Jeffrey Gelfound: OK.
DOJ-Tax Daly: Do you know what that is?
Jeffrey Gelfound: I-I don’t.
DOJ-Tax Daly: OK – But Hunter verified to you that that was a business expense?
Jeffrey Gelfound: Yes, we put it on the returns so …
DOJ-Tax Daly: OK, um, there’s a series of Venmo transfers, large dollar ones, for example, [redacted]
Jeffrey Gelfound: OK.
DOJ-Tax Daly: On August 14th there’s a $1500 expense and on September 4th there’s a $2700 expense.
The $1,500 expense appears to be the one mentioned in the tax indictment, which I wrote about here. That payment was the first obvious charge on Hunter’s Venmo account after two new devices were added to Hunter’s Venmo account in two different cities. It appears to have happened a day earlier than described in the indictment (and than described in this interview, which will be admissible for impeachment at trial). To prove that Hunter intentionally wrote this off improperly, prosecutors will need to prove not just that Hunter — as opposed to the people who accessed his Venmo account days before this — made the payment, that Hunter, rather than the dancer, listed the payment as Art, and that he remembered all that in 2020.
And while the $2,700 payment doesn’t obviously appear in the indictment, it’s yet more proof of how problematic relying on payments Hunter made to sex workers will be for prosecutors (there are plenty of other payments they would have an easier time proving were improper write-offs, though).
The Venmo described as a September 4 payment appears to have been made on August 30, 2018. If that’s correct, then it was paid to a woman who was paid at least three times in two days, probably four. In addition to the $2,700 Venmo payment (shown in pink in the timeline below), she was paid a total of $1,800, via two payments, on Zelle. Then she was entered as a wire transfer recipient in Hunter’s Wells Fargo account, immediately after which someone was transferred $4,000. Those payments are shown in red on the timeline.
The three different methods of payment (from at least two bank accounts and a Visa debit card) are suspect enough.
They happened in a period when Hunter’s life was in remarkable turmoil, even by his standards. On Sunday, August 26, he left his bank card in an ATM machine. The next day, Monday, he either lost his phone or someone used the Lost Phone function to track Hunter as he moved across Venice, CA and ultimately to the AirBNB in the Hollywood Hills where he was staying for two nights. The next day, Tuesday, after he left the AirBNB, he discovered he had left a bag there. Ultimately the owner gave the bag to an Uber driver (but there’s no obvious Uber payment showing that Hunter got the bag back). The next day, Wednesday, Hunter either spent two hours trying to get onto Venmo; or someone spent hours trying to break into his account. Also that day, Hunter’s contact information for Wells Fargo was changed; it looks like Wells Fargo had two separate numbers ending in 9396 for him. That night appears to be when he first interacted with the sex worker the IRS calls Gulnora, because he paid her at close to 4AM. Consistent with what she told HSI 34 months later, they met again the next night, Thursday. He paid her via Zelle at 9:50PM, via Venmo at 11:04PM, and then probably via wire transfer at 6:41AM. Later that day, just after 7PM on August 31, Hunter would buy a new MacBook Pro using two credit cards; this is believed to be the laptop that would eventually end up in Fox News pundit Keith Ablow’s possession. Two and a half hours later, Hunter made an Account Recovery request to Apple (using a different phone number than the one(s) recently added to his Wells Fargo account), and the next day, Saturday, September 1, he started accessing his accounts from the new device. This was one of only two Apple Account Recovery attempts recorded in the publicly available emails, and unless he lost a laptop at the AirBNB, it’s not clear what device had been compromised (though he had lost an iPad earlier in August).
But that’s not all. The $4,000 wire transfer made in the same minute the sex worker was made a wire transfer recipient occurred immediately after something that also frequently occurred on Hunter’s Wells Fargo account: a reset of access after a suspected compromise.
On at least 36 occasions in 2017 and 2018 — and three times (marked in blue in the timeline) in the period in which this payment was made to a woman the IRS is calling Gulnora — Wells Fargo suspended his access because it suspected someone else was trying to access his account, which required him to change his password before he could access it. Most often, the password got changed and Face ID, allowing anyone with access to Hunter’s face or perhaps his fingerprint, would be turned back on. Probably, many if not most of those were not someone else trying to access the account; they were probably just Hunter trying to access the account, in ways that looked suspect. But the result is that he almost certainly repeatedly accessed his bank account while in the presence of a dealer or a sex worker awaiting payment, watching that he reset his password and then turned on Face ID. This would alert them that they could access Hunter’s account by using his face (or fingerprint), either of which would be accessible to them when he was wasted. As a result, like that Venmo payment made earlier in August, law enforcement wanting to prove that Hunter made a particular payment would need a whole lot of evidence about the circumstances of payment, to rule out someone else paying him or herself.
And unless someone interviewed the woman they call Gulnora (who was paid under a Russian last name) a second time, they didn’t get that evidence from her.
As it was, just two pages of nine in the interview pertained to Hunter Biden. The interview appears to have focused on how she became involved in an escort network run on Telegram. She claimed she only took two jobs with the madam who arranged the meeting with Joe Biden’s son — the two dates with Hunter, and one more, with a guy she called “John.” Though later in the interview she described interacting with the madam face to face once and with people she worked with on multiple “occasions,” which sounds like more than two clients (especially since, by description, Hunter called her directly to arrange the second date). The woman wasn’t sure what website he would have used to contact the madam. She was not asked the dates of the trysts.
What she did describe is that she had some uncertainty about the ID Hunter used to verify his identity, because it was not a California Driver’s License. That’s what led Hunter to explain who his father was, after which the woman the IRS calls Gulnora “became afraid.” But then, when she returned to her apartment, a friend provided her more information.
After [Gulnora] left the location, she arrived back at her apartment and told her friend who she was just with. [Gulnora] stated that her friend told her “you have no idea who you’re dealing with.” [Gulnora] stated that she deleted [redacted] number.
So by the time she went back that second day — to be paid $1,200 via Zelle at 9:50 and then $2,700 at 11:04 in the first Venmo payment after whatever had happened with Hunter’s Venmo account days earlier, probably followed by $4,000 the next morning — she did know who she was dealing with.
One more thing about the payments to this woman. Someone attempted to wire her $100 from Hunter’s account on February 27, 2019, in between the time when Hunter’s digital identity was packed up on a laptop and the day when that laptop would walk into a computer repair shop in Wilmington. That payment failed.
I don’t doubt that the sex worker did meet Joe Biden’s son. But there are no less than six possible identity compromises in the days leading up to their meetings. The very same day she was probably paid a fourth time in two days, Hunter Biden attempted to reclaim his digital identity.
It’s not just that prosecutors would have a difficult time proving that Hunter made these payments. It’s that they decided that turning them into a tax felony was the appropriate response to six possible identity compromises of the former Vice President’s son in one week.
Timeline
August 26 at 12:16PM: DroidHunter added to Apple account.
August 26 at 4:16PM: Hunter reserves AirBNB.
August 26 at 4:34PM: Hunter withdrew $800 from an ATM but left the card.
August 26 at 7:24PM: Hunter arrives AirBNB.
August 27 at 1:40AM: Hunter added a new Zelle recipient and then, a minute later, sent him $750. Two hours later, at 3:40 AM Hunter sent another $750.
August 27 at 4:13AM: Wells Fargo suspended his online access. Eight minutes later, Hunter’s password was reset, Face ID was turned back on, a new recipient was added, and $2,000 was transferred to that new recipient.
August 27 at 11:15PM: A sound was played on iPhone.
August 27 at 11:18PM: Hunter’s phone put into Lost Mode.
August 27 at 11:18PM: Apple Pay was suspended on his phone.
August 27 at 11:18PM: iPhone found in Venice, CA.
August 28 at 1:41AM: Wells Fargo suspended his online access. Seven minutes later, Hunter’s password was set, Face ID was turned back on.
August 28 at 9:25AM: iPhone found 11 minute walk away in Venice.
August 28 at 9:30AM: iPhone found 20 minute walk away in Venice.
August 28 at 10:42AM: iPhone found 9 minute walk away in Venice.
August 28 at 11:17AM: iPhone found 26 minute walk away in Venice.
August 28 at 11:35AM: iPhone found 13 minute drive away in LA.
August 28 at 11:53AM: iPhone found 11 minute drive away in LA.
August 28 at 12:11PM: iPhone found 4 minute drive away at AirBNB where Hunter was staying.
August 28 at 5:04PM: Apple Pay was reactivated to a device called “ChatMa.”
August 28 at 5:04PM: A sound was played on iPhone.
August 28 at 10:08PM: Hunter informs AirBNB owner he left a bag there.
August 28 at 11:54PM: AirBNB owner arranges to drop bag off with Uber driver.
August 29 at 2:00AM: Face ID turned on for Wells Fargo (possibly a different account?).
August 29 at 2:13AM: $2,000 requested on Venmo (probably associated with attempt to rent a place).
August 29 at 2:14AM: Please verify your email address on Venmo.
August 29 at 2:15AM: Please verify your email address on Venmo.
August 29 at 2:18AM: Please verify your email address on Venmo.
August 29 at 4:27AM: Please verify your email address on Venmo.
August 29 at 9:23AM: A new recipient, OA, added to Zelle.
August 29 at 9:36AM: A device is registered with Wells Fargo.
August 29 at 9:37AM: $600 sent to OA.
August 29 at 9:43AM: Updated contact info for Wells Fargo (seemingly two numbers ending in 9396); Hunter had at least one other number at the time.
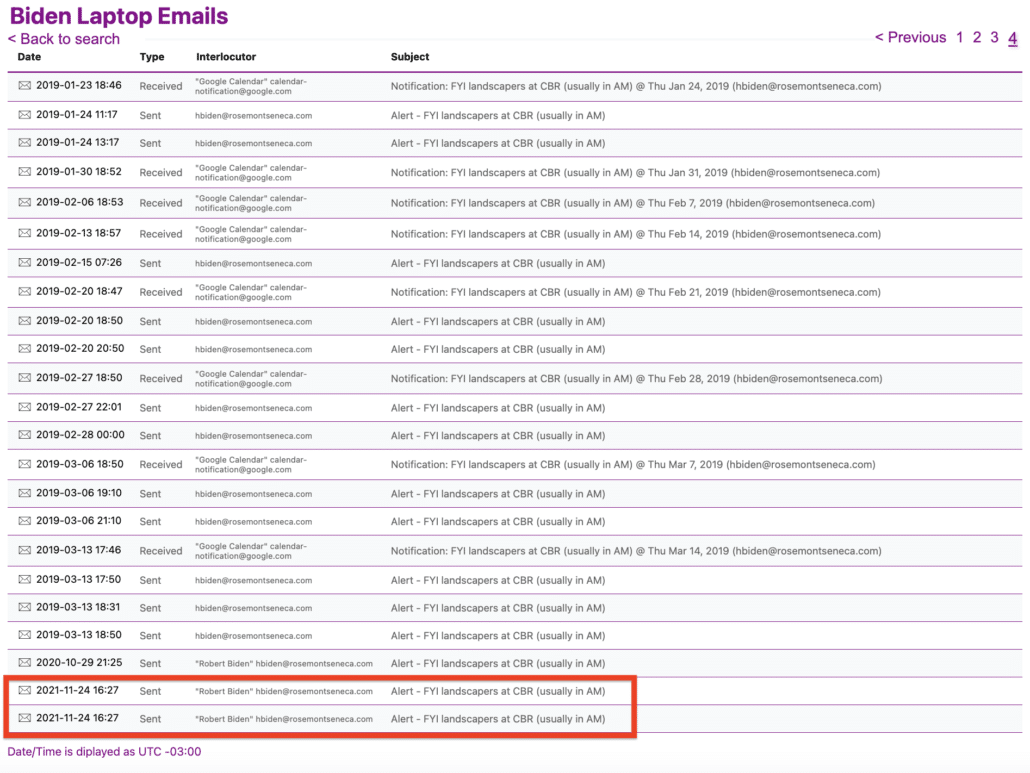
August 30 at 3:57AM: EK added to Zelle.
August 30 at 3:58AM: $600 sent via Zelle to EK from 4605.
August 30 at 4;45PM: $750 sent to Naomi Biden from 5858.
August 30 at 4:46PM: $750 sent to Roberta Biden from 5142.
August 30 at 4:46PM: $1000 sent to IS from 5858.
August 30 at 9:50PM: $1,200 sent via Zelle to EK from 5858.
August 30 at 11:04PM: $2,700 sent via Venmo to EK.
August 30 at 11:33PM: Wells Fargo suspends access.
August 31 at 6:03AM: Hunter’s password was reset.
August 31 at 6:34AM: Face ID turned on for Wells Fargo.
August 31 at 6:41AM: EK added as wire transfer recipient.
August 31 at 6:41AM: $4,000 transferred from 5858.
August 31 at 7:04PM: Ablow laptop purchased, using two credit cards, at Best Buy.
August 31 at 9:36PM: Apple account recovery request.
September 1 at 10:29AM: Password change.
September 1 at 10:34AM: Sign into MacBook Pro.
September 1 at 10:42AM: Sign into iCloud from browser.
September 1 at 4:24PM: Sign into DroidHunter.
September 1 at 4:27PM: KD added as wire transfer recipient.
September 1 at 4:28PM: $10,000 to be transferred on September 4 from 5142.
September 1 at 9:36PM: Call or text from Apple alerting him his Account Recovery was available due.
September 2 at 5:00AM: Hide2Vault downloaded to new Mac.
September 2 at 6:15AM: Sign into Rosemont Seneca.
February 27, 2019: Attempted $100 Zelle payment to EK.